Trend Vision One XDR Integration - Cyber storage host Isolation
- Overview
- Support Statement
- Limitations
- Solution Overview
- Advanced Zero Trust Capabilities
- What is Trend Vision One XDR?
- Integration Architecture
- Solution Configuration in Trend Vision One XDR and Defender Zero Trust
- Prerequisites
- Configuration in Trend Vision One
- Configuration Steps on Eyeglass Virtual Machine
- High Level steps
- Configuration Step by Step
- Configure the Service start and python integration files
- Configure the python packages and customize the tvoxdr integration python code
- Configure Defender Zero Trust Webhooks
- How to test the Integration with Trend Vision One XDR
- Trend Vision One SecOps administrators Integration Experience
Overview
Customers using Trend Vision One XDR endpoint protection solution can now leverage a native integration that initiates a host isolation API integration of a critical Ransomware detection is detected by Security Editions zero trust alert API. Customers can augment the capabilities of Trend Vision One XDR with threat intelligence and Cyber Storage capabilities of Superna Security Edition.
Support Statement
-
NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
Limitations
- Superna Security Edition and Zero Trust integration only supports client machines registered with the XDR on boarding process that contain the same ip address information used when connecting to support storage platforms. The matching of the threat source ip address must match an on boarded and licensed Defender XDR endpoint protection host in the XDR portal.
Solution Overview
