How to Configure Monitor Mode and Ignored Lists
- Monitor Mode List Overview
- How to Configure Monitor Mode List
- How to Enable Monitor Mode for an ECS Cluster
- Ignored Whitelists Overview
- How to convert whitelists to monitor mode lists
- Ignore List Configuration Procedures for Whitelisting path, user or source ip address
- Partial Path Matching Whitelists and Monitor mode lists and Wildcard Path Match Lists
- ECS Object Pattern Matching for bucket and path
- How to apply a partial path whitelist for roaming profiles
Monitor Mode List Overview
This option requires 2.5.7 or later release. This provides new option that is preferred over a whitelist that will ignore all detections for user, path or IP. This option allows a monitor mode to be applied to a user, path or source IP and has the same rules to add entries as whitelisting.
Protection offered by this option allows applications, service accounts to be monitored for detections with alerting and snapshots but no lockout will occur. This is preferable to ignore detections for applications or service accounts.
See how to convert ignore list to monitor mode list below.
How to Configure Monitor Mode List
- Open Ransomware Defender window.Select Settings --> Monitor Only Settings
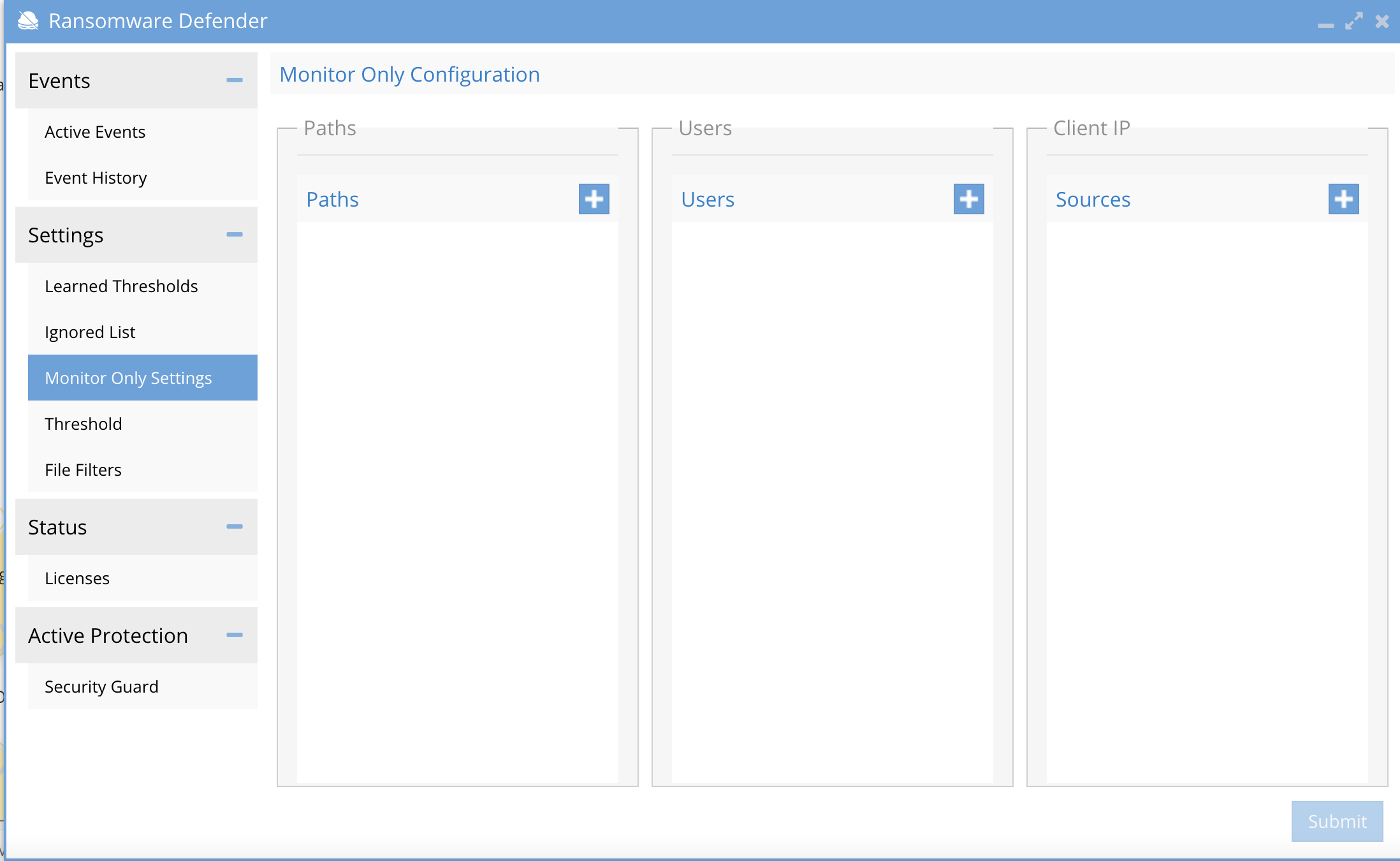
- Use the + to add a path, AD service account or source IP for servers and click submit.
