Eyeglass Solutions Publication
Sentinel Superna Zero Trust Storage Snapshot Playbook
Home
Configure the Playbook Zero Trust API Integration
How to use the Superna User Lockout playbook in Sentinel
How to Configure a Zero Trust Playbook Integration with Cyber Storage Action Snapshot Data
- Overview
- Key Use Case
- Key benefits
- Support Statement
- How to Configure a Zero Trust Playbook Integration with Cyber Storage Action Lockout User
- Configure the Playbook Zero Trust API Integration
- How to use the Superna User Lockout playbook in Sentinel
- How to Configure a Zero Trust Playbook Integration with Cyber Storage Action Snapshot Data
- Configure the Playbook Zero Trust API Integration
- How to use the Superna Critical Data Snapshot playbook in Sentinel
- Importing Logic App Playbooks into Sentinel
Overview
A key capability of SOAR and security automation platforms is the ability to run sophisticated automations that help protect IT assets. In the case of Cyber Storage integration with Superna Zero Trust API allows SecOPS professionals to execute storage layer protection functions directly within the security tools.
Key Use Case
- Run an Incident Playbook to lockout the affected user in the incident from all storage SMB shares to stop a ransomware attack against NAS storage.
- Run an Incident Playbook to snapshot critical data on NAS storage as a proactive step. This playbook will not interrupt user access to storage and will provide a 4 hour snapshot of production data. The critical snapshot feature must be configured in Superna Security Edition.
Key benefits
- Automate security responses for increased reponse times and eliminate human error
- Builds upon a composable security architecture that integrates security tools into workflows and playbooks
- Integrates Cyber Storage capabilities to product unstructured data
Support Statement
- NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
How to Configure a Zero Trust Playbook Integration with Cyber Storage Action Lockout User
- Overview:
- This depends on incident playbooks and the Zero Trust alert integration already being configured. Custom fields in the zero trust alerts that appear in Sentinel are used as an input to this user lockout playbook .
- The steps below import a Logic App template that needs to be customized for your environment and API connections needed to connect to your Sentinel instance.
- Prerequisites:
- Sentinel Azure Instance
- Permissions to Sentinel and Logic Apps creation
- Superna Eyeglass VM api token
- Login to Eyeglass VM as admin --> eyeglass rest API --> Create new token --> provide a name for the token eg Zert Trust, copy the token to be used in the steps below.
- Firewall allows Azure source ip addresses to reach the Superna Eyeglass VM endpoint over port https 443
- Follow the steps in this section and select the playbook template to download before continuing to the configuration steps.
- High-level Summary of the Logic App
- receive the incident data in json format
- Initialize a variable to store the username in the incident
- Parse the incoming incident payload as json data using a schema that includes the custom Zero trust alert details that contains (username, sid, ip address, protocol of the affected shares), store as json object data for use within the Logic App.
- For Each loop to look at the data within the incident
- Pass the custom zero trust alert data into a compose function
- Extract the username field from the payload
- Remove the encoded double \ and " used to store the variable data in json format and end up with a domain\username syntax to be used with the Zero Trust API
- Set the Logic App variable to the user name without " and \ i.e. the cleanUsername
- Then URL encode the string, to allow it to be used within a URL API call, this encodes special characters like \
- Send the URL encoded value into the http function to send the API call to Eyeglass and append username to the API call URL.
- Send the user name to the email function to send an alert email with the locked out user and zero trust email contents
- Done.
