Administration Guides
Multi-domain Detection with Zero Trust API
Home
- Overview
- White paper
- Architecture
- Supported 3rd party Devices
- Requirements
- Features
- Best Practice
- Configuration
- Kemp Flowmon Example
Overview
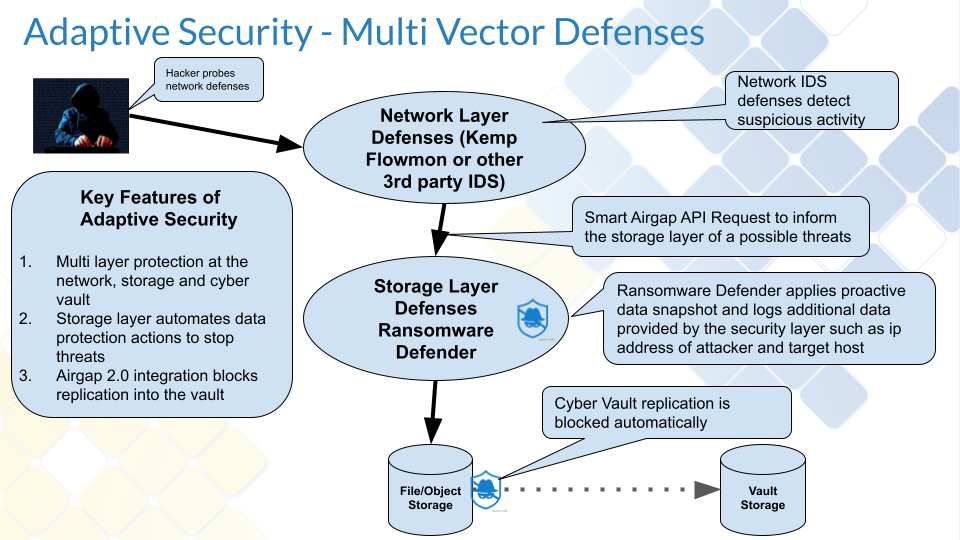
This solution enables a multi-vector detection solution to integrate network level detection (IDS, IPS) with storage level protection available with Ransomware Defender. This provides an early warning and data protection automated snapshot when IDS or IPS detect network attacks against critical application servers that store data on Powerscale clusters.
White paper
Read the white paper on this solution.
Architecture
The snapshot requests will generate a job in the Jobs icon and in a future release an active event will be displayed indicating external detection was raised and will indicate the external device name, detection type, ip of the device under attack.
