SentinelOne Zero Trust Security Host Network Disconnect Integration
- Overview
- Limitations
- Solution Overview
- Video Demo
- Advanced Zero Trust Capabilities
- What is SentinelOne?
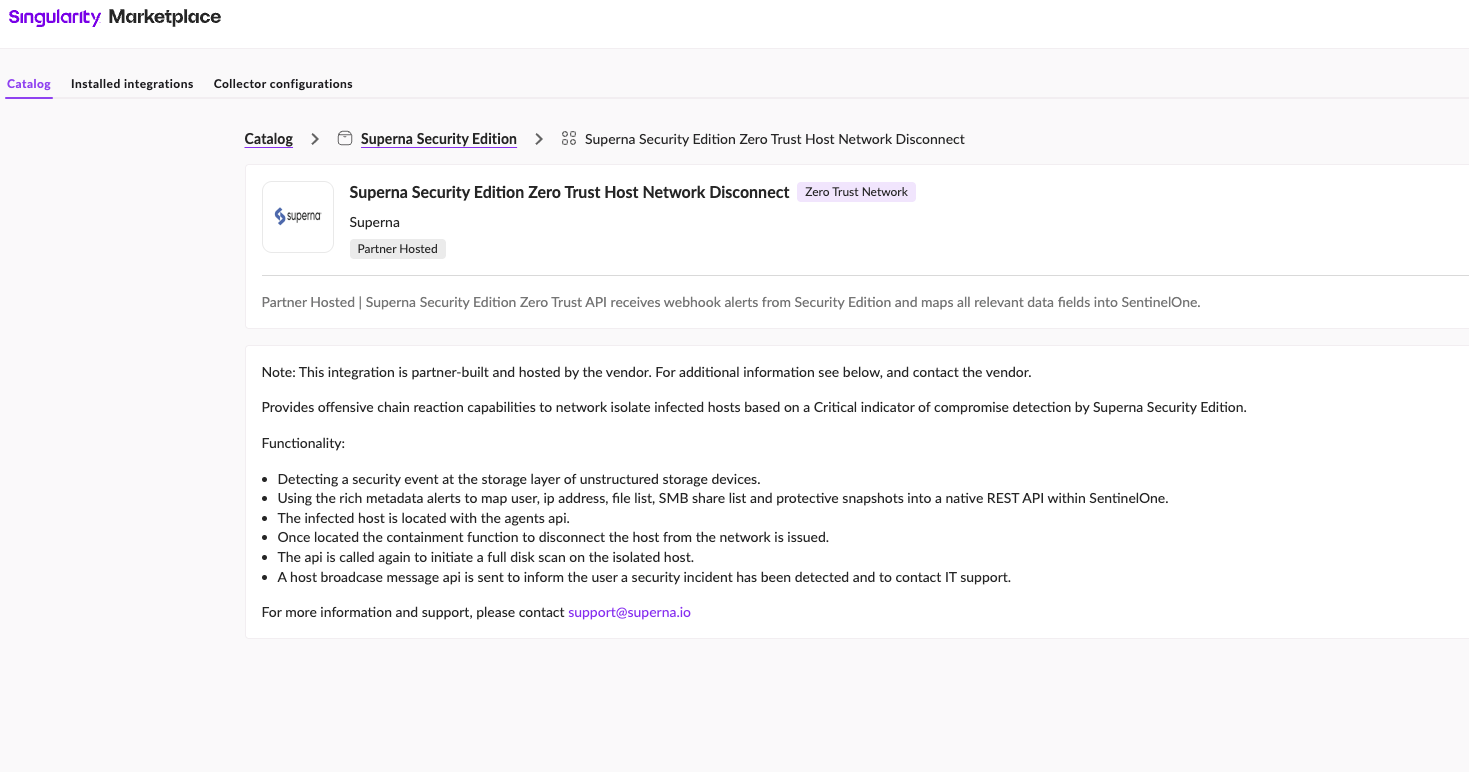
- SentinelOne Marketplace
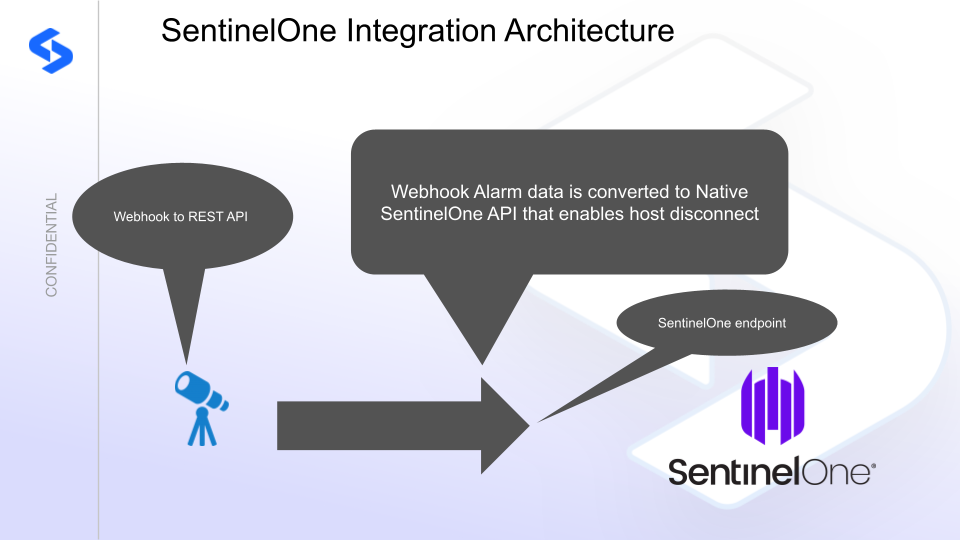
- Integration Architecture
- Solution Configuration in SentinelOne and Security Edition Zero Trust
- Prerequisites
- Configuration in SentinelOne
- Configuration Steps on Eyeglass Virtual Machine
- High Level steps
- Configuration Step by Step
- Configure the Service start and python integration files
- Configure the python packages and customize the SentinelOne integration python code
- Configure Security Edition Zero Trust Webhooks
- How to configure optional actions within the Integration
- How to test the Integration with SentinelOne
- SentinelOne SecOps administrators Integration Experience
- How to Configure Data Security Essentials
- Overview
- Requirements
- Features
- Steps to Configure Event Sync to SentinelOne Host Containment Integration
Overview
Customers using SentinelOne can now leverage a native integration that initiates native API integration to isolate hosts where flagged as compromised by Superna Security Edition.
-
NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
Limitations
- None
Solution Overview
Superna Security Edition Zero Trust API receives webhook alerts from Security Edition and maps all relevant data fields into SentinelOne.
Video Demo
Advanced Zero Trust Capabilities
- Superna Security Edition host Network disconnect api integration with SentinelOne. Default is enabled.
- Optional
- Host broadcast message sent to the host about the security actions taken. Default is disabled.