Configure the Playbook Zero Trust API Integration
- Click on the newly created Logic App resource
- Click on the Logic Designer
- Locate the http object under the last step in the designer
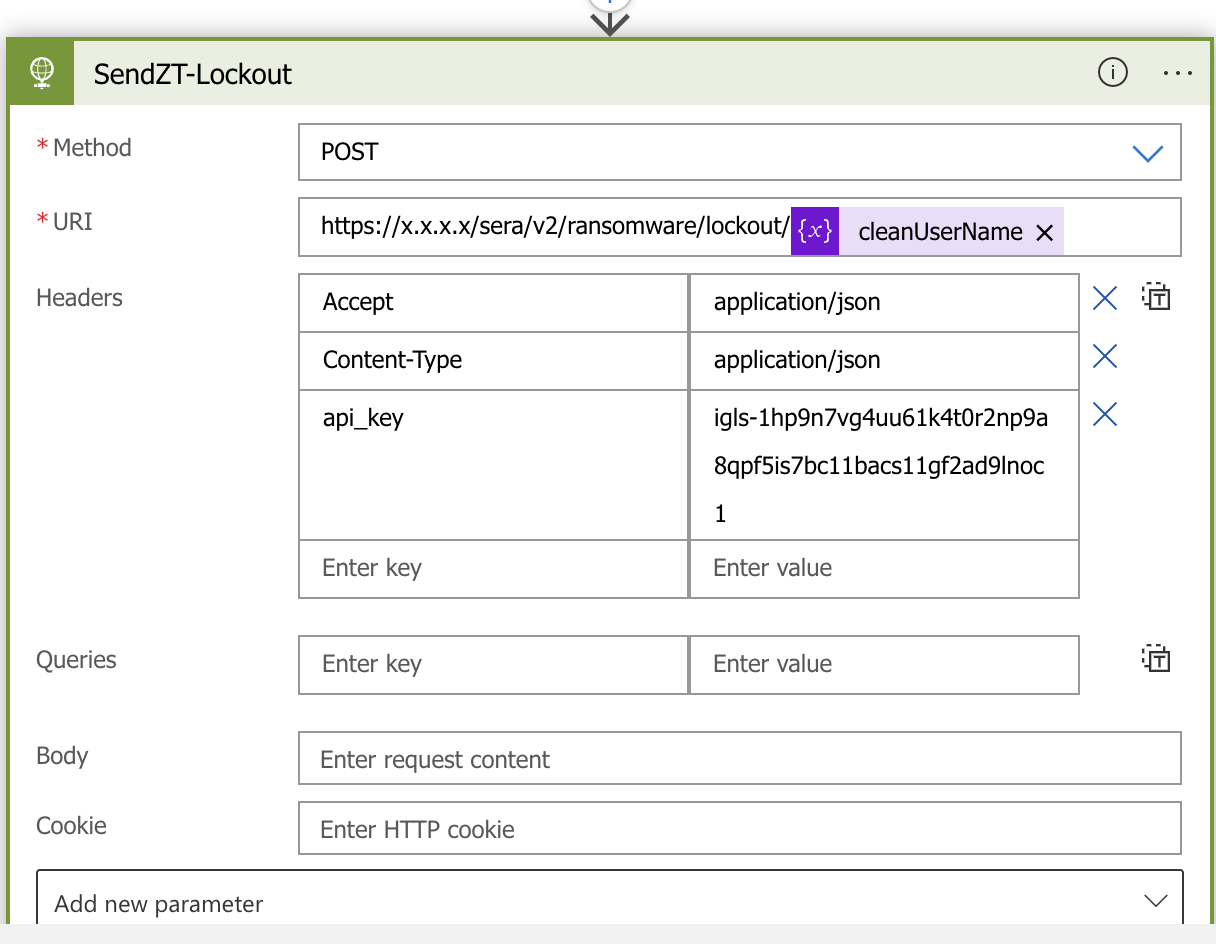
- Edit the HTTP details, the endpoint and use correct hostname or ip address.
- Replace the x.x.x.x
- Replace the API key igls-1hp9n7vg4uu61k4t0r2np9a8qpf5is7bc11bacs11gf2ad9lnoc1 with an api key created in Superna Eyeglass token created with steps above.
- This playbook uses the outlook connection step to send an alert each time this playbook is called. This step can be deleted but it's recommended to send a notification when a user is locked out.
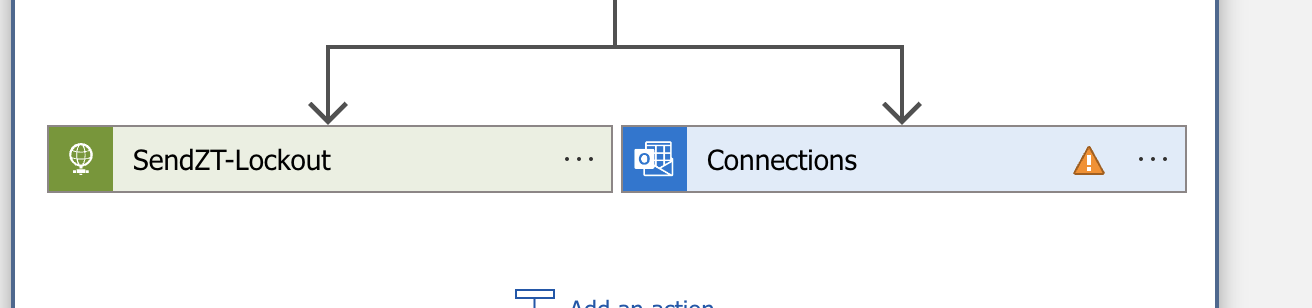
- You will need to register an outlook subscription. See Azure documentation to register a subscription for office365 with Azure. Once this is completed you can open the Logic App designer and click add new connection to use the email option.
