Eyeglass Solutions Publication
ServiceNow Incident Management Integration with Zero Trust Alerts
Home
- Ransomware Defender & Easy Auditor ServiceNow Webhook alarm to Incident Integration
- Support Statement
- How to Configure
- Sample Scripted REST API Webhook
- Steps to use the endpoint with Defender Webhooks
- Production Integration Steps
- Example Incident Created with Zero Trust Webhook and ServiceNow Scripted REST API Capability
- How to Convert an Incident to a Security Incident and Update the list of Affected Share CI's from ServiceNow's CMDB
Ransomware Defender & Easy Auditor ServiceNow Webhook alarm to Incident Integration
Support Statement
- NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
How to Configure
- This integration examples shows how to configure Ransomware Defender Webhook alarms to create an incident in ServiceNow and include the details of the alert in the description. NOTE This is a basic example only and would need to be customized further to map fields in the webhook payload to specific ServiceNow fields.
- Using this guide (How to Integrate Webhooks Into ServiceNow) create a ServiceNow Scripted Rest Resource Webhook
- Example Scripted REST
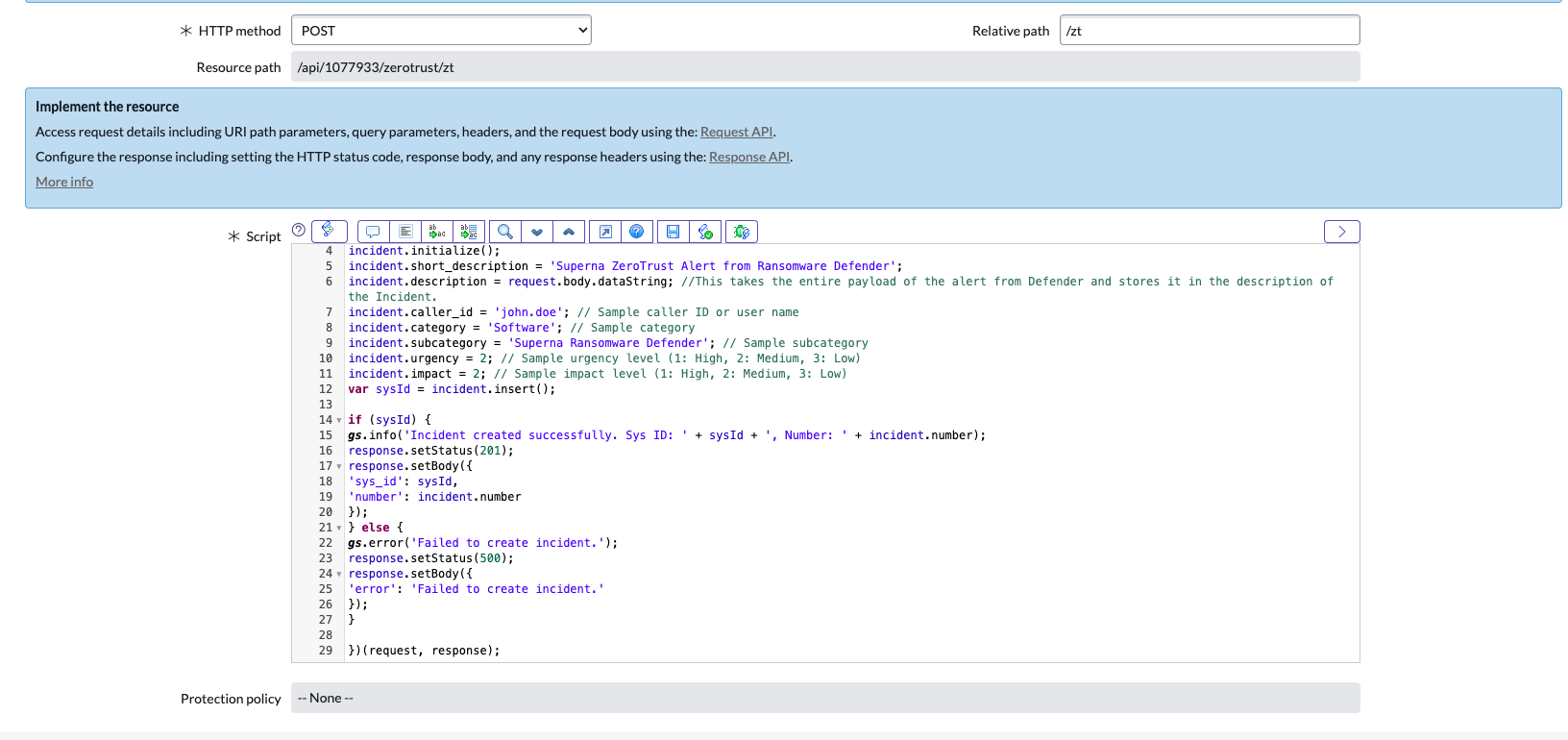
- In the script section
- Example Scripted REST
Sample Scripted REST API Webhook
Features
- Creates new incidents
- Updates incidents when the event ID matches an existing incident, this allows different status updates on an event in security edition to update the working notes in service now to show the history and state changes of the event.
