Immutable Zero Trust Backup with Dell ECS Object Lock
Overview
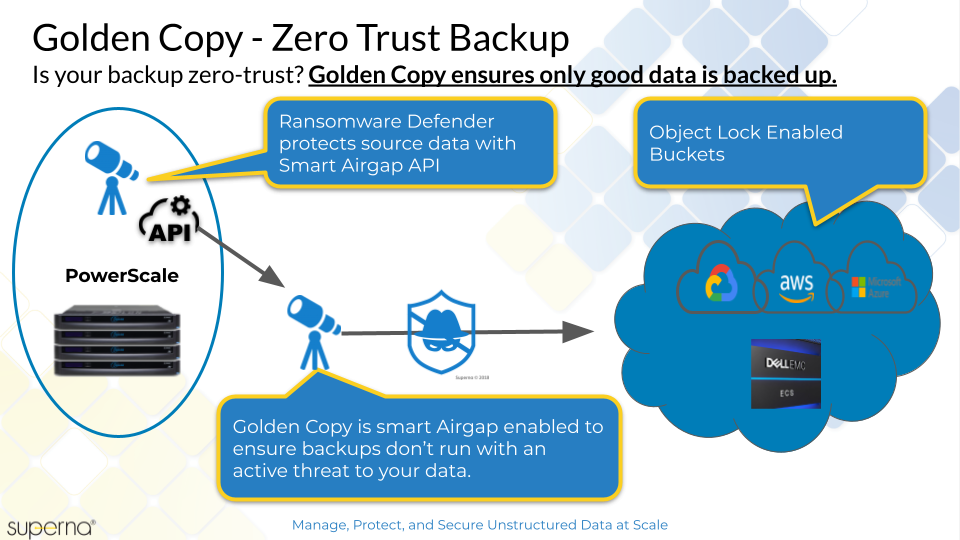
Customers looking for next generation backup solution with immutability option and file versions and long term delete handling can now deploy Dell ECS 3.6.2 or later with Object lock feature. This solution guide explains how to configure Object Lock with ECS and Golden Copy + Ransomware Defender Smart airgap API to enable a zero trust backup solution.
Object lock applied to a version enabled bucket with lock retention set to 6 months or 1 year depending on compliance requirements. Golden copy defaults to incremental mode using delete objects from S3 if deleted on the file system. This will leave locked deleted objects that will remain in the S3 bucket. This default behavior can be disabled to leave deleted files on the files system as S3 objects. This would restore deleted data if a recall job is used. This is not recommended in most cases.
Key Challenge Solved
- Backup data that cannot be deleted even by the root user on the ECS
- Zero trust backup with integration with Ransomware Defender threat detection on production data blocks backup jobs (full or incremental) if any active threats exist on the production data set.
Prerequisites
- Dell ECS 3.6.2 or later
- S3 bucket with object lock enabled in Compliance mode
- Golden Copy 1.1.6 with the Advanced license key
- Ransomware Defender 2.5.8 or later
Topology Diagram
Configuration Steps
- Enable Zero trust api integration with Ransomware defender
- Login to Golden copy node 1
- nano /opt/superna/eca/eca-env-common.conf
- paste this line to the file and change the yellow highlighted x.x.x.x with the ip address of Eyeglass VM, and the API token created to authenticate. API web token can be created from the main menu Eyeglass API menu UI.
- export EYEGLASS_LOCATION=x.x.x.x
- export EYEGLASS_API_TOKEN=yyyyyyyy
- control + x to save and exit
Configure ECS bucket
- Download the ECS perl tools and configure them as needed with credentials to authenticate to the ECS as a user with permissions to modify the target bucket. IAM user is required to modify object lock settings. Adapt these examples
- Create the bucket with object lock, replace x.x.x.x with ip address of your ECS, replace gcbucket with the S3 bucket name to be used with Golden Copy
- /s3curl.pl --id=ecsid --createBucket -- https://x.x.x.x:9021/gcbucket -H "x-amz-bucket-object-lock-enabled: true"
- Set object lock settings on the bucket
- This example uses 180 day lock period
- ./s3curl.pl --id=ecsid -- https://x.x.x.x:9021/gcbucket?object-lock -X PUT -d "<ObjectLockConfiguration><ObjectLockEnabled>Enabled</ObjectLockEnabled><Rule><DefaultRetention><Mode>COMPLIANCE</Mode><Days>180</Days></DefaultRetention></Rule></ObjectLockConfiguration>"
- ./s3curl.pl --id=ecsid -- https://x.x.x.x:9021/gcbucket?object-lock
- output example: <?xml version="1.0" encoding="UTF-8" standalone="yes"?><ObjectLockConfiguration xmlns="http://s3.amazonaws.com/doc/2006-03-01/"><ObjectLockEnabled>Enabled</ObjectLockEnabled><Rule><DefaultRetention><Mode>COMPLIANCE</Mode><Days>180</Days></DefaultRetention></Rule></ObjectLockConfiguration>
- Copy Data to the bucket with Golden copy
- See quick start on Golden Copy with ECS here.
- How to disable file delete syncs see this guide here.
- How to verify an object is locked and the expiry date
- ./s3curl.pl --id=ecsid -- https://x.x.x.x:9021/gcbucket/<clustername>/ifs/GCTest/folder7/bfile2.txt?retention
- example output: <?xml version="1.0" encoding="UTF-8" standalone="yes"?><Retention xmlns="http://s3.amazonaws.com/doc/2006-03-01/"><Mode>COMPLIANCE</Mode><RetainUntilDate>2022-01-25T16:29:39.407Z</RetainUntilDate></Retention>
Summary
This solution protects backup data with compliance mode object lock and versioning on the bucket ensuring backup data cannot be deleted once written. Full version enabled protection each time incremental mode in Golden Copy runs. Zero trust configuration blocks jobs automatically and resumes jobs once the threat has been addressed. Version based recall of locked data with Golden Copy advanced license key.