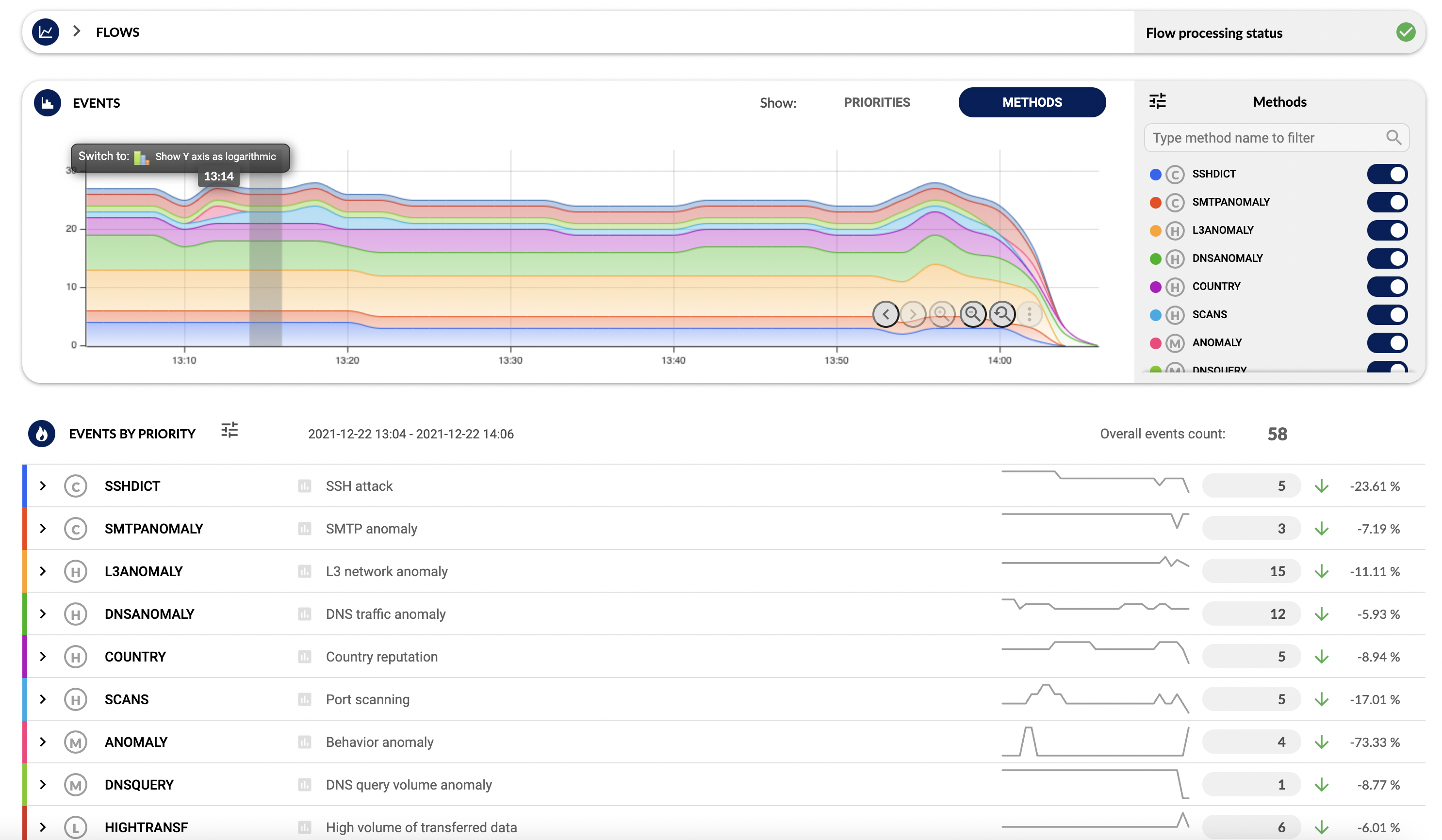
Supported 3rd party Devices
Requirements
- Smart Airgap Feature License
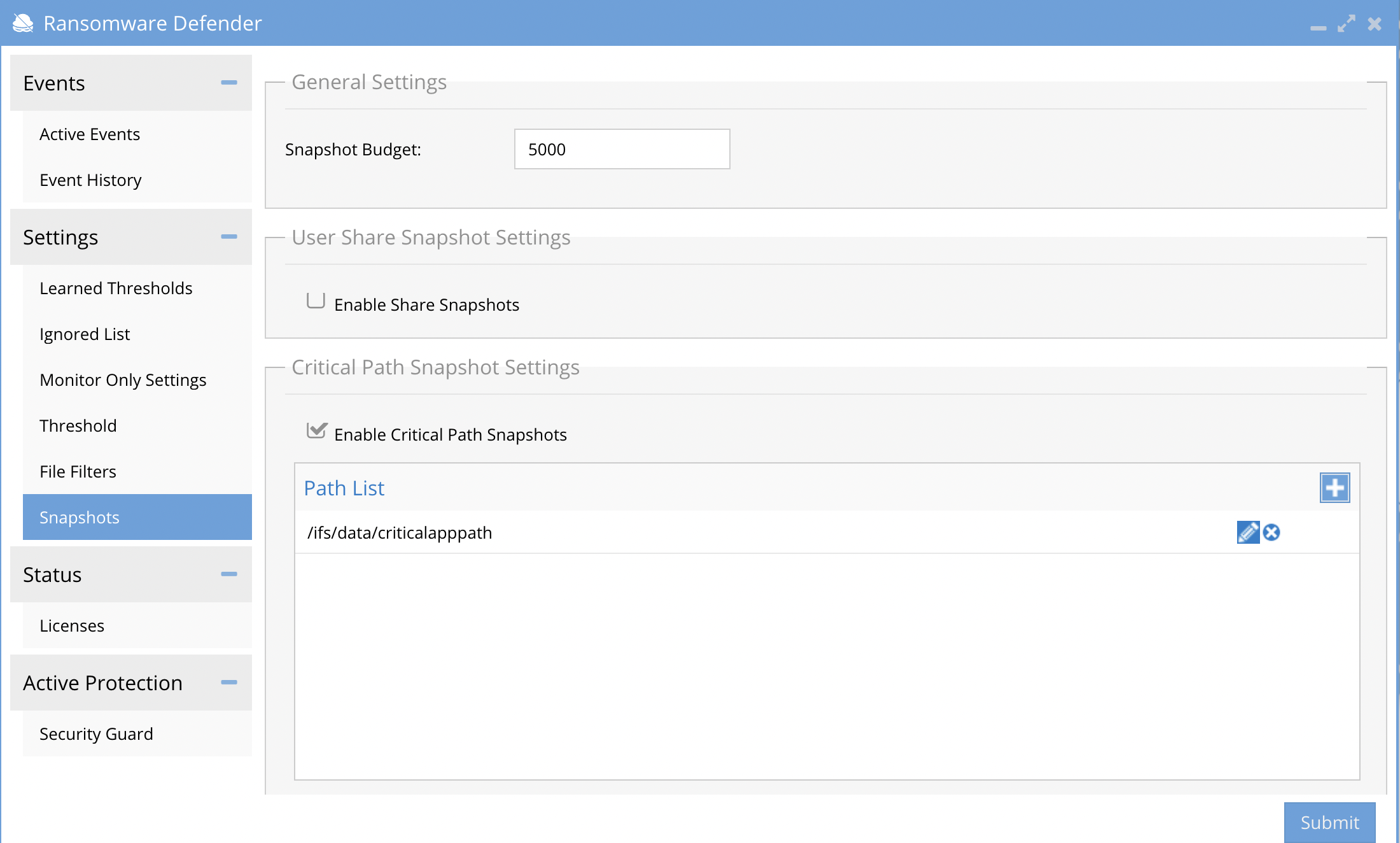
- Critical path feature in Ransomware Defender is documented here. It is configured to target paths on the cluster that should get a snapshot when either a) a detection occurs or b) smart airgap API request from an external system.
Features
- Snapshot request from network security devices
- User lockout request require input of a SID or user name
- Information that can be passed to Ransomware Defender include source detection device name, IP address of the device under attack and the type of attack. This information will be visible in the Ransomware Defender GUI (future release)
Best Practice
- Disable SMB share mode to reduce where snapshots are created.
- Enable critical path mode and target snapshots for critical applications. example PACS data or other business critical application data
- Use default 1 hour snapshot requests and default of 4 hour expiry. Increase the snapshot expiry to ensure your SOC has time to respond to issues and still has a valid snapshot protecting data.
Configuration
- NOTE: Defaults allow one snapshot request per hour and a 4 hour expiry on snapshots. These values can be changed. This prevents too many snapshots being created with false positives coming from the network device.
- Apply the Smart Airgap API following license key apply procedures to activate the external API for 3rd party integration.
- Make sure the critical path feature is enabled and that SMB share snapshots is disabled.
- Login to the eyeglass vm.