- Select Isilon or ECS and fill in the information
-
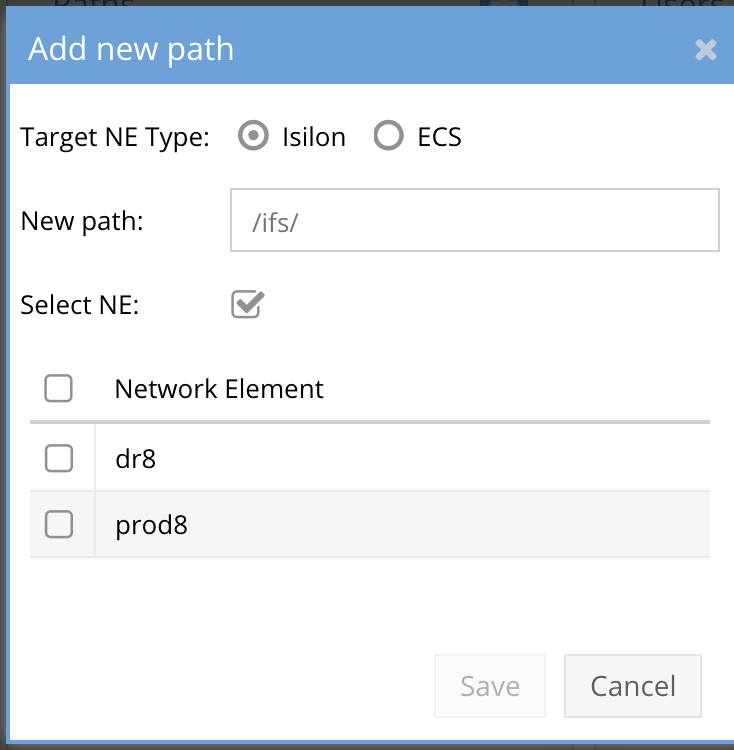
-
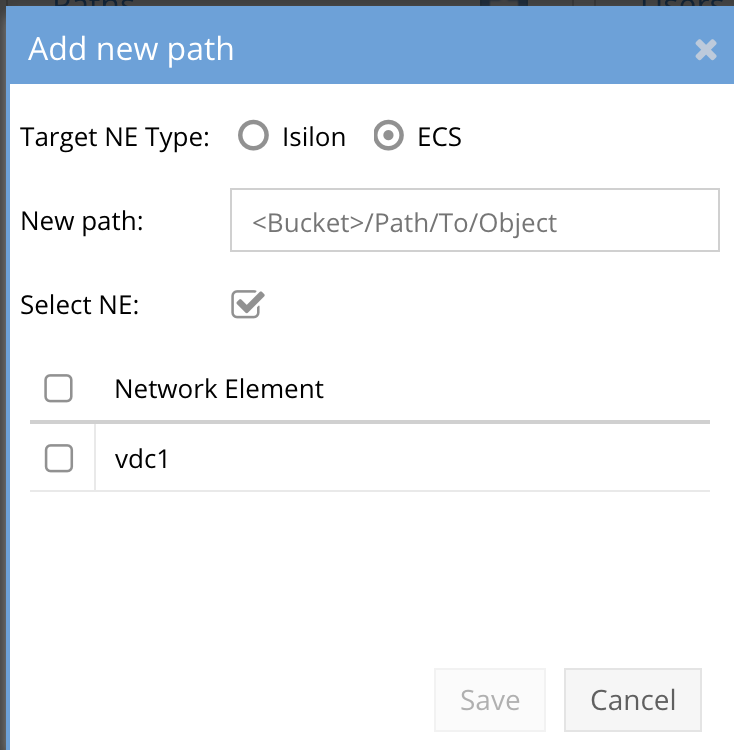
- For ECS enter bucket name and path to object example bucket1/path1/path2/** to match all objects under path2.
