CrowdStrike Fusion SOAR Integration
- Overview
- Limitations
- Solution Overview
- Video Demo
- Typical Use Cases
- Cyberstorage Incident Response - Capabilities
- What is CrowdStrike Fusion SOAR?
- Integration Architecture
- Solution Configuration in CrowdStrike Fusion SOAR and Data Security Edition
- Prerequisites
- Configuration Steps on Eyeglass Virtual Machine
- CrowdStrike FUSION SOAR on premise API proxy Configuration
- Configuration in CrowdStrike Fusion SOAR From the Marketplace
- How to use Cyberstorage Incident Response Application Workflows
Overview
CrowdStrike Fusion SOAR is the Security Orchestration, Automation, and Response (SOAR) platform integrated into the CrowdStrike ecosystem. It is designed to help security teams streamline and automate their workflows, manage incident response, and integrate various security tools to improve efficiency and reduce response times.
Customers using CrowdStrike Fusion SOAR can now leverage a native integration that delivers Cyberstorage Incident Response natively into Fusion SOAR. See Crowdstrike integration landing page
-
NOTE: This documentation is provided "as is" without support for 3rd party software. The level of support for this integration guide is best effort without any SLA on response time. No 3rd party product support can be provided by Superna directly. 3rd party components require support contracts
Limitations
- None
Solution Overview
Superna Data Security Edition Zero Trust API is used to receive workflows and playbook requests through application integrations from the FUSION Foundry application builder interface within Crowdstrike. Once an application and integration are published and released a workflow can be created and leveraged across all incidents with an on demand Workflow action.
