Eyeglass Solutions Publication
Tenable Security Center - Integration
Home
- Overview
- Solution Brief
- Video Overview
- Integration Architecture
- Configuration
- Administration and Operations
- Reporting
- Scanning Data Attack Surface Hosts
Overview
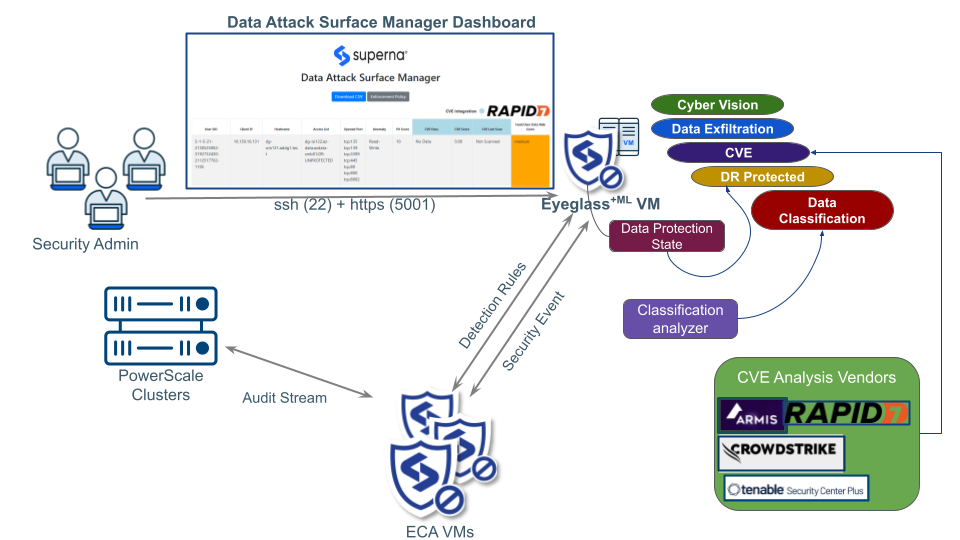
The Tenable integration offers static Assets sync Data Attack Surface tracking within Security Center. This allows reports on the Data Attack surface asset as using the asset as target for more frequent scanning schedule . Vulnerability scan results are fully integrated into the AI prediction model within Superna Data Attack Surface Manager
Solution Brief
Read the Solution brief with Tenable Security Center.
Video Overview
Integration Architecture
Configuration
- The integration requires API access to the InsightVM, once the integration is completed a new Superna Data Attack Surface site is configured to aggregate data risk score hosts discovered by Superna Data Attack Surface Manager.
