Eyeglass Solutions Publication
Sophos Extended Detection and Response XDR Integration Zero Trust Alerting
Home
What is Sophos Extended Detection and Response?
- Overview
- Limitations
- Solution Overview
- Video Demo
- Advanced Zero Trust Capabilities
- What is Sophos Extended Detection and Response?
- Integration Architecture
- Solution Configuration in Sophos Extended Detection and Response and Data Security Edition Zero Trust
- Prerequisites
- Configuration in Sophos Extended Detection and Response
- Configuration Steps on Eyeglass Virtual Machine
- High Level steps
- Configuration Step by Step
- Configure the Service start and python integration files
- Configure the python packages and customize the Sophos Extended Detection and Response integration python code
- Configure Defender Zero Trust Webhooks
- How the Integration works Sophos Extended Detection and Response
- How to test the Integration with Sophos Extended Detection and Response
- Sophos Extended Detection and Response SecOps administrators Integration Experience
Overview
Customers using Sophos Extended Detection and Response XDR can now leverage a native integration that ingests root cause Cyberstorage events to show as Security events .
-
NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
Limitations
- None
Solution Overview
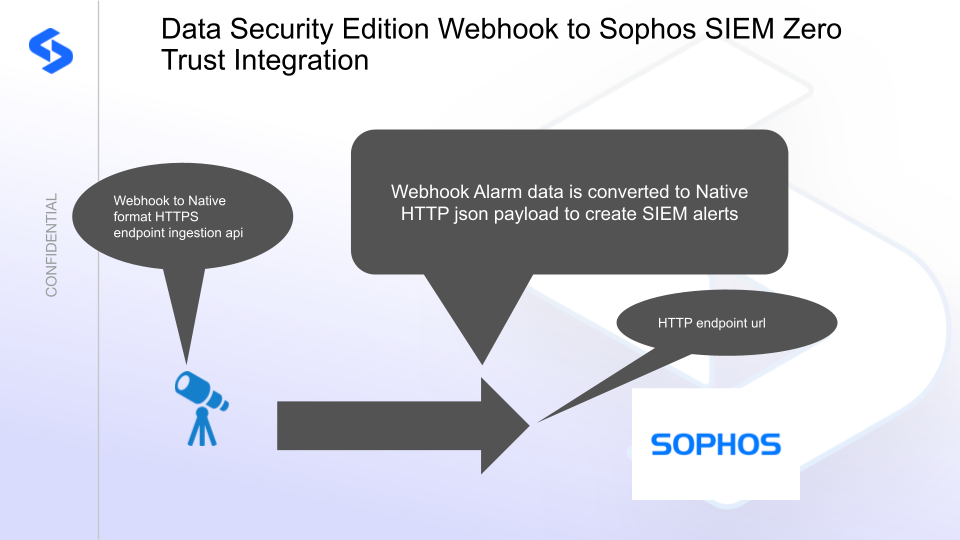
Superna Defender Zero Trust API receives webhook alerts from Security Edition and maps all relevant data fields into the Sophos XDR with a json custom parsing configuration.
Video Demo
Advanced Zero Trust Capabilities
- Webhook to native Sophos Extended Detection and Response SIEM ingestion API and log parsing
- Superna Security Edition host Containment API integration with Sophos Extended Detection and Response
What is Sophos Extended Detection and Response?
