Eyeglass Service Account Minimum Privileges
- Overview
- Step 1 - Creating the local PowerScale Eyeglass User - PowerScale Command Line For Eyeglass DR, Ransomware Defender, Easy Auditor and Storage Cluster Monitor
- Ransomware Defender Cyber Recovery Manager Permissions Required:
- Easy Auditor Additional Permissions Required:
- AnyCopy Additional Permissions Required:
- Step 1A - Search & Recover and Golden Copy Product Service Account Local PowerScale User Account Creation:
- Step 2 - SUDO Root Level Commands Needed for Eyeglass DR & Airgap , Cluster Storage Monitor Unlock My Files
- Steps to create sudo entries on PowerScale
- SUDO file Updates Required for DR Edition & Airgap Enterprise Protected Clusters
- SUDO File Updates Required for Cluster Storage Monitor Unlock My Files Product
- AirGap Cyber Vault deployments on all the protected clusters
- How to Restart Eyeglass services after making permissions changes:
- How to use Eyeglass DR Edition with Compliance Mode Clusters
- How to use Eyeglass DR Edition with Clusters using STIG Hardening
- How to Create Eyeglass Service Account on Dell ECS For Ransomware Defender
- How to create the Airgap Eyeglass Service Account for the Vault Cluster
- Eyeglass Airgap Enterprise vault service account creation for Inside the vault configuration
- Eyeglass Airgap service account Creation for outside the vault configuration only
- Vault cluster sudo file for inside or outside the vault configuration
Overview
Eyeglass communicates with PowerScale clusters to perform discovery and add/update/delete of share, export and quota configuration information. The minimum PowerScale cluster node user privileges required for Eyeglass/PowerScale connectivity to successfully perform configuration replication and support other Eyeglass features are:

|
NOTE: Any change to Eyeglass Service Account privileges requires an Eyeglass sca service restart to recognize the change (procedure below). NOTE: AD or LDAP user is not supported, this lowers the system availability and adds dependency on AD/LDAP servers for API calls, local users on PowerScale have no dependence on AD/LDAP, in addition this generates too many authentication requests for API calls. |
In addition to the creation of the Eyeglass service account on the PowerScale cluster, the sudoer file on the cluster must be updated to allow the Eyeglass service account to execute OneFS CLI commands that require Elevated Permissions to run as root.
Step 1 - Creating the local PowerScale Eyeglass User - PowerScale Command Line For Eyeglass DR, Ransomware Defender, Easy Auditor and Storage Cluster Monitor
Use these permissions for all of the products above.
- Follow create steps below
- Then move to step 2 SUDO file configuration
To provision user and role from the PowerScale Cluster command line:
These commands below are executable by ssh as root on PowerScale and then right-click:

|
Note: Service account set to password never expires. |
isi auth roles create --name EyeglassAdmin --description "EyeglassAdmin role"
isi auth users create eyeglass --enabled yes --password 3y3gl4ss
isi auth users modify eyeglass --password-expires no
isi auth roles modify EyeglassAdmin --add-user eyeglass
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_LOGIN_PAPI
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_AUTH
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_ROLE
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_NFS
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_SMB
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_NETWORK
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_QUOTA
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_LOGIN_SSH
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_AUDIT
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_SYNCIQ
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_NS_IFS_ACCESS
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_EVENT
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_HDFS
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_REMOTE_SUPPORT
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_SNAPSHOT
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_SMARTPOOLS
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_WORM
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_STATISTICS
isi auth roles modify EyeglassAdmin --add-priv ISI_PRIV_JOB_ENGINE
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_CLOUDPOOLS
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_DEVICES
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_FILE_FILTER
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_HARDENING
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_NDMP
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_MONITORING
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_ANTIVIRUS
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_HTTP
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_NTP
* new in 2.5.8 for config backup *
Ransomware Defender Cyber Recovery Manager Permissions Required:
Easy Auditor Additional Permissions Required:
If using Easy Auditor add this additional permission
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_NS_TRAVERSE
AnyCopy Additional Permissions Required:
If using AnyCopy add these additional permissions
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_IFS_BACKUP
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_IFS_RESTORE
Step 1A - Search & Recover and Golden Copy Product Service Account Local PowerScale User Account Creation:
- Follow these instructions to create a dedicated Search & Recover/Golden Copy.
