Eyeglass PowerScale Edition Upgrade Guide
- Read Me First
- Before Executing Upgrade Steps
- In-place Upgrades
- Scenario #1 - Appliances running Older Open Suse OS to the latest release
- Scenario #2 - Appliances running Open Suse 15.1 or 15.2 OS to the latest release
- In-place Upgrade - Installer Download and Upgrade Procedures
- Upgrade to A New Appliance from an Old Appliance
- Step 1 - Upgrade Path From Old Appliance Versions to Open Suse 15.x OS with the latest Release - Backup/Restore Method
- Step 1a - Review Table of Migrated Settings
- Step 1b - Review Historical Eyeglass Data & Settings that are Not Restored before continuing
- Step 2 - Information to Record before Upgrading
- Step 2a - Automated Appliance Configuration Import
- Step 3 - Restore Zip File (old appliance) and Restore to New Appliance Procedures
- Post-Upgrade Steps (All Upgrade Paths)
- Validate - Service account permissions, Eyeglass Job Status, Pool Mappings, Licenses and Cluster Inventory
- Validate - Ransomware Defender, Easy Auditor, Performance Auditor License Assignment
- Validate Ransomware Defender and Easy Auditor settings
Read Me First
New Validations. Expect to get warnings post upgrade. This is expected and is a key feature of this release to detect failover conditions that must be addressed to be ready for failover. If you get alarms it is good, so the issues can be fixed.- SyncIQ Domain Mark for fast fail back - checks both clusters to verify if SyncIQ domain mark exists and will raise warning if not found (NOTE: it will raise warning if you did not apply sudo update on step #1)
- SPN Delegation for Access zone and IP pool failover - This check AD Delegation was completed to the cluster AD objects and the opposite cluster (cross test). If any test fails it will raise a warning with exactly which delegation permission is missing.
- DNS Dual Delegation - This ensures automatic DNS resolution is in place before a failover. This validation will inspect your DNS configuration to determine if the Delegation is correct, A records resolve to subnet service ip's in the correct subnet. If you use Infoblox this validation must be disabled. It only supports standards based Name server delegations and not DNS forwarding.
Before Executing Upgrade Steps
- The upgrade will disrupt Eyeglass services for less than 10 minutes
- A VM level snapshot should be taken before upgrade to allow rollback to the previous version of the appliance
In-place Upgrades
Scenario #1 - Appliances running Older Open Suse OS to the latest release
This option allows customers to upgrade to the latest release without deploying a new OVF to get the latest operating system. NOTE: OS version 42.3, 15.1 no longer receives security updates and is customers choice to stay on this OS of the appliance. NOTE: The OS is not covered by the support contract.
- To check the OS version
- ssh as admin user to Eyeglass
- type cat /etc/os-release
- The OS version is displayed
Scenario #2 - Appliances running Open Suse 15.1 or 15.2 OS to the latest release
- No special steps
- Continue to upgrade instructions here.
In-place Upgrade - Installer Download and Upgrade Procedures
- To complete an offline upgrade:
- Login to support site with a registered support account https://support.superna.net
- Scroll down on page after login to locate the software download validation form.