- The configuration files require the following information.
TENABLE_SECURITY_CENTER_URL = 'PLACEHOLDER' # Replace with Tenable SC URL
TENABLE_ACCESS_KEY = 'PLACEHOLDER' # Replace with Tenable Access Key
TENABLE_SECRET_KEY = 'PLACEHOLDER' # Replace with Tenable Secret Key
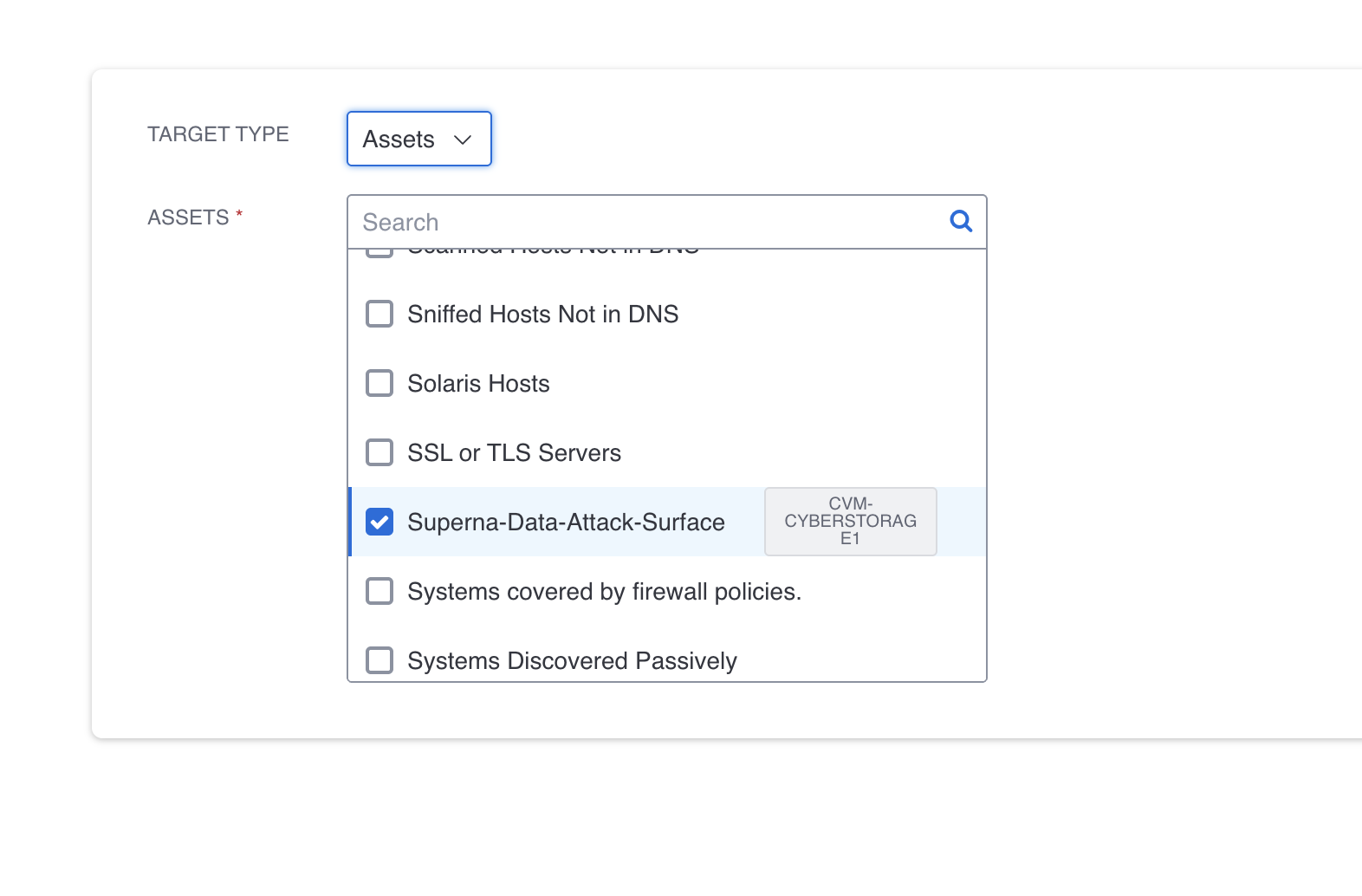
TENABLE_ASSET_NAME = 'Superna-Data-Attack-Surface' # Default Setting Asset Name Superna-Data-Attack-Surface
TENABLE_OFFSET = '5000' # Default Setting Offset 5000
- The scheduled scan data retrieval will be automated by DASM to build the AI model training data. The results of the AI model will be published into the asset list of static IP's within the assets. The schedule scan schedule on the asset will ensure that all Data Attack Surface hosts are scanned for vulnerabilities more frequently.
- Each new Data Risk Score host will be synced to the Asset named Superna-Data-Attack-Surface. I This allows filtering reports and dynamic assets with the custom tag.
