- What's New
- Key Features:
- Built in Roles and user accounts:
- Use Cases for Custom Roles:
- Local Eyeglass OS user accounts:
What's New
- Release 2.5.6 20258 or later has simplified adding users and groups to roles by validating the SID or GID in the GUI before saving the role. Using the SID and GID now allows AD group names to include spaced or some special characters.
- The user name to login can use any syntax with any case of the login without any special requirements example domain\username or username@domain can be used without regard for the AD UPN value of the account.
- The upgrade to this release will convert the RBAC file to include SID and GUID automatically without any user actions to switch to this new role mapping implementation.
Key Features:
Role Based Access Control (RBAC) for Eyeglass allows any role combination to be created based on Eyeglass desktop icons. Custom roles can be created to meet any requirement of access to Eyeglass features:
- Default admin user has all privileges
- Default read-only role can see all icons
- Create roles and assign icons of functionality
- Map to user or group in AD, local Isilon/PowerScale users and groups.
- All authentication is done through PowerScale API to an authentication provider, and SMB AD password validation to access zone SmartConnect FQDN's
Built in Roles and user accounts:
Eyeglass ships with built in roles and users as follows:
- admin
- Has all permissions for all products
- Default password 3y3gl4ss
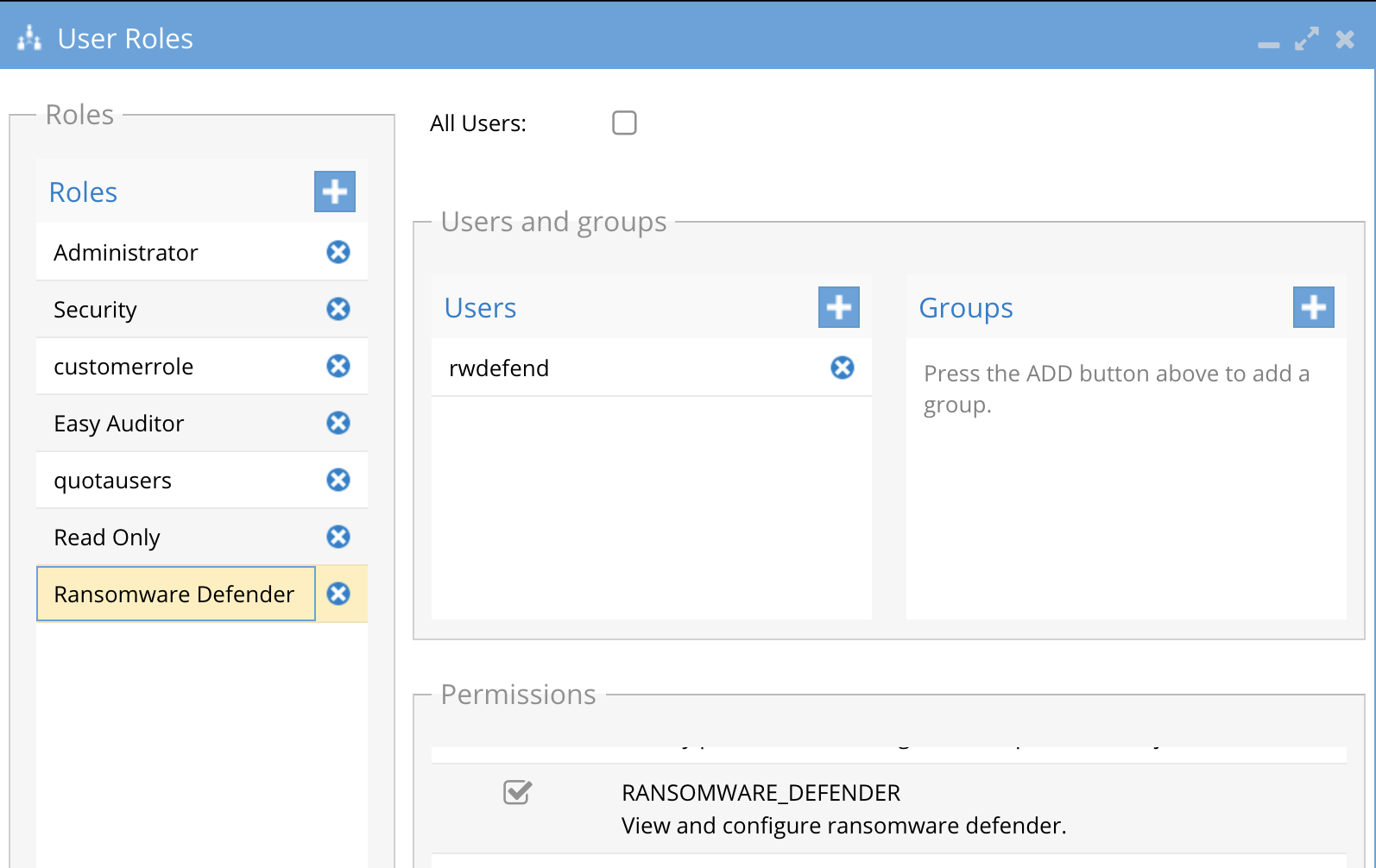
- rwdefend
- Assigned the builtin role Ransomware Defender with ability to manage and monitor Ransomware Defender product
- Default password 3y3gl4ss
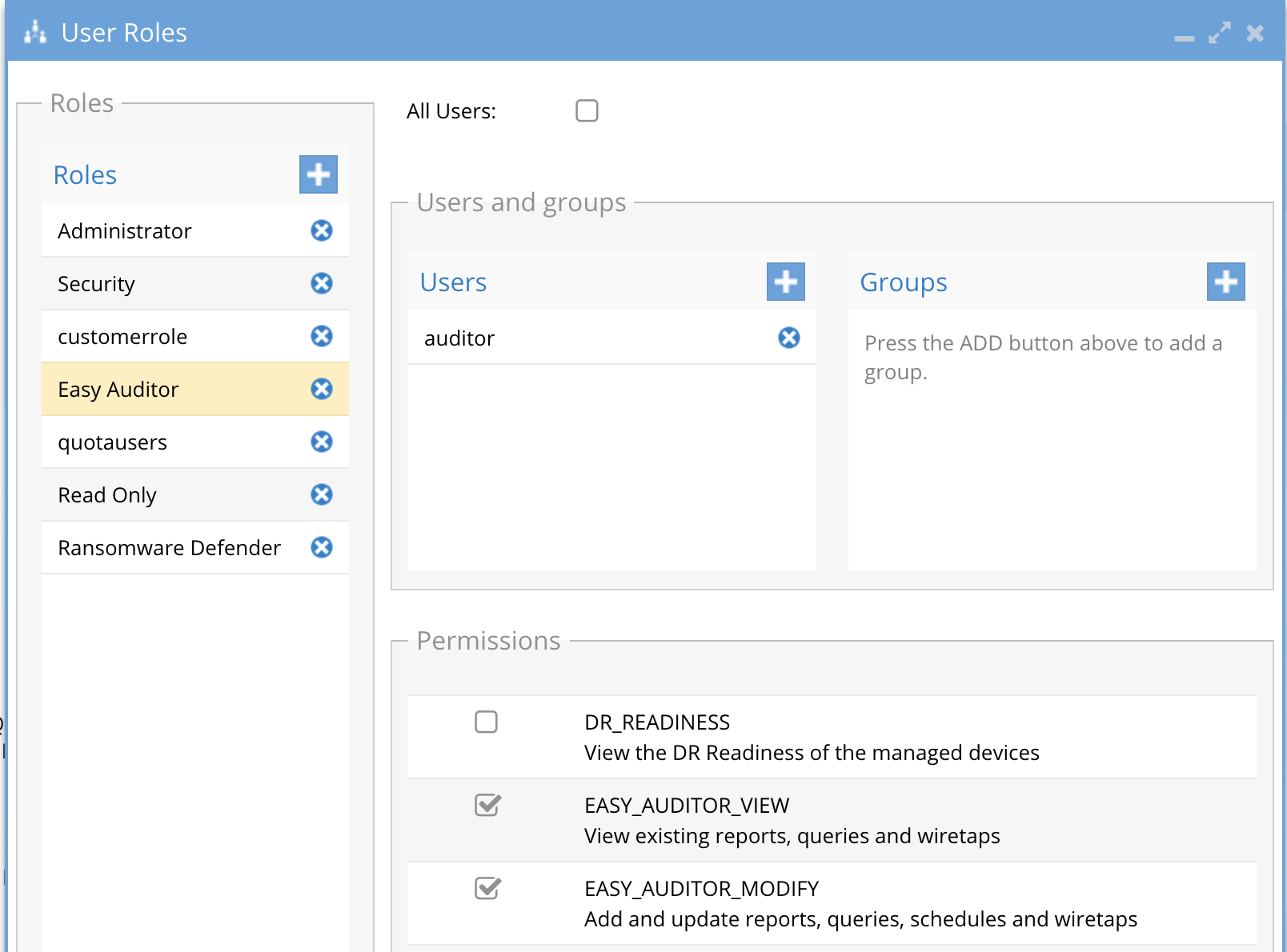
- auditor
- User has read and modify permissions within the Easy Auditor application
- Default password 3y3gl4ss
- Assigned the Auditor builtin group role
-
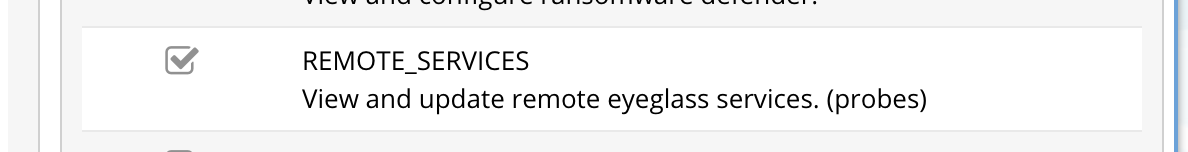
- This also includes the manage remote services icon to see Eyeglass clustered agent status
Use Cases for Custom Roles:
- Monitoring only -readonly role
- Departmental login for DR readiness view
- Security for Ransomware monitoring (Ransomware Defender)
- Unlock my files Help desk (Cluster Storage Monitor license)
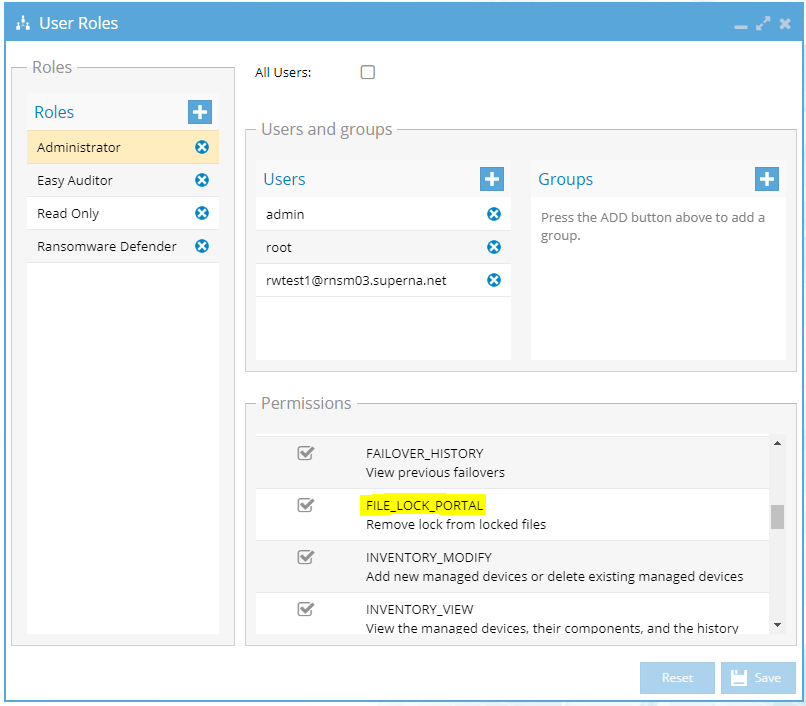
- Use this permission to create a Help desk role for unlock my files portal
- Auditing for file audit (Easy Auditor)
- Failover only administration functions (i.e can not add new clusters)
- Logging and monitoring only
- Storage monitoring only (no DR functions)
- Cluster reporting only (no DR functions or storage monitoring)
- Centralized security to match PowerScale Role based Access groups to include DR functions with SyncIQ
Eyeglass Authentication Options
Local Eyeglass OS or Proxy Login are the two types of login Eyeglass supports. Local Login uses a user account created in the OS. Proxy Login options use PowerScale as the authentication provider, and proxies the user id and password to Ision for authentication validation and group membership. Custom roles can be created in Eyeglass that can use local or proxy login for access control.
The following sections describe how to configure and use Local Eyeglass OS or Proxy Login.
Local Eyeglass OS user accounts:
When entering local users we recommend the syntax UNIX_USERS to represent the domain. Example - UNIX_USERS\read (this is a convention to ensure its easy to know where this user will exist for authentication)
How to create new local user on the appliance:
- Ssh admin@x.x.x.x
- Sudo -s (enter admin pwd)
- useradd <user name>
- passwd <user name> (to set a password)