A cybersecurity platform that correlates security data from various sources like endpoints, servers, firewalls, and cloud environments to provide a holistic view for detecting, investigating, and responding to threats
Integration Architecture
Solution Configuration in Sophos Extended Detection and Response and Data Security Edition Zero Trust
Prerequisites
- Installed Security Edition
- Eyeglass OS appliance version 15.5
- cat /etc/os-release
- License key for the Zero Trust API
- Sophos Extended Detection and Response HTTP endpoint data source
Configuration in Sophos Extended Detection and Response
- Create an http ingest cloud endpoint by following the steps here (https://docs.taegis.secureworks.com/integration/connectCloud/http_ingest/)
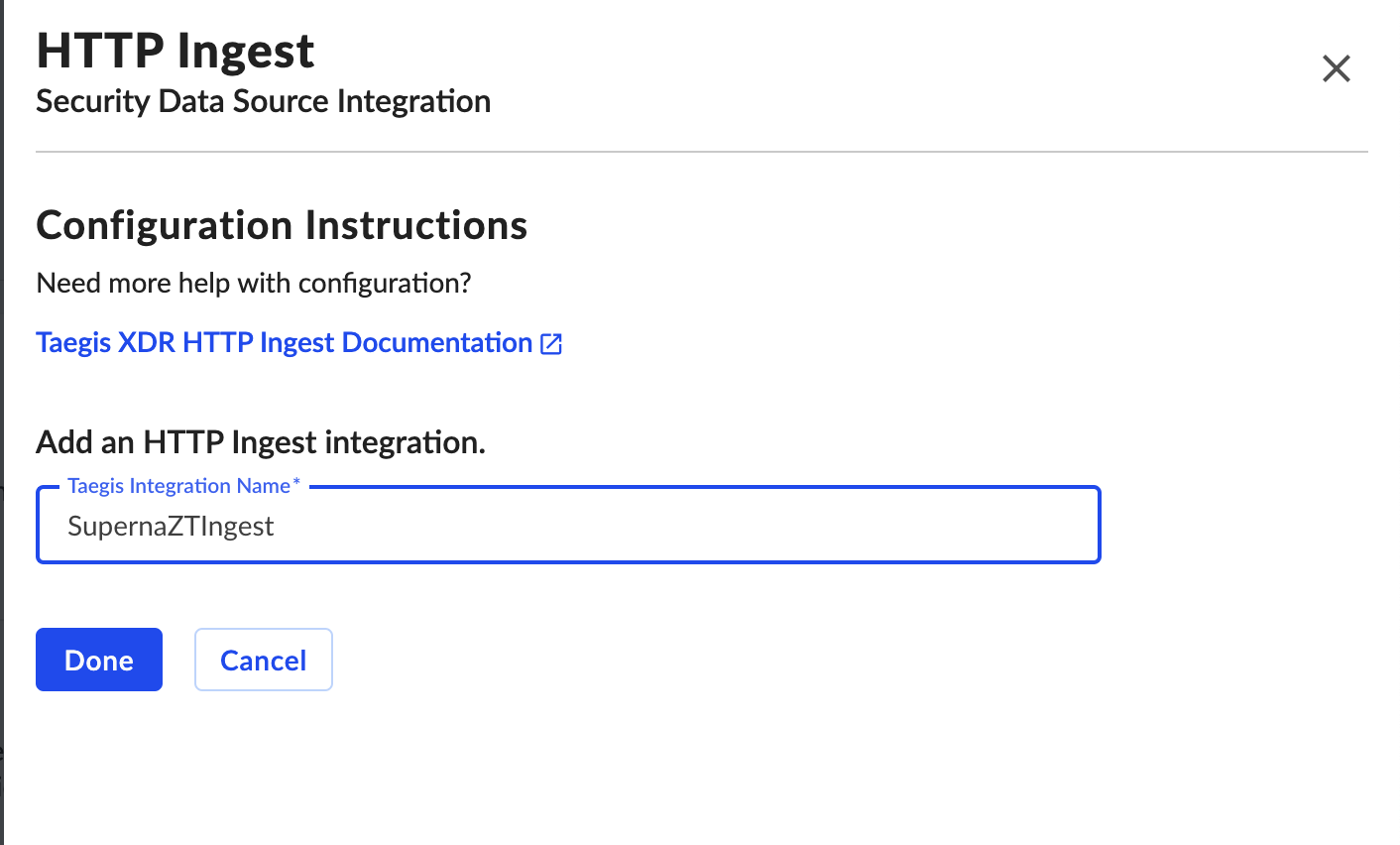
- Record the URL and API key for use later
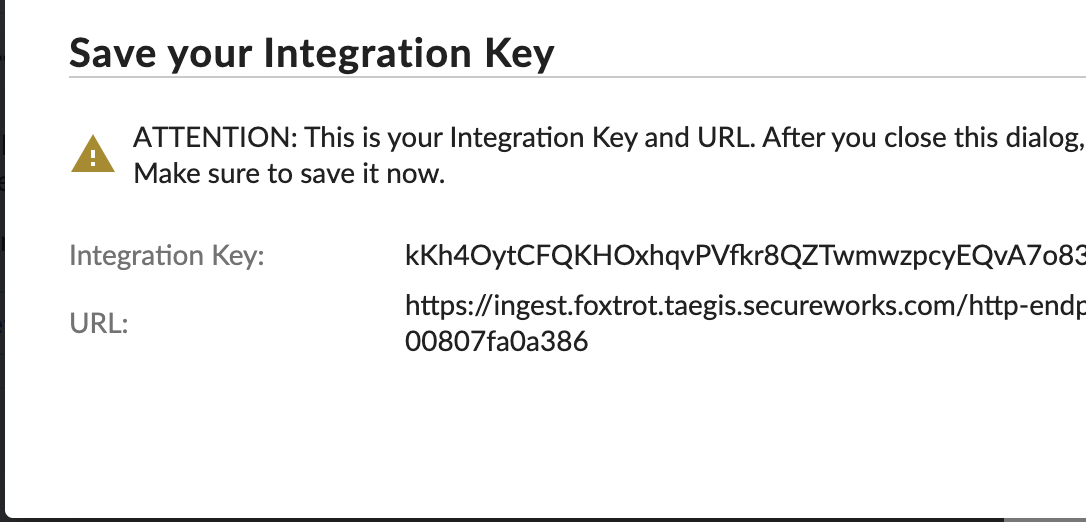
- The Taegis platform from Sophos has a Superna parser builtin to the platform that will recognize the Superna payload and automatically parse the payload and maps the fields.
- Done.
Configuration Steps on Eyeglass Virtual Machine
High Level steps
- Create python location to run the application on the Eyeglass vm
- Create python main application script
- Create linux systemd service and set to auto start
- Create Zero Trust configuration in Defender
- Update the main script to customize with Sophos Extended Detection and Response python code
- Test the script is running as a service
- Create a test event in Defender to validate the alerts appear as indexed parsed events in Sophos Extended Detection and Response
Configuration Step by Step
Configure the Service start and python integration files
# Sophos Integration Deployment Instructions
Login to the Eyeglass VM via SSH as the admin user:
ssh admin@<your-vm-ip>
# Become root
sudo -s
mkdir -p /opt/superna/cgi-bin
chown -R sca:users /opt/superna/cgi-bin