- Get the appliance ID from the about window of the Eyeglass desktop
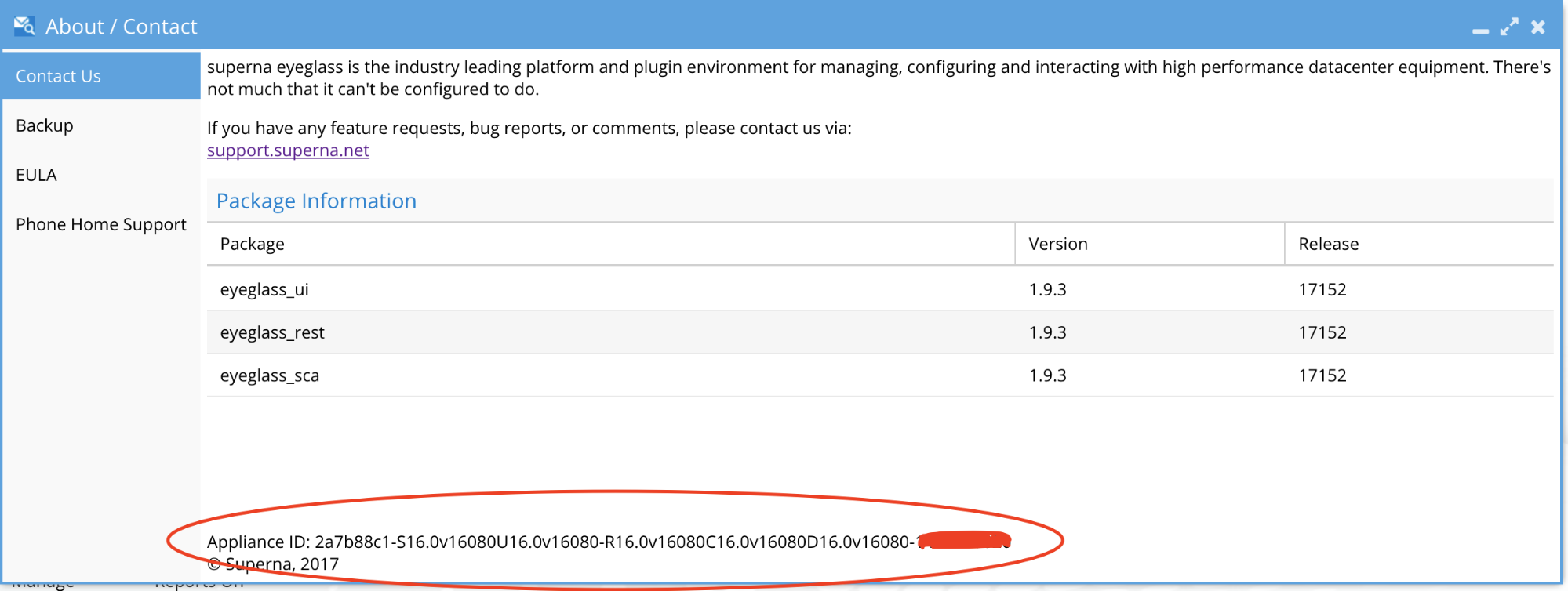
- Enter the appliance ID and click download button to retrieve the offline installer. NOTE: This command checks for an active support contract, and will only download software if support contract validation is successful.
- Use winscp tool (google winscp download) to copy the offline package onto the appliance with the admin user and password.
- ssh to the Eyeglass appliance and sudo to root command: sudo su - (you will be prompted for the admin password again)
- Make the offline package executable: chmod 755 <filename>
- Run the installer: ./<filename>
- You may be prompted for Phone Home Agreement if not previously set. Enter ‘y’ or ‘n’ to continue. Phone Home allows remote monitoring and faster support that allows remote log collection.
- Once the update is completed, login to the Eyeglass web page.
- IMPORTANT: Refresh any open Eyeglass window to ensure that you have latest changes.
- Check the About Eyeglass window and verify version shows the version you downloaded. The full list of releases can be found here.
- Complete
- Check Post upgrade steps here
Upgrade to A New Appliance from an Old Appliance
- Follow the steps in the next sections to complete the backup and restore process from an old appliance to a new appliance
Step 1 - Upgrade Path From Old Appliance Versions to Open Suse 15.x OS with the latest Release - Backup/Restore Method
All Appliance versions prior to latest version are using Open Suse OS versions that no longer have security patches available (13.1, 13.2 , 42.1, 42.3, 15.1). Use this upgrade option to get upgraded to the latest Eyeglass release and get the latest Open Suse 15.x OS that includes automatic security patch updates. NOTE: If you are using an older version appliance backup file some settings are not retained depending on the backup file release version. The table in this document outlines settings that are migrated.
- Follow steps to download the new OVF here
- Deploy new Eyeglass VM using the install guide as a reference.
- NOTE: The new appliance ip address can be different than the old appliance IP.
- Reference the table of settings that are migrated in the next section.
- After the new appliance is deployed and you can login to the webUI and ssh then continue with the steps below.
