Eyeglass Service Description
Part number “SEL-Eyeglass Cluster Addon Install Service - myqotes eyeglass-P016 Dell SKU AB109744”
Revision 2 Feb 6, 2020
Service - Superna ™ Install and Config Service Description
(Data Security, Data Insights, Data Orchestration, Data Security Essentials)
- Overview
- Project Plan Summary
- Prerequisites
- ECA Cluster Install & Config Service:
- Ransomware Defender Section:
- Easy Auditor Section:
- Search & Recover Section:
- Golden Copy Section
- Performance Auditor Section
- Data Security Essentials Upgrade Service Scope
- Prerequisites
- Scope
Overview
This service is designed for customers who are deploying Superna Eyeglass Ransomware defender and/or Easy Auditor and need installation and configuration assistance.
NOTE: This part number is used for Ransomware Defender OR Easy Auditor products. Quantity 2 of this service is required if both products have been ordered.
Scope: Covers a single clustered Eyeglass agent installation and configuration, with up to 2 collocated same site Clusters.
Service Delivery: Remote WebEx
Operating Hours: Monday to Friday 2:00 AM to 3:00 PM EDT
Terms and Conditions of task covered in product maintenance agreement Support Services Agreement
Mandatory: Eyeglass Installation Questionnaire Form completed located here with all questions answered. Service will not be scheduled until completed in full.
Exclusions:
NOTE: Only product documentation will be followed. This is not a consulting service.
Installation Technicians are not authorized to provide design recommendations, for DR features.
Hands on changes to external IT components example DNS, PowerScale, Active Directory or other non Superna supplied products.
Service delivery requires customer to have hands on knowledge of all external IT components.
NOTE: This service is not a security audit. Consulting services should be purchased. Installation technician is not authorized to provide security advice.
Project Plan Summary
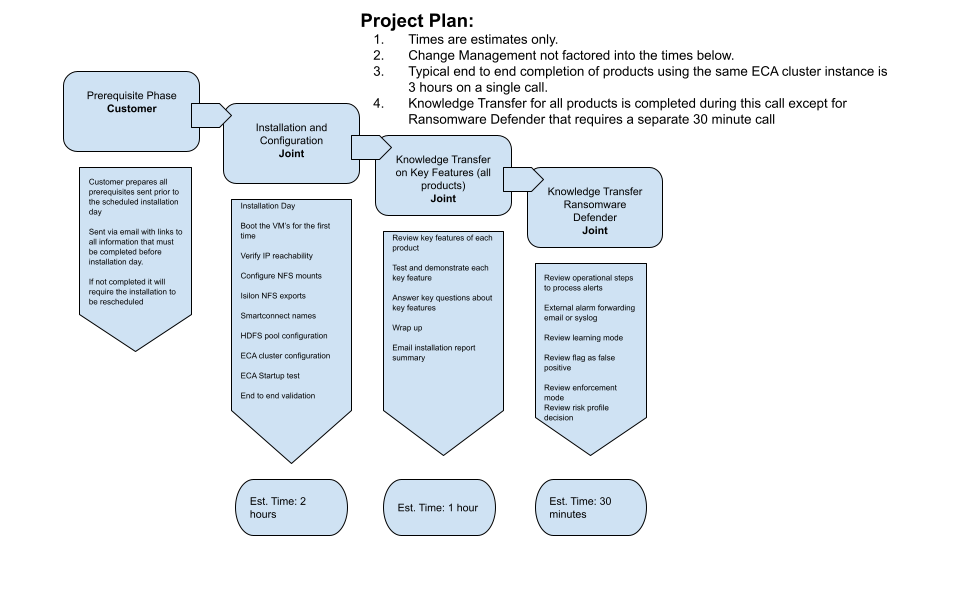
Prerequisites
Customers must complete these steps prior to scheduled installation and configuration
Confirm that Eyeglass DR Edition is installed
Ransomware Defender and/or Easy Auditor Installation and/or Search & Recover Checklist Form has been submitted
Easy Auditor Only - HDFS license key is installed , contact Dell EMC account team to request the license key.