- Initiate full scan of the host to look for threats inside the host. Default is disabled.
What is SentinelOne?
SentinelOne Marketplace
The solution is documented in the Marketplace
Integration Architecture
Solution Configuration in SentinelOne and Security Edition Zero Trust
Prerequisites
- Installed Security Edition
- Eyeglass OS appliance version 15.5
- cat /etc/os-release
- License key for the Zero Trust API
- SentinelOne
Configuration in SentinelOne
To generate an API token in SentinelOne , you'll need to follow these steps.
Create an API token for a service account user.
- Create a log write api key
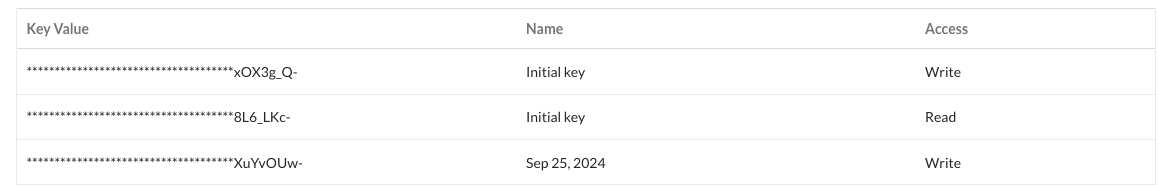
- Record the api token to be used in the integration script.
Configuration Steps on Eyeglass Virtual Machine
High Level steps
- Create python location to run the application on the Eyeglass vm
- Create python main application script
- Create linux systemd service and set to auto start
- Create Zero Trust configuration in Security Edition
- Update the main script to customize with SentinelOne python code
- Test the script is running as a service
- Create a test event in Security Edition to validate the alerts appear as indexed parsed events in SentinelOne
Configuration Step by Step
Configure the Service start and python integration files
Configure the python packages and customize the SentinelOne integration python code
- Customize the application code by downloading the python code from this link to download
- Open the python template file in a text editor. NOTE: make sure to only replace the values and do not delete any of the commas
- Locate this section in the file # Define the endpoint and API token as variables to add your SentinelOne api token and endpoint for API calls .