Superna Defender Zero Trust API receive webhook alerts, parses the key information from the alert and initiates API calls to Vision One to match the infected host to a host registered with Endpoint protection portal. Once the host mapping has been validated an automated isolation request is initiated.
Advanced Zero Trust Capabilities
- Host Isolation - This optional feature allows an inbound Zero trust alert that contains user lockout status will also trigger a machine isolation to ensure this host can not continue to attack other systems within the IT infrastructure
- In order to enable this function locate the settings section in the python code provided below and change the global variable to true from false. The default is true for this integration.
- host_isolation = 'true'
- In order to enable this function locate the settings section in the python code provided below and change the global variable to true from false. The default is true for this integration.
What is Trend Vision One XDR?
Trend Vision One bridges risk management, XDR, and zero trust architectures to support business operations and objectives. Extend your protection, detection and response capabilities across endpoint, servers, workloads, email, network, cloud, and identity.
Integration Architecture
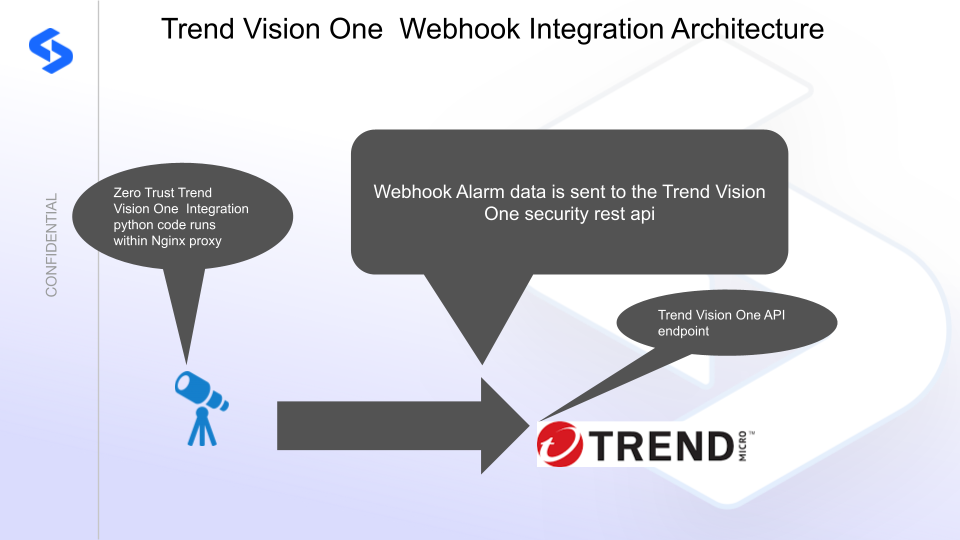
Solution Configuration in Trend Vision One XDR and Defender Zero Trust
Prerequisites
- Installed Ransomware Defender and or Easy Auditor or Defender for AWS
- Eyeglass OS appliance version 15.5
- cat /etc/os-release
- License key for the Zero Trust API
- Trend Vision One XDR
Configuration in Trend Vision One
- Create client API token
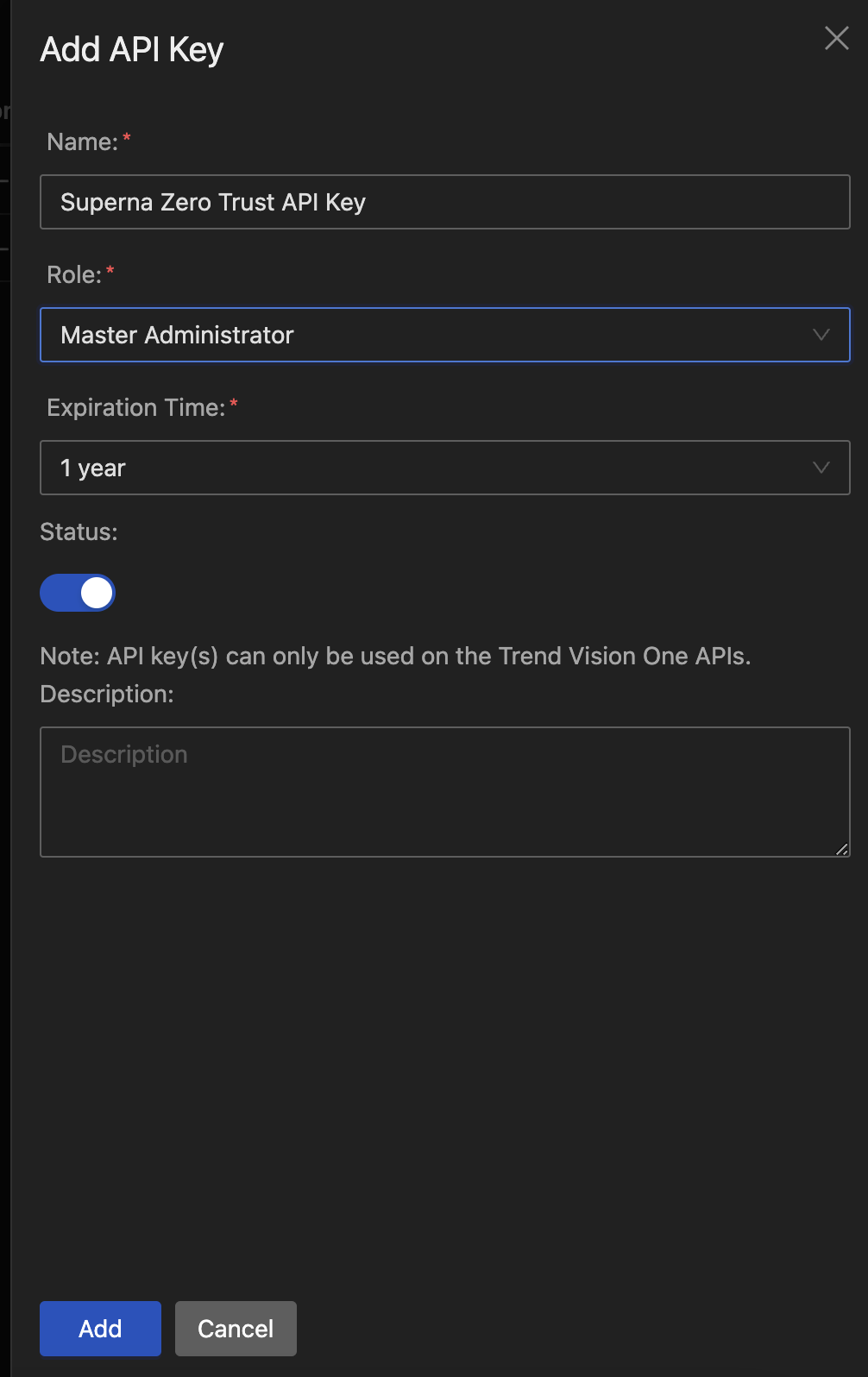
- Save the api key created to integrate with the python integration code in the steps below.