chmod -R u+rwX,g+rwX /opt/superna/cgi-bin
# Switch to the SCA user
sudo -u sca -s
cd /opt/superna/cgi-bin
# Create Python virtual environment for the integration
python3 -m venv venv-sophos
source venv-sophos/bin/activate
# Install required Python packages
pip install pprint flask boto3 requests logging socket json
deactivate
# Create integration script files
touch sophos.py
touch sophos.sh
chmod +x sophos.py
chmod +x sophos.sh
# Create the sophos.sh launch script
nano /opt/superna/cgi-bin/sophos.sh
# Paste the following into the file:
#!/bin/bash
export PATH="/opt/.pyenv/bin:$PATH"
source /opt/superna/cgi-bin/venv-sophos/bin/activate
exec python /opt/superna/cgi-bin/sophos.py
# Make the script executable
chmod +x /opt/superna/cgi-bin/sophos.sh
# Exit back to root
exit
whoami # confirm you are root
# Create the systemd service unit file
nano /etc/systemd/system/sophos.service
# Paste the following into the file:
[Unit]
Description=Webhook listener for Zero Trust API translations and integrations
After=network.target
[Service]
Type=simple
User=sca
Group=users
WorkingDirectory=/opt/superna/cgi-bin
ExecStart=/bin/bash /opt/superna/cgi-bin/sophos.sh
Restart=always
RestartSec=5
[Install]
WantedBy=multi-user.target
# Reload systemd to register the new service
systemctl daemon-reload
# Enable the service to start on boot (do NOT start it yet)
systemctl enable sophos
Configure the python packages and customize the Sophos Extended Detection and Response integration python code
- Customize the application code by downloading the python code from this link to download
- Open the python template file in a text editor. NOTE: make sure to only replace the values and do not delete any of the commas
- Locate this section in the file # Define the endpoint and API token as variables to add your Sophos Extended Detection and Response api token and endpoint for API calls .