- Add the API URL and API token into this section below
- # SentinelOne instance URL and API tokeninstance_url = "https://yyyyyy.sentinelone.net"api_token = "xxxxxx"
- nano /opt/superna/cgi-bin/sentinelone.py
- Open the file locally in Windows OS notepad and use control-A or select all the text in the python template
- Paste the clipboard into the ssh terminal session with the open nano editor file
- save the file
- press control+x
- Answer yes to save and exit the nano editor
- Start the service and verify it is running
- systemctl start sentinelone
- systemctl status -l sentinelone
- Verify the service is started successfully and returns "active and running".
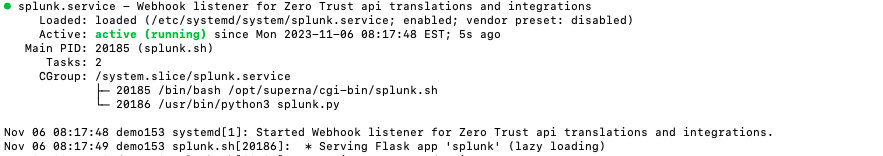
- If the service does not start do not proceed and double check the steps above are completed.
Configure Security Edition Zero Trust Webhooks
- The next step creates an Zero Trust Webhook URL.
- Configure Zero Trust endpoint in Ransomware Security Edition Zero Trust tab.
- Recommended Configuration: Only Critical and Major events and only the webhooks that set lockout or delayed lockout. Customers can customize based on specific requirements. The goal is to send findings versus a list of alarms that do not pinpoint a security incident.
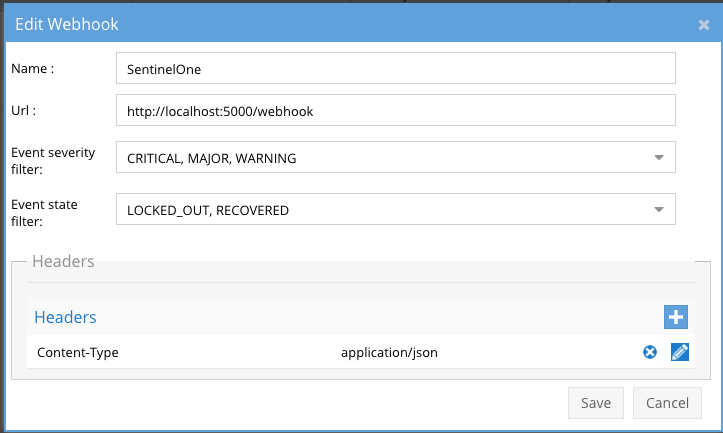
- The endpoint url above will use localhost and will send Webhooks to the application service listening on port 5000. URL to use in the configuration
- http://localhost:5000/webhook
- Add the Content-Type header with value of application/json as shown above to complete the webhook configuration.
- Click save to commit the configuration.
- Click save on the main Webhook configuration page
- Configure Zero Trust endpoint in Ransomware Security Edition Zero Trust tab.
- Test the configuration is working following the next section
How to configure optional actions within the Integration
- The integration code will default to host isolation enabled, host broadcast disabled, full scan disabled.
- Edit the integration code as follows to enable optional actions.
- # Flags to enable/disable features
- enable_isolation = True # Set this to False to disable isolation
- enable_broadcast = True # Set this to False to disable broadcast messages
- enable_full_scan = True # Set this to False to disable full disk scan
- nano /opt/superna/cgi-bin/sentinelone.py
- edit to True the options you want to enable
- Then save using control+x to save the file
- systemctl start sentinelone
How to test the Integration with SentinelOne
- Follow these steps to test the integration.
- Edit the integration script and locate this section
- # test an IP using hard coded# host_ip = 'x.x.x.x'# severity = 'CRITICAL'
- remove the # for the host_ip and severity line and enter an ip address for a SentinelOne endpoint to test the Isolation API
- Create a test lockout to generate a webhook,
- Create a banned file extension type in the Security Edition File Filter list
- Using a windows client pc mount an SMB share protected by Security Edition and create files with this section , create at least 100 files, verify your pc is locked out and an event is generated in the console.
- Now check SentinelOne console to verify if the network isolation network disconnect was processed.
- See below what the user experience looks like in SentinelOne console.
- Make sure to add the comment lines back when done using the # at the front of the line and save the file.