- The same rules defined for syntax of Whitelists is the same for Monitor mode lists. See pattern matching examples below.
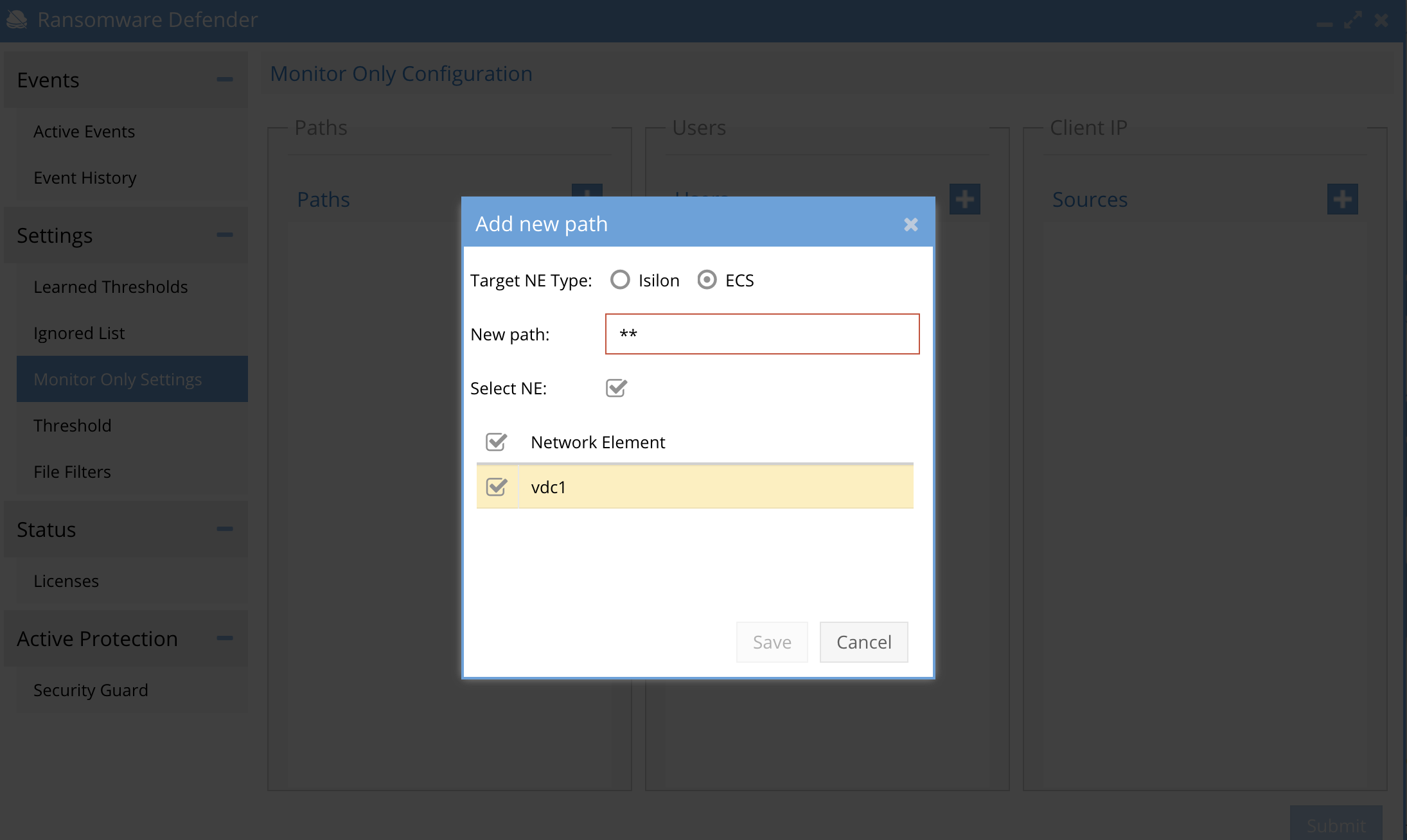
How to Enable Monitor Mode for an ECS Cluster
- The ECS monitor mode option is set using a wild card match for all buckets all objects. Open the monitor settings tab. Click to add a path entry and configure as per the screenshot.