- Add the API URL and API token into this section.
- Secureworks_URL = "https://xxxxxxx"Secureworks_key = "yyyyyy"
- nano /opt/superna/cgi-bin/sophos.py
- Open the file locally in Windows OS notepad and use control-A or select all the text in the python template
- Paste the clipboard into the ssh terminal session with the open nano editor file
- save the file
- press control+x
- Answer yes to save and exit the nano editor
- Start the service and verify it is running
- systemctl start sophos
- systemctl status -l sophos
- Verify the service is started successfully and returns "active and running".
- If the service does not start do not proceed and double check the steps above are completed.
Configure Defender Zero Trust Webhooks
- The next step creates an Zero Trust Webhook URL.
- Configure Zero Trust endpoint in Ransomware Defender Zero Trust tab.
- Recommended Configuration: Only Critical and Major events and only the webhooks that set lockout or delayed lockout. Customers can customize based on specific requirements. The goal is to send findings versus a list of alarms that do not pinpoint a security incident.
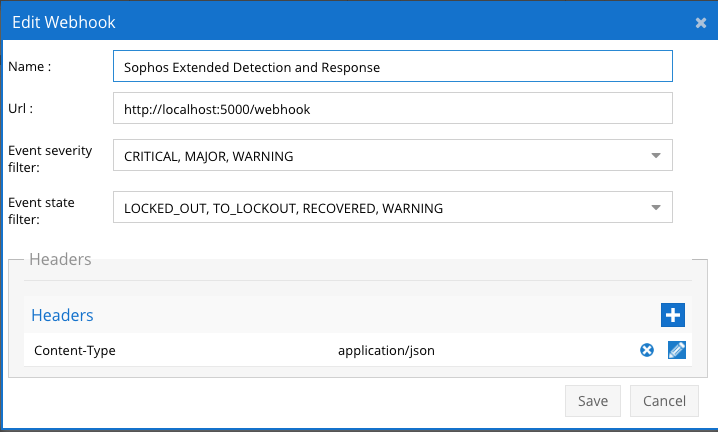
- The endpoint url above will use localhost and will send Webhooks to the application service listening on port 5000. URL to use in the configuration
- http://localhost:5000/webhook
- Add the Content-Type header with value of application/json as shown above to complete the webhook configuration.
- Click save to commit the configuration.
- Click save on the main Webhook configuration page
- Configure Zero Trust endpoint in Ransomware Defender Zero Trust tab.
- Test the configuration is working following the next section
How the Integration works Sophos Extended Detection and Response
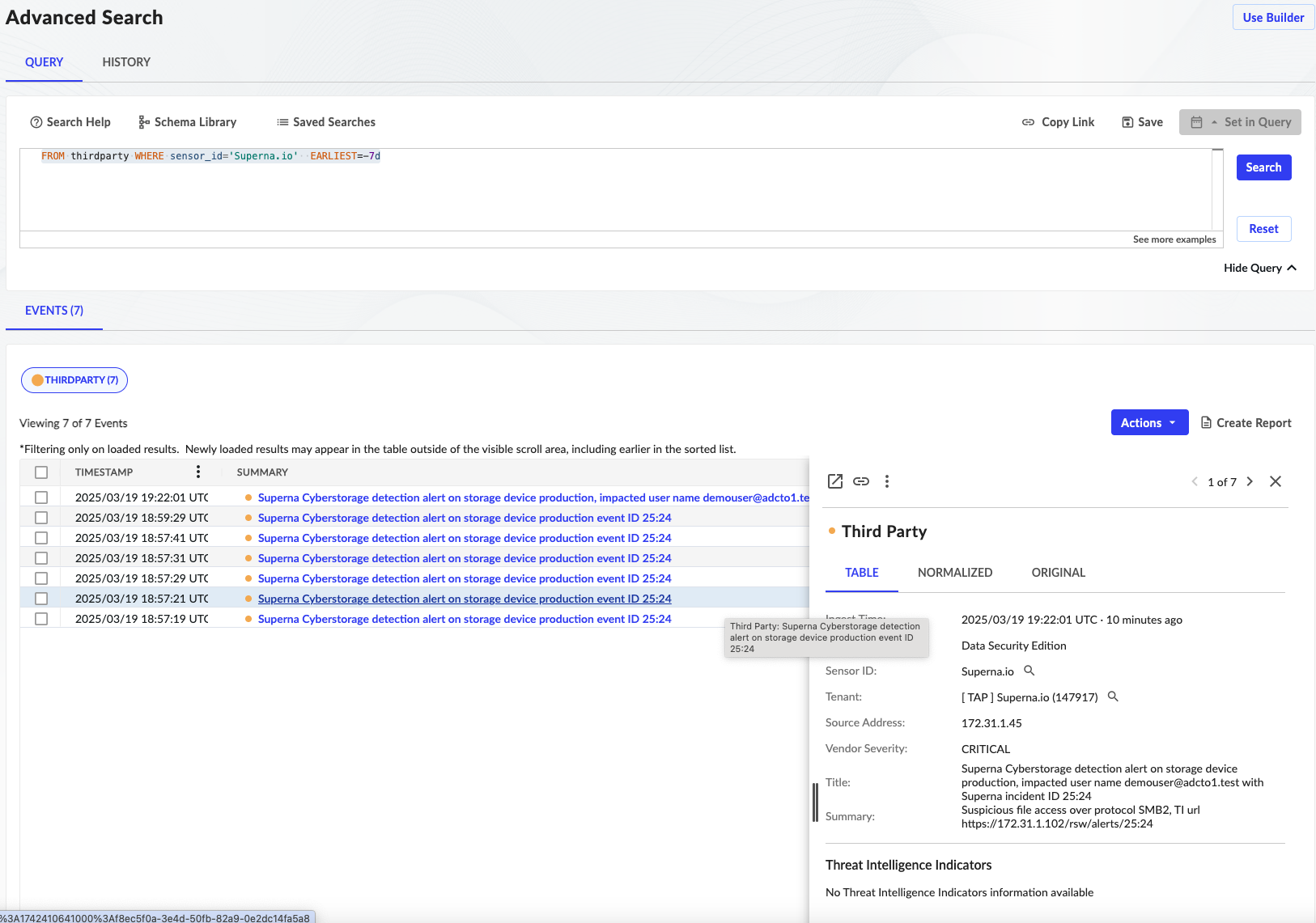
- After the integration is completed security events will be sent to the HTTP endpoint and parsed by the parser mapping key fields to the thirdparty schema. The events will be found by searching with the following syntax.
- Syntax of the search for the last 7 days: FROM thirdparty WHERE sensor_id='Superna.io' EARLIEST=-7d
