How to Configure Syslog Forwarding of Formatted Audit messages to an External Syslog Server
- Overview
- How to configure syslog forwarding
- Example syslog message format sent by the ECA
- How to view Syslog forwarding Statistics
- How to debug syslog forwarding when you syslog server does not receive messages
- How to Configure event filtering before forwarding
- Example filter for a path called /ifs/data/smb01/test123
- Example of how to exclude audit records from /ifs/.ifsvar
- Syslog Configuration Forwarding Parameters
Overview
This configuration is optional and only needed when events should be forwarded another logging system link Splunk or other logging tools. The ECA can run an additional dock container that consumes events and formats for syslog forwarding. This container can run on all nodes and allows for parallel forwarding of events.
How to configure syslog forwarding
- Login to each node that you want to enable syslog forwarding over ssh as ecaadmin. NOTE: each node needs the file edited to configure the forwarding. The instructions assume all nodes except node 1 will forward to syslog server.
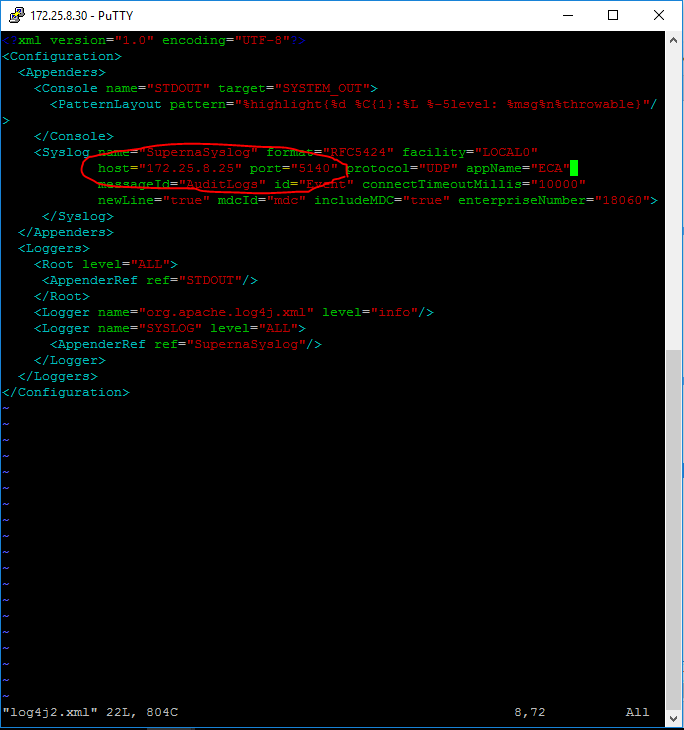
- vim /opt/superna/eca/conf/syslogpublisher/log4j2.xml
- Add the ip address of the syslog server and the UDP port for your syslog server. NOTE: You must edit the default port in the file 5140 and change this to the port used by your syslog server. NOTE: Default syslog servers use port 514
- Save the file
- The docker container does not start by default to start this container, Add an entry to the docker overrides file to start the container on nodes 2-N.
- vim /opt/superna/eca/docker-compose.overrides.yml
- add a section as per image below make sure to space the entries exactly as shown
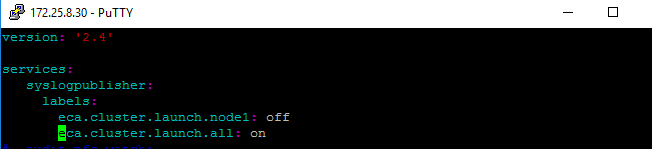
- save the file
- To update all nodes with the new syslog configuration run the following command:
- ecactl cluster push-config
- To start the container now and follow the steps below:
- Now create the container on all nodes
- ecactl cluster exec "ecactl containers up -d syslogpublisher"
- NOTE: This will start the container
- This will start the container on node 1 and should be removed in production environments
- On node 1 run this commands to stop and remove the container, Answer yes to the prompt to remove.