Confirmed the license key is installed before scheduled installation date by emailing sales@superna.net
Access Zone has been configured for the Easy Auditor database. Consult Dell documentation to complete these steps.
Access Zone name eyeglass with path /ifs/data/igls/analyticsdb
An IP pool created with 3 node members and the pool assigned to the Access zone eyeglass created in the previous step
3 ip addresses allocated
Smartconnect name configured and DNS delegation correctly resolves with round robin IP addresses
NOTE: Installation cannot be scheduled until these steps are confirmed to sales@superna.net
On the day of installation confirm availability of the DNS administrator to make changes if the above steps requires debugging or was mis configured.
All products
Firewall ports opened as per documentation for Eyeglass Eyeglass Ports Requirements and Scalability Limits
Firewall ports opened as per documentation for ECA clusters. ECA Cluster application port requirements.
ECA Cluster Install & Config Service:
Initial Setup:
The following are initial setup steps whether installing Ransomware Defender, Easy Auditor , or Search & Recover:
Eyeglass Ransomware Defender/Easy Auditor Install Phase - Remote Install with customer via Webex meeting to accomplish the following:
Prerequisite - Gather site installation requirements from submitted Installation Checklist Form for review
Prerequisite- Identify VM deployment option:
VM count depends on products purchased
1 physical ESX host and 3-6 VM’s (lowest HA option)
3 physical hosts and 1 VM per host (highest HA option)
Prerequisite - Deploy OVA (vcenter administrator required)
Require 3-6 VM ip addresses
Require Eyeglass IP address
Require open ports between Agent and Eyeglass, Agent and cluster as per installation guide
Require Access Zone (HDFS enabled) to be created for Agent database
Create IP pool with at least 3 nodes in the IP pool and 3 IP addresses
Install OVA with above prerequisites
Test connectivity ip and ports between components (Eyeglass, Agent and cluster)
Installation Completed
Configuration Phase - Webex
Apply License to Eyeglass
Verify license
Edit configuration file on agent startup (api token created in Eyeglass)
Startup clustered agent code
Validate correct startup
Validate DB create on HDFS Access Zone
Validate Service heartbeat in Eyeglass with Service Manager Icon
Validate shutdown and restart of cluster success
Configure PowerScale to audit files in an Access Zone for testing phase
Configure Turboaudit with NFS mounts on audit directory on all ECA nodes
Enable auditing on one or more access zones
- Verify audit messages are being processed
Completed
Go to the Ransomware Defender Section if the product was purchased
Go to the Easy Auditor Section if the product was purchased
Go to the Search & Recover Section if the product was purchased
Go to the Golden copy Section if the product was purchased
Ransomware Defender Section:
This only applies if the service was purchased with Ransomware Defender.
Test and Configuration Phase - Ransomware
Configure Security Guard feature
Validate successful execution
Configure schedule
Knowledge transfer on log file validation for Security guard
Enable monitor mode to baseline user behavior
Review Security assessment on enforcement section in the admin guide
Customer to decide on Low , Medium or High risk profile. Review decision criteria in the admin guide. How to determine threat response settings to meet your Company’s Risk Profile
Update check list in installation document this section was reviewed
Configure settings as per customer risk profile decision.
Over 2-3 weeks schedule validation sessions on the installation
Collect support logs
Explain white list settings to customer and future behaviors that have lockout that may require ongoing white list updates.
Make white list changes from analysis of statistics and user behaviors detected apply to installation. Repeat process until detections are set correctly for customer environment
Knowledge Transfer Phase - Ransomware
How to enable production mode
Operational cluster management section
Start, stop, upgrade
How to process security incidents work flow from the admin guide How to respond to Security Events for Warning, Major or Critical Events
How and when to make white list changes when introducing new server applications that write data to PowerScale.
Enable monitor mode
Monitor application and events
Exit monitor mode when application work flow does not generate security incidents
How to use ECACTL CLI and key command troubleshooting
Start cluster ecactl cluster start
Stop cluster ecactl cluster down
Check for running containers ecactl containers ps
Get stats on running containers ecactl stats
UI walk through ransomware
Active Events
Event History
Settings
Statistics
Licensing
Managed Services Icon
Security Guard
Service complete
Easy Auditor Section:
This only applies if the service was purchased with Easy Auditor.