Step 1a - Review Table of Migrated Settings
Eyeglass Configuration Item | Source Appliance software version > 1.8.0 |
Restoring local credentials for clusters | Yes |
Restoring licenses keys | Yes |
Adjusting licenses keys to latest format | Yes |
Job Schedules | Yes |
Job Initial state Setting (enabled, disabled) | No |
custom settings with igls adv command. | Yes |
Restore Notification Center settings1
| Yes |
Restoring failover log history (if available) | Yes |
Restoring custom RBAC roles (if available) | Yes |
Restoring API tokens (if available) | Yes (as of 1.9.0) |
Restoring Ransomware Defender security guard logs (if available) | Yes |
Restoring cluster Configuration reports (if available)
| Yes |
Restoring Current Job state (enabled, disabled, DFS mode) (if available) | Yes |
Alarm history | No |
Old Backups Archives | No |
Cluster Storage Monitor Data (if available) | No |
RPO Generated Reports | No |
RPO Report Data | No |
Failover Scripts | Yes |
Ransomware Defender Settings and History (if available)
2. schedule is restored but no other settings - these need to be re-added manually with user service account and password. | No |
Step 1b - Review Historical Eyeglass Data & Settings that are Not Restored before continuing
- All existing Eyeglass databases are removed, no backup is made.
- NOTE: This will delete databases and they will be rediscovered on startup. DO NOT USE this method if you have Cluster Storage Monitor or Ransomware Defender historical events or RPO Report data that you need to retain. Contact support if this applies to you scenario.
Step 2 - Information to Record before Upgrading
- Take a screenshot of the Eyeglass Jobs window prior to upgrade. This can be used as a reference to verify Job state and type. Example auto type or dfs type.
- (if IP pool mode configured) Take a screenshot of the IP Pool failover policy to pool mappings
- (if Ransomware Defender) Take a screenshot of Ransomware Defender
- Flag as False Positive (2.5.6 and lower) / Learned Thresholds (2.5.7 and higher)
- Ignored List
- Threshold window all settings
- Allowed Files (2.5.6 and lower) / File Filters (2.5.7 and higher)
- Monitor Only Settings (2.5.7 and higher)
- (if Easy Auditor) Take a screenshot of Easy Auditor
- Active Auditor Triggers configured
Step 2a - Automated Appliance Configuration Import
- Requirements:
- Must be running 2.5.7.1 or later new OVA appliance. Check About Icon for the version. NOTE: Do not use this command if not running the correct version and use Step 3 below if running a version < 2.5.7.1
- SSH access from new appliance to the old appliance
- New appliance is deployed on a new ip address
- 2.5.7.1
- ECA must be updated to point at the new eyeglass IP address
- 2.5.8
- This release will automatically update the ECA configuration and update the Eyeglass IP address and API token and push the change to all ECA nodes
- NOTE: This option will not migrate custom threat file settings on ECA. This is not a common modification to ECA deployments and does not apply to most deployments.
- NOTE: This command can take 10 minutes to run.
- On the new appliance login as admin
- run import command: igls app pull-config --ip=<ip> --user=<user>
- IP = address of the old eyeglass appliance
- --user = admin
- You will be prompted for the password
- The command will automate the following steps:
- create a backup
- copy the backup to the new appliance
- apply the backup to the new appliance.
- Update the ECA configuration to use the new eyeglass IP address
- NOTE: after this command completes you will need to restart the ECA cluster to update the firewall configuration.
- login to ECA node 1 and run ecactl cluster down, followed by ecactl cluster up
- NOTE: after this command completes you will need to restart the ECA cluster to update the firewall configuration.
- Shutdown the OS on the source appliance
- done.
- Once the steps complete - Skip to - Check Post upgrade steps here
Step 3 - Restore Zip File (old appliance) and Restore to New Appliance Procedures
- Take an Eyeglass Restore backup from your old Eyeglass appliance.
- Download the Restore backup locally and then copy the zip file backup using scp or winscp to the newly deployed Eyeglass Appliance. It should be placed in /tmp folder .
- See Restore Backup button that is required versus support backup. The Restore backup includes SSL private keys, the support backup does not. This applies to Releases > 2.5.3
-
- Power off the old Eyeglass appliance. It is not supported to have multiple Eyeglass appliances managing the same clusters.
- SSH to new Eyeglass appliance and login as admin (default password 3y3gl4ss). Issue “sudo su -” to enter in root mode (default password 3y3gl4ss).
- From the command line execute the command
- igls app restore /tmp/<eyeglass_backup.xxxx.zip> --anyrelease
- Replacing /tmp/<eyeglass_backup.xxxx.zip> with the name of the Eyeglass Archive file always including full path.
