Planning Guide for AnyCopy
Overview
The AnyCopy tool allows delegation of high performance data coping between clusters or within a cluster using SMB share level security. The roles include a read only user to view copy jobs, a user role and and administrator role that can configure pre and post scripts and review all copy jobs created by users. It is recommended to start by creating RBAC roles to meet your requirements for monitoring copy jobs.
SyncIQ polices created by AnyCopy will be created in copy mode only and will be named as follows <name of copy job>_User_Copy_<unique number>. The default behavior for all copy jobs create the policy of the duration of the copy and then clean up and delete the policy afterwards. This is done to avoid leaving many policies for manual clean up. There is a GUI option to leave the policy after the job.
SyncIQ default behavior will use all nodes in the cluster when replicating data, this will require the correct firewall ports are open between any clusters that are licensed for AnyCopy. If bandwidth usage is a concern between clusters, the network bandwidth feature on the cluster should be used to allocate bandwidth usage for AnyCopy.
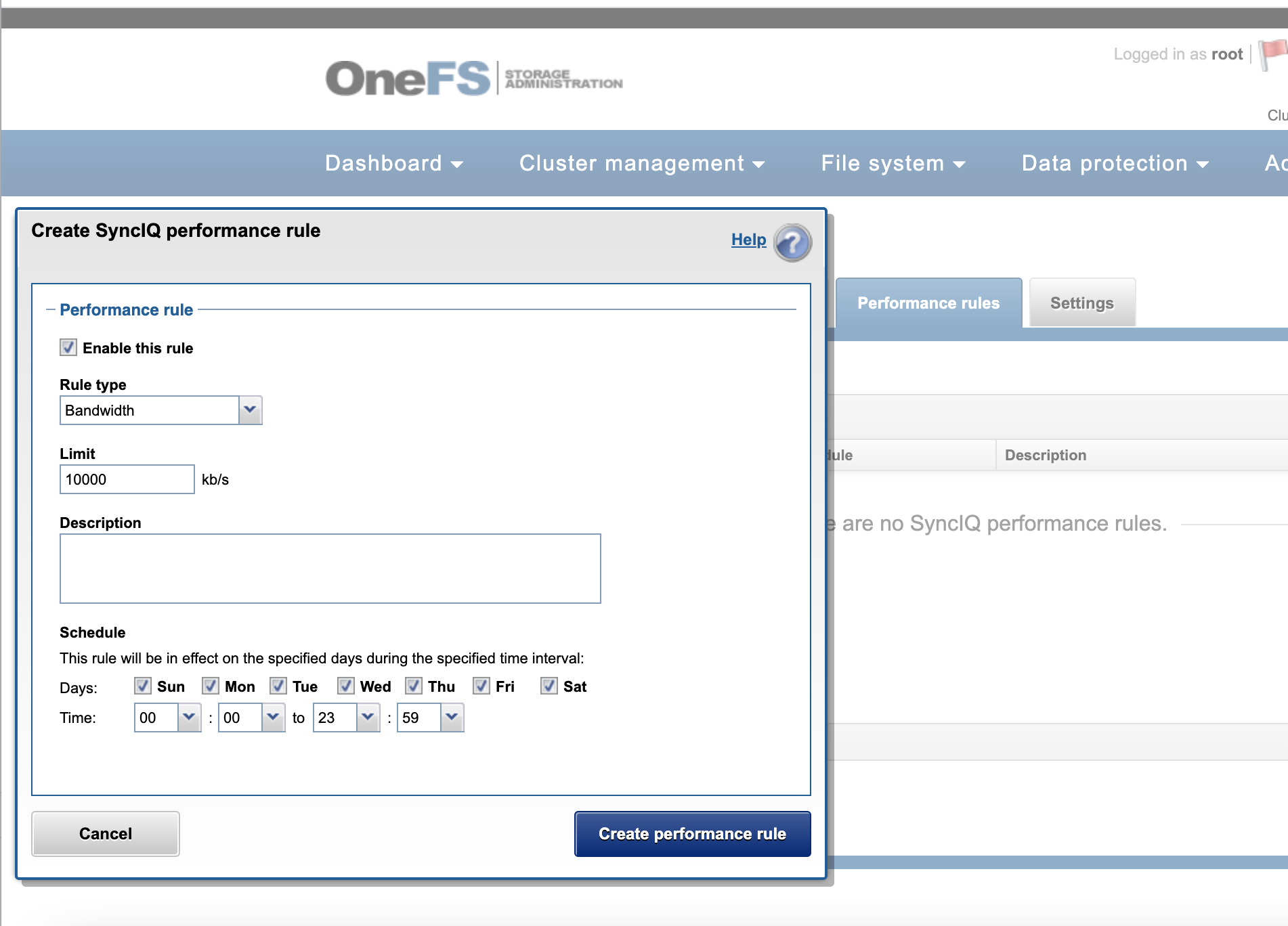
To change the default nodes used for SyncIQ on any policy that is created is possible using the SyncIQ settings tab to set the IP pool used by all synciq policies. This will allow restricting which nodes are used for AnyCopy policies that are created.
Data Security for Copy Jobs
The AnyCopy product is intended to maintain data security while allowing end users or administrators to start copy jobs using SyncIQ. This means user and administrator role within AnyCopy Eyeglass appliance must have SMB share access to any data on the source and target cluster to be allowed to configure a copy job. This maintains the data permissions already in place. This also means RBAC login is required to configure a copy job even if the user is logged in as administrator locally to the eyeglass VM. The copy job history will store the user name that created the copy job as an audit trail of the copy job creator.
If a user access to an SMB share is removed and they no longer have access to the SMB share, they will be blocked from running the job again from job history. Security is applied in all UI screens to validate access before allowing the job to run.
If everyone full control SMB share permissions are used, then the local admin user in Eyeglass will be allowed to create copy jobs. This is the only exception that otherwise require AD login via RBAC to Eyeglass to auto detect SMB groups and share level access. NOTE: NTFS ACLs are not used to restrict selection of folders for source or target paths.