Dual Vector Warning Detection in 2.5.7 or later
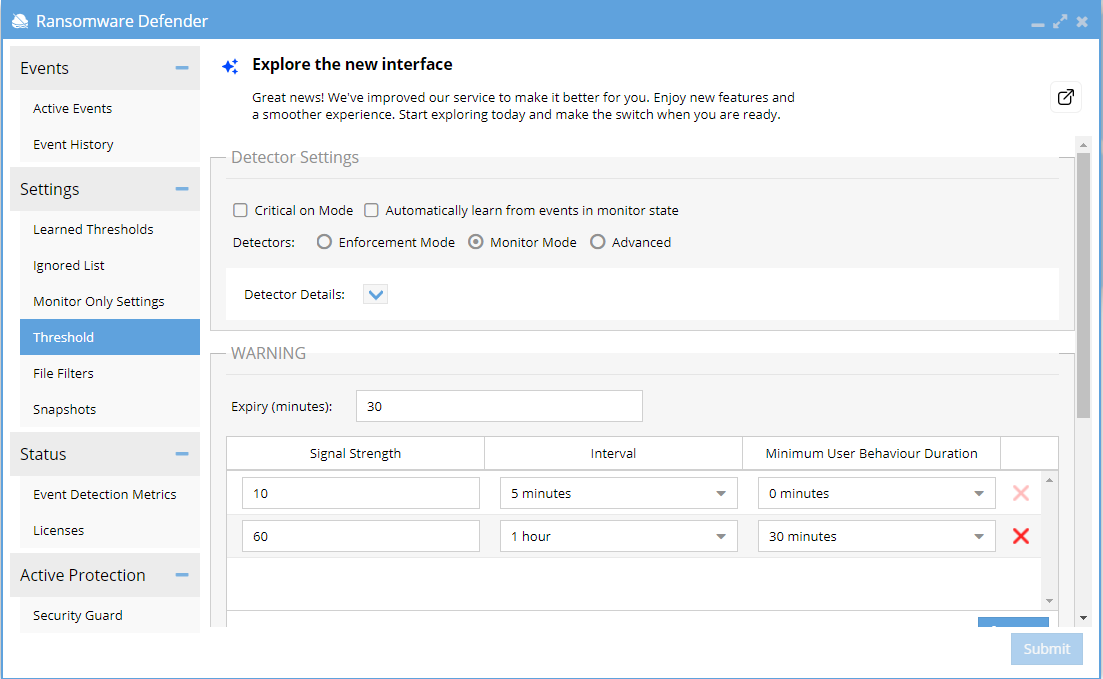
A new behavioral detection option looks for different behaviors within the Warning severity. This new option will add one additional pattern of suspicious user activity that is designed to ignore spikes in user detection signals and provides a new analysis vector on user IO behavior to generate warnings. This allows analysis of signals against a single and dual vector detection function. One vector may not trip a warning but the dual vector logic can detect and raise a warning.
This feature also allows customization to add N dual vector detection settings by clicking the add button to add a new dual vector setting. The product defaults to a single and dual vector setting. NOTE: Warnings trigger proactive snapshots on all shares accessible to the user.
In the screenshot example below
- Single Vector Warning is default from < 2.5.7 release setting. 10 signals or more in a 5 minute time window will trigger a warning but it does not matter when the 10 signals appear in the 5 minute window. This is a single vector detection.
- Dual Vector Warning sets a minimum duration for the activity and is intended to catch slower but longer duration behaviors. The default is 60 signals in a 60 minute window but the 60 signals must persist over a time period > than 30 minutes from the first signal timestamp to the last signal timestamp. This second vector (30 min) operates within the first window (1 hour). The dual vector will only raise a warning if both conditions are true. This is to protect against "slow burn" ransomware variants that will encrypt data at a lower rate.
- Additional Dual vector triggers can be added