Eyeglass Solutions Publication
Sumo Logic SOAR Integrations
Home
What is Sumo Logic SOAR?
- Overview
- Support Statement
- Limitations
- Solution Overview
- Advanced Zero Trust Capabilities
- What is Sumo Logic SOAR?
- Integration Architecture
- Solution Configuration in Sumo Logic SOAR
- Prerequisites
- Configuration in Sumo Logic SOAR
- How to test the Integration with Sumo Logic SOAR
- Sumo Logic SOAR Alert Monitor Playbook Integration
- Prerequisites
- Critical Data NAS Snapshot Alert Monitor
Overview
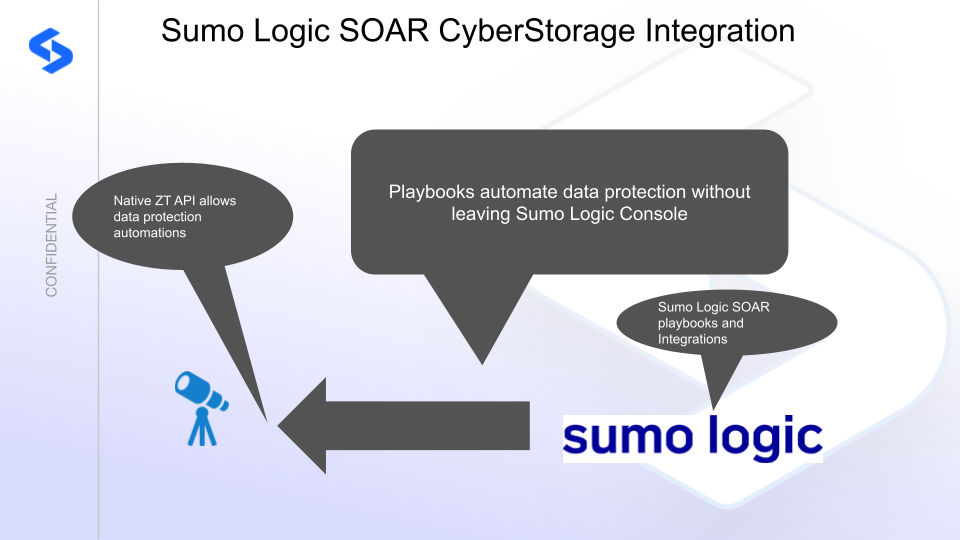
Customers using Sumo Logic SOAR solution can now leverage a native integration Playbook and Integrations that enables Cyber Storage . Customers can augment the capabilities of Sumo Logic SOAR with threat intelligence and Cyber Storage capabilities of Superna Security Edition.
Support Statement
-
NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
Limitations
- None
Solution Overview
Superna Defender Zero Trust API enables native playbooks and integrations within Sumo Logic Cloud SOAR or Sumo Logic automations within the SIEM platform.
Advanced Zero Trust Capabilities
- SOAR Playbooks that enable the following use cases
- Snapshot critical NAS data to create an immutable rollback point. This snapshot can be used by Data Security Edition to recover data from a cyber attack with automated single file recovery and compromised data quarantine.
- User lockout workflow allows triggering a user account permissions lookup and blocking the users access to data. This would be used when a users credentials are compromised and proactive data protection actions should be taken. NOTE: unblocking a user can be completed from the Data Security Essentials Active Alert incidents interface.
What is Sumo Logic SOAR?
Sumo Logic Cloud Cloud SOAR provides security analysts and SOC managers with enhanced visibility across the enterprise to thoroughly understand the scope and context of an attack. Streamlined workflows and automated playbooks that automate data protection responses can extend Cyber Storage protection to Sumo Logic customers. Streamlined incident response provides better outcomes from Cyber attacks.
Integration Architecture
Solution Configuration in Sumo Logic SOAR
Prerequisites
- Installed Security Edition
- Eyeglass OS appliance version 15.5 or later
- cat /etc/os-release
- License key for the Zero Trust API
- Zero Trust API token from Eyeglass
- Sumo Logic SOAR or Sumo Logic base SIEM product
- Automation Bridge installed https://help.sumologic.com/docs/platform-services/automation-service/automation-service-bridge/#requirements
Configuration in Sumo Logic SOAR
Steps to Import Playbooks and Integrations for Automation
- Log in to Sumo Logic console and open automation integrations

- Select the + Integration button to import a yaml file defition of the integration.