isi auth roles create --name EyeglassAdminSR --description "Eyeglass Search & Recover role"
isi auth users create eyeglassSR --enabled yes --password 3y3gl4ss
isi auth users modify eyeglassSR --password-expires no
isi auth roles modify EyeglassAdminSR --add-user eyeglassSR
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_LOGIN_PAPI
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_AUTH
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_SMB
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_NFS
isi auth roles modify EyeglassAdminSR --add-priv ISI_PRIV_SNAPSHOT
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_DEVICES
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_NS_TRAVERSE
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_NS_IFS_ACCESS
isi auth roles modify EyeglassAdminSR --add-priv ISI_PRIV_JOB_ENGINE
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_NETWORK (New As of May 2019)
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_STATISTICS
isi auth roles modify EyeglassAdminSR --add-priv ISI_PRIV_CONFIGURATION
****** Only required ACL security mode and file recovery portal feature *************
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_IFS_BACKUP
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_IFS_RESTORE
********* new as of 1.1.5 File pool reporting ***********
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_CLOUDPOOLS
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_SMARTPOOLS
***** only add below for Golden Copy Product 1.1.6 and later requires these *****
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_LOGIN_SSH
isi auth roles modify EyeglassAdminSR --add-priv ISI_PRIV_NETWORK
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_SMARTPOOLS
********** Golden Copy ACL permissions collection and apply on recall *******************
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_IFS_BACKUP
isi auth roles modify EyeglassAdminSR --add-priv-ro ISI_PRIV_IFS_RESTORE
Step 2 - SUDO Root Level Commands Needed for Eyeglass DR & Airgap , Cluster Storage Monitor Unlock My Files
In order to execute the some commands from the CLI that are not available in the PAPI for OneFS and require root-level (sudo) privileges for execution, this allows service accounts to run the command without having root access.
Apply the settings that apply to the applications you have purchased, apply to all clusters managed by Eyeglass products.
Steps to create sudo entries on PowerScale
- Edit the sudoer file using the PowerScale isi_visudo command.
- Sudo file opens in vi editor.
- NOTE: Add lines for the applications you need to enable; each product has different sudo requirements, review each section that applies below.
- Save your changes. ( : then type wq!)
- Repeat step for each cluster managed by Eyeglass.
SUDO file Updates Required for DR Edition & Airgap Enterprise Protected Clusters
Add the following lines DR product:
# (new for 2.5.6 DR validation)
Add the following line, if your PowerScale version is below 9.5.0
entries should be deleted for 2.5.6 or later releases
SUDO File Updates Required for Cluster Storage Monitor Unlock My Files Product
AirGap Cyber Vault deployments on all the protected clusters
eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ?? curl *
eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ? whoami; hostname
eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ?? whoami; hostname
The new entries for Cluster Storage Monitor UnLock My files are for 9.3 isilons and the later version:
eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -s isi smb openfiles list *
eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array isi smb openfiles close *
# airgap enterprise permissions to ping the vault cluster
eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ? ping *
eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ?? ping *
How to Restart Eyeglass services after making permissions changes:
- SSH to Eyeglass appliance
- Type: sudo su - (to elevate to root user - enter the admin user password)
- Type: systemctl restart sca
- Type: systemctl status sca (to verify sca service active and running after the restart)