SentinelOne SecOps administrators Integration Experience
Overview: Once configured, Superna Security Edition integration with SentinelOne enables real time alert ingestion using the integration code and host network disconnect. This ensures compromised hosts are disconnected from the network after a serious incident detection at the storage layer.
- Host before any Cyber Storage detecctions.
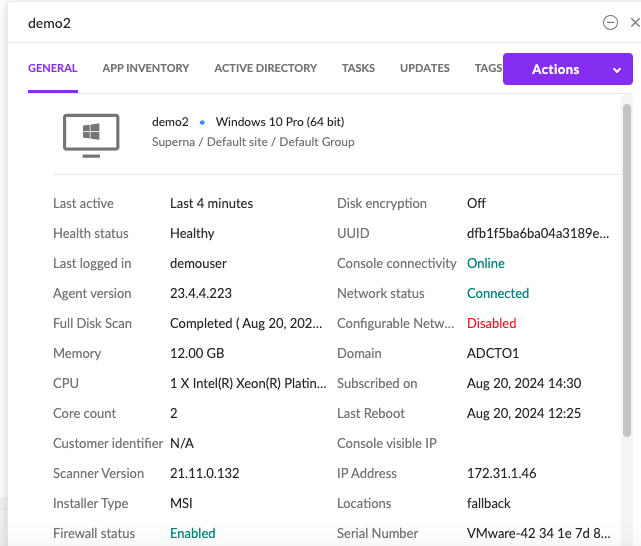
- After a detection in Security Edition and integration code activated the host will look like this.
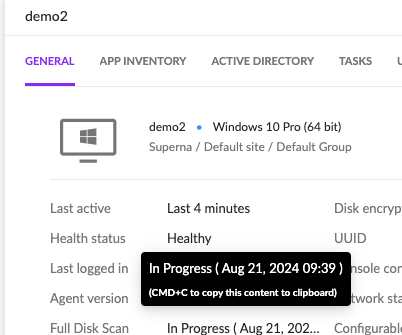
- Integration response log
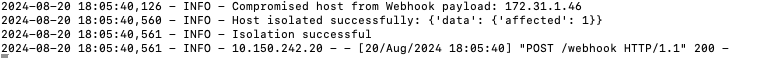
- Network status now shows Disconnected.
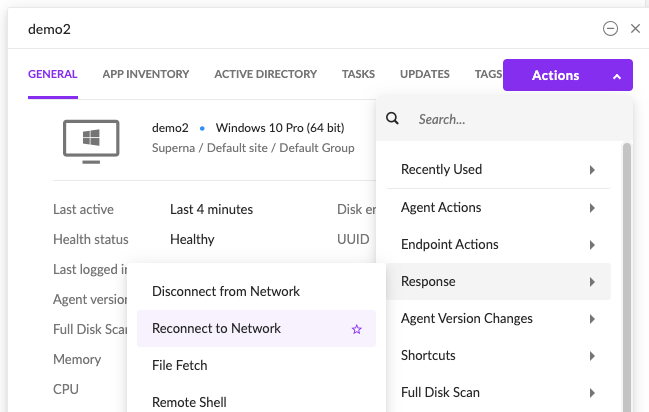
- To reconnect to host use the actions menu
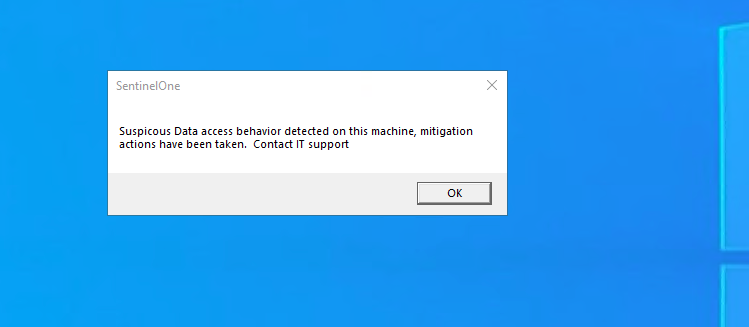
- If host broadcast message is enabled the host will see this message (text can be customized)
-
- If full scan is enabled as a response action the console will indicate a full scan has been started.
How to Configure Data Security Essentials
Overview
Data Security Essentials saves alerts to the Windows Event log to a custom application log. This integration will extract the log entries and the json payload contained within them and format as webhook data to send to SentinelOne to issue the host containment to the endpoint provided by SentinelOne.