- You will be prompted to continue. Enter “y” to continue.
- For example:
- igls app restore /tmp/eyeglass_backup_17-07-05_20-42-08.zip --anyrelease
- Do you want to revert to the archive at /tmp/eyeglass_backup_17-07-05_20-42-08.zip? [y/N]: y
- Once the restore is complete continue below
- For 2.5.6 to 2.5.7 anyrelease restore where Ransomware Defender or Easy Auditor products are used then these additional steps are required to restore custom Ransomware Defender/Easy Auditor Settings:
- If you have this file present on your ECA node 1, /opt/superna/eca/conf/common/overrides/ThreatLevels.json, copy it to the new Eyeglass appliance into the /opt/superna/sca/data directory and apply same owner and permission as other files in the folder.
- sudo to root
- copy the ThreatLevel.json file into the /opt/superna/sca/data directory
- chmod 644 /opt/superna/sca/data/ThreatLevels.json
- chown sca:users /opt/superna/sca/data/ThreatLevels.json
- On the new Eyeglass appliance if this file /opt/superna/sca/data/rwdefender/RSWSettings.json exists delete it
- rm /opt/superna/sca/data/rwdefender/RSWSettings.json
- Then download the matching 2.5.7 run file for Eyeglass upgrade and copy it to the 2.5.7 appliance and then run it to restore custom Ransomware Defender settings - see instructions here for In Place Upgrade - Installer Download and Upgrade Procedures.
- If you have this file present on your ECA node 1, /opt/superna/eca/conf/common/overrides/ThreatLevels.json, copy it to the new Eyeglass appliance into the /opt/superna/sca/data directory and apply same owner and permission as other files in the folder.
- Check Post upgrade steps here
Post-Upgrade Steps (All Upgrade Paths)
Validate - Service account permissions, Eyeglass Job Status, Pool Mappings, Licenses and Cluster Inventory
- Mandatory Step - Check minimum permissions sudo section in this document are all in place for your release. This will generate errors if permissions are not correct. Use this guide to review sudo permissions.
- Login to the new Eyeglass appliance and check:
- Open Jobs window and verify all jobs modes are set correctly and appear in either config sync or DFS section. The screenshot taken before should be used to check the jobs are in the correct mode.
- If the jobs are in the wrong mode please set the mode correctly with the bulk actions menu.
- (only If IP Pool failover Mode is configured otherwise skip) use the screenshot taken above to verify the synciq pool mappings using the DR Dashboard mapping screen to verify they look correct.
- Open License Manager Icon and verify Licenses are visible.
- Open Inventory Icon and verifyClusters are displayed.
- Log in to the Eyeglass web page and open the Eyeglass Main Menu -> Notification Center and verify that the Alarm Severity Filter is correctly set
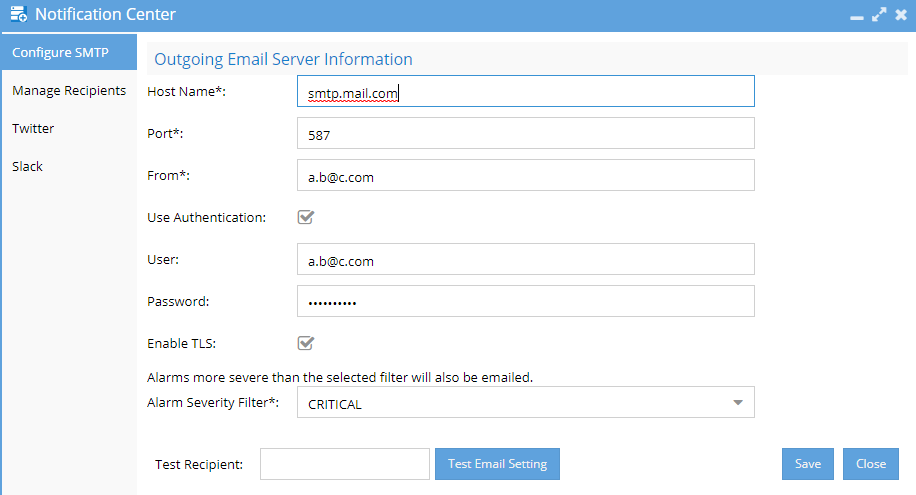
- And verify that the Email Recipients are correctly set with the correct Email Type.