Configuration Steps on Eyeglass Virtual Machine
High Level steps
- Create python location to run the application on the Eyeglass vm
- Create python main application script
- Create linux systemd service and set to auto start
- Create Zero Trust configuration in Defender
- Update the main script to customize with Trend Vision One XDR python code
- Test the script is running as a service
- Create a test event in Defender to validate the alerts appear as indexed parsed events in Trend Vision One XDR
Configuration Step by Step
Configure the Service start and python integration files
Configure the python packages and customize the tvoxdr integration python code
- Customize the application code by downloading the python code from this link to download
- Open the python template file in a text editor. NOTE: make sure to only replace the values and do not delete any of the commas
- Locate this section in the file and replace the yellow sections with the api token saved above.
- Section named "Trend Vision One Integration section" in the downloaded python template code above.
- Replace the yellow with the api key and make sure to paste it between the single quotes
- token = 'xxxxxx'
- nano /opt/superna/cgi-bin/tvoxdr.py
- Open the file locally in Windows OS notepad and use control-A or select all the text in the python template
- Paste the clipboard into the ssh terminal session with the open nano editor file
- save the file
- press control+x
- Answer yes to save and exit the nano editor
- Start the service and verify it is running
- systemctl start tvoxdr
- systemctl status -l tvoxdr
- Verify the service is started successfully and returns "active and running".
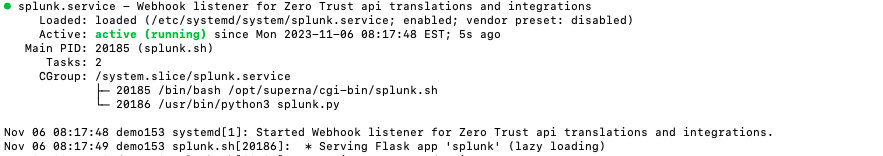
- If the service does not start do not proceed and double check the steps above are completed.
Configure Defender Zero Trust Webhooks
- The next step creates an Zero Trust Webhook URL.
- Configure Zero Trust endpoint in Ransomware Defender Zero Trust tab.
- Recommended Configuration: Only Critical and Major events and only the webhooks that set lockout or delayed lockout. Customers can customize based on specific requirements. The goal is to send findings versus a list of alarms that do not pinpoint a security incident.
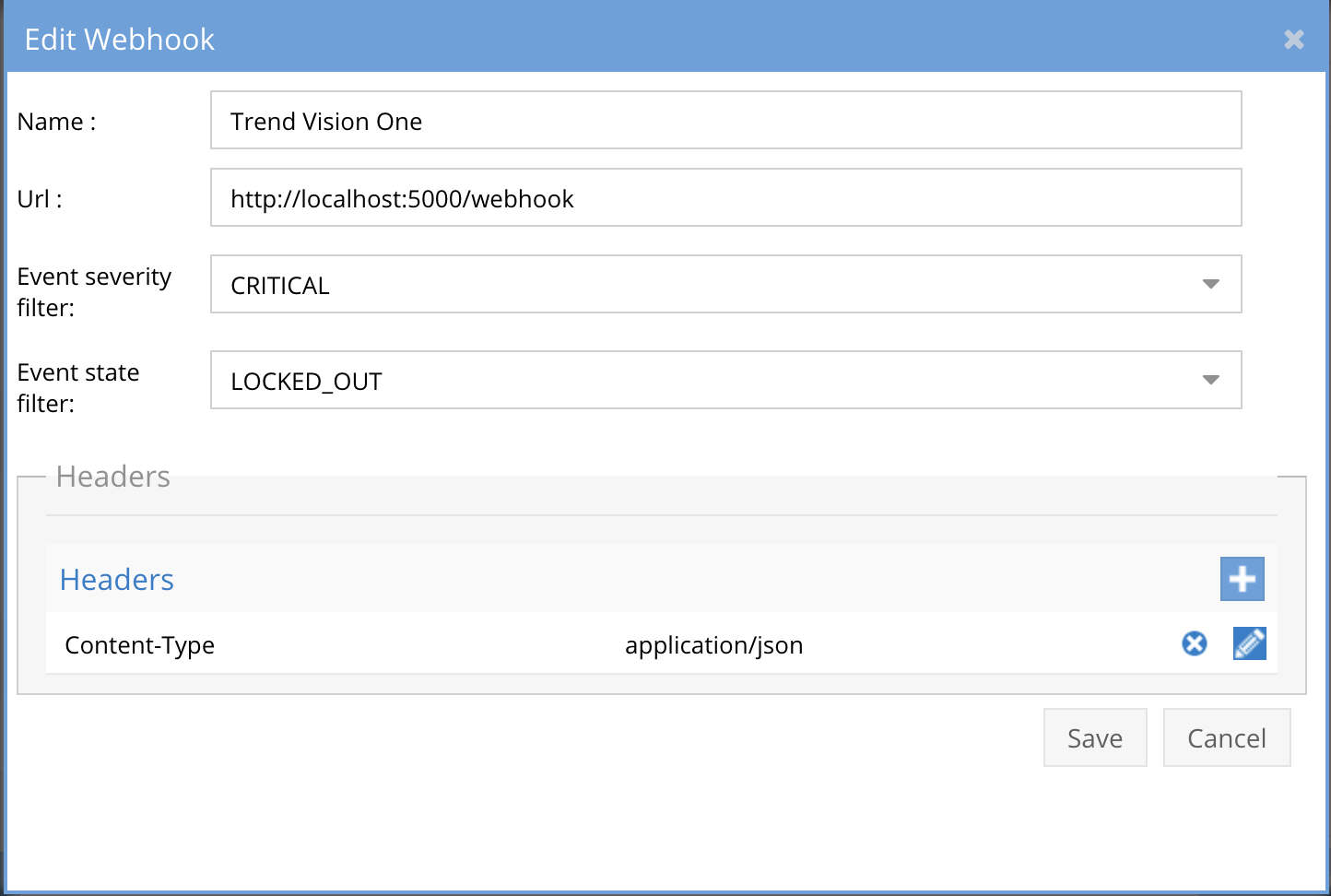
- The endpoint url above will use localhost and will send Webhooks to the application service listening on port 5000. URL to use in the configuration
