Securonix SIEM Zero Trust Alerts
- Overview
- Support Statement
- Limitations
- Solution Overview
- Advanced Zero Trust Capabilities
- What is Securonix SIEM?
- Integration Architecture
- Solution Configuration in Securonix SIEM and Defender Zero Trust
- Prerequisites
- Configuration in Securonix SIEM
- Configuration Steps on Eyeglass Virtual Machine
- High Level steps
- Configuration Step by Step
- Configure the Service start and python integration files
- Configure the python packages and customize the Securonix integration python code
- Configure Defender Zero Trust Webhooks
- How to test the Integration with Securonix SIEM
- Securonix SIEM SecOps administrators Integration Experience
Overview
Customers using Securonix SIEM solution can now leverage a native integration that initiates native ingestion API alerts from Security Editions zero trust alerts. Customers can augment the capabilities of Securonix SIEM with threat intelligence and Cyber Storage capabilities of Superna Security Edition.
Support Statement
-
NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
Limitations
- None
Solution Overview
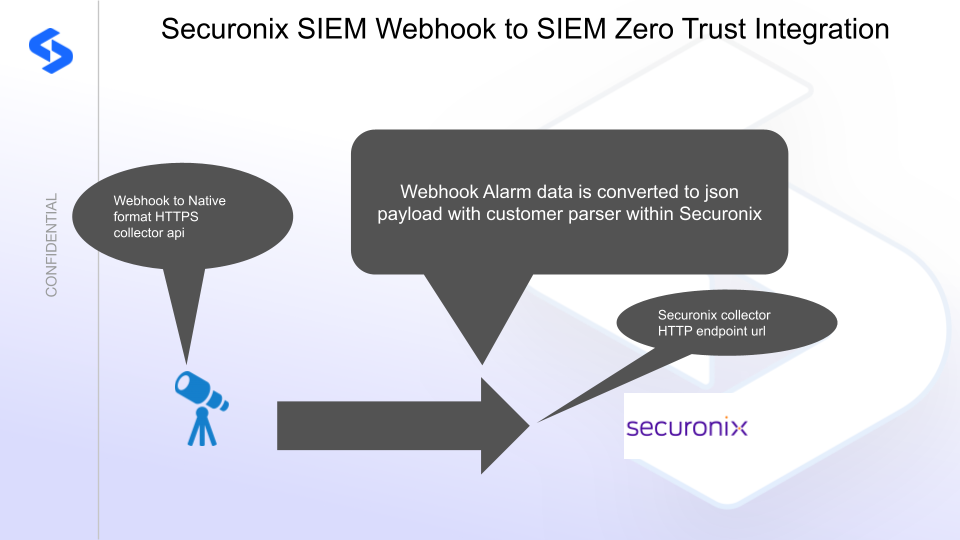
Superna Defender Zero Trust API receives webhook alerts and parses the key data into a HTTPS API payload events that are sent to the SIEM collector endpoint url. Securonix SIEM (Security Information and Event Management) is a modular architecture that provides real-time visibility of your IT infrastructure, which you can use for threat detection and prioritization.
Advanced Zero Trust Capabilities
- Webhook to native HTTPS collector API alarm integration
What is Securonix SIEM?
Integration Architecture
Solution Configuration in Securonix SIEM and Defender Zero Trust
Prerequisites
- Installed Security Edition
- Eyeglass OS appliance version 15.5
- cat /etc/os-release
- License key for the Zero Trust API
- Securonix SIEM
Configuration in Securonix SIEM
The steps below create a collector endpoint,
Steps to Create an Generic Webhook Cloud Collector
- Log in to Securonix SIEM Console
- Login to SNYPR
- Navigate to Menu > Add Data > Activity in the SNYPR application
- Click Add Data > Add Data for Supported Device Type to setup the ingestion process.
- Choose Vendors
- Click Vendor in the Resource Type Information section and select the following information:
- Vendors: Search for Superna.
- Resource Type: Search for Superna Eyeglass Zero Trust
- Parser Name: Select SCNX_SUPERN_SUPERNAEYEGLASSZEROTRUST_ZTS_HTT_JSO
- Create a resource group name and set the timezone, Source data name and set Authentication to Header based. Enter a header value that will be used to authenticate. This is an api key to access the endpoint.
