Administration Guides
S3 On Premise Cyber Vault Solution
Home
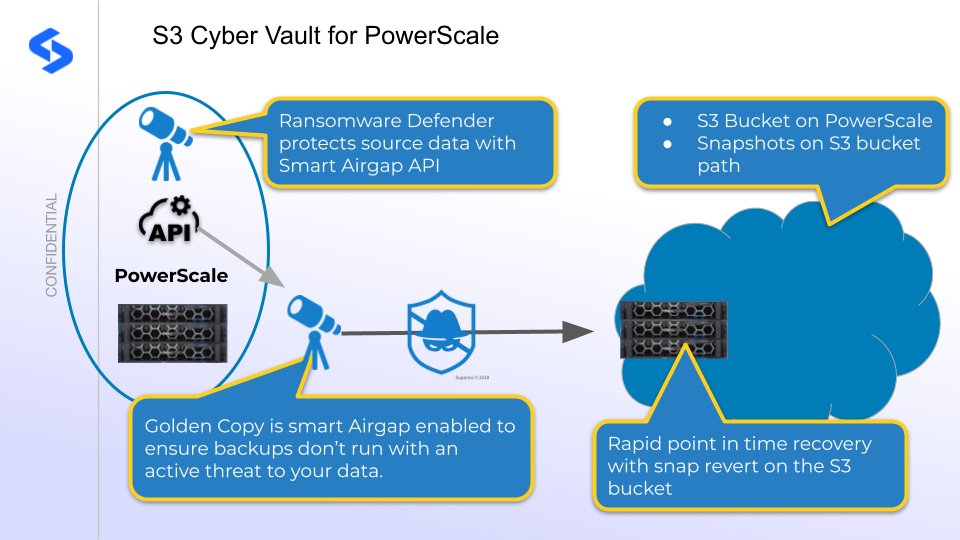
- Overview
- Key Challenges Solved
- Prerequisites
- Topology Diagram
- Configuration Steps
- Configure PowerScale bucket
- Configure Golden Copy
- Data Recovery & Cluster Configuration Backup
- Summary
Overview
Customers looking for next generation backup solution with an immutability option and file versioning support that require a rapid RTO for data recovery can now leverage Golden Copy and Ransomware Defender with PowerScale S3 protocol creates a Cyber Vault solution. Can also be leveraged with Cloud Storage for an offsite
Key Challenges Solved
- 3-2-1 policy allows the vault storage to use only the S3 protocol to access the vault in a steady state.
- Rapid RTO of a Cyber Vault backup using PowerScale and the S3 protocol
- File Versioning space efficiency. Unlike traditional S3 storage where versions of the same file consume the full size of the file regardless of the bytes that changed in the file, The powerscale solution leverages block level differencing within Snapshots to save space when storing versions of the same files.
- Support for file versioning and repaid object recovery in bulk using Snapshots on PowerScale versus S3 version aware recall with Golden copy. This provides a much faster point in time recovery using S3 storage
- Integrated with Ransomware Defender Zero Trust Backup API to ensure backups automatically stop replication with the source data is under threat.
Prerequisites
- PowerScale 9.x or later
- S3 bucket configured on PowerScale
- Golden Copy 1.1.7 or later with the Advanced license key
- Ransomware Defender 2.5.12 or later
Topology Diagram

Configuration Steps
- Enable Zero trust api integration with Ransomware defender
- Login to Golden copy node 1
- nano /opt/superna/eca/eca-env-common.conf
- paste this line to the file and change the yellow highlighted x.x.x.x with the ip address of Eyeglass VM, and the API token created to authenticate. API web token can be created from the main menu Eyeglass API menu UI.
- export EYEGLASS_LOCATION=x.x.x.x
- export EYEGLASS_API_TOKEN=yyyyyyyy
- control + x to save and exit
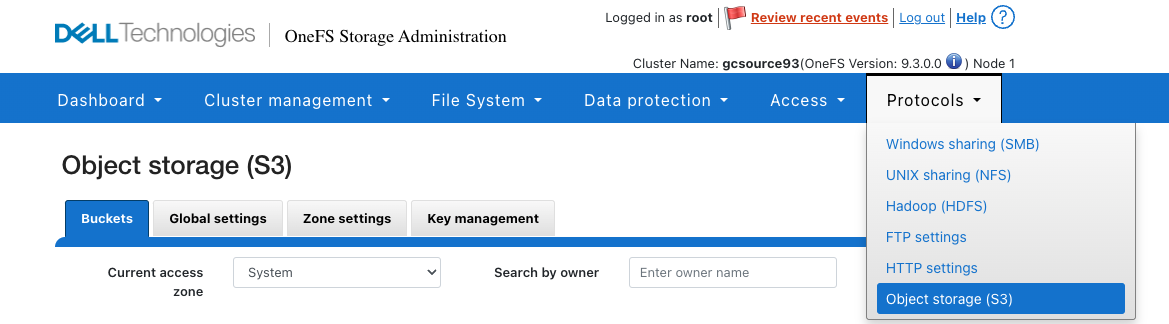
Configure PowerScale bucket
- Login to create a bucket
- Create a set of keys associated to an AD or local user
- Create the bucket example /ifs/data/cybervaultdata
- Create a daily snapshot on this same path and set the retention to match your recovery RPO goals. Example daily and retain for 30 days before expiring the snapshot
Configure Golden Copy
- NOTE: Delete handling needs to be configured globally on Golden Copy. Determine if you want data deleted from the cybervault S3 bucket during incrementals or to leave deleted data in the vault.
- Login as ecaadmin
- Modify the sample command below for your environment
- searchctl archivedfolders add --isilon gcsource93 --folder /ifs/data/archive--accesskey xxxxx --secretkeyyyyyyy --endpoint https://y.y.y.y:9021 --bucket test --region us-east-1 --endpoint-ips z.z.z.z,w.w.w.w --cloudtype ecs --customMetaData --storeFileHistory
- replace the yellow values with correct values for your environment. The endpoint ips should be the IP of nodes in the IP pool serving data for the S3 bucket.
- Run a full backup job
- Configure an incremental job on the folder definition to run before the schedule snapshot on the cyber vault path.
- Best Practice: Enabling the Configuration backup feature in Golden Copy exports all shares, nfs exports, quotas to json format and stores a copy on the vault cluster. This is documented here. This provides not only a data protection solution but also a device level solution to restore the cluster configuration information.
Data Recovery & Cluster Configuration Backup
- Recovery Scenarios
- Scenario 1 - To recover data the PowerScale can leverage SMB or NFS access in read only or read write mode anywhere in the file system tree that was created by Golden Copy.
- Select a snapshot version and reverting Golden Copy backup data to any point in the passed based on snapshot retention settings on the Vault cluster
- Scenario 2 - Restore data to the source PowerScale using Golden copy recall feature. Full or partial recovery of any path in the file system is possible to prioritize which data is recalled first.
- Scenario 3 - Create SyncIQ policies on the Vault cluster and use differential mode to only copy updated data back to the production cluster OR create new policies to replicate data to a new powerscale cluster.
- Scenario 4 - Determine if the configuration data backup is needed. Copy the json files to the PowerScale cluster and run the import configuration CLI commands to read the json files and create the configuration information on the cluster. Consult with Dell support on the specific steps.
- Scenario 1 - To recover data the PowerScale can leverage SMB or NFS access in read only or read write mode anywhere in the file system tree that was created by Golden Copy.
Summary
This solution protects provides a Cyber Vault on S3 storage that is capable of sharing data in a read-only state