- http://localhost:5000/webhook
- Add the Content-Type header with value of application/json as shown above to complete the webhook configuration.
- Click save to commit the configuration.
- Click save on the main Webhook configuration page
- Configure Zero Trust endpoint in Ransomware Defender Zero Trust tab.
- Test the configuration is working following the next section
How to test the Integration with Trend Vision One XDR
- To test the integration follow these steps
- Prerequisites In Trend Vision One and Eyeglass:
- install the Trend Vision One agent on a test machine. Record the ip address of this test machine.
- Get the ip address of the Eyeglass vm
- download this curl command template and open with a text editor and locate the ip address of eyeglass at the very end of text and replace the ip address with the IP address of your eyeglass vm.
- Also edit the client ip section of the curl command by searching the text clientIPs":["172.31.1.45"] and replace only the ip address with the IP of the test machine running the Trend Vision One agent.
- This will now simulate a zero trust alert on this host when the curl command sends the webhook payload to the integration python code to process.
- Copy all the text in the text editor
- ssh to the eyeglass vm as the admin user
- paste the entire cli command text to the ssh prompt to send sample data to the running Zero Trust application. This will send test data directly to the application to be processed and sent to Trend Vision One Integration service that is running on the Eyeglass VM.
- The output of a successfully processed webhook test will return this text in the ssh terminal
- done sending event to tvoxdr and check for http 200 and success count in response
- How to review the process logs from the web application
- sudo -s
- journalctl -f -u tvoxdr
- This allows you to view the logs generated by the application.
- To log to a file and review with nano showing only the most recent 250 lines.
- journalctl -f -n 250 -u tvoxdr > /tmp/ztwebhook.log
- nano /tmp/tvoxdr.log
- In the log below the response code from the Trend Vision One api call should show http 200 status code and successCount 1 to indicate the Finding was successfully created.
- You can also view tvoxdrd.log for specific error messages.
- Login to the Trend Vision One Main Dashboard to check the Response Management screen. This is where remote api requests will be recorded. See screenshot example below.