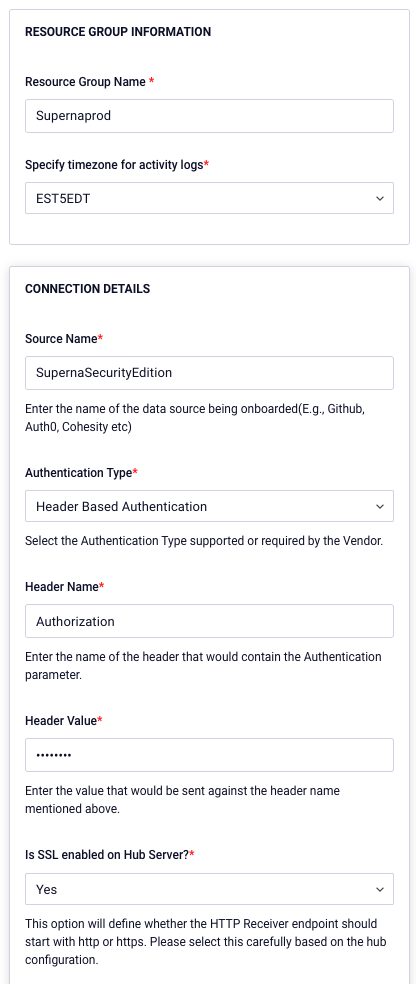
- Select Generate Receiver endpoint button.
- Record the URL and the header value to be used to update the integration below.
- Leave all other fields at the defaults
- Click Activate Event Receiver
- Click through Save & Next and update the receiver to complete the configuration.
- Consult with Securonix support on other none default tab configurations.
- Once test events are generated with the steps below you should be able to see parsed messages
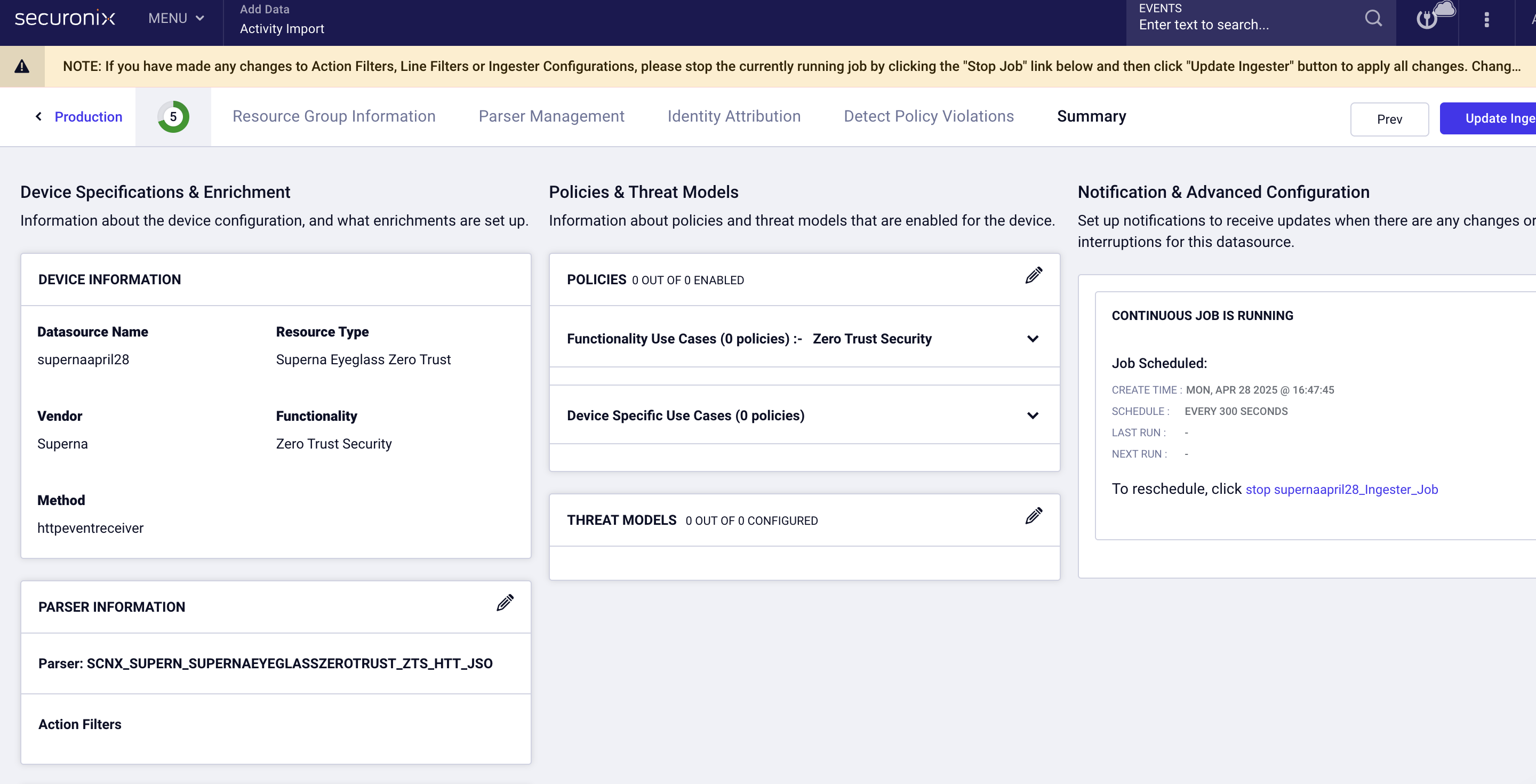
- The summary page should set the job interval to 300 seconds.