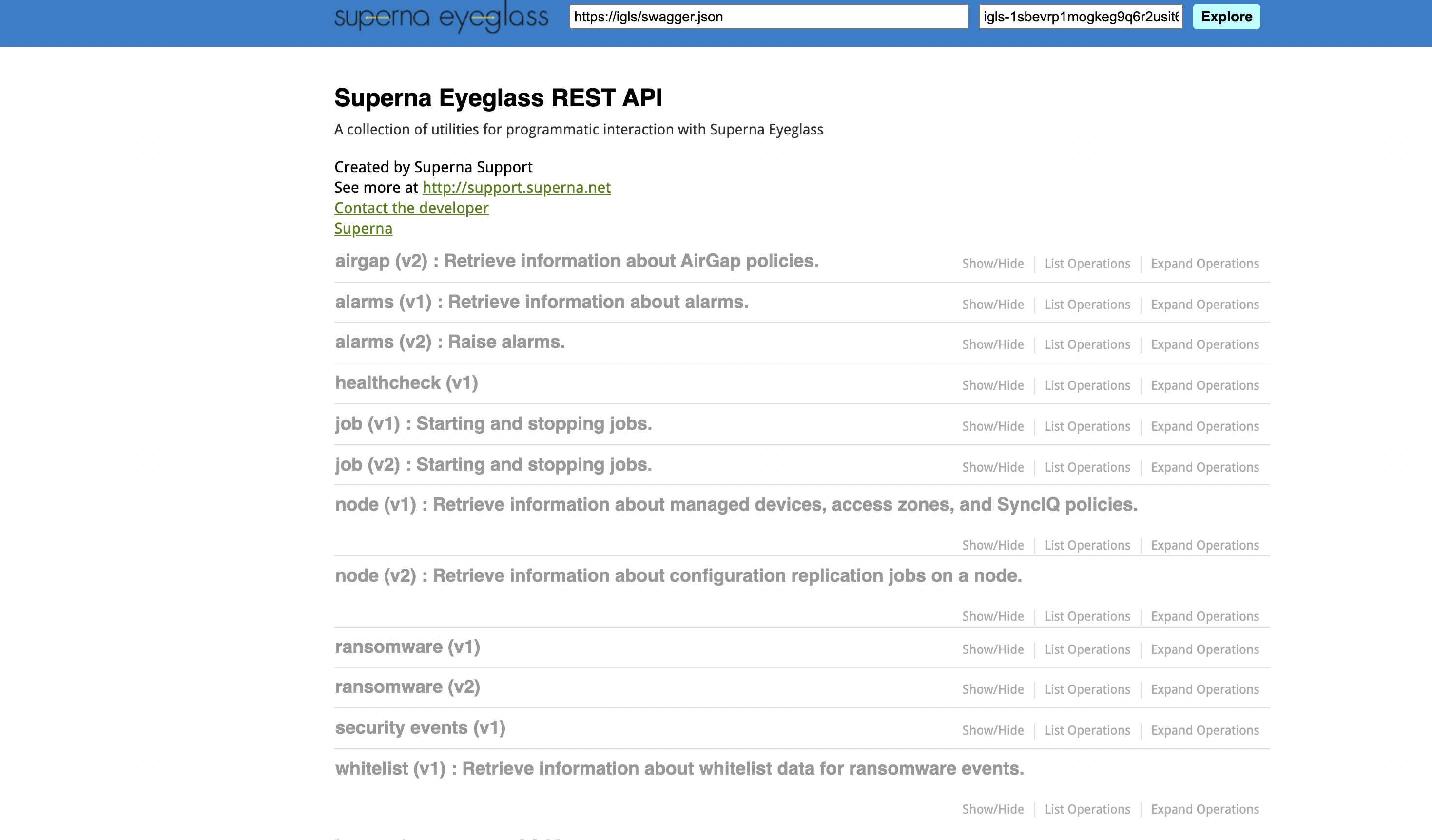
- Using the API explorer to build the curl command with an authentication token to be used to integrate with the IDS or IPS system that will used to integrate with Ransomware Defender.
- Open Eyeglass main menu and select Eyeglass REST API Menu item, Generate a new api token and provide a name example smartairgap. Copy the api token and open the the API Explorer button.
- Use the explorer interface to select the Ransomware Defender api section and select the critical path route. Click Generate to produce a curl command that can be used to request that critical paths get a snapshot applied.