Test and Configuration Phase - Easy Auditor
Verify audit data is being stored in the analytics database with query interface
Run test user query report
Run test path based report
Test Where did my folder go?
Rename a directory or drag and drop a directory
Run search in Where did my folder go?
Review test wiretap functionality on a path with a test user mounting and accessing files
Verify user activity is visible in the UI
Review decode of open files and actions
Knowledge Transfer Phase - Easy Auditor
How to build a query and filter on user, path, file extension, file action
How to run query reports
Cluster Operations
How to use ECACTL CLI and key command troubleshooting ECA cluster issues
Start cluster ecactl cluster up
Stop cluster ecactl cluster down
Service complete
Search & Recover Section:
This only applies if the service was purchased with Search & Recover.
- Configuration Phase - Search & Recover
- Download: The OVA can be downloaded by following the normal download instructions here.
- The menu item to select is VMware OVF installers and select the Eyeglass Search & Recover download
Deploy to vCenter: During deployment to VMware enter the IP address information for each node, Enter cluster name all lowercase with no special characters.
- Add License keys:
- Download keys using supplied token in process here.
- Copy the license zip file to node 1 using SCP or Winscp utility to copy the zip file using Secure Shell protocol, login with ecaadmin and password above
- Apply License keys:
- Follow add license keys CLI instructions section "Licensing CLI Commands " in the Admin Guide.
- Add cluster:
- Follow add cluster CLI instructions section "Adding, Viewing Clusters " in the Admin Guide.
- Follow add cluster CLI instructions section "Adding, Viewing Clusters " in the Admin Guide.
- Add Path to be indexed:
- Follow the instructions to add a folder for indexing in the section "How to add a folder path to be Indexed" in the Admin Guide.
- Follow the instructions to add a folder for indexing in the section "How to add a folder path to be Indexed" in the Admin Guide.
- Start Indexing Jobs:
- Follow the instructions to start indexing job in the section "How to start a full index job on a path" in the Admin Guide.
- Monitor Indexing Statistics:
- Follow the instructions to monitor indexing progress of the folder path added above in the section "How to Monitor Index Jobs" in the Admin Guide.
- Test Phase - Search & Recover
- Login and try some searches:
- open a browser https://x.x.x.x (ip is node 1 of the cluster)
- Enter an AD user login using DOMAIN\user or user@example.com (note domain name must be uppercase) and then password.
- Try a search for data in the path you indexed.
- NOTE: The user you login must have Share permissions to the path was added to be indexed data
- Advanced Feature Walk though
- Try a file size range search
- Download the results to CSV
- Download a script with example ISI command isi get -D and output to a results file >> results.txt
- Knowledge Transfer Phase - Search & Recover
- Explain Solutions available with the product. Guide here.
- Explain how to use the diagnostic tools and how to access. Guide here.
- Explain index process for full versus incremental and lag to detect changed files.
- Demonstrate how to generate a support backup and how to download from the admin download page Guide here.
- Explain how to download CSV and large scripts from the admin download page. Guide here.
- Explain how to set the results location FQDN for smartconnect and how SMB share names are inserted dynamically. Guide here.
- Explain where to find advanced field search syntax examples and search rules with wild cards. Guide here.
- Explain the security modes on indexed folders, guide Here.
Golden Copy Section
This only applies if the service was purchased with Golden Copy.
- Configuration Phase - Golden Copy
- Download: The OVA can be downloaded by following the normal download instructions here.
- The menu item to select is VMware OVF installers and select the Eyeglass Golden Copy download
Deploy to vCenter: During deployment to VMware enter the IP address information for each node, Enter cluster name all lowercase with no special characters.
- Add License keys:
- Download keys using supplied token in process here.
- Copy the license zip file to node 1 using SCP or Winscp utility to copy the zip file using Secure Shell protocol, login with ecaadmin and password above
- Apply License keys:
- Follow add license keys CLI instructions section "Licensing CLI Commands " in the Admin Guide.
