How to respond to Security Events for Warning, Major or Critical Events
- Read Me First
- Security Event Triage Process to Collect Key Information for Your Security Incident Response Process
Read Me First
On detection of a possible ransomware event we can provide you with a relative severity of the detection and then provide with you information to make a decision such as files affected, user associated with event and client IP. This information should be used in conjunction with your security incident response process and security tools such as virus scanning and inspecting users computer to reach a conclusion whether or not it is a ransomware event. A detection event should be evaluated based on the signal strength column and the severity column on an Event as additional information for you security response process.
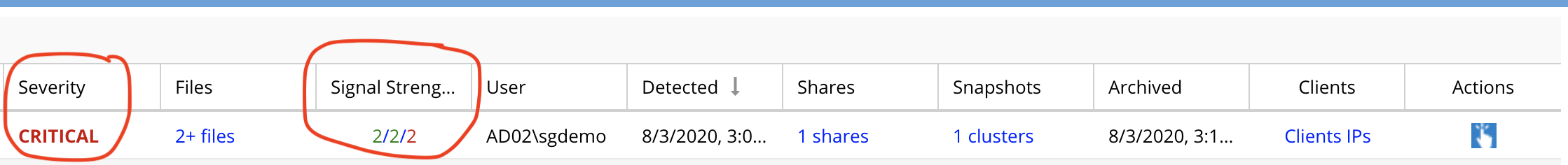
The information below should be used when following the process in this guide, get the signal strength and severity of the event and then review ranges below to determine the relative severity of the User Behavior. Your Ransomware Defender settings determine when a user will be locked out based on the signal strength value and settings for Severity. If you are in Monitor Mode, no lockout will occur and manual lockout is required from the actions Menu.
Quick Assessment
- Use Severity and signal strength values to assess the event
- Severity level is determined by the settings in your environment
- Warning - is considered low probability of infection
- Major - an increased probability of infection or a medium User Behavior
- Critical - is a strong Ransomware user behavior and an indication of a possible infection. A decision to lockout the user should be determined along with reviewing the files affected
- Signal Strength - For any Severity level a higher signal strength count indicates the User Behavior is a continuous pattern. A continuous repeating detection pattern is consistent with Ransomware activity and should be used as an input to a response action based on the security incident response process.
Security Event Triage Process to Collect Key Information for Your Security Incident Response Process