- Example curl command that is integrated into network security devices
- curl -k -X POST --header 'Content-Type: application/json' --header 'Accept: application/json' --header 'api_key: igls-12js1pbq52b4dgj5n8erffe15h6esk7lj8onkuf6sfn741221b5e' 'https://x.x.x.x/sera/v2/ransomware/criticalpaths' -d "{}"
- Summary:
- Integration of this curl command can be setup as a trigger response. Recommended for critical detections in the security device to avoid too many snapshot requests.
- Integration into any device is possible include email gateways, endpoint protection consoles and SIEM solutions.
Kemp Flowmon Example
- A custom script trigger was attached to event severities
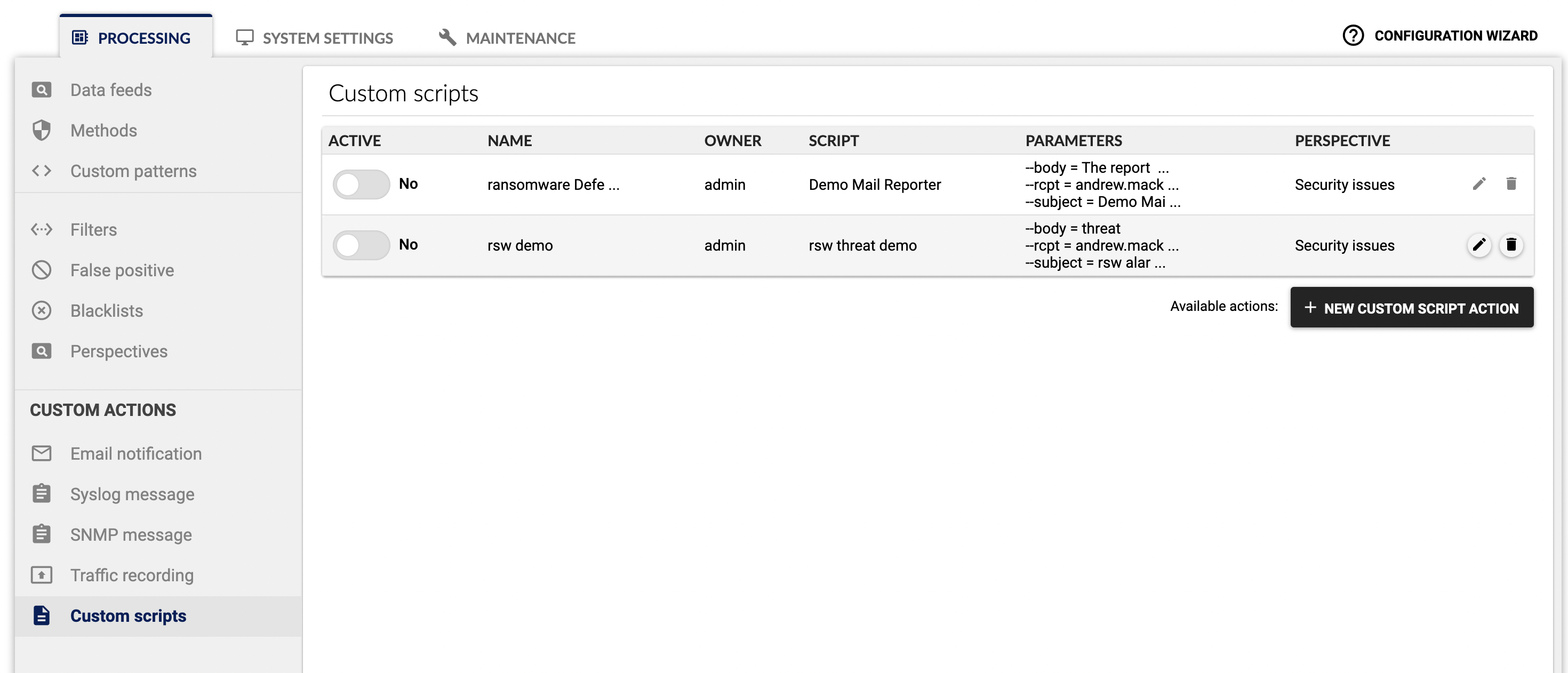
- This detection fired the snapshot request after an ssh brute force attack to a critical application server that was configured for monitoring with Flowmon.