- If monitor mode is enabled, the incident will be created but closed with the history showing the work notes. This feature allows monitor mode customers to test the integration without creating open incidents in ServiceNow
- Download the code here.
- Open the file and copy and paste the script text to the endpoint script editor.
See example below
Steps to use the endpoint with Defender Webhooks
- Save the Resource script after you paste it
- Disable Security for testing.
- Get the endpoint url for the webhook in Defender
- The resource would be https://yourInstance.service-now.com/<resource_Path>
- In this example the resource path is displayed in the editor
- Configure the Webhook in Ransomware Defender Zero Trust UI
- See guide above for more details
- Non authenticated - See below with headers section added for Content-Type and value application/json
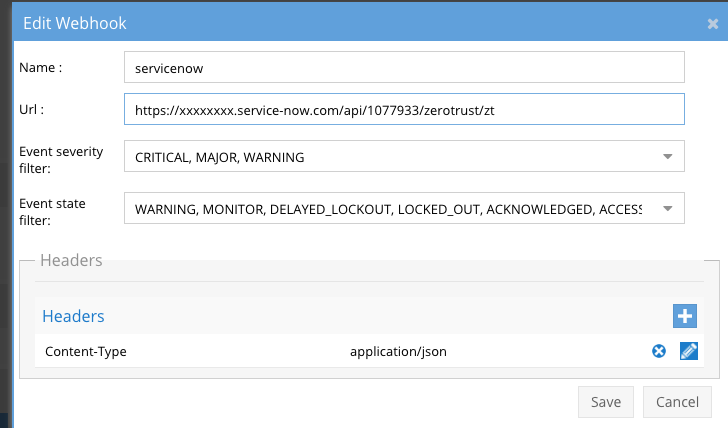
- If using authenticated endpoints add an additional HTTP Header using Authorization key and Basic xxxxxx , where xxxxx is the api key provided by ServiceNow.

- Save and click the test button
- If successfully configured you will receive an Incident number back see below.
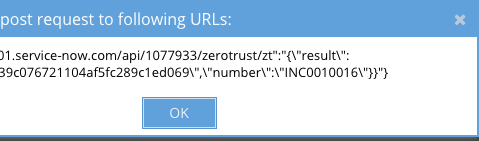
- Done
Production Integration Steps
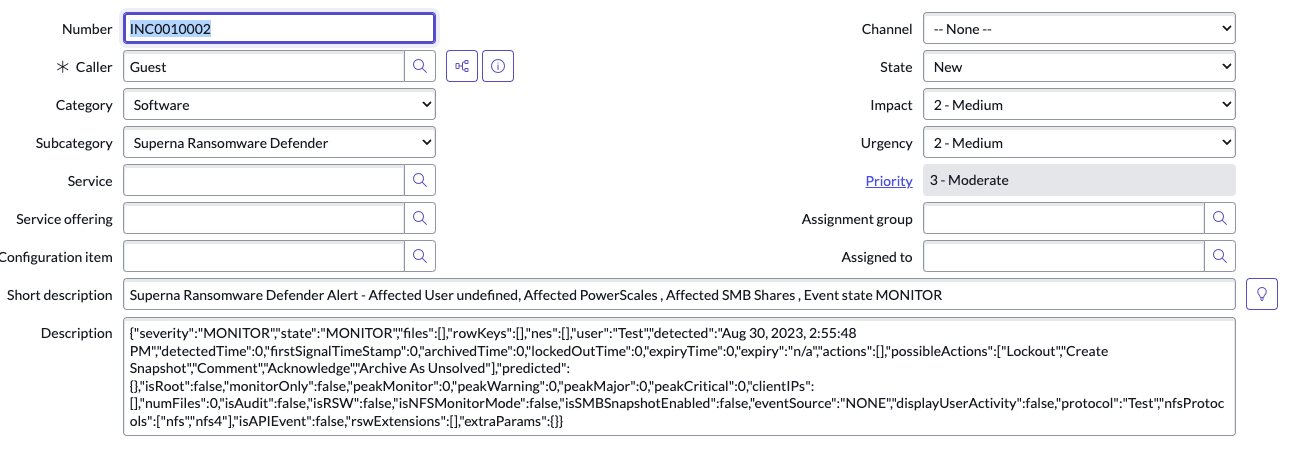
In this example, the variables are filled with sample values but could be extracted from the Alarm payload sent by Ransomware Defender and mapped to the ServiceNow fields
- The code sample above includes logic to extract variables from the payload of the Zero trust Ransomware Defender and maps the Severity fields in the Superna alarm to map to the ServiceNow Impact and Urgency incident fields. This code can be modified to change the mapping as required.