Video Demo
Typical Use Cases
- The Superna Cyberstorage Incident Response application provides industry first capabilities to SOC Managers and analysts to protect data directly during Incident response process without needing any direct access or knowledge of storage systems.
- Incident Examples
- User account is phished
- Run Snapshot and user lockout workflows
- Suspected host breach by an attacker
- run snapshot workflow to protect data and provide a roll back point from an immutable snapshot
- Large DDOS attack on external firewall
- Protect data with snapshot workflow
- Employee termination
- Disabling an AD account is not enough, running user block action guarantees that user account cannot login to modify , delete or take corporate data
- User account is phished
Cyberstorage Incident Response - Capabilities
- Zero trust CrowdStrike application, integration and workflows to extend offensive data protection as an action to respond to any incident within Crowdstrike.
- Superna Data Security Edition Integrations enable the following Cyberstorage Incident Response Actions.
- Cyberstorage IR - Critical Data Snapshot API as defensive response to any incident within Next-Gen SIEM. This creates immutable snapshots on critical data on all NAS devices protected by Superna.
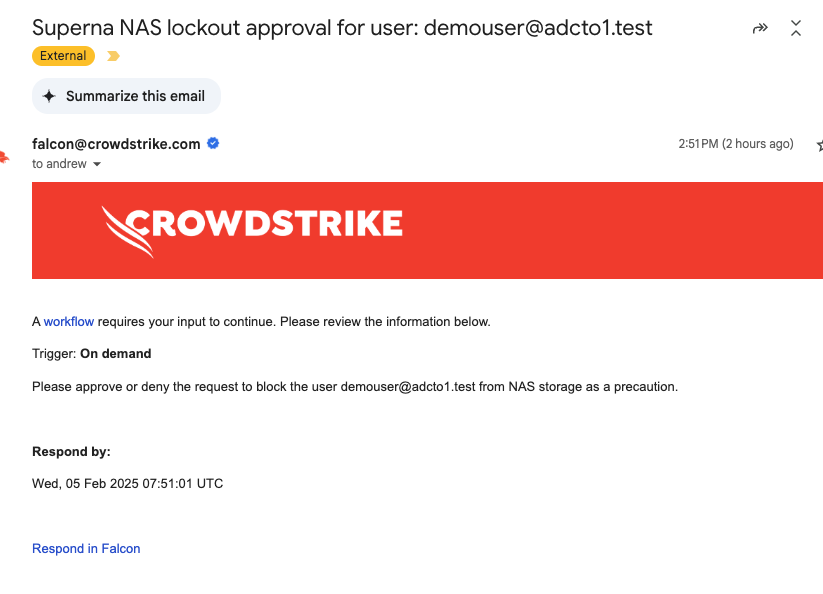
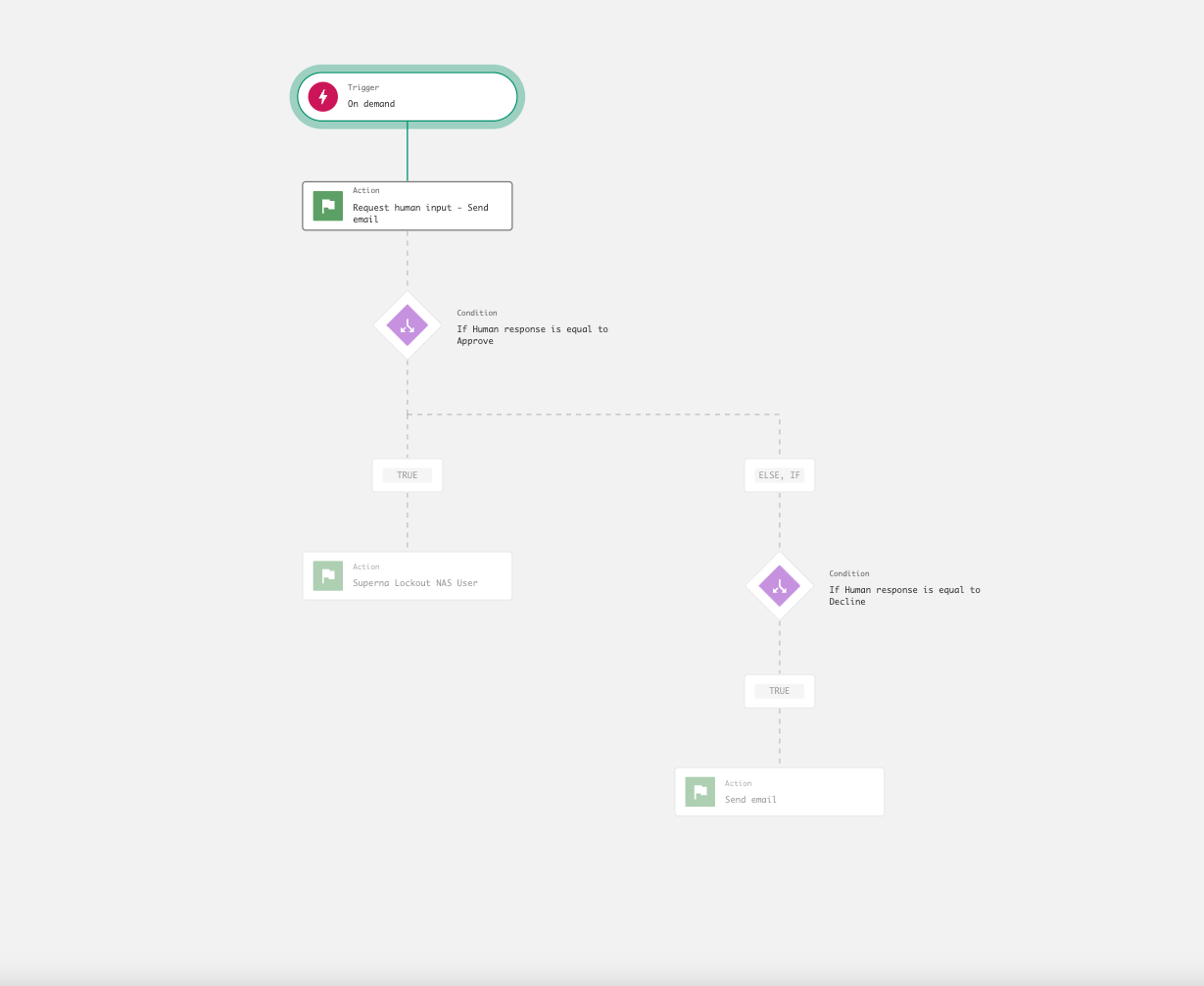
- Cyberstorage IR - User Data Block - Allows SecOPS to block a user and leverages approval workflow to route request to approve a user lockout
- Cyberstorage IR - User Data Restore - Allows SecOPS to restore a users data access and leverages approval workflow to route request to approve or deny a user restore by the SecOPS manager
What is CrowdStrike Fusion SOAR?
