Administration Guides
How to Manage Threat Detectors - Advanced Consult Support
Home
Overview
This is new advanced option in 2.5.7 or later releases. The Ransomware Defender solution is built on many threat detectors that detect user behavior, honeypot files and banned file extensions. This is an option that should never be changed without support advising when to use this option. Changing these settings can disable detection without understanding the impact of the changes.
How to Disable all threat Detectors
- This option will disable all threat detectors and will disable all detections for all severities. This option should never be used unless you need to temporarily need to disable detections.
- Login to Ransomware Defender
- On the Settings --> Threshold tab
- Click Monitor All and then the submit button. NOTE: This disable all detections until you change back to Enable All Option and click submit button again.
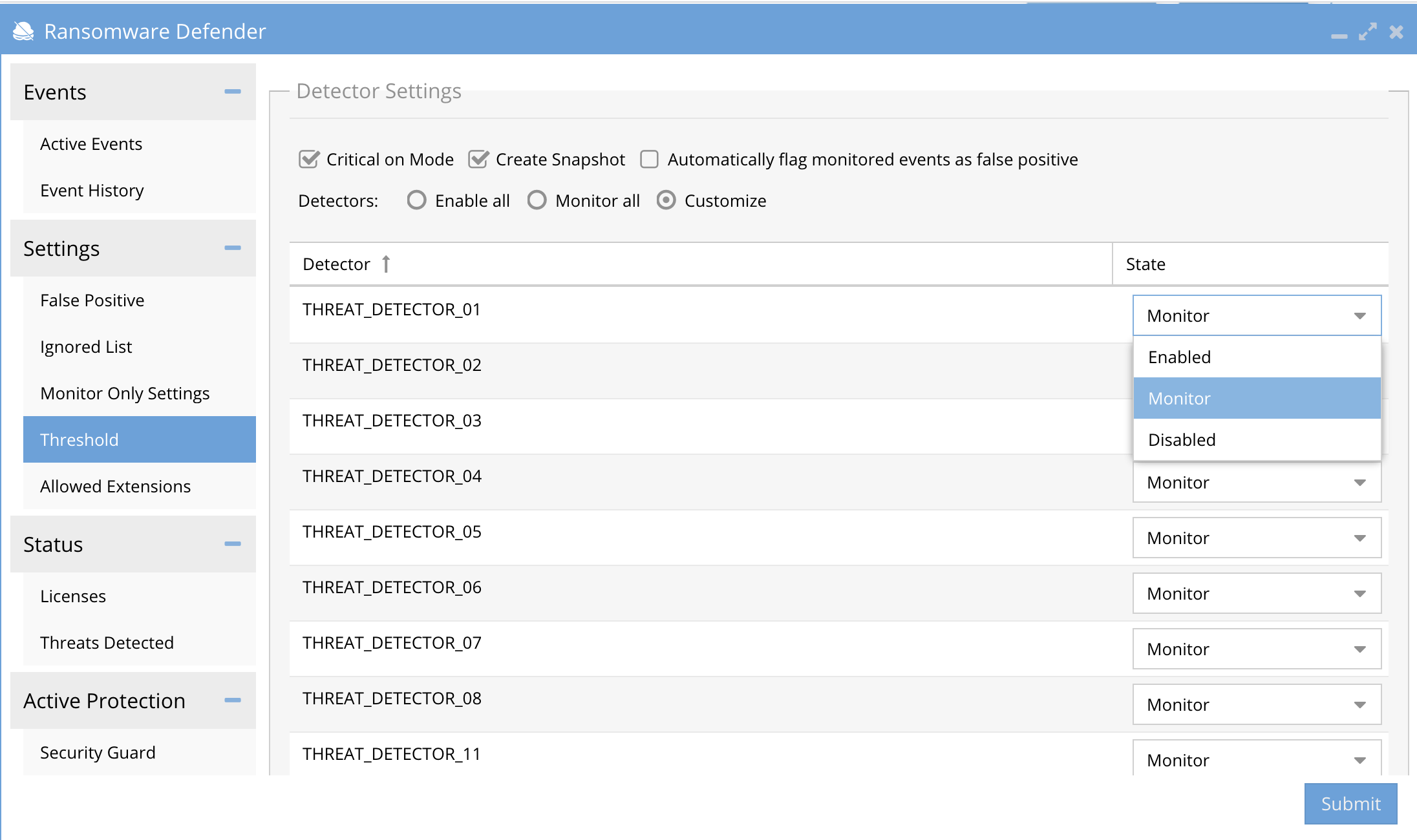
How to Customize each Threat Detector State
- The customize option allows individual threat detectors to be disabled and switched into Monitor only mode. Monitor only mode allows the detector to alert, snapshot but it will not lockout. If the threat detector is disabled it will no longer protect the file system. NOTE: These settings should not be changed without consulting with support, any misconfiguration can disable protection of your file system.
- See the screenshot below on how to switch the mode of each threat detector.