- ecactl containers stop syslogpublisher
- ecactl containers rm syslogpublisher
- Now create the container on all nodes
- Verify your syslog server is now receiving events sample syslog format below.
- To monitor the forwarding function and events received and sent use this command to monitor the syslog container on one eca node (note all ECA nodes are forwarding events).
- ecactl logs --tail 200 --follow syslogpublisher (this command will show stats every minute for events received by the container and sent to your syslog server).
- done
Example syslog message format sent by the ECA
- 2019-07-07T20:49:22.328Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x8","path":"\\\\00505699a9f1aecd965b770a3472e43955d2\\System\\ifs\\spark-logs\\.f6b02da1-6f42-43a3-b02a-ae87564c255b","protocol":"HDFS","server":"node 172.31.1.131 07/07 16:49:21.964
- 2019-07-07T20:49:22.332Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\00505699a9f1aecd965b770a3472e43955d2\\System\\ifs\\spark-logs\\.f6b02da1-6f42-43a3-b02a-ae87564c255b","protocol":"HDFS","server":"nod 172.31.1.131 07/07 16:49:21.964
- 2019-07-07T20:49:22.333Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x8000","path":"\\\\00505699a9f1aecd965b770a3472e43955d2\\System\\ifs\\spark-logs\\.f6b02da1-6f42-43a3-b02a-ae87564c255b","protocol":"HDFS","server":"n 172.31.1.131 07/07 16:49:21.964
- 2019-07-07T20:49:22.334Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40000","path":"\\\\00505699a9f1aecd965b770a3472e43955d2\\System\\ifs\\spark-logs\\.f6b02da1-6f42-43a3-b02a-ae87564c255b","protocol":"HDFS","server":" 172.31.1.131 07/07 16:49:21.964
- 2019-07-07T20:49:22.334Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\00505699a9f1aecd965b770a3472e43955d2\\System\\ifs\\spark-logs\\.f6b02da1-6f42-43a3-b02a-ae87564c255b","protocol":"HDFS","server":"nod 172.31.1.131 07/07 16:49:21.964
- 2019-07-07T20:49:22.335Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\00505699a9f1aecd965b770a3472e43955d2\\System\\ifs\\spark-logs\\.f6b02da1-6f42-43a3-b02a-ae87564c255b","protocol":"HDFS","server":"nod 172.31.1.131 07/07 16:49:21.964
- 2019-07-07T20:49:22.335Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x20","path":"\\\\00505699a9f1aecd965b770a3472e43955d2\\System\\ifs\\spark-logs\\.f6b02da1-6f42-43a3-b02a-ae87564c255b","protocol":"HDFS","server":"nod 172.31.1.131 07/07 16:49:21.964
- 2019-07-07T20:59:40.816Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\0050569960fcd70161594d21dd22a3c10cbe\\System\\ifs\\data\\policy1\\search\\cow.txt","protocol":"SMB2","server":"node001","clientIP":"1 172.31.1.131 07/07 16:59:40.430
- 2019-07-07T20:59:40.817Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\0050569960fcd70161594d21dd22a3c10cbe\\System\\ifs\\data\\policy1\\search\\cow.txt","protocol":"SMB2","server":"node001","clientIP":"1 172.31.1.131 07/07 16:59:40.446
- 2019-07-07T20:59:40.817Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x2","path":"\\\\0050569960fcd70161594d21dd22a3c10cbe\\System\\ifs\\data\\policy1\\search\\cow.txt","protocol":"SMB2","server":"node001","clientIP":"17 172.31.1.131 07/07 16:59:40.446
- 2019-07-07T20:59:40.821Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\0050569960fcd70161594d21dd22a3c10cbe\\System\\ifs\\data\\policy1\\search\\cow.txt","protocol":"SMB2","server":"node001","clientIP":"1 172.31.1.131 07/07 16:59:40.446
- 2019-07-07T20:59:40.823Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\0050569960fcd70161594d21dd22a3c10cbe\\System\\ifs\\data\\policy1\\search\\cow.txt","protocol":"SMB2","server":"node001","clientIP":"1 172.31.1.131 07/07 16:59:40.446
- 2019-07-07T20:59:40.829Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\0050569960fcd70161594d21dd22a3c10cbe\\System\\ifs\\data\\policy1\\search\\cow.txt","protocol":"SMB2","server":"node001","clientIP":"1 172.31.1.131 07/07 16:59:40.446
- 2019-07-07T20:59:40.831Z syslogpublisher.node1.demoeca.eca.local ECA 1 AuditLogs - {"eventCode":"0x40","path":"\\\\0050569960fcd70161594d21dd22a3c10cbe\\System\\ifs\\data\\policy1\\search\\cow.txt","protocol":"SMB2","server":"node001","clientIP":"1 172.31.1.131 07/07 16:59:40.461
How to view Syslog forwarding Statistics
- NOTE: No log exists to see events within the ECA. The forwarding feature uses programmatic access to an internal message bus that is not exposed to viewable.