Requirements
- Follow the SentinelOne integration steps above to configure the Scripted REST API endpoint integration.
- Install python for Windows on the Data Security Essentials host and allow the installation to add python to the path variable. https://www.python.org/downloads/windows/
- NOTE: Ensure it's installed for all users so service accounts have access, by enabling for all users during installation.
- The integration code matches event log entries from Custom trigger BOT policies and File management policies
- The event log source names are below
- Superna Data Security Essentials BOT Service
- Superna Data Security Policy Engine
- The event log source names are below
Features
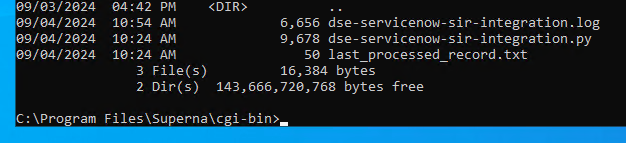
- Logs for each execution are stored in the path below along with the python code.
- Each execution will store the event log record ID and date time and event number of the last processed event in a file called last_processed_record.txt. This file is read on each execution to continue processing from last record. The record number is not visible in Event Viewer, the date time and event number can be used to understand where in the log the last processing occurred.
- The schedule sync runs every minute and only processes events since the last record and logs all processing as well as event matches in the log file for debugging.
- Only events that match the severity filter will be processed for client ip address. The sample code defaults to Major and Critical severity events all other severities will be ignored.
Steps to Configure Event Sync to SentinelOne Host Containment Integration
- Download the integration code from here. (Right Click Save as to download)
- Modify the python and update the SentinelOne integration settings highlighted in yellow to match your environment.
- # SentinelOne API credentialsclient_id = 'xxxxxx'client_secret = 'yyyyyyy'base_url = "https://api.us-2.SentinelOne.com"# Configurationserver = 'localhost'log_name = 'Data Security Essentials'source_names = ['Superna Data Security Essentials BOT Service', 'Superna Data Security Policy Engine']trigger_severities = ['MAJOR', 'CRITICAL','WARNING'] # Configure severities that should trigger containmentenable_isolation = True # Set to False to disable isolation actions
- Copy the Python code into C:\Program Files\Superna\cgi-bin on the Data Security Essentials host and name the file sentinelone-dse.py
- Install python dependancies
- MANDATORY Step: Open a command prompt as the service account (hold down shift and right click the command prompt icon) run as option to login as the service account dse-service. This is required to install the python packages under the correct user account.
- Install the dependencies with this command
- pip install pywin32 requests
- This command installs the windows API python libraries needed to read the event log.
- Test the script can correctly reach your SentinelOne instance from a dos prompt
- cd C:\Program Files\Superna\cgi-bin
- python SentinelOne-dse.py
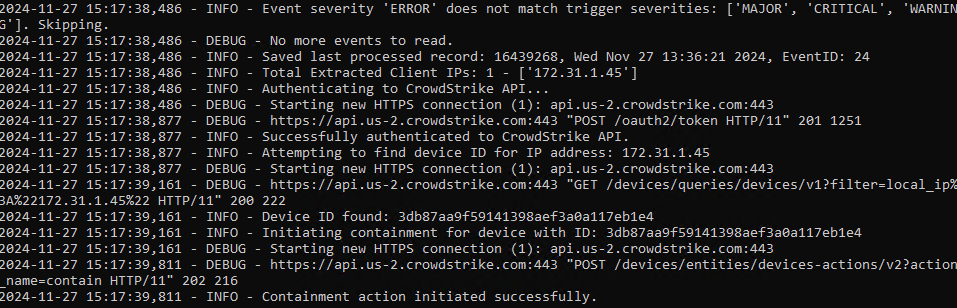
- The output should display event log entries that match and will ignore severities that do not match script settings . It will display the event payload details in json format and will show the data that was sent to the SentinelOne endpoint.
- Example output
- You can also review this file last_processed_record.txt to see the last date and time within the event log and event id that was last processed. This file can be deleted to have the script start reading from the oldest windows event log entry. This can be done for testing puposes.
- The above examples shows the output when a client ip address is successfully located and the host containment api returns success.
- The example below is logged when event data is processed and inspected for client ip and matching severity.
- Steps to Schedule sync alerts into SentinelOne Security Incidents
- Open secpol.msc, Local policies
- Give the Data security essentials AD service account the "Logon as a batch job" OS permission.