- Download the YAML files for Snapshot Automation of NAS data. Unzip the file yaml files.
- Import both YAML files
- This should import an integration and an HTTP POST API action
- Edit the Resource defaults (snapshotapidata) on the integration to enter the IP address of the eyeglass VM and update the HTTP headers section with the API key from Eyeglass.
- Create API token, Login to Eyeglass VM --> Integrations Icon --> API token tab --> + to create a new token , enter a name. copy the token value to update headers following steps below. In the image below replace the 172.31.1.102 ip address with your Eyeglass VM.
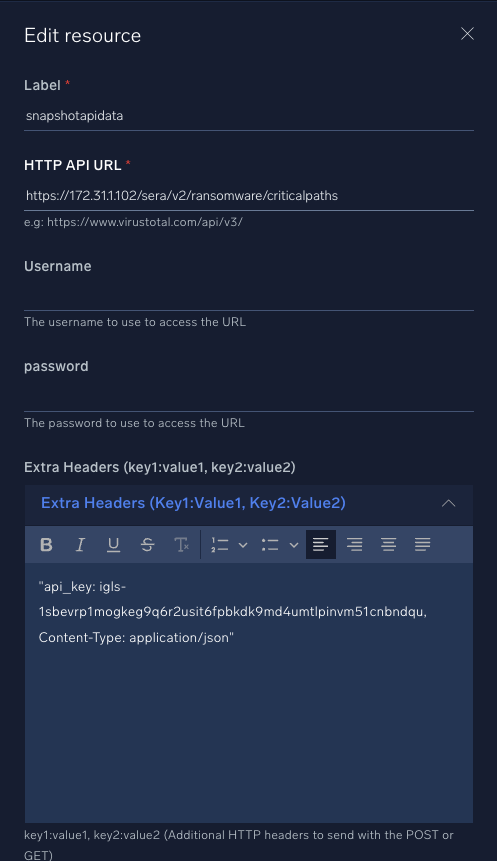
- Edit this text and replace the yellow with your API token. "api_key: igls-1sbevrp1mogkeg9q6r2usit6fpbkdk9md4umtlpinvm51cnbndqu, Content-Type: application/json" and paste into the header section.
- Scroll down and select the Automation Bridge name that will be used to proxy API calls to an on premise endpoint.

- Click Save
- Import the Playbook
- Click the + to import a playbook
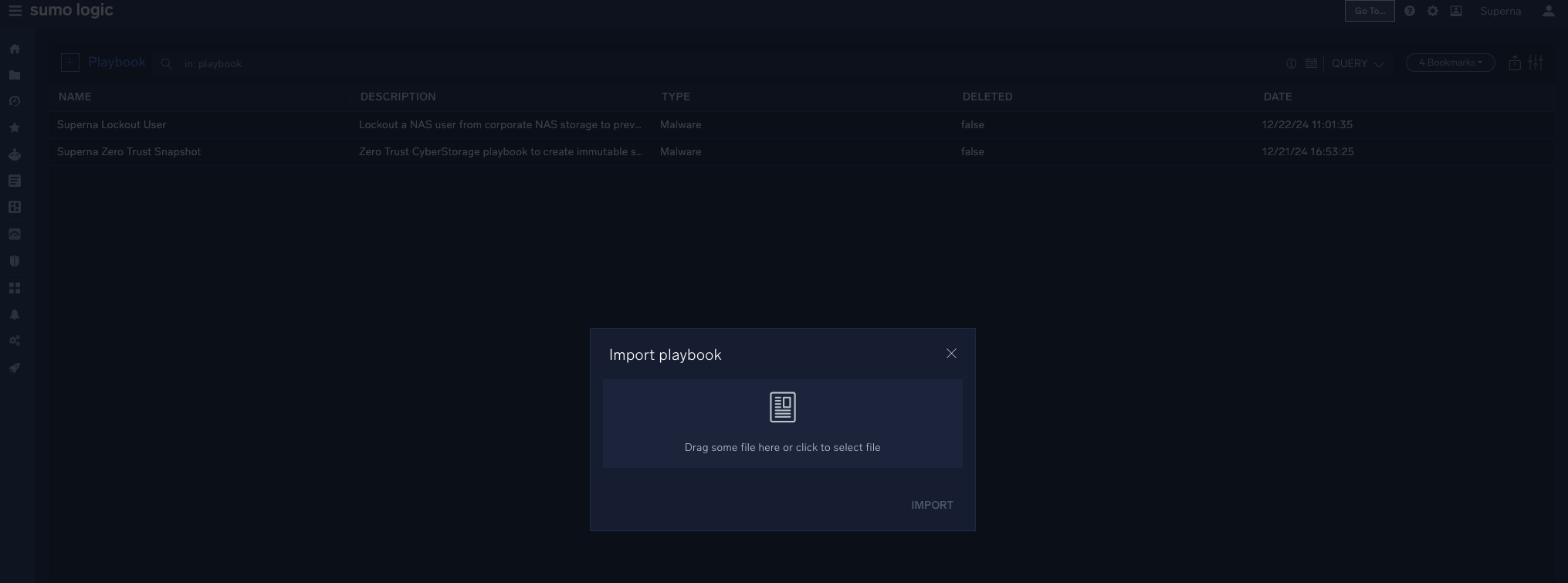
- Download this Playbook compressed file.