- Reduce Response Times: Automates actions like isolating endpoints, notifying stakeholders, and updating tickets, reducing the time it takes to respond to threats.
- Improve Consistency: Ensures responses follow predefined workflows, reducing the risk of human error.
- Scale Operations: Enables small teams to handle a larger volume of alerts and incidents by automating repetitive tasks.
- Integrate Disparate Tools: Connects your entire security stack, allowing seamless data sharing and action coordination.
Integration Architecture
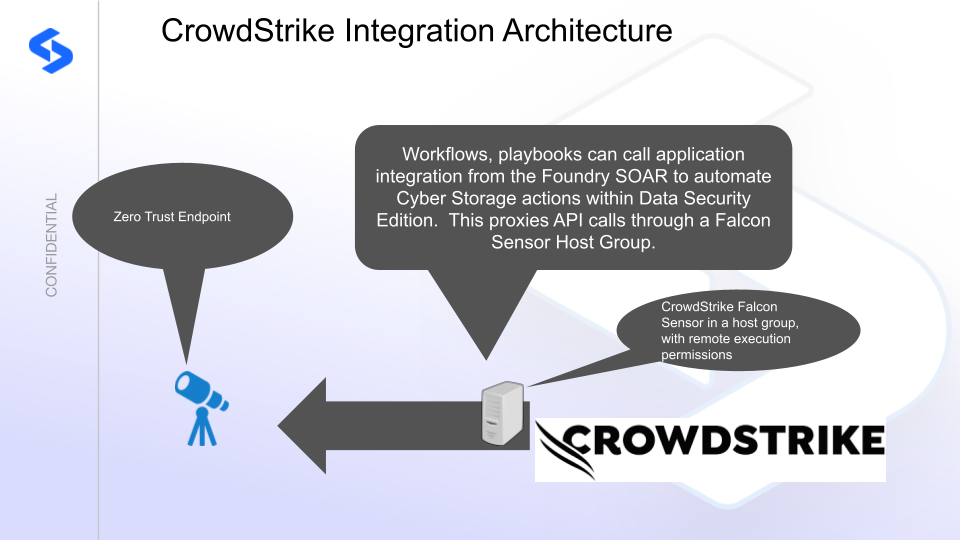
Solution Configuration in CrowdStrike Fusion SOAR and Data Security Edition
Prerequisites
- Installed Security Edition
- Eyeglass OS appliance version 15.5
- cat /etc/os-release
- License key for the Zero Trust API
- CrowdStrike Fusion SOAR application entitlement
- NOTE: Falcon Sensor host in a host group with remote execution permissions assigned. The host group hosts need to be able to reach the Eyeglass Zero trust endpoint over TCP port 443 from the Host group hosts.