- See the steps below to create test events.
- Syntax of the search for the last 7 days: FROM thirdparty WHERE sensor_id='Superna.io' EARLIEST=-7d
- Now you can configure rules to create investigations based on the sensor ID. See the section below.
How to test the Integration with Sophos Extended Detection and Response
- To test the integration follow these steps
- Prerequisites In Sophos Extended Detection and Response and Eyeglass:
- download this curl command template and open with a text editor and locate the ip address of eyeglass at the very end of text and replace the ip address with the IP address of your eyeglass vm.
- Also edit the client ip section of the curl command by searching the text clientIPs":["172.31.1.45"] and replace only the ip address with the IP of the test machine running the Sophos Extended Detection and Response agent.
- Edit the section below and add the client_id and client_secret with values from the Sophos Extended Detection and Response Console.
- # Your Sophos Extended Detection and Response API credentialsSecureworks_URL = 'xxxxx'Secureworks_key = 'yyyyyy'
- Update the base url if needed.
- # The API base URL for Sophos Extended Detection and Responsebase_url = "https://api.us-2.Sophos Extended Detection and Response.com"
- This will now simulate a zero trust alert on this host when the curl command sends the webhook payload to the integration python code to process.
- Copy all the text in the text editor
- ssh to the eyeglass vm as the admin user
- Paste the entire cli command text to the ssh prompt to send sample data to the running Zero Trust application. This will send test data directly to the application to be processed and sent to Sophos Extended Detection and Response Integration service that is running on the Eyeglass VM.
- The output of a successfully processed webhook test will return this text in the ssh terminal
- done sending event to sophos and check for http 200 and success count in response
- How to review the process logs from the web application
- sudo -s
- journalctl -f -u sophos
- This allows you to view the logs generated by the application.