Administration and Operations
Reporting
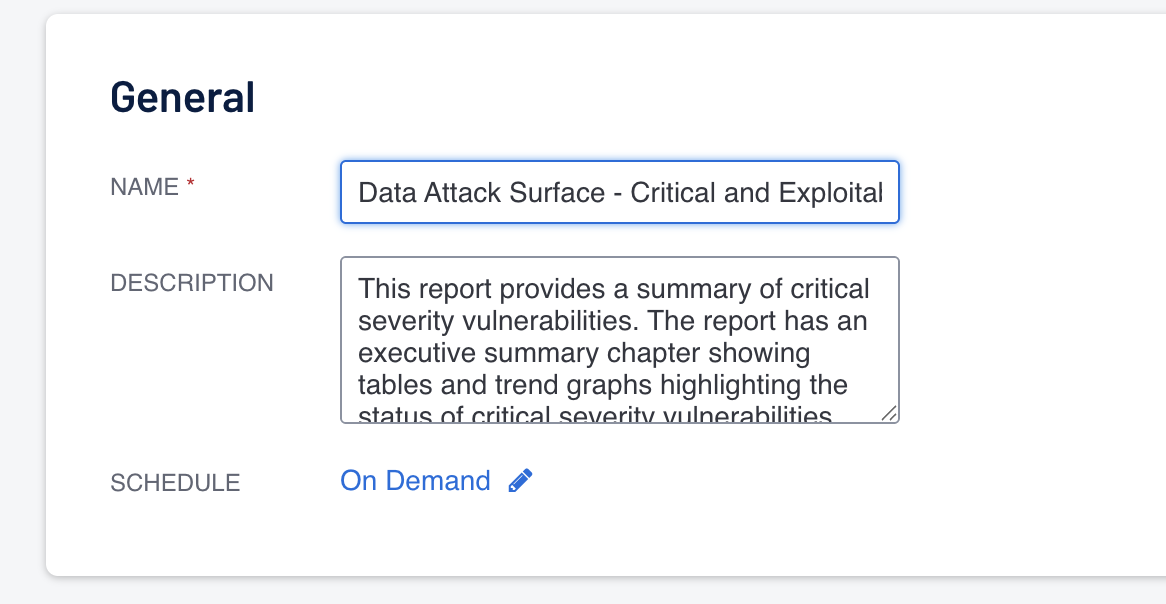
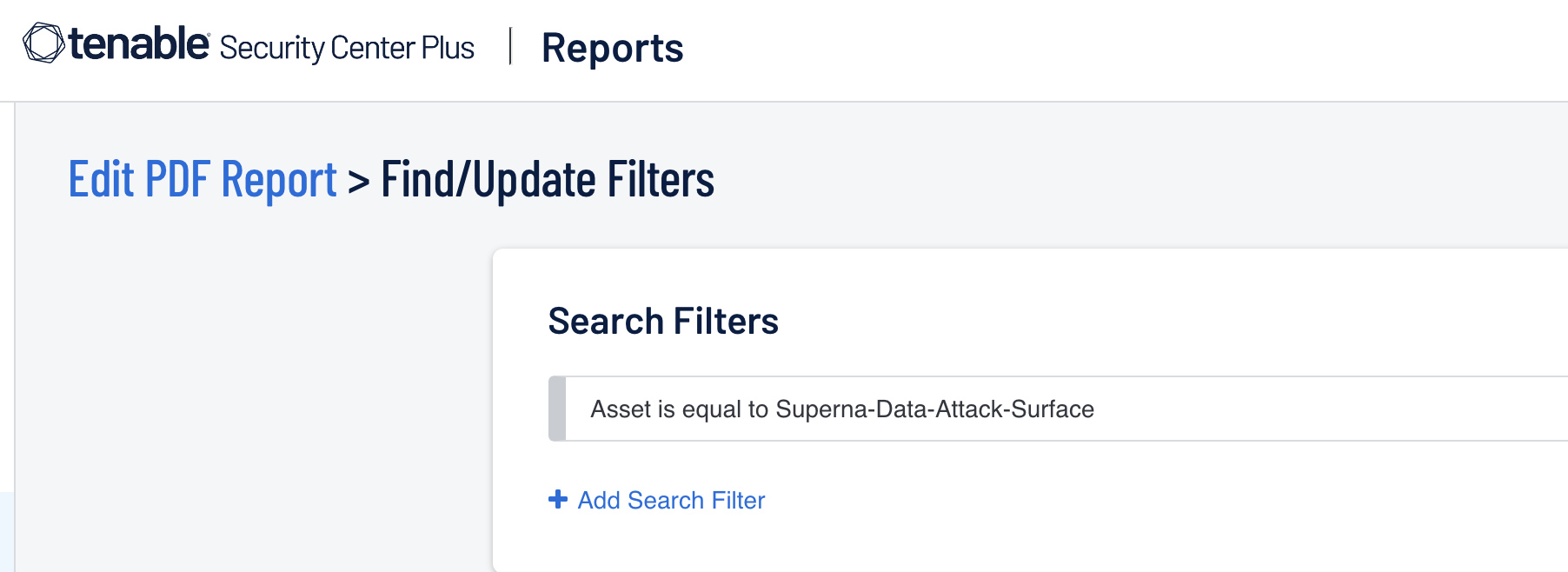
- Report Filtering by Superna created Asset
- Open the Report interface and create any new report definition.
- Set the filter equal to the Asset created by DASM
