Introduction to this Guide
Overview
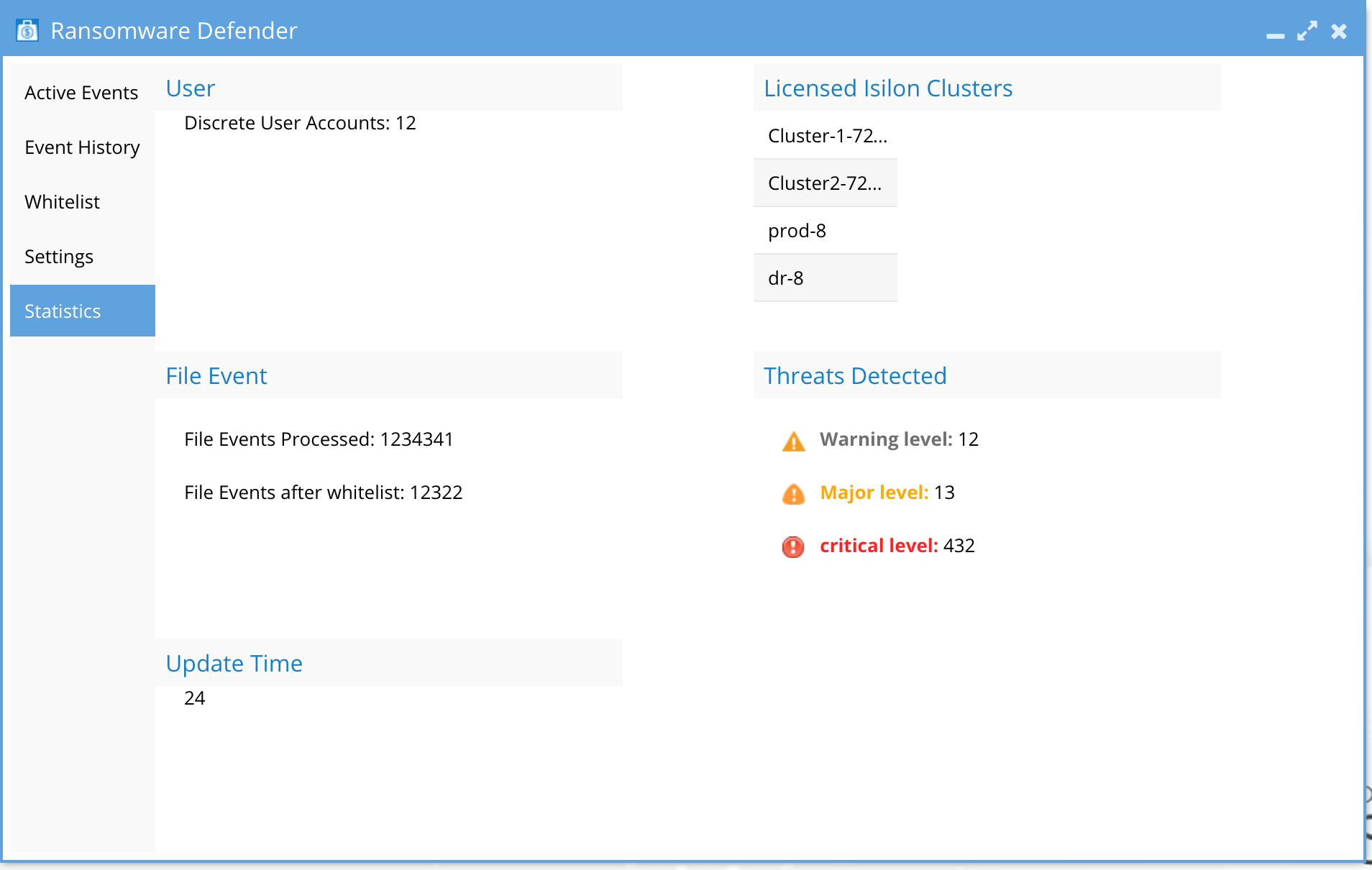
This guide covers the configuration, setup, and monitoring of Ransomware Defender. The solution is deployed with a 3 VM cluster, that processes PowerScale & ECS audit files, with an active active design for maximum availability to survive hardware or software failures.
The active defense solution monitors for user behaviors that are malicious, consistent with Ransomware encryption techniques of customer files. Network-attached SMB mounts on user workstations exposes PowerScale critical data. It can also protect object storage on Dell ECS.
Three levels of detection are possible Warning, Major, and Critical with automated defense options increasing with detection levels.
Abbreviations:
- ECA: Ransomware Defender Application - the entire Ransomware defender stack that runs in a separate VM outside of Eyeglass.
- ECA: Eyeglass Clustered Agent
Prerequisites, Requirements, and Feature Limitations:
Prerequisite:
Read this first:
It's assumed that all workstations and other entry points for Ransomware are running current virus malware software. Ransomware Defender is a second line of defense product.
ECA Installation Requirement:
The Superna Eyeglass Clustered Agent (ECA) vAPP used by Ransomware Defender therefore a Single host for ECA VM’s OR multiple hosts for a high level of availability is required (See the Eyeglass Clustered Agent vAPP Install Guide.)
Licensing Requirement:
Registered PowerScale or Dell ECS clusters licensed for Eyeglass DR qualify to be licensed with Ransomware Defender. Each writable cluster requires an agent license and agent maintenance. The license manager is used to assign licenses.
A system alarm will be issued in the case of insufficient licenses and more writable clusters are detected in the audit event messages.
Note: A cluster can be monitored by the ECA without a license when it's the cold or DR cluster.
Additional Requirements:
- Eyeglass VM installed.
- Cluster discovery licenses (per node or per cluster) that need to be managed by the Eyeglass instance.
- Ransomware feature license and a Ransomware agent license for all writable clusters protected by Ransomware Defender.
- CPU limits applied to ECA cluster object in vCenter.
- Hardware recommendation (see install guide).
Feature limitations:
- SMB shares created with variable expansion will only support %U for snapshot creation.
- NFS lockout is supported but disabled by default unless IGLS to enable.
- NFS lockout requires license lists to use ip address to correctly lockout.
- Object storage and all buckets