- Click the upload button and provide the compressed gz file as the input. This will import all the files needed to create the playbook, that leverages the integration created in the previous step.
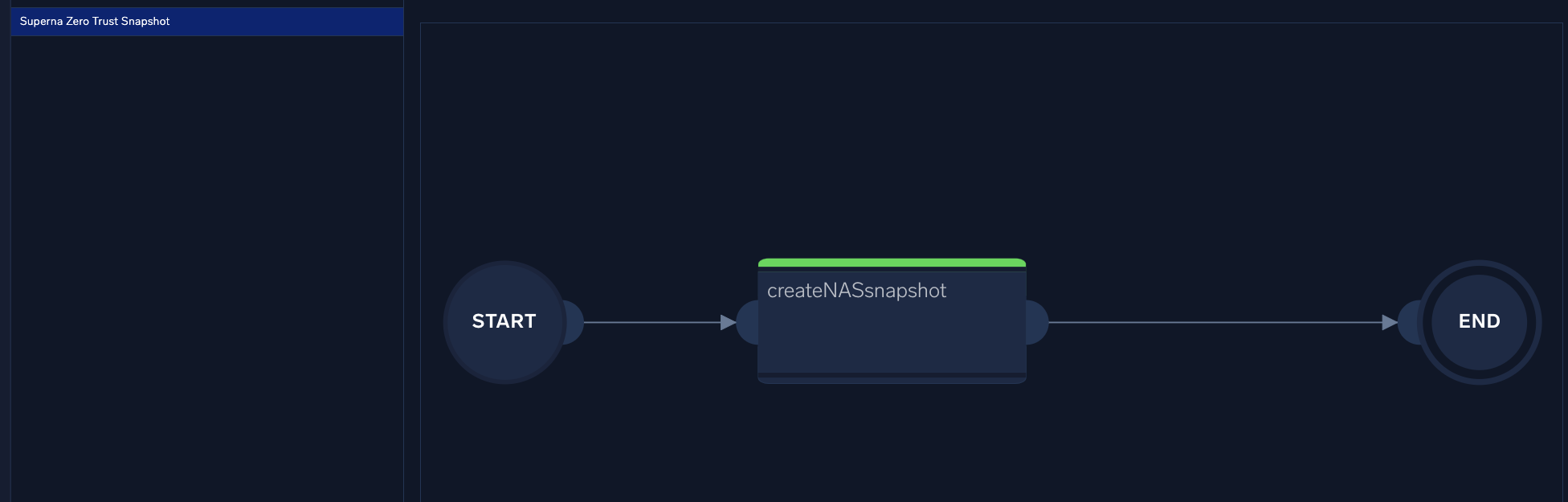
- done
How to test the Integration with Sumo Logic SOAR
- To test the playbook use the playbook test option
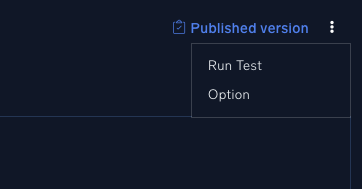
- the 3 dots reveal a test option
- Change the drop down to show custom
- Then click Run
- A successful execution will show the results of the API call and green success
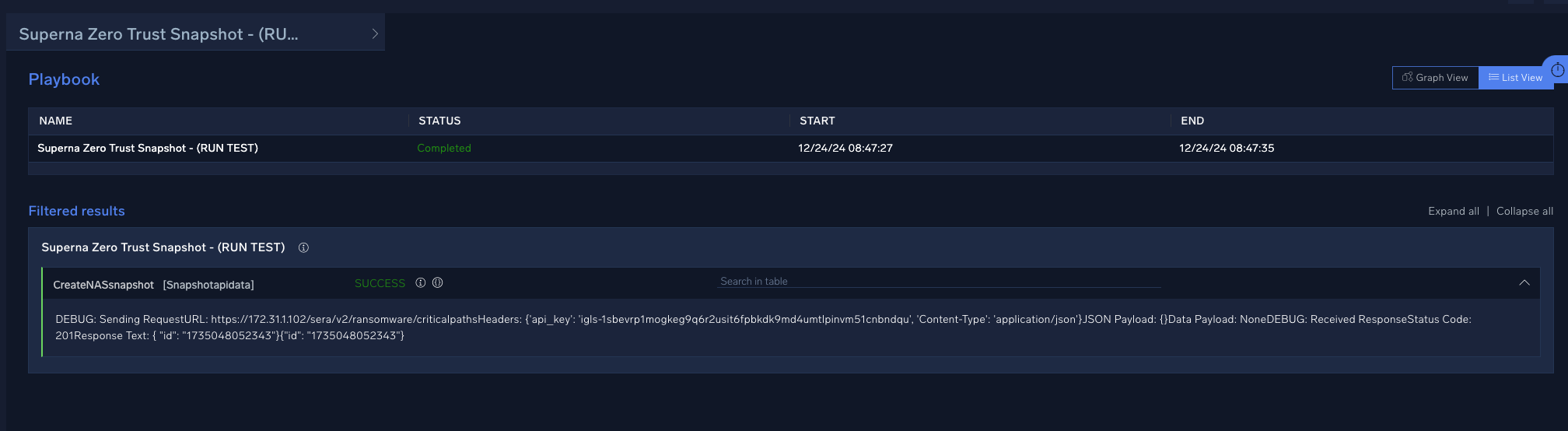
Sumo Logic SOAR Alert Monitor Playbook Integration
The Sumo Logic SOAR automation playbooks can be integrated with Alert monitors. The examples below provide pre-built Alert Monitors that can be imported and leverated witht he integration and playbooks.
Prerequisites
- Installed and configured all Superna integration and playbooks as per steps in this guide.
Critical Data NAS Snapshot Alert Monitor