- done
Configuration Steps on Eyeglass Virtual Machine
High Level steps
- Create python location to run the application on the Eyeglass vm
- Create python main application script
- Create linux systemd service and set to auto start
- Create Zero Trust configuration in Defender
- Update the main script to customize with Securonix SIEM python code
- Test the script is running as a service
- Create a test event in Defender to validate the alerts appear as indexed parsed events in Securonix SIEM
Configuration Step by Step
Configure the Service start and python integration files
Configure the python packages and customize the Securonix integration python code
- Customize the application code by downloading the python code from this link to download
- Open the python template file in a text editor. NOTE: make sure to only replace the values and do not delete any of the commas
- Locate this section in the file and replace the yellow sections to match your securonix endpoint URL. The endpoint url is unique and can be copied from the console into the variable below.
- # Securonix HTTP Collector EndpointSecuronix_URL = "xxxxxxxx"Securonix_key = "yyyyyyy"
- nano /opt/superna/cgi-bin/securonix.py
- Open the file locally in Windows OS notepad and use control-A or select all the text in the python template
- Paste the clipboard into the ssh terminal session with the open nano editor file
- save the file
- press control+x
- Answer yes to save and exit the nano editor
- Start the service and verify it is running
- systemctl start securonix
- systemctl status -l securonix
- Verify the service is started successfully and returns "active and running".
- If the service does not start do not proceed and double check the steps above are completed.
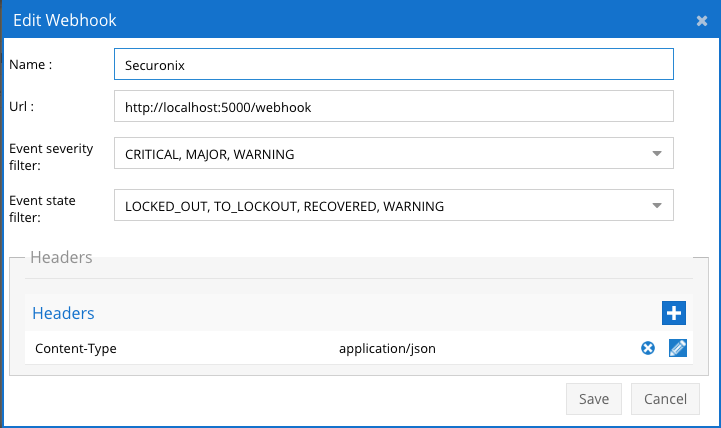
Configure Defender Zero Trust Webhooks
- The next step creates an Zero Trust Webhook URL.
- Configure Zero Trust endpoint in Ransomware Defender Zero Trust tab.
- Recommended Configuration: Only Critical and Major events and only the webhooks that set lockout or delayed lockout. Customers can customize based on specific requirements. The goal is to send findings versus a list of alarms that do not pinpoint a security incident.
- The endpoint url above will use localhost and will send Webhooks to the application service listening on port 5000. URL to use in the configuration
- http://localhost:5000/webhook
- Add the Content-Type header with value of application/json and the content-encoding with value gzip as shown above to complete the webhook configuration.
- Click save to commit the configuration.