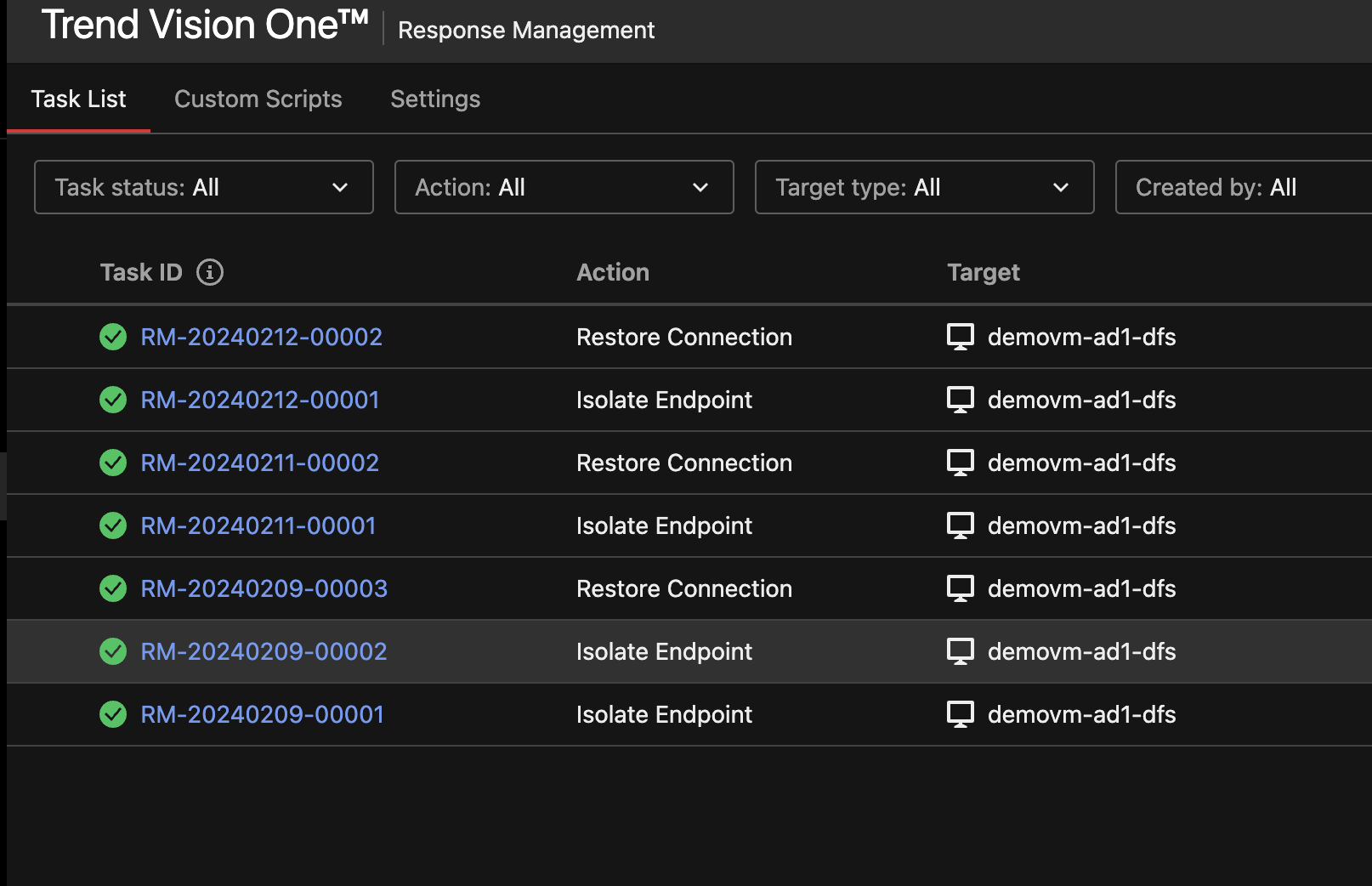
- The Isolate Endpoint is a request to isolate a host named demovm-ad1-dfs. Once the host is Isolated from the network, it can no longer connect externally until the restore communications options has been completed in the Response Management application.
- NOTE: email alerts on response actions should be monitored to know when an attack has occured. Zero trust emails or other integrations can be leveraged to be alerted when security incidents are detected at the storage layer.
- To Restore communications to an Isolated host use the the dots next to the task an select Restore connection.

- Done
Trend Vision One SecOps administrators Integration Experience
- Once the integration has been configured and is running. Critical lockouts in Security Edition will now trigger host Isolation API requests in Trend Vision One.
- The investigation steps and assigning to a Secops analyst to login to Security Edition to view details of the incident. No security API exists to create incidents in Vision One at this time.
- The recovery options for data can be completed within the Vision One console response management application. Application data recovery can be completed within Security edition with cyber Recover Manager workflow to restore data from snapshots with push button automation.
- The endpoint should remain isolated until an inspection and remediation plan for the workstation has been completed. Once remediation steps on the host have been completed the Response management application within Vision One can be used to restore communications to the workstaton.