Ignored Whitelists Overview
Ransomware Defender allows the administrator to specify paths, users, and client or server IP address to exclude from Ransomware processing. No detections will be processed once a whitelist is applied based on the matching criteria.
New in 2.5.7 is Monitor only option for Users, Paths, our source IP's.
Best Practise:
This option should always be used before whitelisting since monitor only mode will provide data protection with snapshots and alerting without a lockout.
How to convert whitelists to monitor mode lists
- This is now the recommended option for all customers upgrading to 2.5.7 to convert the whitelist to the monitor mode list. This offers increased data protection without lockout. Whitelist should be used for less critical data or data that can easily be recreated.
- Two methods exist to convert the cli command here.
- GUI option available on the ignore list GUI.
- See the GUI option at the bottom of the screen.
- You will need to confirm the conversion process that will remove all ignore list settings and move them to the monitor mode list.
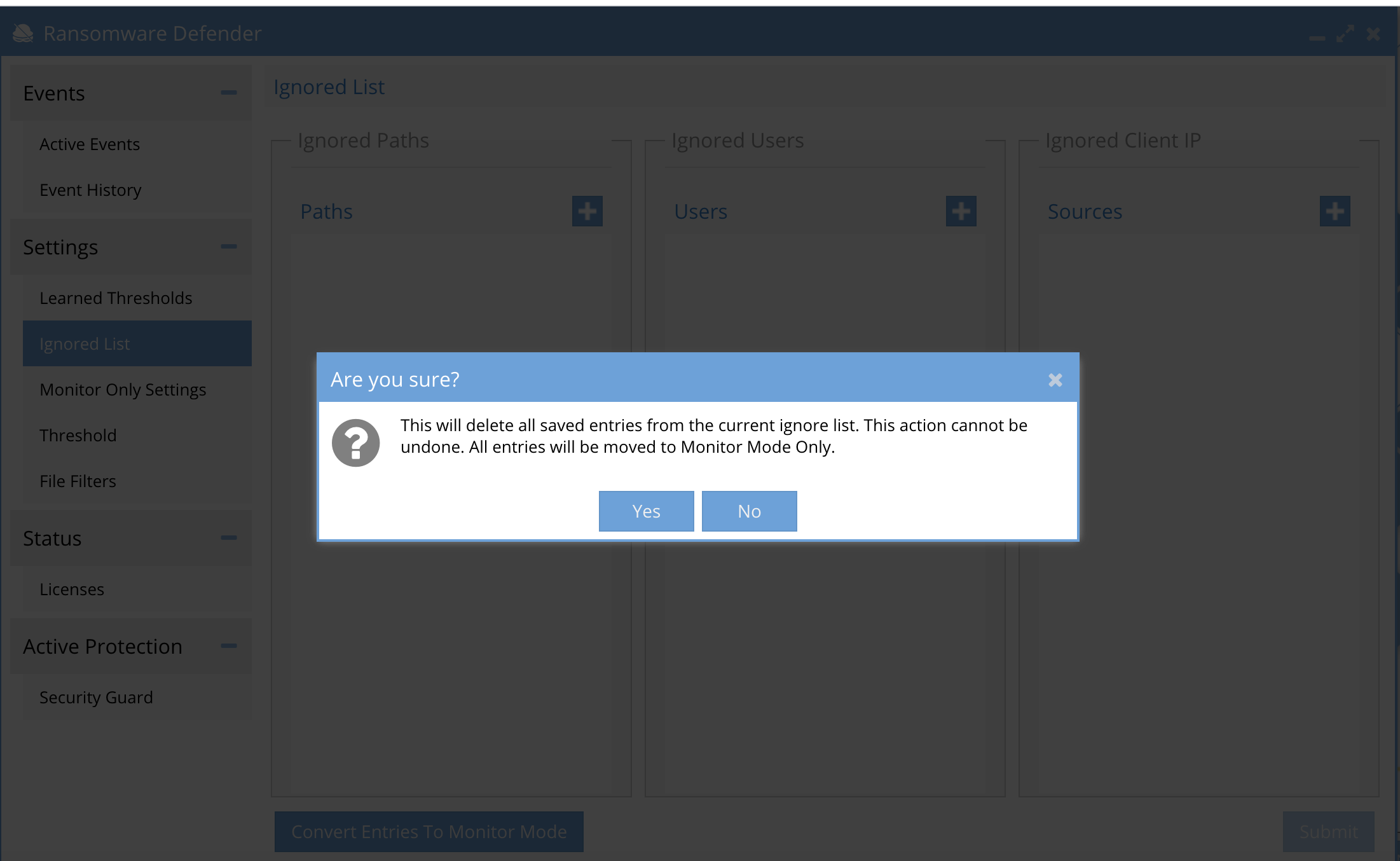
Ignore List Configuration Procedures for Whitelisting path, user or source ip address
Follow the steps below to add ignore list of paths, uses, or server/client source IP. This will skip processing all events based on the settings applied in this section. NOTE: Changes take effect immediately after saved . Consult support for recommended settings. NOTE: Use monitor mode lists first before using a whitelist that ignores detections.
- Open Ransomware Defender window.
- Select Settings --> Ignored List tab