Configuration Steps on Eyeglass Virtual Machine
- Create an API token to use the Zero Trust API
- Login as admin
- Open the Integrations Icon
- Create a token from the API token tab
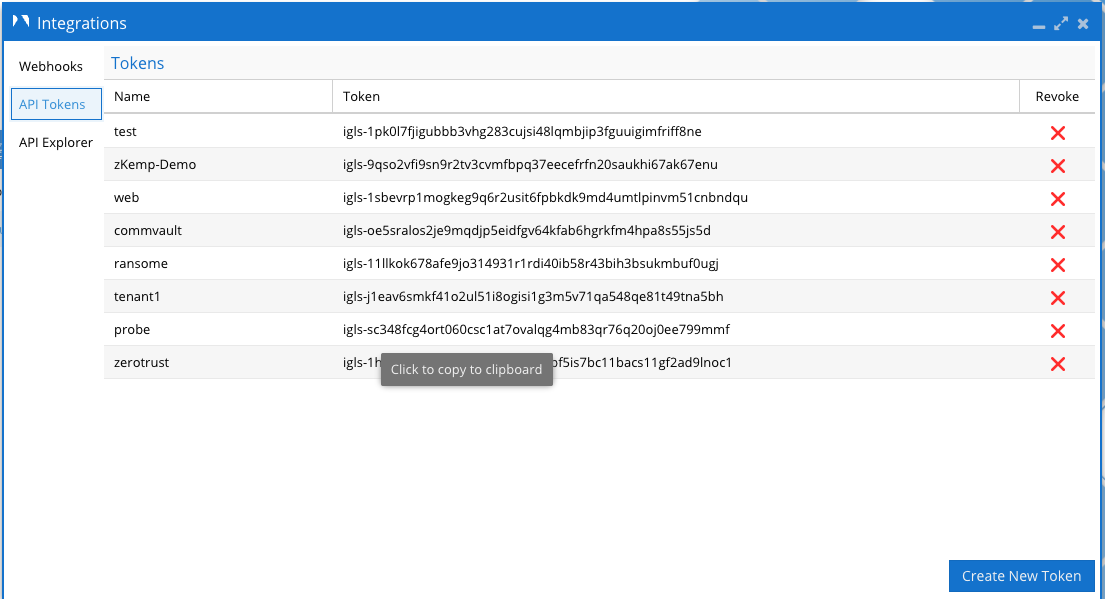
- Create a name for the token example Fusion SOAR
- Copy and record the api token for the steps below
- Record the Eyeglass VM IP address for the steps below.
- Done
CrowdStrike FUSION SOAR on premise API proxy Configuration
- To issue API calls that can reach on premise infrastructure requires a Falcon sensor host within a host group.