- To log to a file and review with nano showing only the most recent 250 lines.
- journalctl -f -n 250 -u sophos > /tmp/ztwebhook.log
- nano /tmp/sophos.log
- In the log below the response code from the Sophos Extended Detection and Response api call should show http 200 status code and success Count 1 to indicate the Finding was successfully created.
- You can also view sophos.log for specific error messages.
- Login to the Sophos Extended Detection and Response and verify new incident is raised.
- download this curl command template and open with a text editor and locate the ip address of eyeglass at the very end of text and replace the ip address with the IP address of your eyeglass vm.
- Done
Sophos Extended Detection and Response SecOps administrators Integration Experience
Overview: This covers some functions of the Sophos Extended Detection and Response solution that allows for Incident Response based on 3rd party event parsing.
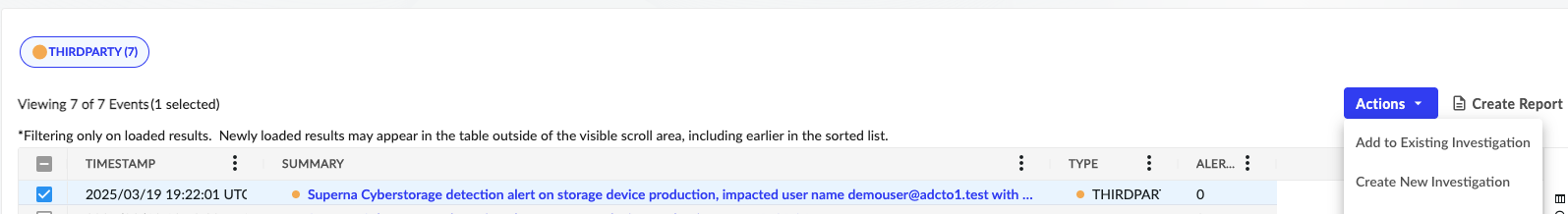
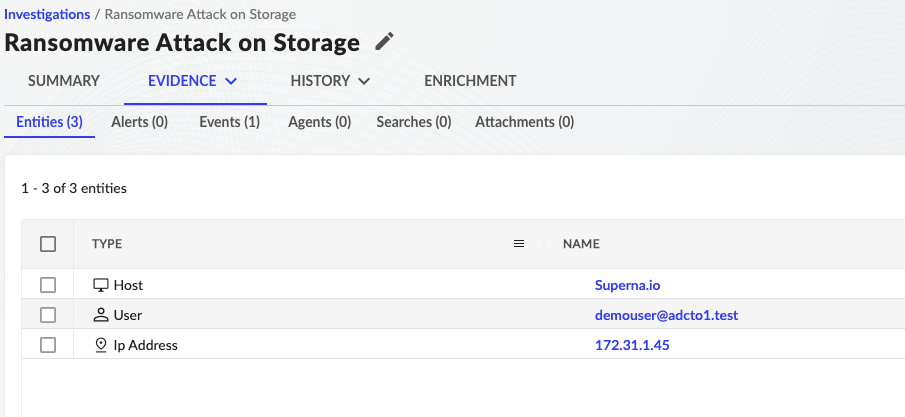
- The event schema is mapping allowing for seamless Investigations with all nessessary evenidence populationed. From the advanced search interface an log entry can be selected and select action to create an investigation.
- Click on the Investigations tab or view investigation after it is submitted.