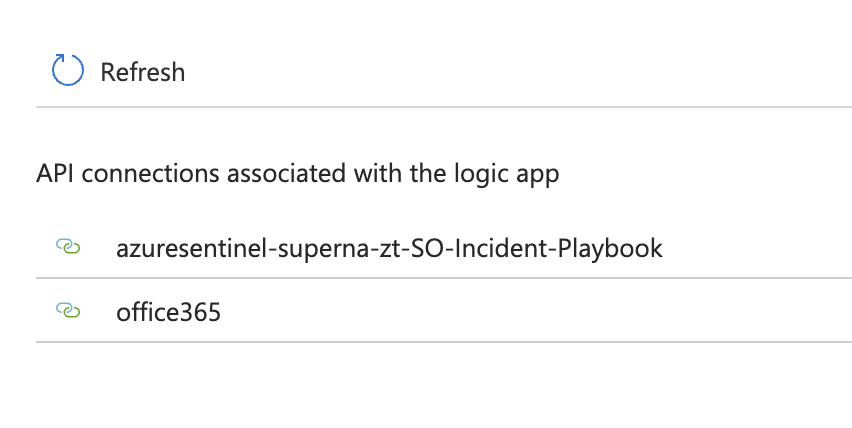
- Once registered it should appear in the Logic app API connections
- If you do not want to configure email , you have the option to delete this step and save the Logic app playbook without the email option enabled. This can always be added later on.
- Make sure to click save after each step
- Done, the playbook is ready to test from the steps below.
How to use the Superna User Lockout playbook in Sentinel
How to Configure a Zero Trust Playbook Integration with Cyber Storage Action Snapshot Data
- Overview:
- This depends on incident playbooks and the Zero Trust API. This does not use custom fields in alerts and can be enabled as a preemptive protection integration for Secops administrators.
- Prerequisites:
- Sentinel Azure Instance
- Permissions to Sentinel and Logic Apps creation
- Superna Eyeglass VM api token
- Login to Eyeglass VM as admin --> eyeglass rest API --> Create new token --> provide a name for the token eg Zert Trust, copy the token to be used in the steps below.
- Firewall allows Azure source ip addresses to reach the Superna Eyeglass VM endpoint over port https 443
- Follow the steps in this section and select the playbook template to download before continuing to the configuration steps.
- High-level Summary of the Logic App
- Receive the incident data in json format
- Call the HTTP zero trust api to issue critical data snapshot request to all protected Storage devices managed by Superna Security Edition. With the correct api token and headers set.
- Done.
Configure the Playbook Zero Trust API Integration
- Click on the newly created Logic App resource
- Click on the Logic Designer
- Edit the endpoint and use correct hostname or ip address
- Replace the x.x.x.x
- Replace the API key igls-yyyyy with an api key created in Superna Eyeglass token created with steps above.

- click the save button when done
- Done, the playbook is ready to test from the steps below.
How to use the Superna Critical Data Snapshot playbook in Sentinel
- Use Case: This playbook would be used by Secops when they suspect an incident may be malware, ransomware or any threat to corporate data. This play creates a proactive snapshot of all storage devices managed by Superna Security Edition.