- Follow host group documentation here. Name the host group APIProxy so it is easily identified when assigning this host group to the application definition.
- Grant remote execution permissions to this host.
Configuration in CrowdStrike Fusion SOAR From the Marketplace
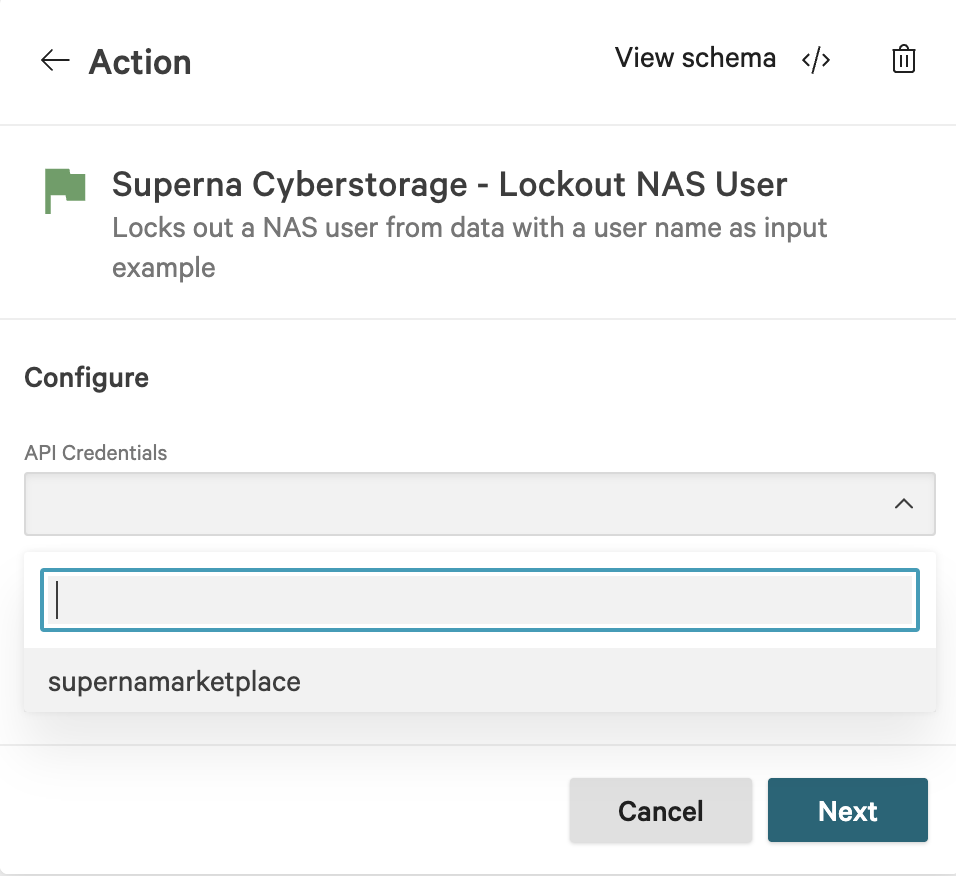
- Open the Marketplace and search for Superna
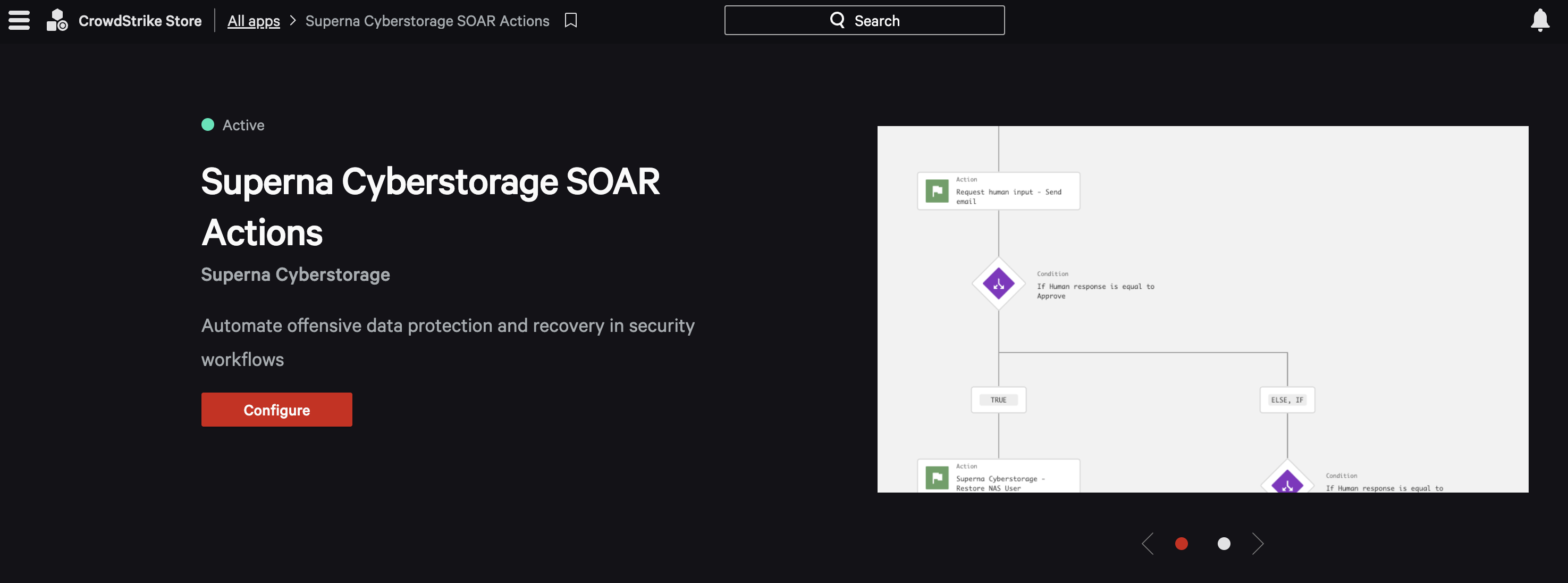
- Click Configure, click Add configuration
- Provide a name for the configuration, enter the ip address of the Eyeglass VM , enter the API key created in the steps above. Select the host group that was configured in the steps above to proxy api requests to on premise endpoints. Check the box to ignore SSL certs.