- Add cluster:
- Follow add cluster CLI instructions section "Adding, Viewing Clusters " in the Admin Guide .
- Follow add cluster CLI instructions section "Adding, Viewing Clusters " in the Admin Guide .
- Add Path to be copied:
- Follow the instructions to add a folder for archiving in the section "How to manage folders to be copied or synced" in the Admin Guide .
- Follow the instructions to add a folder for archiving in the section "How to manage folders to be copied or synced" in the Admin Guide .
- Start Archiving Jobs:
- Follow the instructions to start indexing job in the section "archive (start a copy job)" in the Admin Guide .
- Monitor Archive jobs:
- Follow the instructions to monitor indexing progress of the folder path added above in the section "How to monitor copy job performance and job log" in the Admin Guide .
- Verify Copy Jobs and How to Review reports:
- Review summary copy reports
- Review detailed copy reports
- Test Phase - Golden Copy
- Login and try monitor copy reports:
- open a browser https://x.x.x.x (ip is node 1 of the cluster)
- eccaadmin and password
- Start a file copy, monitor the copy, review copy logs
- Advanced Feature Walk though
- How to configure folders for S3 storage types (add, modify , delete)
- Walk through folder flags and meaning of how to configure features
- Knowledge Transfer Phase - Golden Copy
- Explain best practices and when to use copy, vs sync mode
- Explain use cases for deferred delete, Airgap
- Explain single file restore
- Explain bulk restore and commands
- Explain rate limiting options for bandwidth
- Explain concurrent file copy settings and impact of increasing
- Explain PowerScale node use case
- Explain load balancing copies to target storage
Performance Auditor Section
This only applies if the service was purchased with Performance Auditor.
- Configuration Phase - Performance Auditor
- Enable the EVTreporter service on the ECA cluster
- Increase RAM on ECA nodes as per sizing table here.
- Verify Eyeglass open ports for the Performance Auditor application table is here.
- Verify Turbo audit events are being processed by EVT reporter container
- Verify cluster audit events are enabled to support the Performance Auditor features here.
- Test Phase - Performance Auditor
- Open the Performance Auditor application and verify the display is showing analysis data
- Switch views to verify all metrics are reported including AD user names
- Knowledge Transfer Phase - Performance Auditor
- Explain top 5 per category display and view switching
- Explain drill in to an object in each view and how this is used to identify who, what user , what files or application is generating the most work load per node or cluster wide
- Explain yellow band display is baseline computed from all nodes in the cluster as 2 standard deviations above and below cluster wide average and how to use this baseline to track which nodes are above average load level (same applies to all the other views)
- Explain application read and write mode tracks SMB or NFS application requests per second as a way to understand relative application efficiency for NAS operations.
- Demonstrate pinning feature to add a user to the display that is not in the top 5, explain who pinning allows comparison of an object outside the top 5. Demonstrate file extension pinning to monitor an applications impact on cluster resources.
- Demonstrate how to switch rate from MB's to GB's or KB's depending on the throughput rates of the monitored object.
Data Security Essentials Upgrade Service Scope
Prerequisites
Must be completed before scheduling the upgrade. Estimated time to complete 4 hours.
- Windows Server OS > 2019
- 4 x cpu
- 32 GB or more of ram
- Microsoft SQL Database
- Remotely hosted or installed co-resident
- Versions 2019 or later
- Install IIS Web server component on Windows Server OS
Scope
- Validate SQL database access service account access and firewall ports to reach SQL server database
- Run Data Security Essentials (documentation)
- Verify upgrade
- Verify previous configuration and policies are present
- Verify license key
- Install new license key
- Configure auditing data collection for testing of ingestion and reporting
- Select a path or SMB share to collect audit data
- Create IO in this path
- Verify audit data ingestion
- Verify reports execute
- Knowledge transfer on new features
- Ransomware policy enable steps for banned file list and response action
- Test banned file response on a test user on the test path or smb share
- Ransomware Behavior detection enable steps
- Custom behavior policy creation walk through.
- Ransomware policy enable steps for banned file list and response action