ManageEngine SIEM Log360 Zero Trust Alarm Integration SYSLOG
- Overview
- Support Statement
- Limitations
- Solution Overview
- Advanced Zero Trust Capabilities
- What is ManageEngine SIEM Log360?
- Integration Architecture
- Solution Configuration in ManageEngine SIEM Log360and Defender Zero Trust
- Prerequisites
- Configuration in ManageEngine SIEM Log360
- Configuration Steps on Eyeglass Virtual Machine
- High Level steps
- Configuration Step by Step
- Configure the Service start and python integration files
- Configure the python packages and customize the log360 integration python code
- Configure Defender Zero Trust Webhooks
- How to test the Integration with ManageEngine SIEM Log360
- ManageEngine SIEM Log360 SecOps administrators Integration Experience
Overview
Customers using ManageEngine SIEM Log360 solution can now leverage a native integration that initiates native ingestion API alerts from Security Editions zero trust alerts. Customers can augment the capabilities of ManageEngine SIEM Log360with threat intelligence and Cyber Storage capabilities of Superna Security Edition.
Support Statement
-
NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
Limitations
- None
Solution Overview
Superna Defender Zero Trust API receives webhook alerts and parses the key data into a syslog UDP or TCP event that is sent to log360. ManageEngine SIEM Log360 (Security Information and Event Management) is a modular architecture that provides real-time visibility of your IT infrastructure, which you can use for threat detection and prioritization.
Advanced Zero Trust Capabilities
- Webhook to native syslog alarm integration
What is ManageEngine SIEM Log360?
Integration Architecture
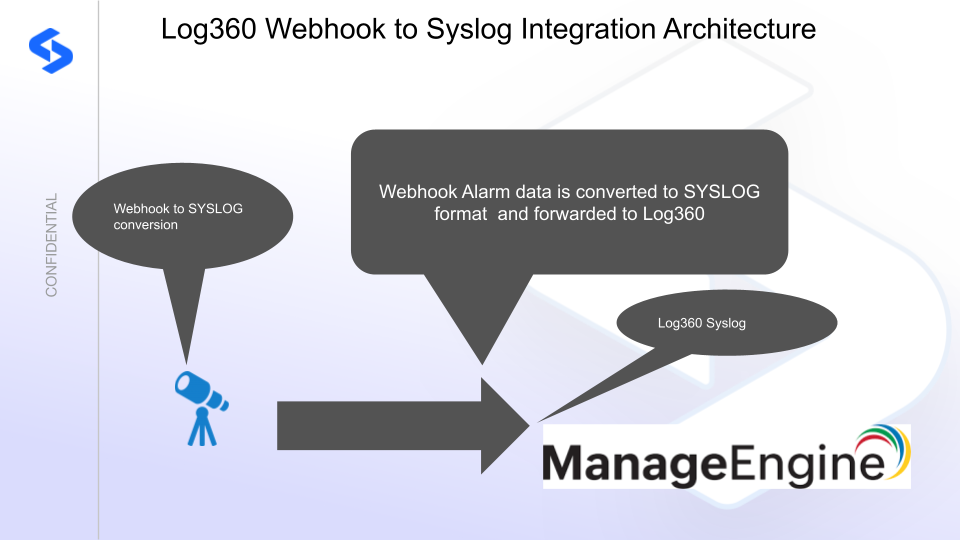
Solution Configuration in ManageEngine SIEM Log360and Defender Zero Trust
Prerequisites
- Installed Security Edition
- Eyeglass OS appliance version 15.5
- cat /etc/os-release
- License key for the Zero Trust API
- ManageEngine SIEM Log360
Configuration in ManageEngine SIEM Log360
The steps below create a custom log parsing rule and
- Login to your Log360 UI to Create a custom parsing rule
- SIEM --> Settings --> Custom log Format
- Click Add log format and Type Superna
- Now click Manage Parse Rules
- Add parser rule
- Rule name Superna and method Delimiter with delimiter as comma

- Download the text from this link (right click download as file) and Open the file and copy all the text and paste into the left hand box under the Log heading and click Save. (NOTE the parsing and delimiter values must be set correctly for auto field extraction to work correctly.)
- You will see fields in the right hand window to assign field names as follows below. Enter the field names exactly as shown.