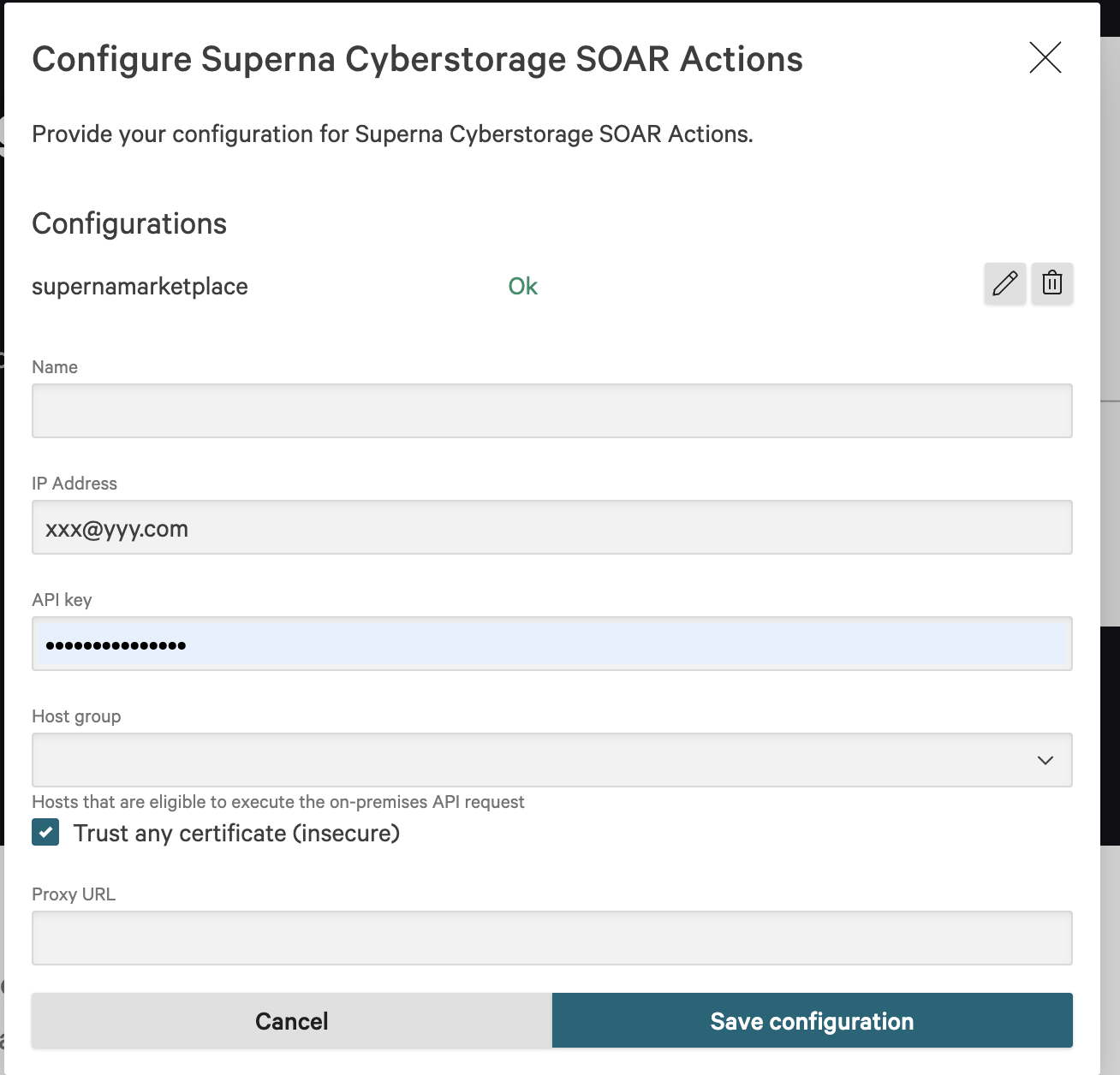
- Click Save
- Now import the playbooks for Snapshotting critical data, block user access to data and restoring user access to data.