- When an incident is being viewed select the Run Playbook (preview)
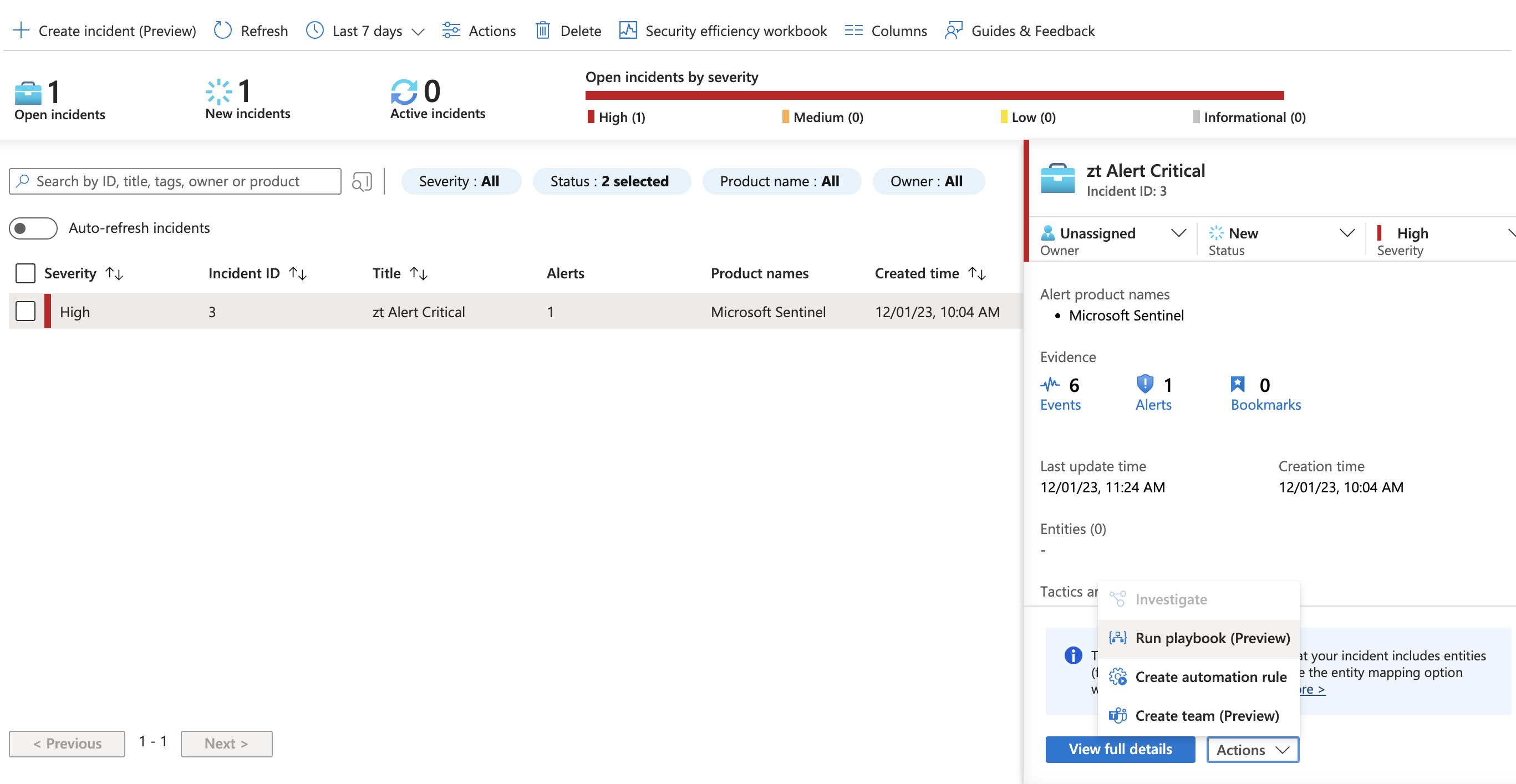
- Select the playbook for snapshot creation and click the run option and view the results to verify it completes correctly.
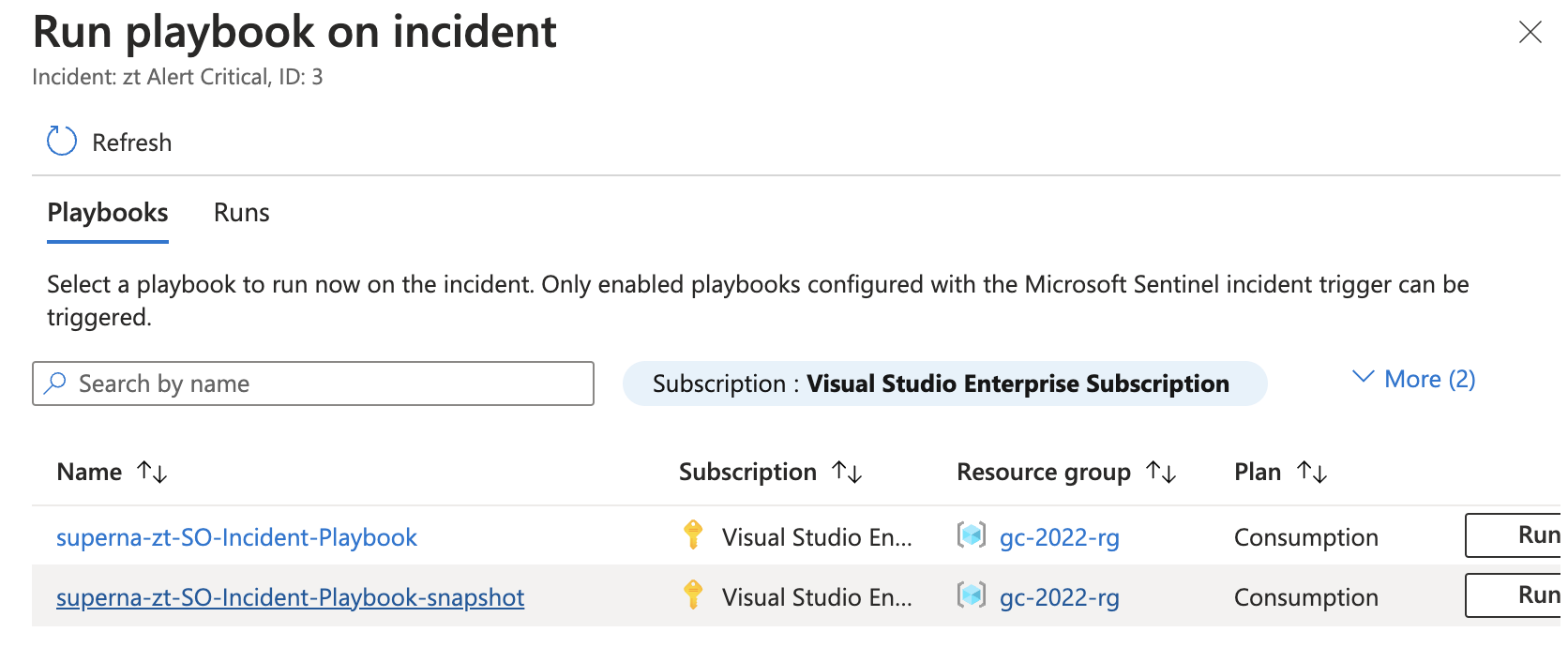
- Done.
Importing Logic App Playbooks into Sentinel
- Import Logic App Template Steps