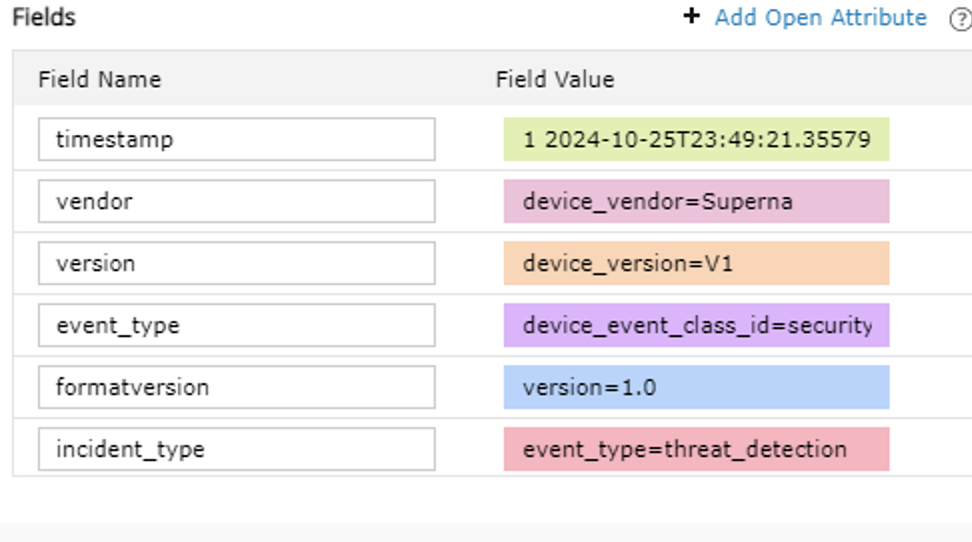
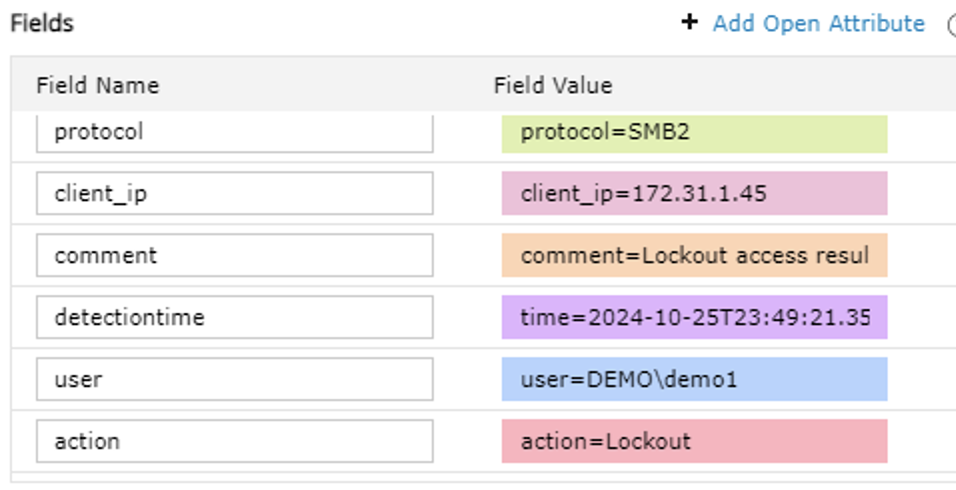
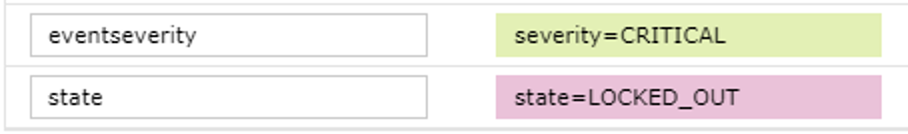
- Click Save rule
- The custom parsing rule step is now complete.
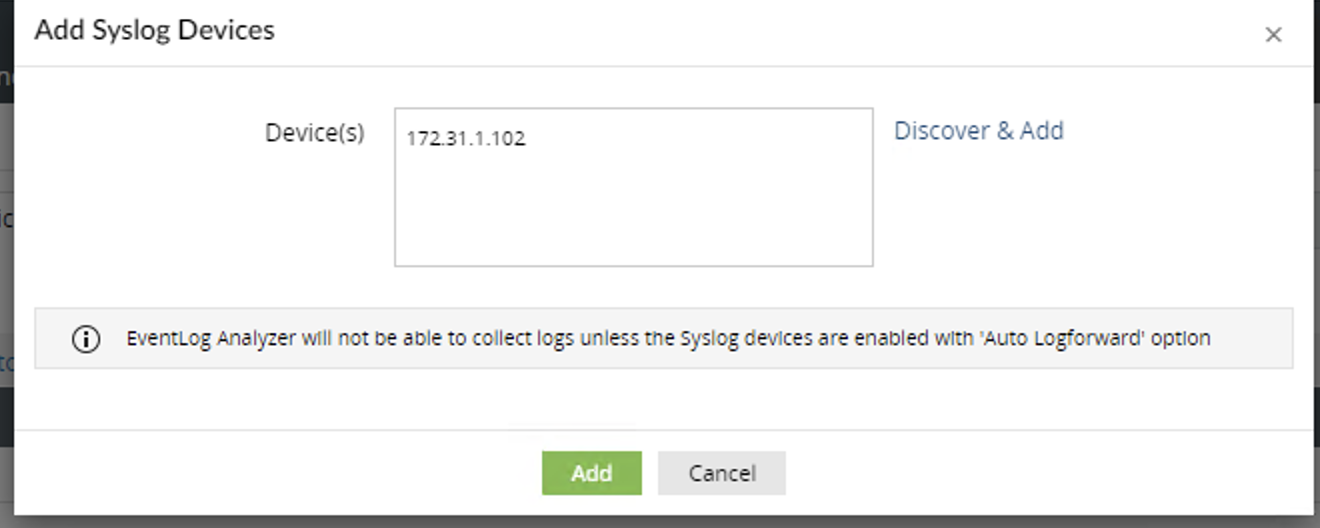
- SIEM --> Settings --> Device Management --> Syslog devices
- Follow the steps below to send test UDP events to leverage auto device configuration for auto device discovery. Once events are viewed in the Event Receiver viewer the syslog device should appear automatically. The ip address will be listed if reverse DNS lookup fails.