- The short description was used to summarize the key data in Security events. This can also be customized further.
Example Incident Created with Zero Trust Webhook and ServiceNow Scripted REST API Capability
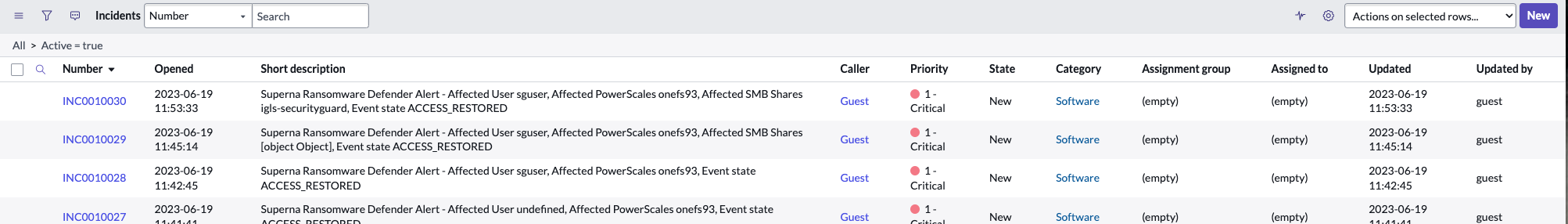
- Incident details
How to Convert an Incident to a Security Incident and Update the list of Affected Share CI's from ServiceNow's CMDB
Overview
Customers that have invested in Security Incident Response module in their ServiceNow instance can convert ZeroTrust incidents into security incidents and assign CI's for the affected SMB or NFS exports on the PowerScale or other storage cluster. This allows customers to fully leverage the Superna ZeroTrust Incident integration and the ServiceNow CMDB integration for a complete service to security workflow enabled solution.
Requirements
- Configured Zero Trust webhook integration
- Installed ServiceNow Security Incident and Response module
How to Convert an Incident to a Security Incident
- View the incident created by the ZeroTrust Webhooks script integration
- The button on the right will convert the incident to a security incident. Notice the business rules that executed and the new SIR id assigned to Jay Wang Security Analyst.

