Overview
When Compliance Mode is enable on PowerScale cluster it prevents users from modifying or deleting files for compliance purposes.
Note: This guide applies to PowerScale Clusters with OneFS version 8.0.1.x and later.
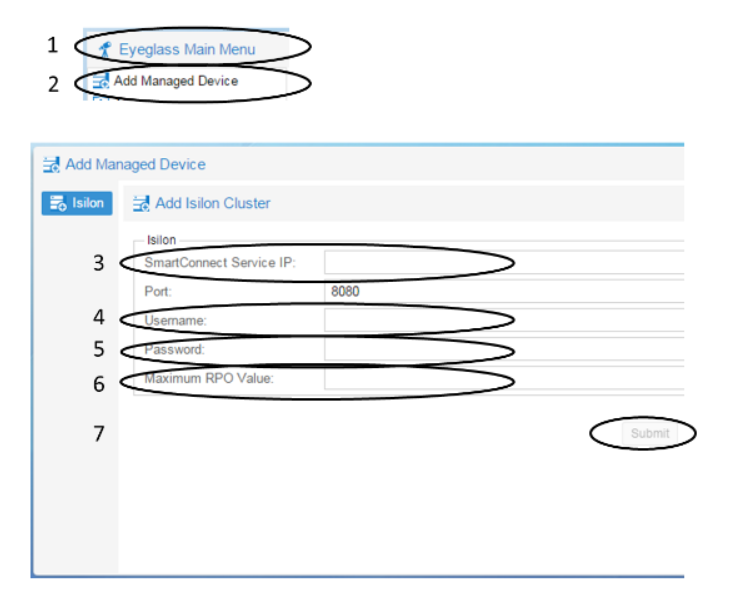
Eyeglass appliance installation
Follow the installation guide until “Add PowerScale Cluster” section in the install guide.
Use “compadmin” user account to register the PowerScale Clusters on Eyeglass Appliance (Step 4).
Clusters with compliance mode active do not allow files owned by root to be modified. In regular installations “eyeglass” user account is used to register the PowerScale cluster and minimum privileges are required to set up, sudoers file cannot be edited to add eyeglass account so this is the reason the compadmin user in compliance mode is required to register the cluster.
Consideration replicating SmartLock directory:
You can create two types of SmartLock directories: enterprise and compliance. Enterprise directories allow you to protect files without restricting the cluster with the regulation rule 17a-4. Complies directories are protected with the regulation rule 17a-4 and delete is not available.
Note: This guide is focused on compliance directories.
Limitations for source directory and target directory of a SyncIQ policy:
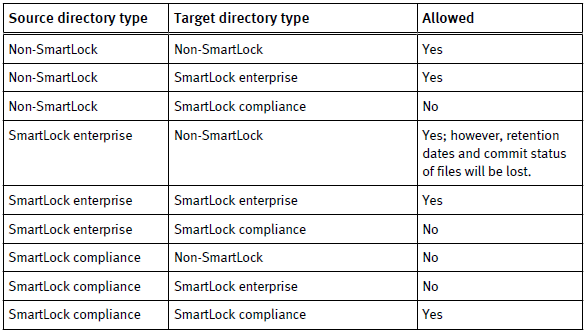
Requirements for compliance directories before creating a synciq policy:
- The smartlock directory must be created on target prior to run the SyncIQ policy.
- If the compliance directory is not created on target the replication job will fail.
- Smartlock directory configuration settings are not replicated. If you change setting on source you must change them in target.
- The SyncIQ policy and SmartLock compliance directory must be configured at the same root directory level. A SmartLock compliance directory cannot be nested inside a SyncIQ policy.
Operations with compliance mode:
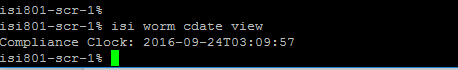
Set compliance clock
The compliance clock must be configured before create SmartLock compliance directories. It is important to follow the EMC best practices when enabling a compliance mode. NTP configuration is recommended to set up on all nodes of source and target clusters to ensure all clock nodes are synchronized.
To set compliance mode follow this steps:
1. Start ssh session to PowerScale cluster and login with compadmin user account.
2. Set the compliance clock by running the following command
isi worm cdate set
3. Check if the compliance clock is running with the following command
isi worm cdate view
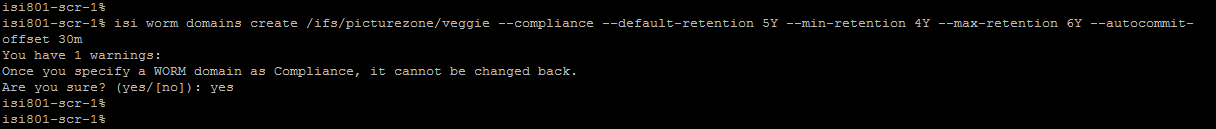
Creation of SmartLock directory on Source
Once you create SmartLock directories you can commit files in that directory to WORM state.
- Click File System > SmarLock > WORM.
- Click Create Domain.
Define type (compliance) and directory path.
You can define the default retention period, minimum and/or maximum retention period. Also an autocommit time period.
Using CLI Command:
- Open a secure shell (SSH) connection to any node in the cluster and log in.
- Run the isi worm domains create command.
For Example:
The following command creates a compliance directory with a default retention period of 5 years, a minimum retention period of 4 years, a maximum retention period of 6 years, and an autocommit time period of 30 minutes.
View SmartLock directory settings:
Use this command to view SmartLock Directory settings:
1. Open a secure shell (SSH) connection to any node in the cluster and log in.
2. Run the isi worm domains list command.
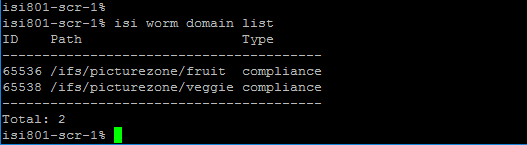
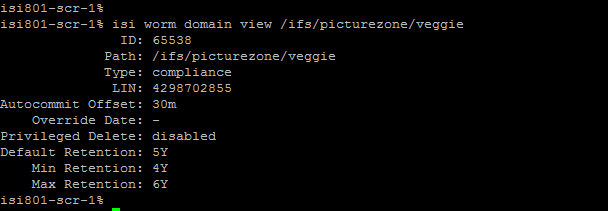
To view details about the SmartLock directory perform isi worm domains view <domain-directory>
View a file WORM status:
To check the WORM status of the file, perform the follow command:
1. Start ssh session to PowerScale cluster and login.
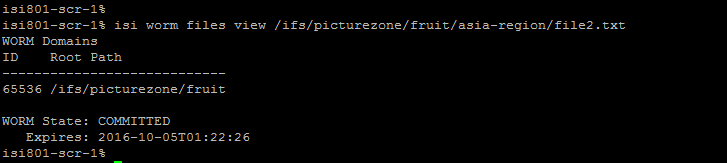
2. Check the WORM status of the file by running the following command
isi worm files view <file>
For example,
Failover and Failback operations with Eyeglass
According with your environment and requirements follow the Failover Configuration Guides on Superna documentation website.
Before failover or failback operations check the following documentation and Failover Planning Guides:
Using the compadmin user account on Eyeglass failover and failback operations has the following known restrictions with system permissions and privileges.