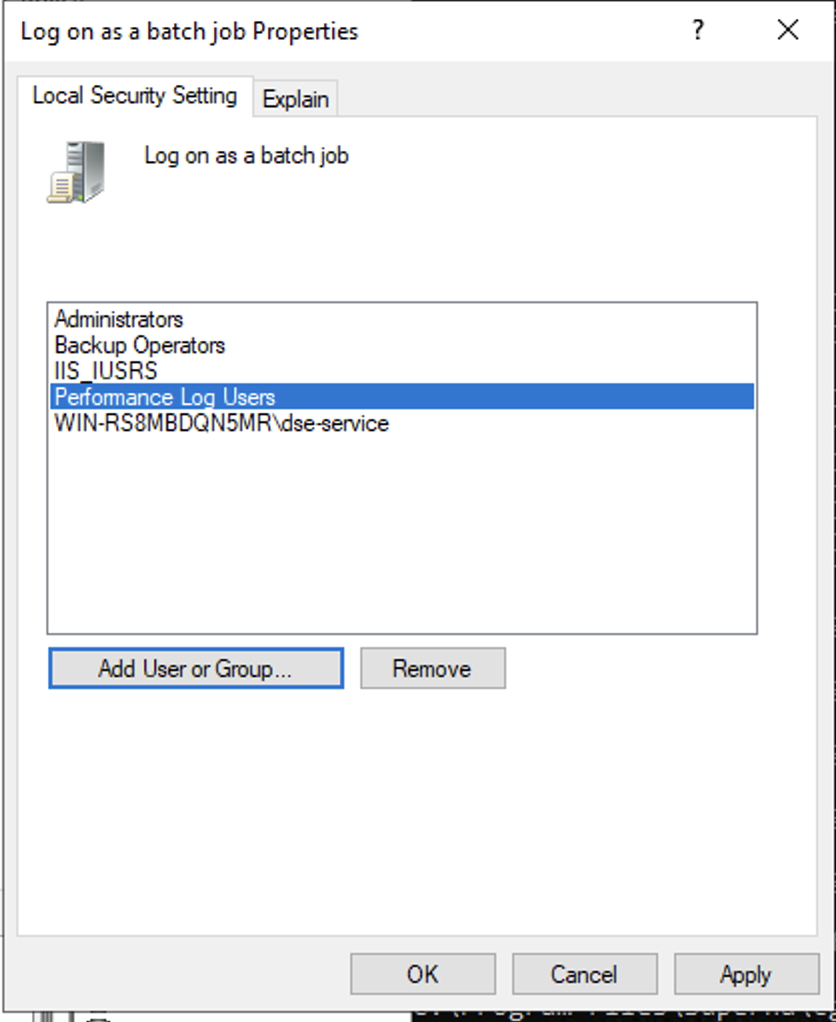
- Create a file
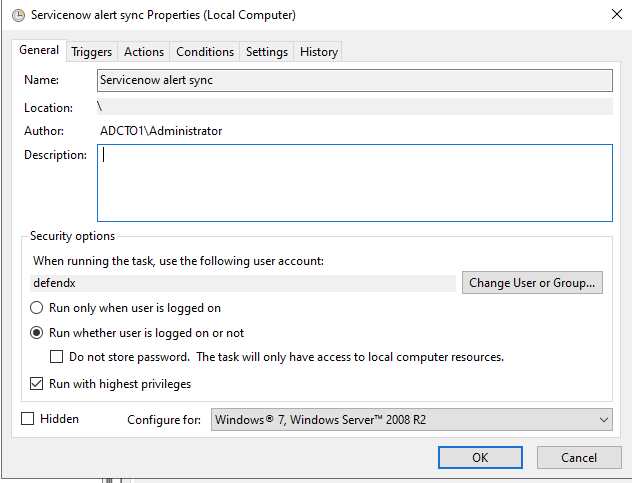
- Right click this link to save to a file. The task scheduler XML file to import into Task Scheduler
- You can rename the xml from Servicenow alert sync.xml to SentinelOne integration.xml.
- Open Task Scheduler
- Run taskschd.msc, right click task schedule library

- Import the xml file
- You will be prompted with the task definition, you will need to change the service account to match your service account name and domain and re-enter the password to save the task scheduler. All other settings are configured and match the path and settings used above. Adjust any parameters that you changed if you did not use all the steps above.
- Edit the name "SentinelOne Containment integration"
- Click the Actions tab and browse to select the file C:\Program Files\Superna\cgi-bin\SentinelOne-dse.py
- Click ok to save
- done.