- The steps below import a Logic app template that needs to be customized for your environment.
- Download this json template file for the Zero Trust Snapshot Playbook
- Download this json template file for the Zero Trust Lockout Playbook
- Login to Azure Console and enter 'Template Deployment' and select this option in the results.
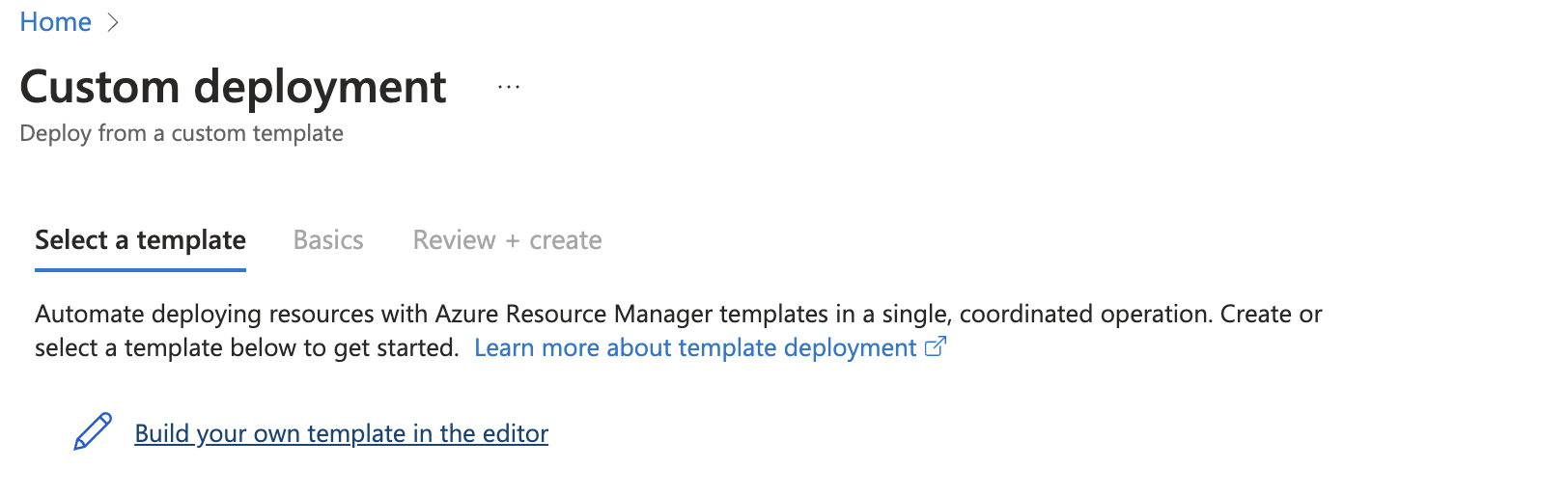
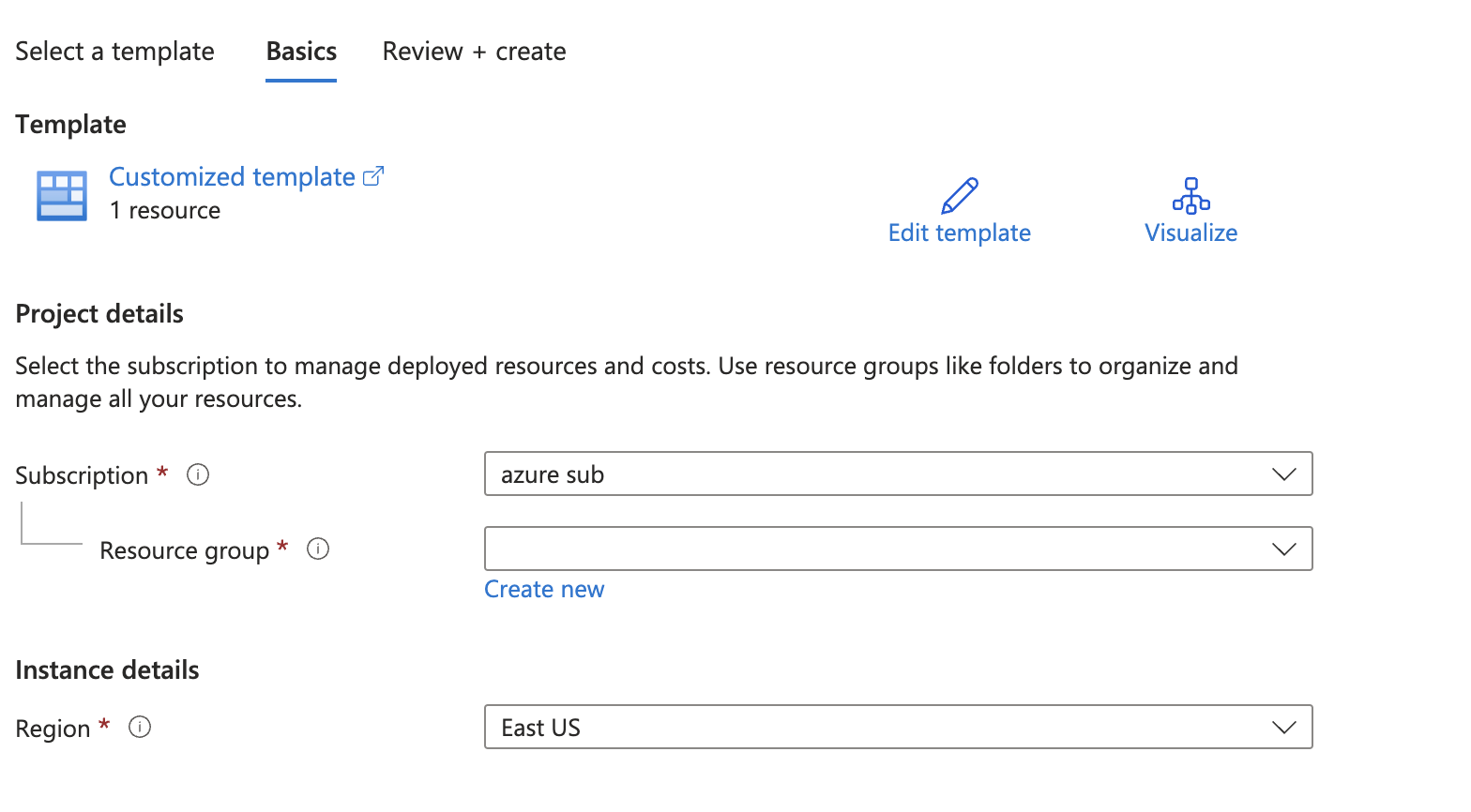
- Create a New Template Deployment
- select "Build your own template in the editor".
- Click "Load file" to upload the JSON file.
- After loading or pasting the template, click "Save".
- Fill in the subscription, resource group that is used for Sentinel and the region
- Click review and create to create the new "Incident Playbook"
- Done. See next step to configure it.