- Open the Alert Monitor UI on the console
- Import a new Monitor definition
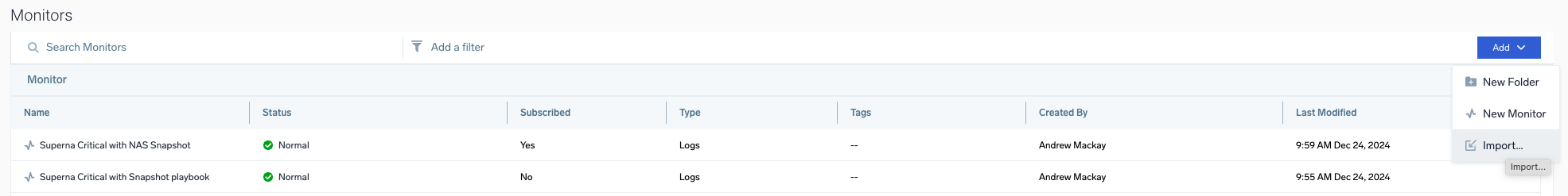
- Download the json definition of the Superna Critical with Snapshot playbook monitor. (right click download and save as)
- Open this file to import the playbook definition.
- It should be enabled by default. Click subscribe on the playbook action menu to be notified when this monitor triggers.
- Now edit the Monitor and scroll down to the automated playbooks section and make sure the playbook is listed (Superna Zero Trust Snapshot), you may need to paste the name again and save the monitor to link the playbook ID with your instance's ID number for the playbook.

- Example Alert
- Done.
- NOTE: The snapshot playbook could be associated with other Monitor definitions for any scenario where protecting data is a required next step. Example user account has been phished or multiple failed login attempts indicating a brute force attack on passwords.