When a security event has been detected, the steps to review and take actions should be followed exactly as listed below and then follow your internal security incicdent response process.
- Open Ransomware Defender Active Events tab.
- Review the files that tripped the detector and to download the CSV file associated to the event. Review these files.
- Each event shows the number of files associated with the active or archived security event. NOTE: The list of files shown here are the files that tripped the detector and were stored with the event. A limit of 100 files is stored in the Eyeglass database, that populates the browser tree. See screen shot below
-
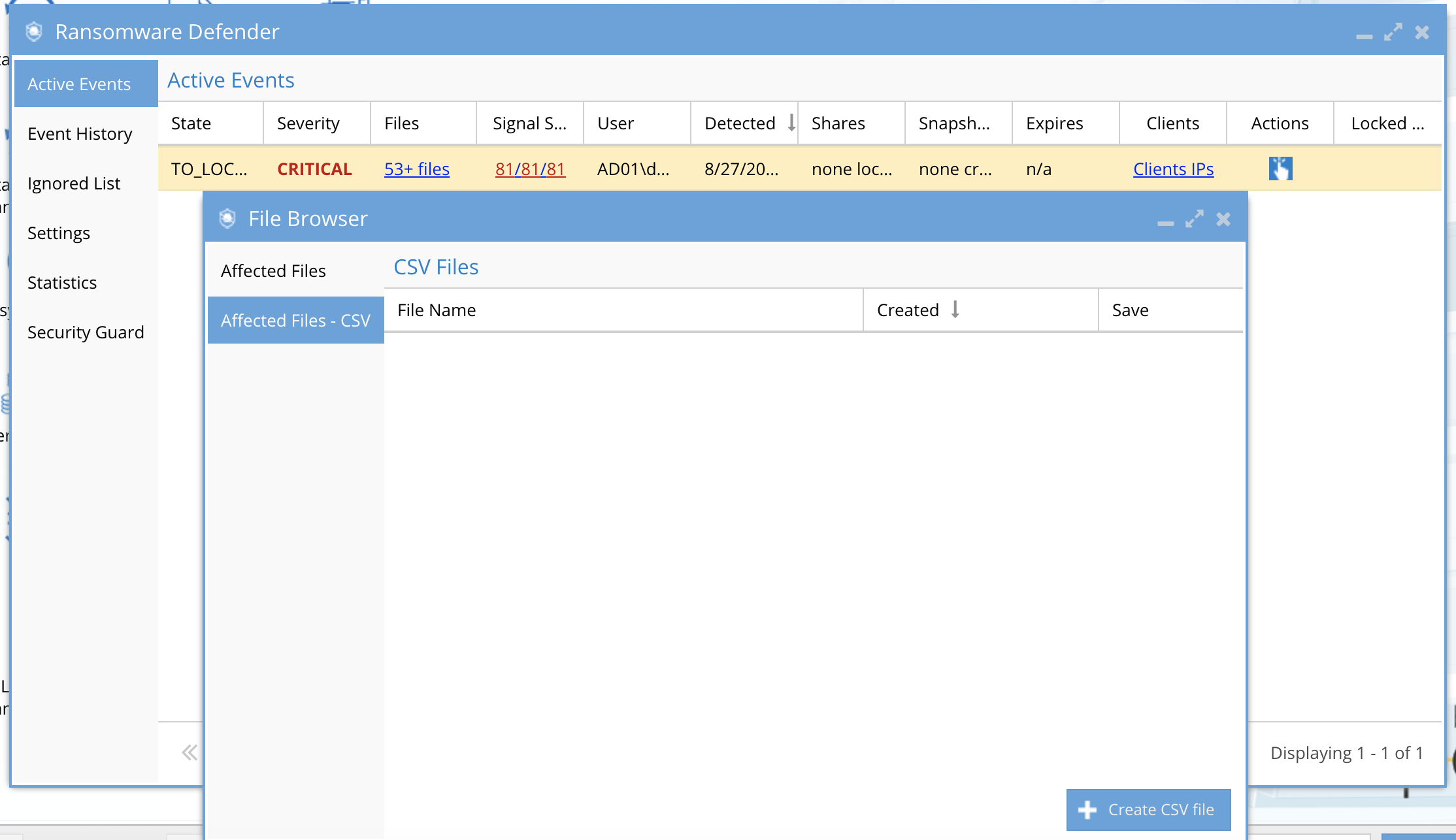
- The CSV download of affected files will list all sections for this user for all time, the date stamp in the file should be used to indicate when the detection occurred, the file name. NOTE: It is possible to have more files associated with the event than the CSV shows, if the event was active for more than 1 hour. The list of files in the CSV represents only files deemed to have tripped a detector, and NOT files accessed or saved in this time period that did NOT trip a detector.
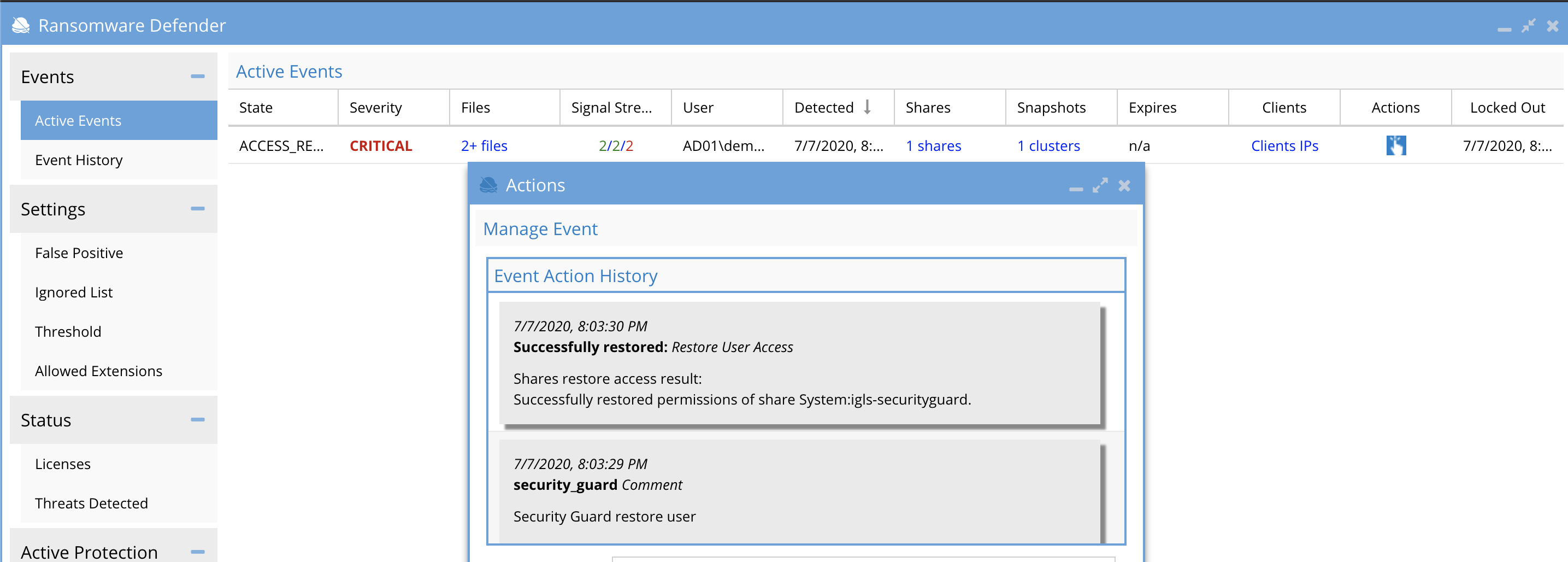
- Review the list the following elements of the active event to review what occurred from the lockout:
- Click on the "Shares" link to review the shares with a lockout applied.
- Click on the "Snapshots" link to review the snapshots that were applied to shares.
- Click on the "Clients IP's" link to review the source IP of the subnet of the infected computer.
- Click the "Actions" menu to review the time stamps of each action applied to this event including share lockout, snapshots. The Action menu also provides a menu of actions that will be used based on the Warning, Major and Critical event severity, to make a decision on next steps.
- Sample event screenshot
- Review the severity (Warning, Major and Critical) response steps in the topics below. To evaluate which files tripped the security detectors use the steps in this section to understand how the files download and browse window assists.