- To manually add the eyeglass device, you can use the following steps. Only use one method to register the device.
- Go to devices

- Add Device for syslog devices
- Add the Eyeglass ip and click Add
- Go to devices
- Now edit the device in the SIEM settings section to update the log type to the custom parsing log format created above.
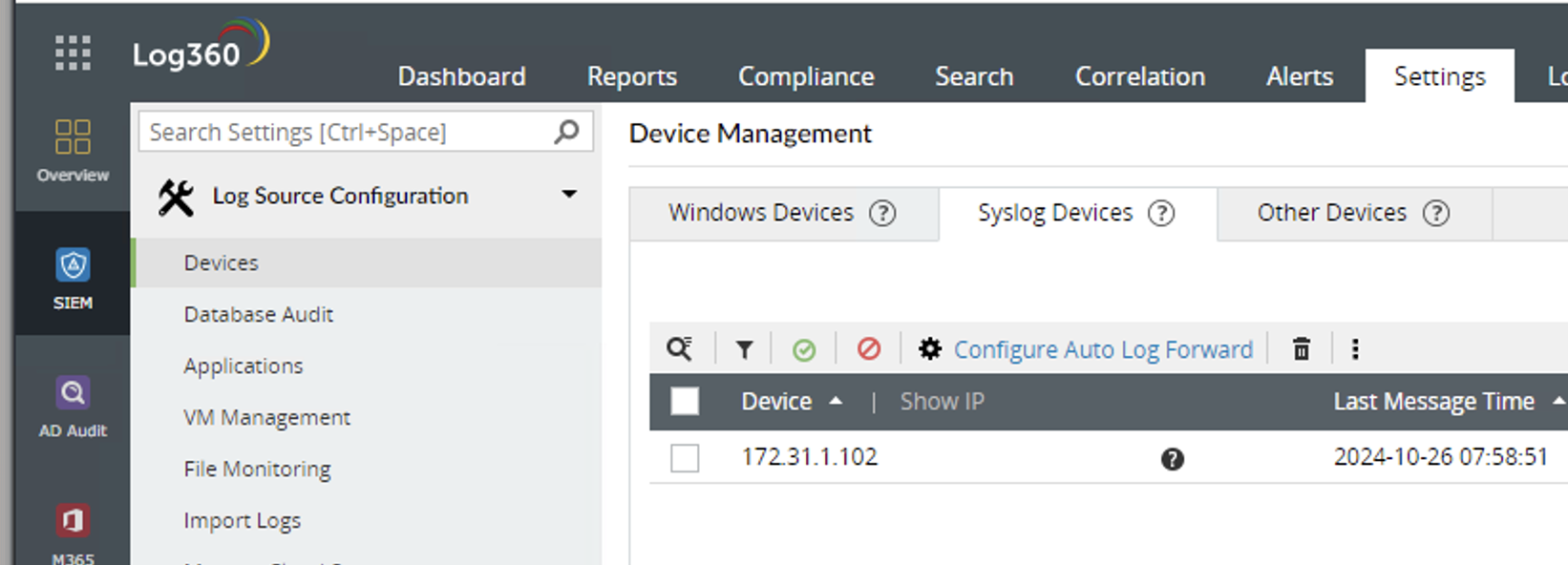
- Set the log type to Superna custom to ensure the log parsing is applied to all logs for the Eyeglass vm. The custom log parsing
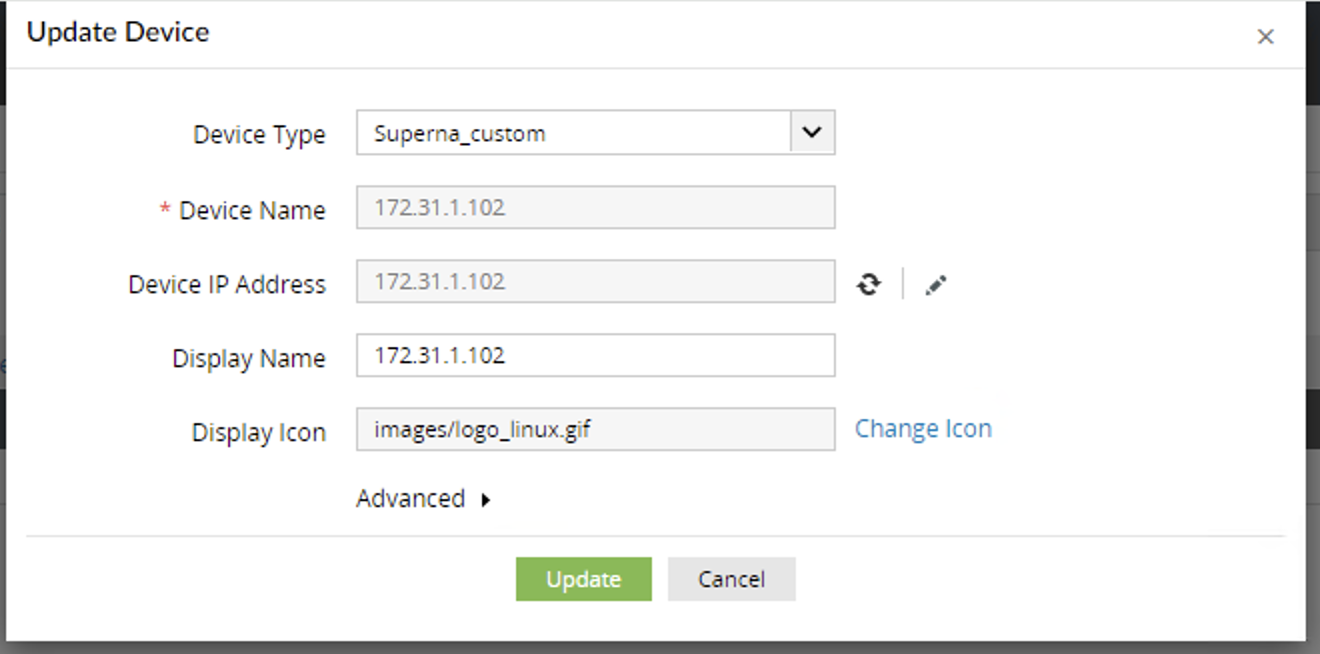
- Update the device
- Log parsing configuration steps are completed. Logs sent from the integration will now be parsed correctly.
Configuration Steps on Eyeglass Virtual Machine
High Level steps
- Create python location to run the application on the Eyeglass vm
- Create python main application script
- Create linux systemd service and set to auto start
- Create Zero Trust configuration in Defender
- Update the main script to customize with ManageEngine SIEM Log360 python code
- Test the script is running as a service
- Create a test event in Defender to validate the alerts appear as indexed parsed events in ManageEngine SIEM Log360
Configuration Step by Step
Configure the Service start and python integration files
Configure the python packages and customize the log360 integration python code
- Customize the application code by downloading the python code from this link to download
- Open the python template file in a text editor. NOTE: make sure to only replace the values and do not delete any of the commas