- To view statistics of each ECA nodes forwarding function run this command on node 1 of the eca cluster after logging as the ecaadmin user.
- ecactl cluster exec "ecactl logs --tail 20 syslogpublisher"
- Each node will output the events it received for forwarding and the number of files it sent to the configured syslog server
- example
- In the example below the Sent events shows the total all time and the rate per second over the last minute. Stats are updated each minute on each node. The example below shows a rate of 794 audit events forwarded per second over the last minute. The last event ts date is the date of the time stamp indicating when the event itself was created on the cluster. This gives you an idea of how current relative to the current time versus the forwarding functions progress.
- syslogpublisher | 2020-09-21 12:58:28,269 AnalysisModule:146 INFO : Events Sent: | total 15040319 | rate 794.77 | last event ts: Mon Sep 21 12:58:28 UTC 2020
How to debug syslog forwarding when you syslog server does not receive messages
- These steps assume you have check firewalls and verified this is not the issue and that the correct forwarding port has been used on the ECA configuration.
- login to eca node 2, 3, 4, 5 etc.. since each node forwards syslog messages. You should use the stats command in the above section to determine which ECA node is showing sent audit events. Then use tcpdump on that node to capture UDP messages.
- sudo -s (to become root user)
- zypper in tcpdump (requires Internet connection to ECA)
- Monitor UDP syslog on the ECA node
- tcpdump -i eth0 udp port 514 (this command will display all UDP packets on port 514 to the console)
- The messages will look like this once a packet is captured with the destination host name or IP shown. Yellow highlight in the example.
- 09:54:43.379985 IP 172.31.1.135.45750 > syslog.internal.superna.net.syslog: SYSLOG local0.info, length: 664
How to Configure event filtering before forwarding
Use this configuration to select events from a specific path or below and forward only these events to the syslog server. This avoids a large volume of syslog data being sent when only a subset is needed. This same concept can be used to pattern match on a SID, event type in the raw syslog message. You will need to experiment with the pattern match for specific events.
The example below covers path based matching, to match against other fields setup forwarding first to syslog, then review the fields in the event messages to build matching filters for other fields such as user or event type.
- Review the syntax below and edit the log4j2.xml file to add your filter
- Example to match all syslog events for the path /ifs/data/smb01/test123
- login to eca node 1 as ecaadmin over ssh
- vim /opt/superna/eca/conf/syslogpublisher/log4j2.xml
- Insert a line using yellow highlighted example below and adjust the filter for your matching criteria.
- Save the file
- :wq
- done
- Push the configruation to all nodes
- ecactl cluster push-config
- Restart the syslog publishing container on all ECA nodes to reload the configuration
- ecactl cluster services restart --container sysylogpublisher --all
- done
Example filter for a path called /ifs/data/smb01/test123
After making a change to this file you must
- ecactl cluster push-config
- ecactl cluster services restart --container sysylogpublisher --all
Example of how to exclude audit records from /ifs/.ifsvar
After making a change to this file you must
- ecactl cluster push-config
- ecactl cluster services restart --container sysylogpublisher --all
Syslog Configuration Forwarding Parameters
Adavanced options for forwarding.