- Configure the name of the report
- Execute the report to see the scope of the vulnerabilities on critical data hosts.
- Sample report
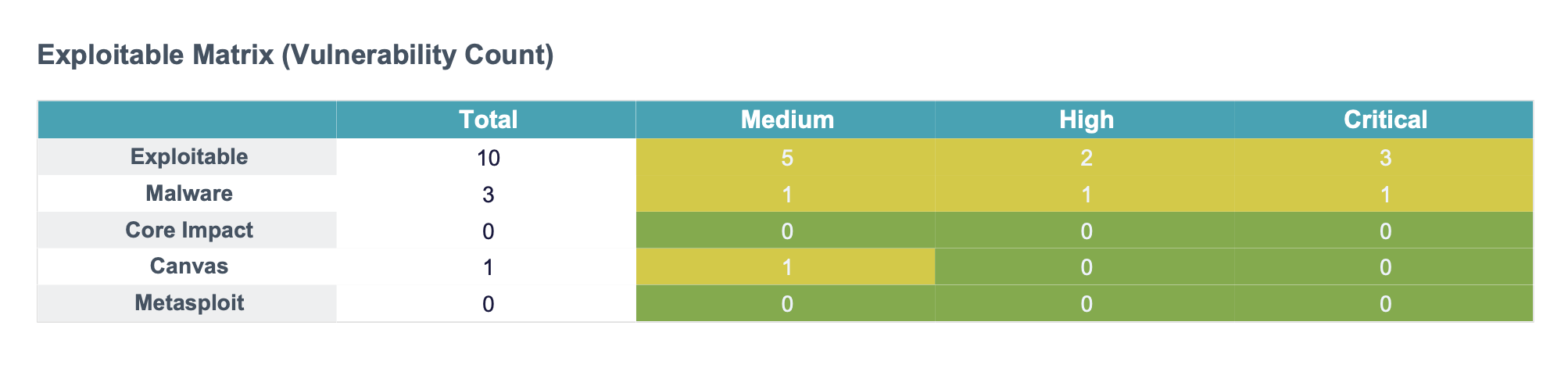
- Download pdf sample
- Repeat these steps to focus a report on the Data Attack Surface hosts
Scanning Data Attack Surface Hosts