How to use Eyeglass DR Edition with Compliance Mode Clusters
For clusters using compliance mode sudoer and root access is not permitted.
This means that clusters must be added to Eyeglass using the user below:
Compadmin
How to use Eyeglass DR Edition with Clusters using STIG Hardening
- You can enable STIG OS hardening on the cluster using:
- isi hardening apply --profile=STIG --report=true
- done
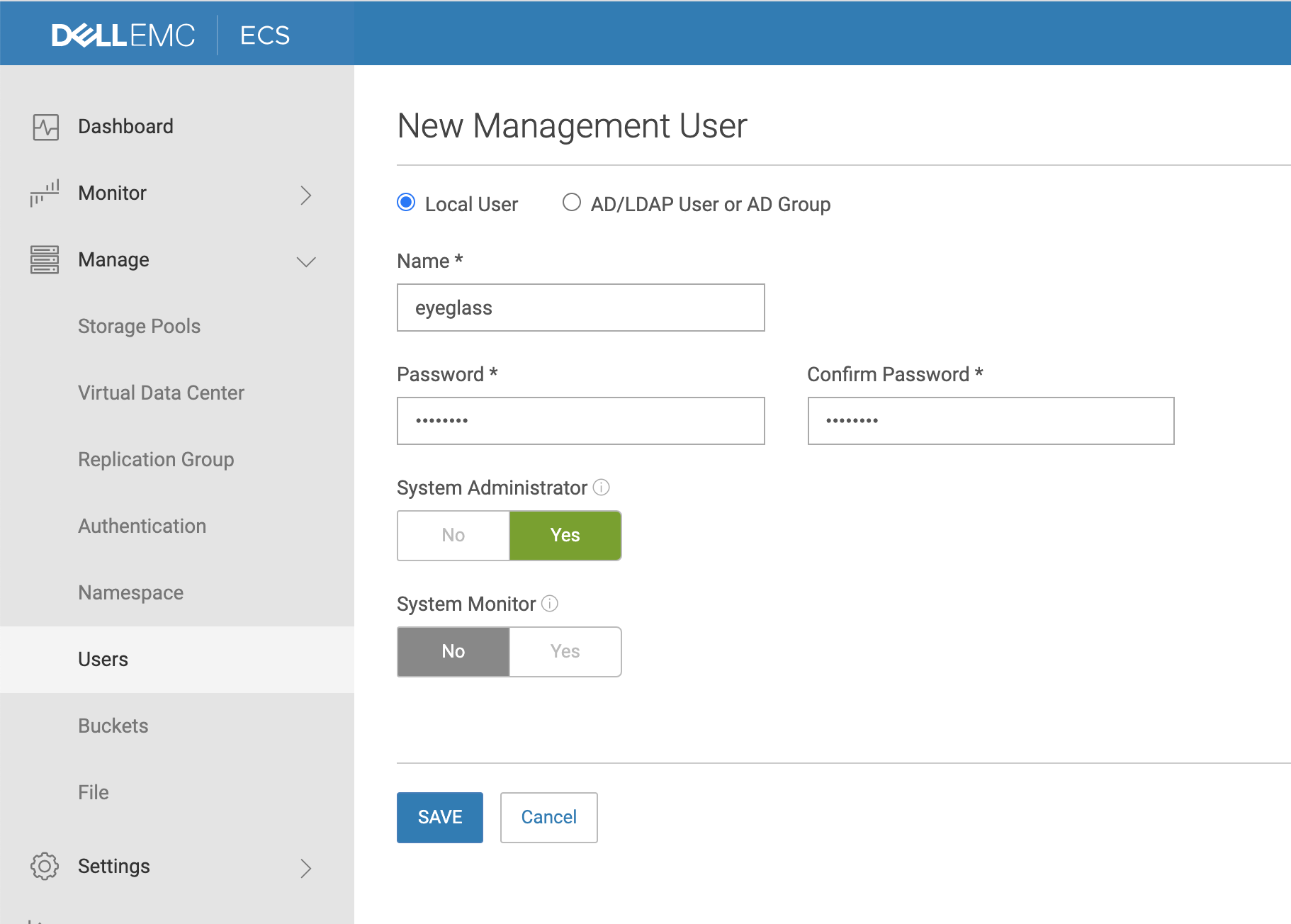
How to Create Eyeglass Service Account on Dell ECS For Ransomware Defender
- Login to the ECS as admin, expand the management menu, click users, select Management users tab, Click New User.
- Complete the form as per below example. User name eyeglass with administrator role assigned and set a password.
How to create the Airgap Eyeglass Service Account for the Vault Cluster
Follow these steps on the vault cluster during vault cluster hardening. Replace the yellow with a strong password, the security officer or security personnel should only know that.

| NOTE: The protected production cluster requires additional sudo permissions for vault alarm collection and Enterprise vault secure tunnel communications to Ransomware Defender. See the eyeglass service account update section for the eyeglass service account. |
Eyeglass Airgap Enterprise vault service account creation for Inside the vault configuration
Create this user on the vault cluster if using inside the vault configuration.
isi auth roles create --name EyeglassAdminvault --description “EyeglassAdmin role Vault”
isi auth users create eyeglass --enabled yes --password 3y3gl4ss
isi auth users modify eyeglass --password-expires no
isi auth roles modify EyeglassAdminvault --add-user eyeglass
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_LOGIN_PAPI
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_DEVICES
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_NS_IFS_ACCESS
isi auth roles modify EyeglassAdminvault --add-priv ISI_PRIV_JOB_ENGINE
isi auth roles modify EyeglassAdminvault --add-priv ISI_PRIV_NETWORK
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_LOGIN_SSH
isi auth roles modify EyeglassAdminvault --add-priv ISI_PRIV_SYNCIQ
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_EVENT
Eyeglass Airgap service account Creation for outside the vault configuration only
Create this user on the vault cluster if using outside the vault configuration without a vault agent running inside the vault.
isi auth roles create --name EyeglassAdminvault --description “EyeglassAdmin role Vault”
isi auth users create eyeglass --enabled yes --password 3y3gl4ss
isi auth users modify eyeglass --password-expires no
isi auth roles modify EyeglassAdminvault --add-user eyeglass
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_LOGIN_PAPI
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_DEVICES
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_NS_IFS_ACCESS
isi auth roles modify EyeglassAdminvault --add-priv ISI_PRIV_JOB_ENGINE
isi auth roles modify EyeglassAdminvault --add-priv ISI_PRIV_NETWORK
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_LOGIN_SSH
isi auth roles modify EyeglassAdminvault --add-priv ISI_PRIV_SYNCIQ
isi auth roles modify EyeglassAdmin --add-priv-ro ISI_PRIV_STATISTICS
isi auth roles modify EyeglassAdminvault --add-priv-ro ISI_PRIV_EVENT
Vault cluster sudo file for inside or outside the vault configuration
- Edit the sudoer file using the PowerScale isi_visudo command.
- Sudo file opens in vi editor
- eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_gather_info
- eyeglass ALL=(ALL) NOPASSWD: /usr/local/bin/curl -s -k -i -m 3600 -0 -X PUT --upload-file /ifs/data/Isilon_Support/pkg/*
- eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ? curl *
- eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ?? curl *
- eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ? whoami; hostname
- eyeglass ALL=(ALL) NOPASSWD: /usr/bin/isi_for_array -n ?? whoami; hostname
- Save your changes. ( : then type wq!)
- Repeat on each protected cluster (clusters outside the vault that replicate into the vault)