- Locate this section in the file and replace the yellow sections to match your log360 endpiont ip address, port and set TCP flag to false if you need UDP.
- SYSLOG_SERVER = 'x.x.x.x' # Replace with your syslog server addressSYSLOG_PORT = 514 # Replace with your syslog server portFACILITY = 13 # Facility code for security audit logSEVERITY = 2 # Severity level for critical messagesUSE_TCP = False # Set this flag to True for TCP, False for UDP
-
- nano /opt/superna/cgi-bin/log360.py
- Open the file locally in Windows OS notepad and use control-A or select all the text in the python template
- Paste the clipboard into the ssh terminal session with the open nano editor file
- save the file
- press control+x
- Answer yes to save and exit the nano editor
- Start the service and verify it is running
- systemctl start log360
- systemctl status -l log360
- Verify the service is started successfully and returns "active and running".
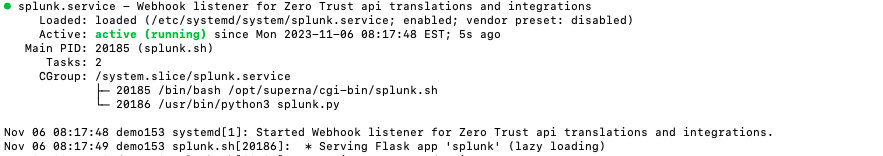
- If the service does not start do not proceed and double check the steps above are completed.
Configure Defender Zero Trust Webhooks
- The next step creates an Zero Trust Webhook URL.
- Configure Zero Trust endpoint in Ransomware Defender Zero Trust tab.
- Recommended Configuration: Only Critical and Major events and only the webhooks that set lockout or delayed lockout. Customers can customize based on specific requirements. The goal is to send findings versus a list of alarms that do not pinpoint a security incident.