- Now Click on the SIR xxx number to view the new Security Incident
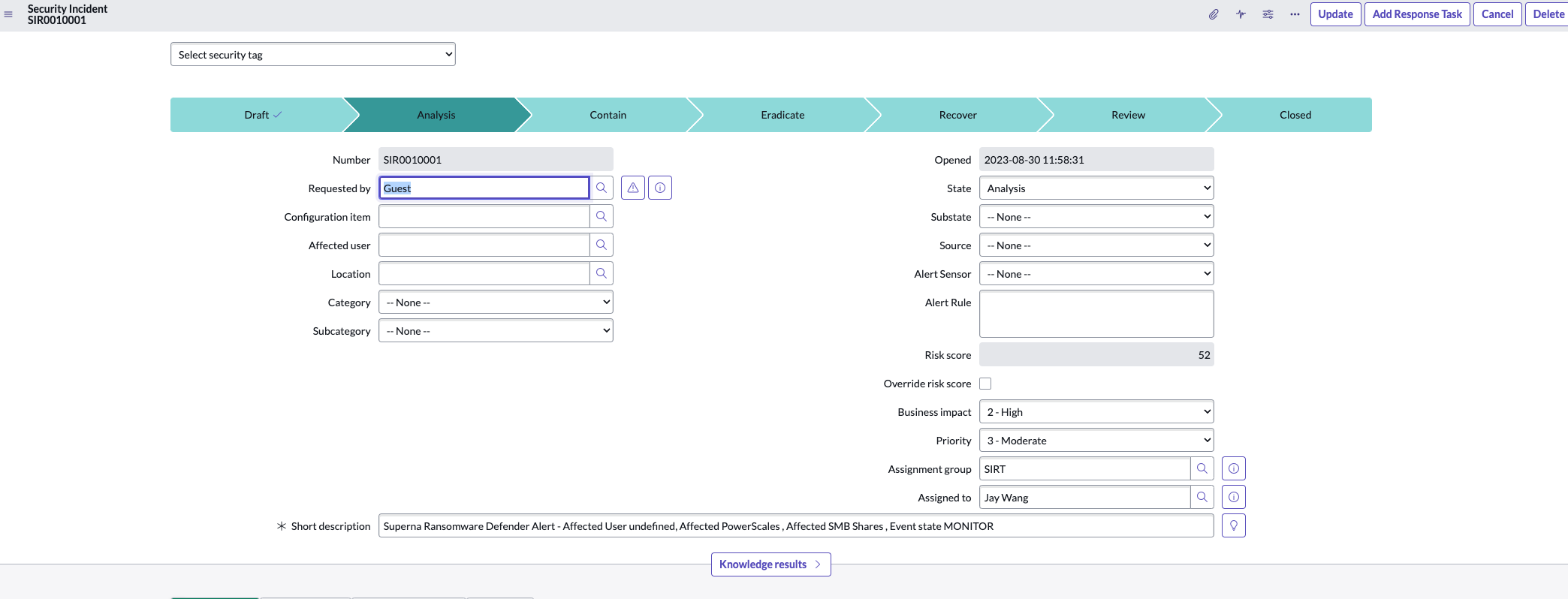
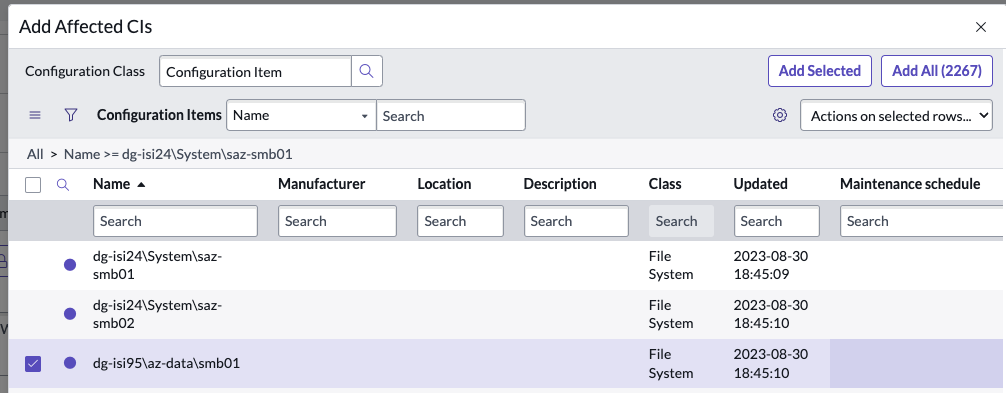
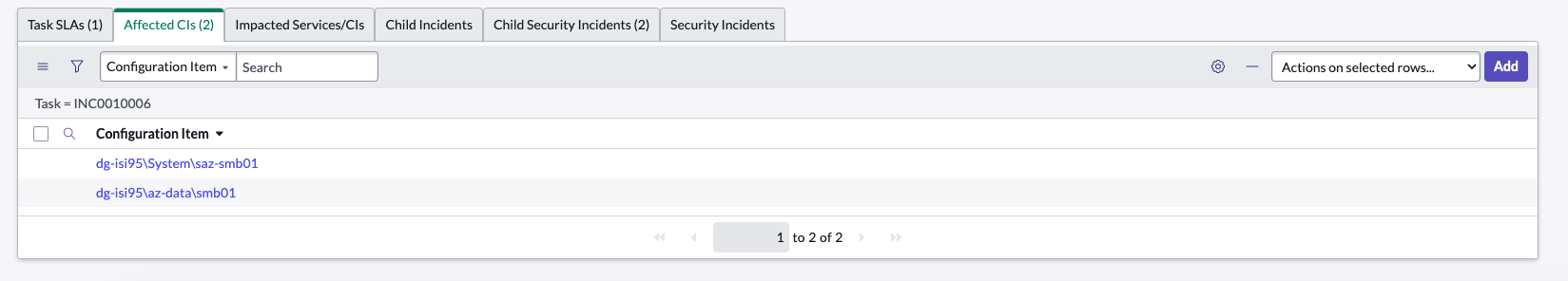
How to Update Affected CI's to indicate the scope of the Security Incident
- Open the Security Incident Dashboard or the SIR itself
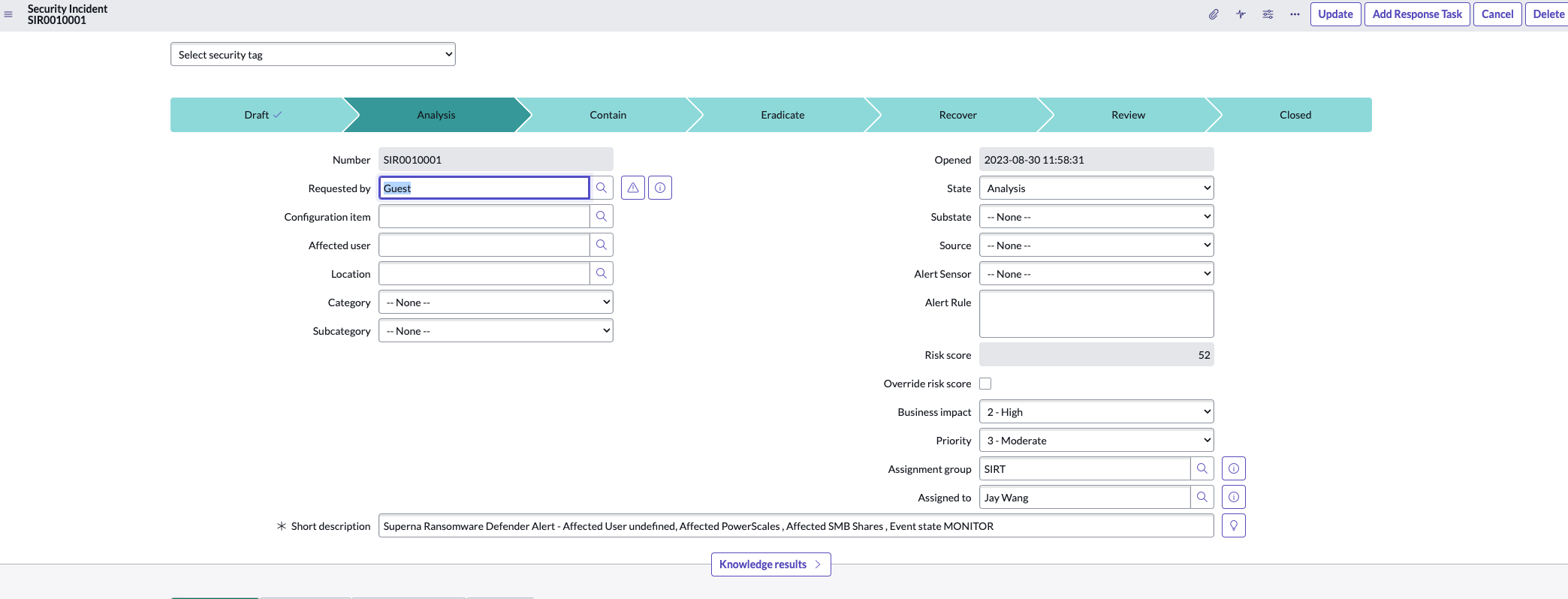
- Security Incident fields can be filled in from the description information

- Copy affected User field to the Affected User SIR field, if your Active Directory users are synced to Servicenow you can search for the user to select from the list.
- Copy the affected SMB share name from the short description to lookup the affected SMB share CI in the CMDB (the CMDB integration must be completed)
- Click Add
- Search for the SMB share name listed in the short description of the Security Incident