- Enter a path, AD user domain\userid, or server or client IP address and save.
- NOTE: all 3 options can be used
- New Paths (full path is required example /ifs/data/xxx)
- Active Directory Users (domain\userid or user@domainname)
- ECS users should be enter by name
- Client IP is the IP of a client or server.
- NOTE: each ignore column is an OR, meaning if ANY of the listed ignore values is found in an audit message it will be dropped before processing. The first matched ignore list will drop the audit event.
Partial Path Matching Whitelists and Monitor mode lists and Wildcard Path Match Lists
Partial path matches for different uses cases, where a partial match is required. This option works for paths or objects paths with ECS objects.
Example, use case is roaming profiles stored on an SMB share. The profile is saved each time the user logs on and off the desktop session. Windows writes data to the roaming profile in a similar IO pattern to Ransomware using a read and write with a hashed file name. This can trip a false positive lockout.
How path and file matching works with whitelists
- The * character is in place of a directory in a path. Example: /ifs/data/home/*/.
- If using * at the end of a path, it becomes a file name wild card. Example: /ifs/data/home/usera/* is any file in the usera folder.
- To wild card multiple subdirectories below "usera" folder this syntax is required. Example: /ifs/data/usera/** This will whitelist all subfolder below "usera" folder.
The portion of the profile where these files are stored for roaming profiles is below the AppData portion of the path.