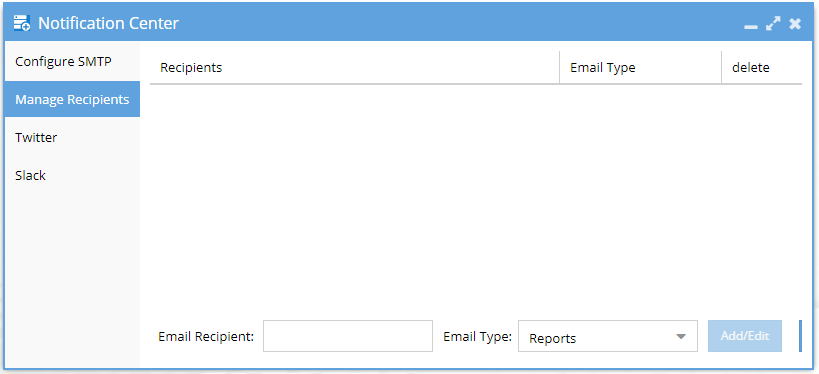
- done
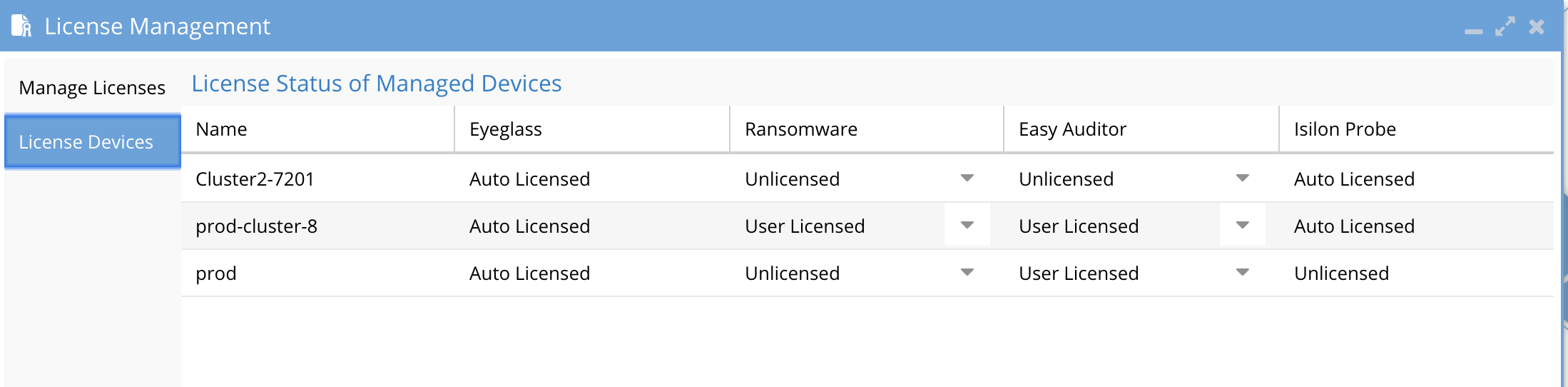
Validate - Ransomware Defender, Easy Auditor, Performance Auditor License Assignment
- This step is mandatory to ensure licenses are assigned to the correct cluster. This release no longer supports auto assigned license mode to clusters
- Login to Eyeglass
- Open License Manager
- Click on Licensed Devices tab
- First STEP: Set each cluster that should NOT be licensed to Unlicensed status using the drop down menu.
- 2nd STEP: Set each cluster listed to User Licensed for the product(s) that should be assigned to this cluster. Example the production writeable clusters should be set to User Licensed for Ransomware Defender or Easy Auditor.
- Click the submit button to save.
Validate Ransomware Defender and Easy Auditor settings
Validate that Ransomware Defender and Easy Auditor settings preserved after upgrade:
- (if Ransomware Defender) verify
- Flag as False Positive (2.5.6 and lower) / Learned Thresholds (2.5.7 and higher)
- Ignored List
- Threshold window all settings
- Allowed Files (2.5.6 and lower) / File Filters (2.5.7 and higher)
- Monitor Only Settings (2.5.7 and higher)
- (if Easy Auditor) verify
- Active Auditor Triggers configured