- Fusion SOAR -> Content Library -> search for Superna
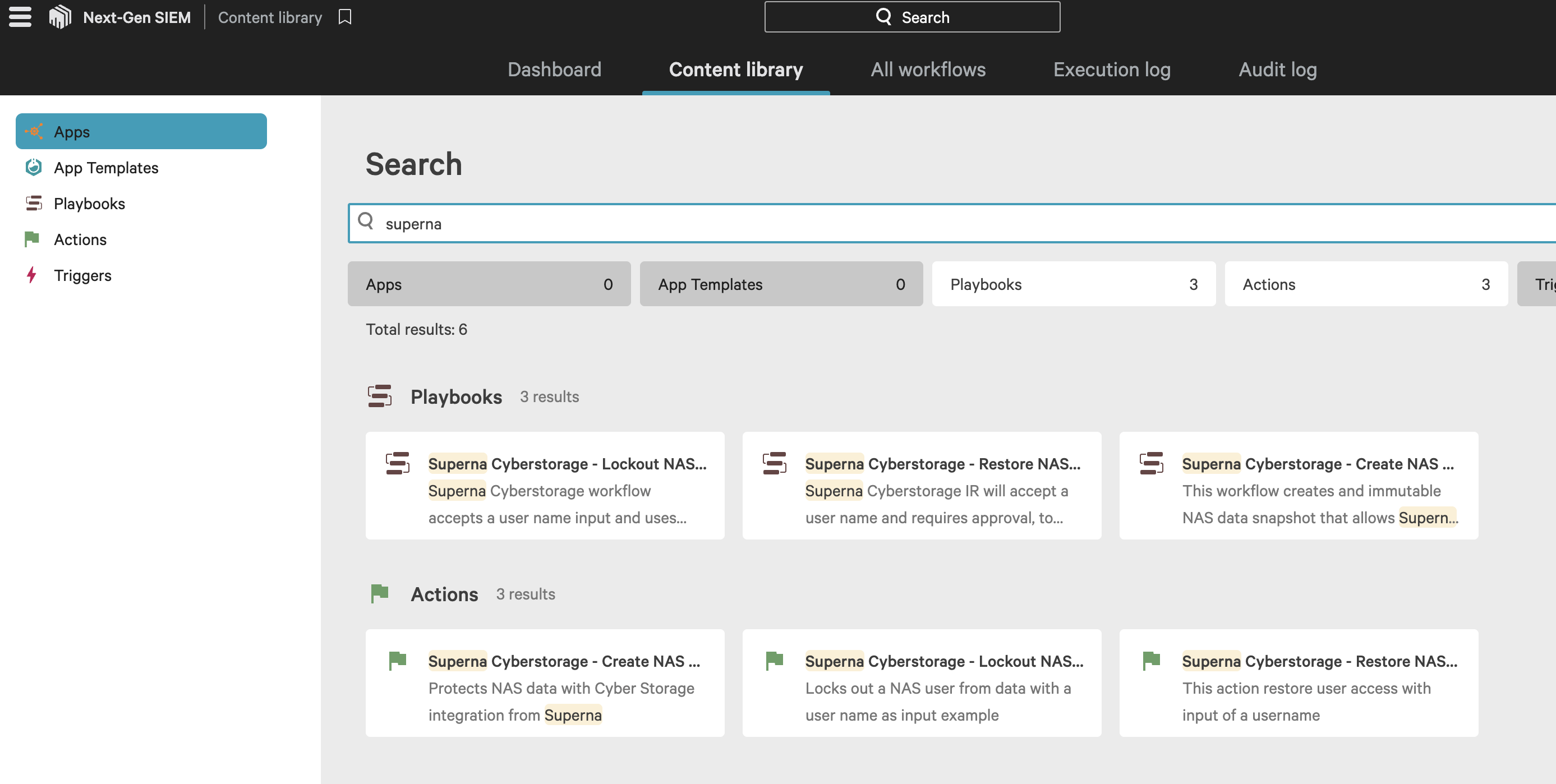
- Select the first playbook
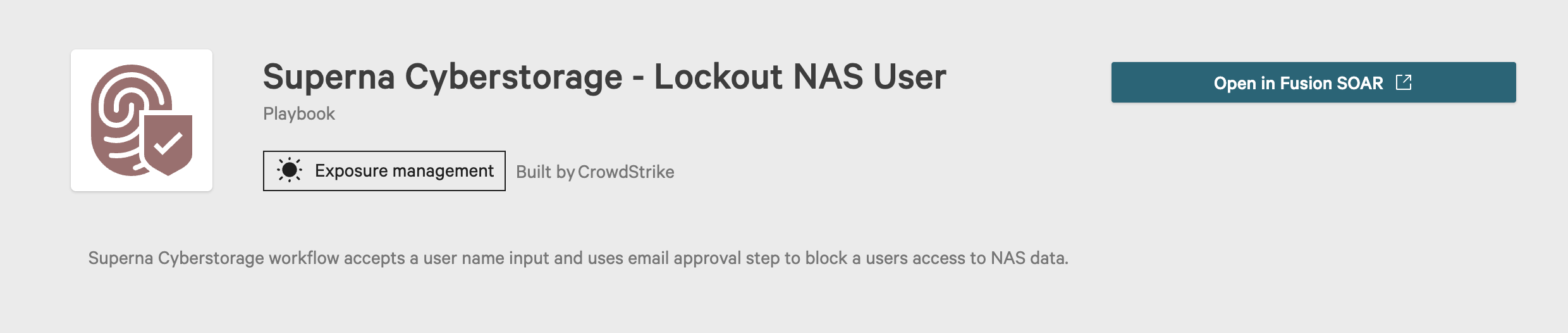
- Click Open In Fusion SOAR
- Click Customize playbook
- Select the Action and set the configuration drop down to match the configuration name in the steps above.
- Save the playbook.
- Repeat these steps of each of the playbooks to add them to your Next Gen SIEM configuration and enable the status to make them available to SOC analysts.