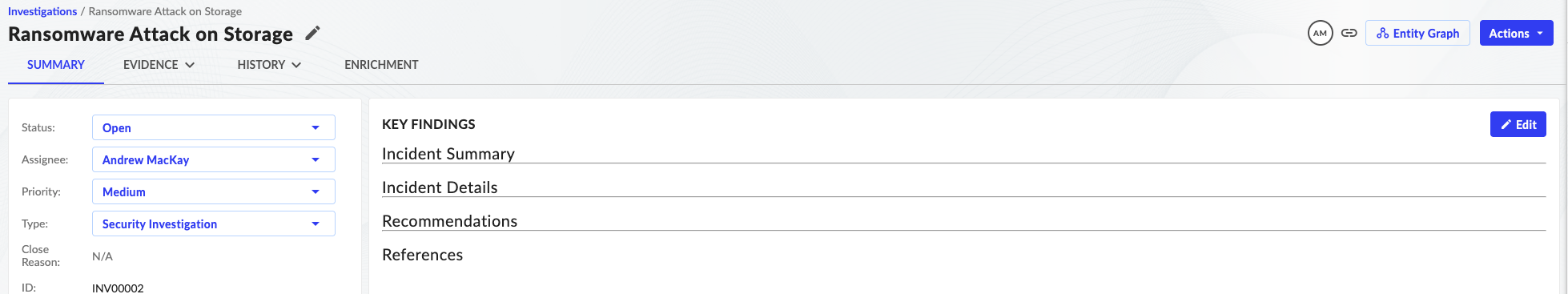
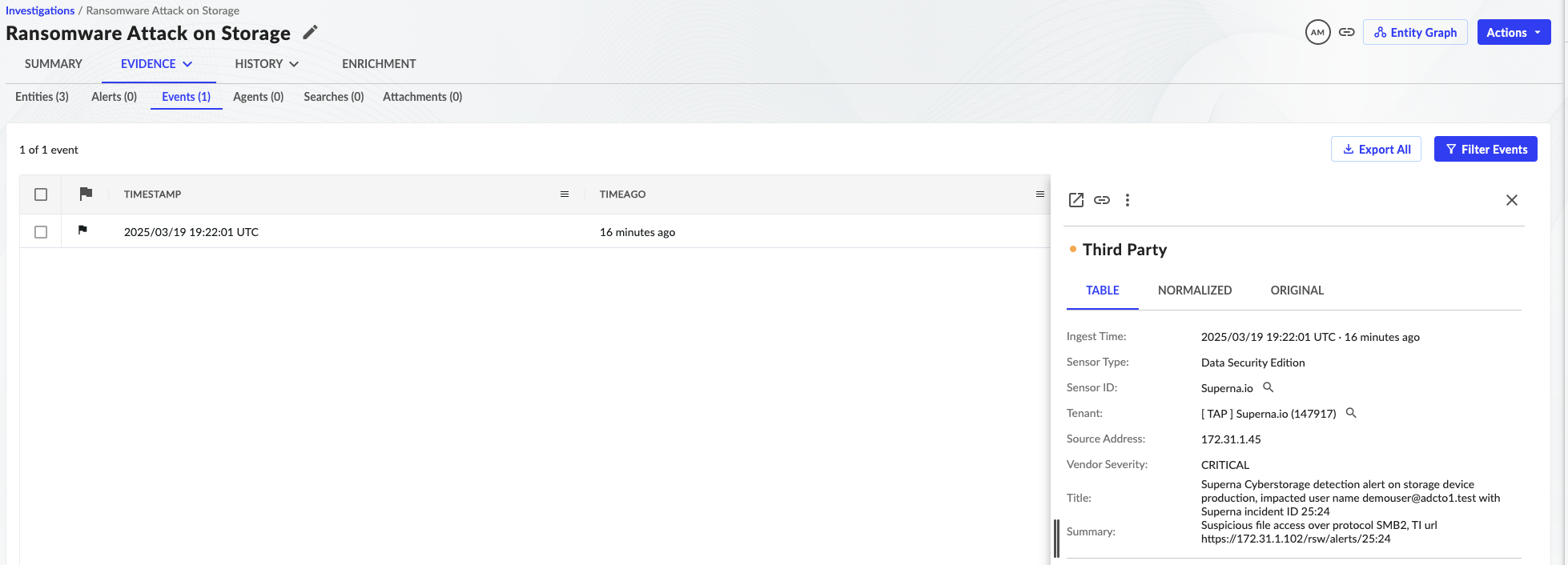
- Click on the Evidence Tab
- The key host, user and IP information is populated to allow further investigation with other tools like Vulnerablity Scanners or Endpoint protection security tools. The impacted user is listed for automated actions to disable the account.
- Click on the Events tab to review details of the incoming event.
- To investigate the details of the Threat Intelligence copy and paste the TI url into a new tab and login to Data Security Edition to view the details of the incident including snapshots the list of files, SMB/NFS shares.