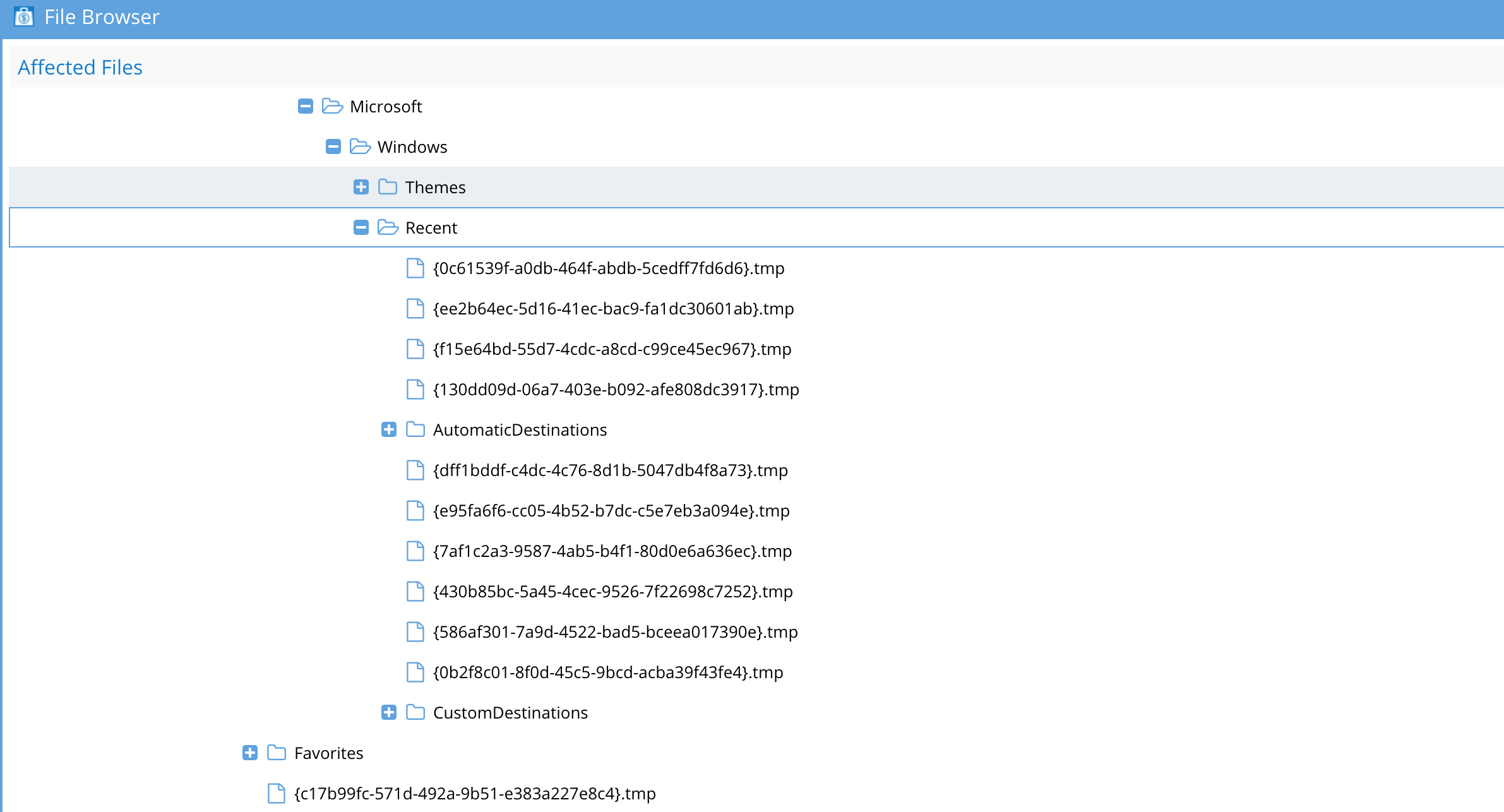
Example of a partial path from a roaming profile: The .tmp file in this example has a file name structure similar to Ransomware variants, and can trip a threat detector and lockout the user.
AppData\Roaming\Microsoft\Windows\Start Menu\Programs\System Tools\{7347b4c0-96d8-45e3-abe2-d7ffde9840a4}.tmp
Example false positive from a roaming profile detection on a SMB share
ECS Object Pattern Matching for bucket and path
- Match the whole ECS cluster using the pattern:
- **
- Match a specific path in any bucket using the pattern:
- */path/to/object
- Match all direct children of a path using the pattern:
- <bucket>/path/*
- Match all descendants of a path using the pattern:
- <bucket>/path/**
- Match exact object:
- <bucket>/path/to/object
How to apply a partial path whitelist for roaming profiles
- Open Ransomware Defender Icon, click on Ignored List tab under settings.
- A Path-based entry will be used. Click the plus sign and select a cluster from the list.
- Enter a path using the information below, and click submit to save once done.
- Example: full path to a share storing roaming profiles for many users.
- If your unc path to store profiles was this: \\ad1.test\FOdemo\Corpdata\%USERNAME%, and this was an PowerScale path of /ifs/data/corpdata/:
- Enter a whitelist path of /ifs/data/corpdata/*/AppData/**
- This will replace the first * with the user name and the second * with any path in the roaming profile, and ignore roaming profile updates to these paths for all users storing roaming profiles on corpdata home directory path