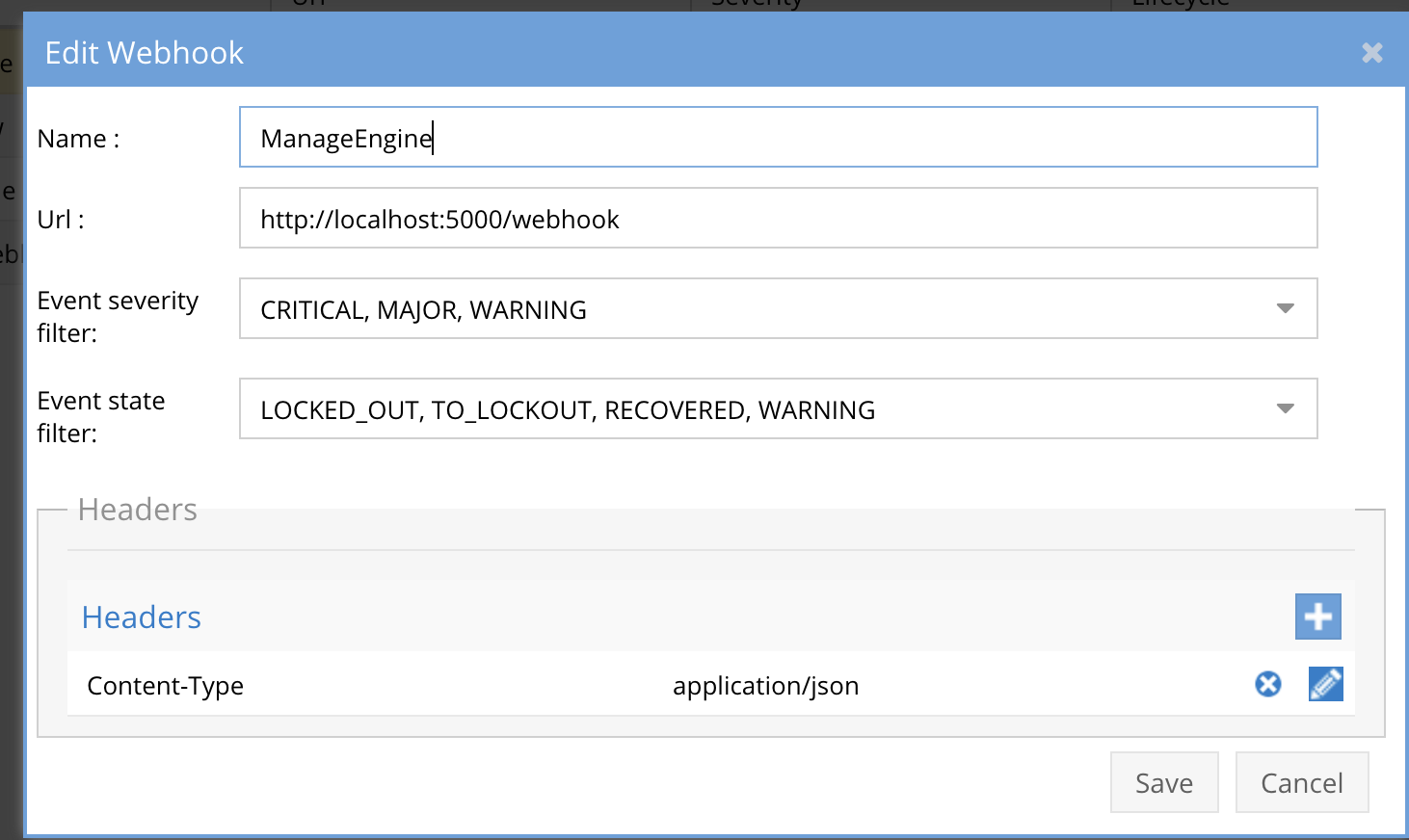
- The endpoint url above will use localhost and will send Webhooks to the application service listening on port 5000. URL to use in the configuration
- http://localhost:5000/webhook
- Add the Content-Type header with value of application/json as shown above to complete the webhook configuration.
- Click save to commit the configuration.
- Click save on the main Webhook configuration page
- Configure Zero Trust endpoint in Ransomware Defender Zero Trust tab.
- Test the configuration is working following the next section
How to test the Integration with ManageEngine SIEM Log360
- To test the integration follow these steps
- Prerequisites In ManageEngine SIEM Log360and Eyeglass:
- install the ManageEngine SIEM Log360agent on a test machine. Record the ip address of this test machine.
- Get the ip address of the Eyeglass vm
- download this curl command template and open with a text editor and locate the ip address of eyeglass at the very end of text and replace the ip address with the IP address of your eyeglass vm.
- Also edit the client ip section of the curl command by searching the text clientIPs":["172.31.1.45"] and replace only the ip address with the IP of the test machine running the ManageEngine SIEM Log360agent.
- This will now simulate a zero trust alert on this host when the curl command sends the webhook payload to the integration python code to process.
- Copy all the text in the text editor
- ssh to the eyeglass vm as the admin user
- Paste the entire cli command text to the ssh prompt to send sample data to the running Zero Trust application. This will send test data directly to the application to be processed and sent to ManageEngine SIEM Log360Integration service that is running on the Eyeglass VM.
- The output of a successfully processed webhook test will return this text in the ssh terminal
- done sending event to log360 and check for http 200 and success count in response
- How to review the process logs from the web application
- sudo -s
- journalctl -f -u log360
- This allows you to view the logs generated by the application.
- To log to a file and review with nano showing only the most recent 250 lines.
- journalctl -f -n 250 -u log360 > /tmp/log360.log
- nano /tmp/log360.log
- In the log below the response code from the ManageEngine SIEM Log360 api call should show http 200 status code and successCount 1 to indicate the Finding was successfully created.