- Done.
How to use Cyberstorage Incident Response Application Workflows
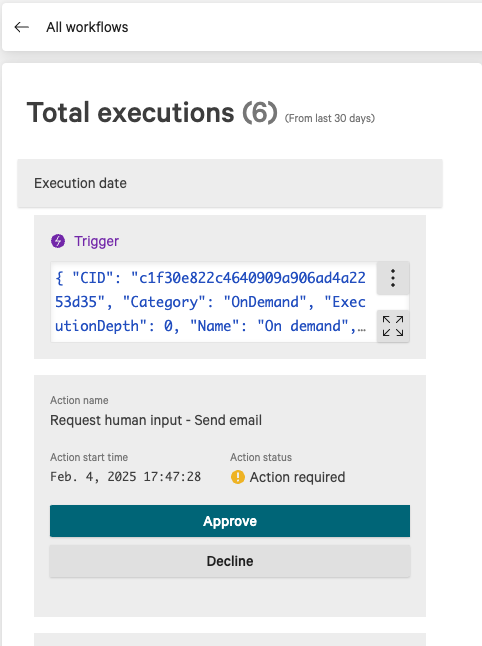
- Execute the workflows from Next-Gen SIEM SOAR Workflows, 2 of the workflows have approval via email configuration. The approval can be completed from the email or from the console when viewing the execution of the workflow. See both examples below to approve the workflow. The snapshot workflow does not require input or approval.