- Click save on the main Webhook configuration page
- Recommended Configuration: Only Critical and Major events and only the webhooks that set lockout or delayed lockout. Customers can customize based on specific requirements. The goal is to send findings versus a list of alarms that do not pinpoint a security incident.
- Configure Zero Trust endpoint in Ransomware Defender Zero Trust tab.
- Test the configuration is working following the next section
How to test the Integration with Securonix SIEM
- To test the integration follow these steps
- Prerequisites In Securonix SIEMand Eyeglass:
- install the Securonix SIEMagent on a test machine. Record the ip address of this test machine.
- Get the ip address of the Eyeglass vm
- download this curl command template and open with a text editor and locate the ip address of eyeglass at the very end of text and replace the ip address with the IP address of your eyeglass vm.
- Copy all the text in the text editor
- ssh to the eyeglass vm as the admin user
- Paste the entire cli command text to the ssh prompt to send sample data to the running Zero Trust application. This will send test data directly to the application to be processed and sent to Securonix SIEM Integration service that is running on the Eyeglass VM.
- The output of a successfully processed webhook test will return this text in the ssh terminal
- done sending event to securonix and check for http 200 and success count in response
- How to review the process logs from the web application
- sudo -s
- journalctl -f -u securonix
- This allows you to view the logs generated by the application.
- To log to a file and review with nano showing only the most recent 250 lines.
- journalctl -f -n 250 -u securonix > /tmp/securonix.log
- nano /tmp/securonix.log
- In the log below the response code from the Securonix SIEM api call should show http 200 status code and successCount 1 to indicate the Finding was successfully created.
- You can also view securonix.log for specific error messages.
- Done
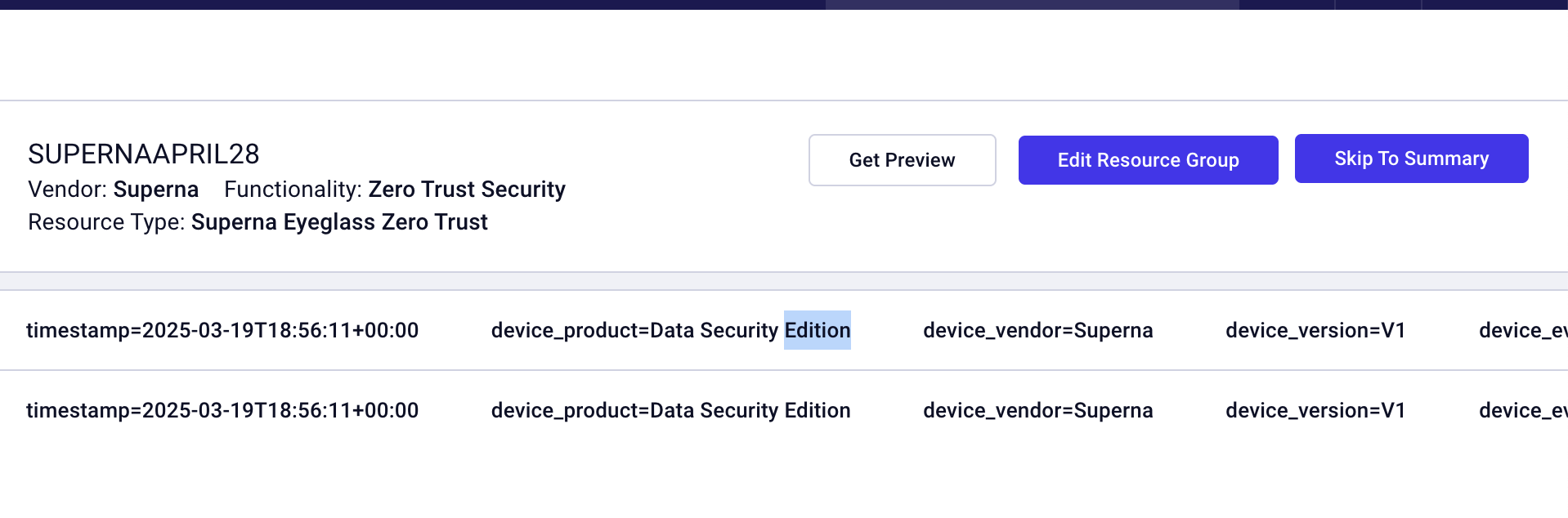
Securonix SIEM SecOps administrators Integration Experience
Example parsed results after an alert is sent to the collector endpoint url and parsed.