- You can also view log360.log for specific error messages.
- Login to the ManageEngine SIEM Log360 and verify lot events can be seen in the log event viewer
- Done
ManageEngine SIEM Log360 SecOps administrators Integration Experience
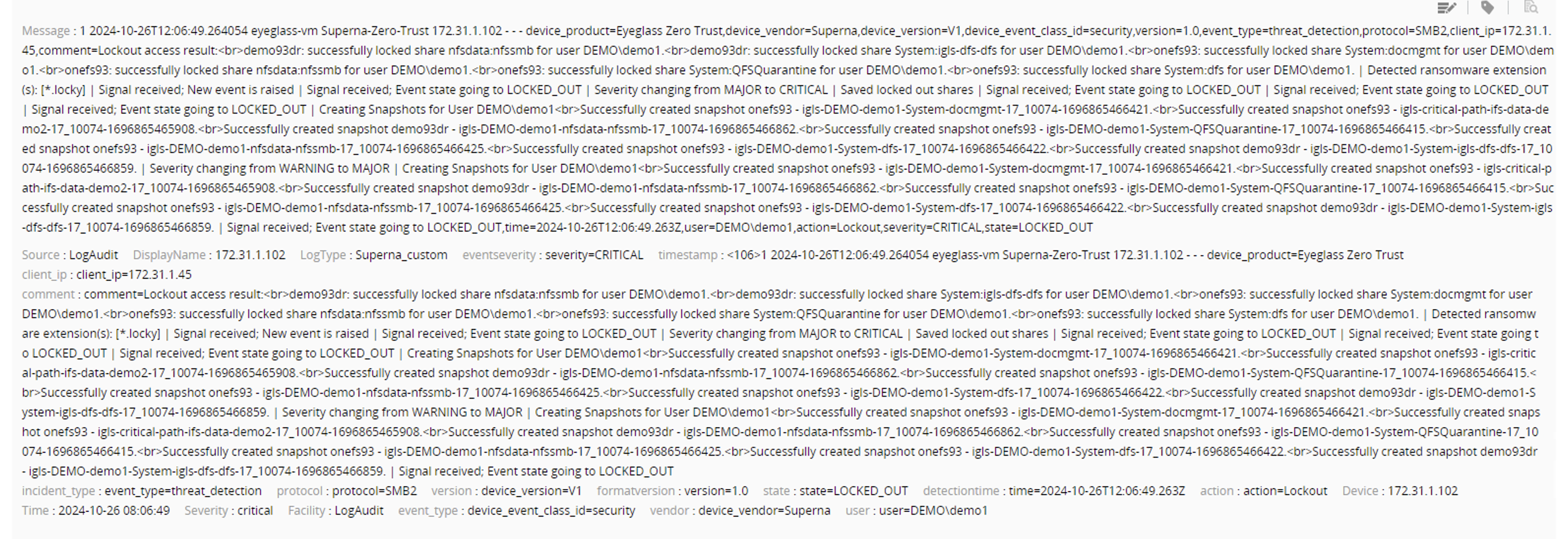
Once the custom parsing rules and device has been updated, any new messages will now be parsed and all fields can be extracted and used for further trigger correlation rules.
- Example log that is fully parsed