- Open the Scans interface
- Create a new scan definition and set the name
-
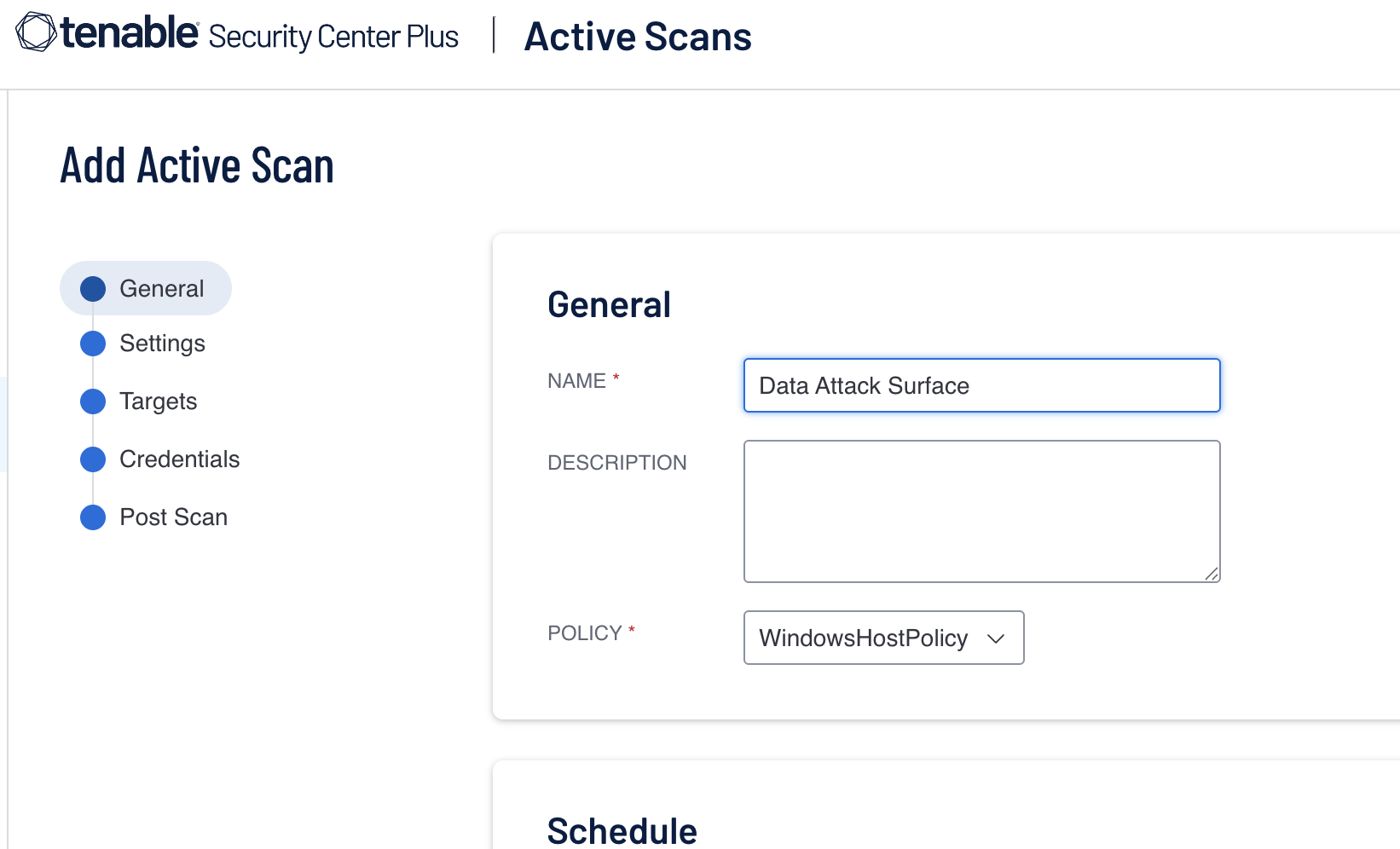
- Set the settings as required
- Set the targets tab as follows to use the Asset created
- Set any other settings as needed and submit the scan definitions.
- Execute the scan
-