-
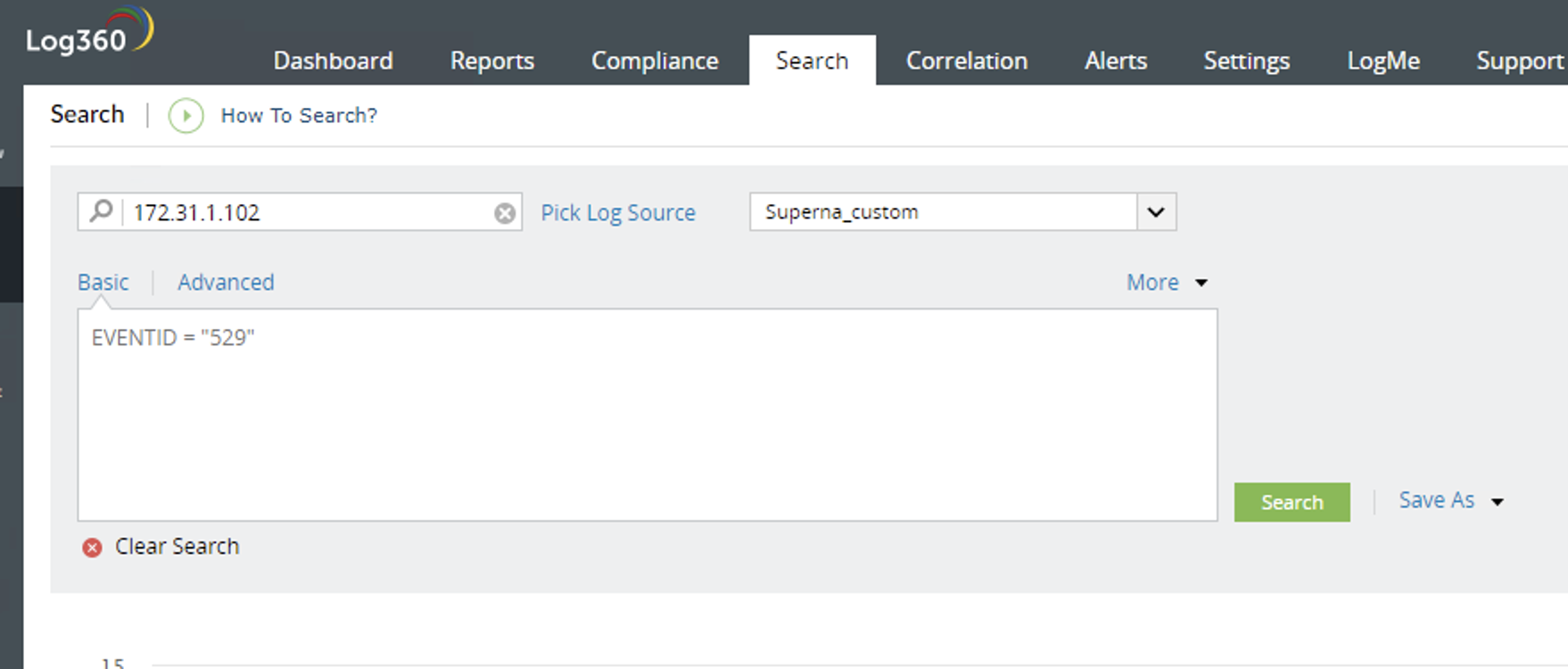
- Example search with log type set to Superna_custom
- Create an Alert Rule for Superna Zero Trust Events
- Search Criteria - Criteria = (incident_type:event_type=threat_detection) AND (vendor:device_vendor=Superna) AND (LogType:Superna_custom)
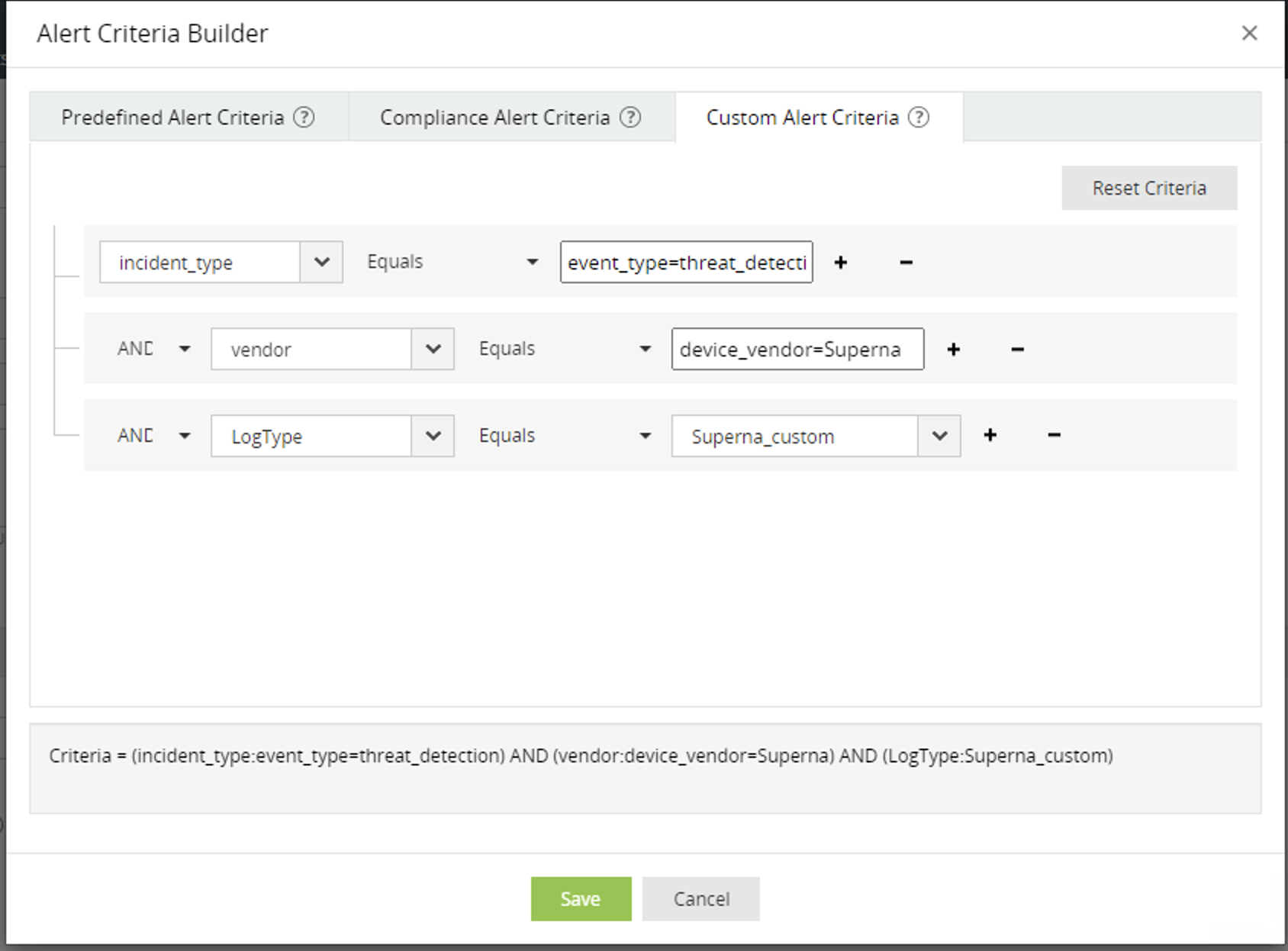
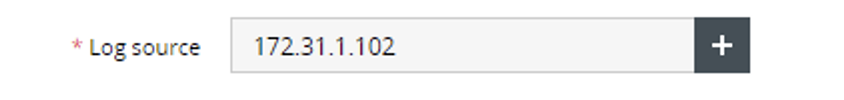
- Fill in the name of the customer alert example Superna Zero Trust Alert and notification rules.
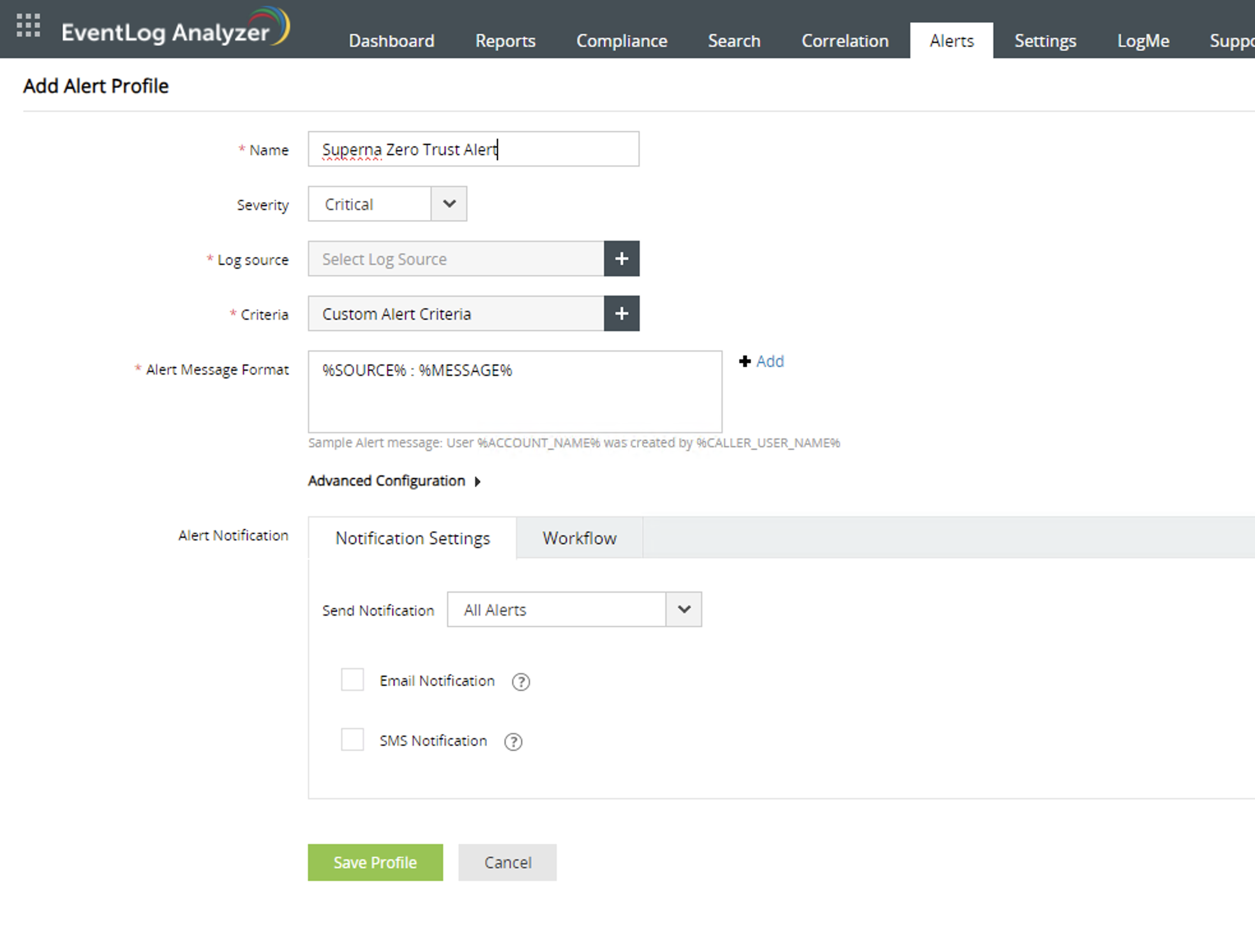
- Set the log source to the ip address host name of the eyeglass VM device.