- Ransomware Defender Protection Modes
- Best Practise
- How Ransomware Defender Protects your Data
- How to determine threat response settings to meet your Company’s Risk Profile
- Threat Response Settings
- Automated Threat Responses Settings
- Recommended Threat Response Setting for Low Risk tolerance
- Recommended Threat Response Settings for Medium Risk tolerance
- Recommended Threat Response Settings for Medium-High Risk tolerance
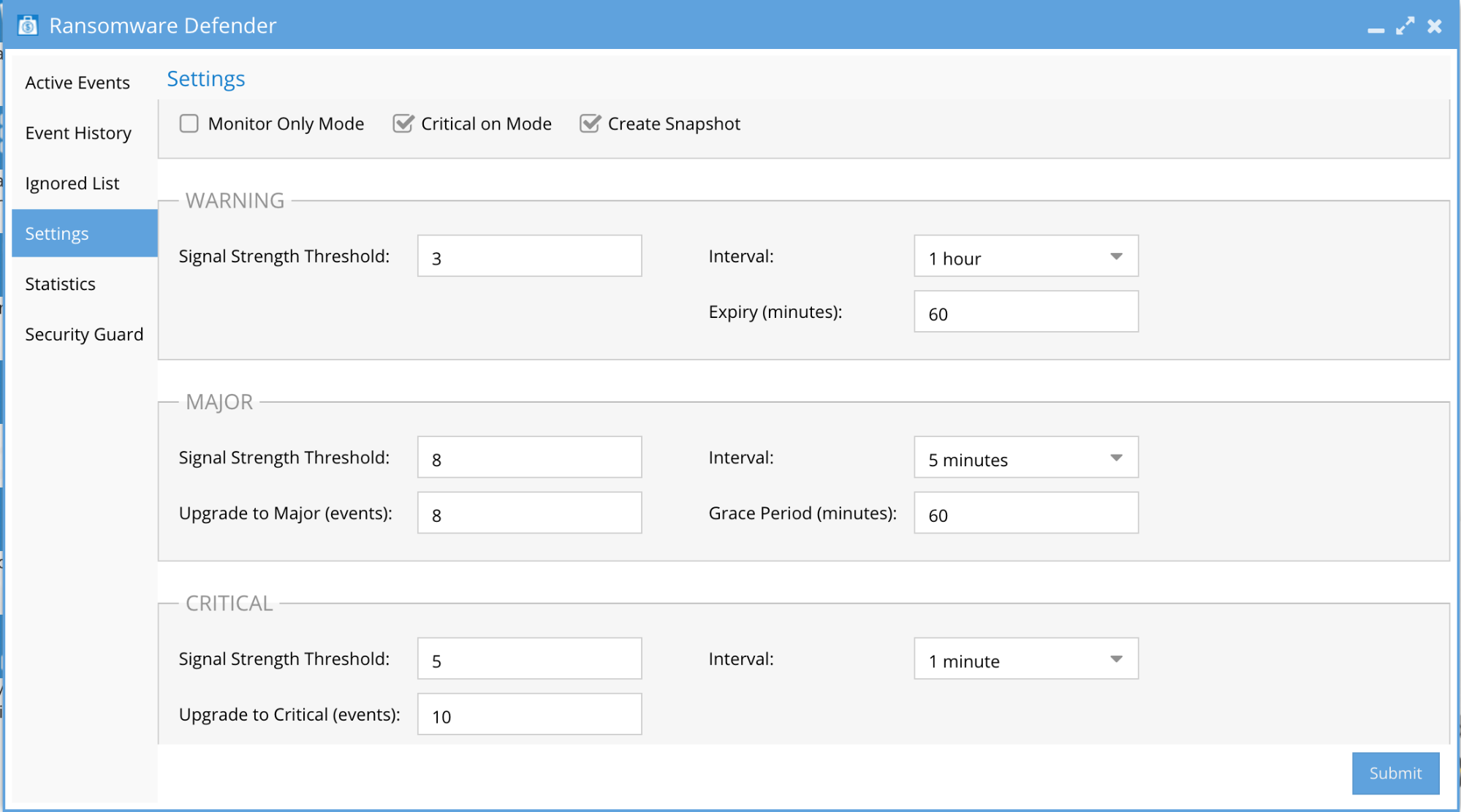
Ransomware Defender Protection Modes
The 3 different modes all protect the file system and each mode determines how you should respond to alarms. The target events per day should be < 1 per day and see the process below to achieve this with learning mode.
NOTE: Enforcement mode is not required to protect the file system. All modes protect the file system.
Best Practise
- Use Monitor mode if you do not have the ability to assess threats 7/24
- Only Use enforcement mode if you have 7/24 SOC or if you can tolerate a user being locked out of the file system until an administrator can assess the threat.
- Use Learning mode until detections per day < 1 and use learning mode if you introduce a new application to learn it's behavior.
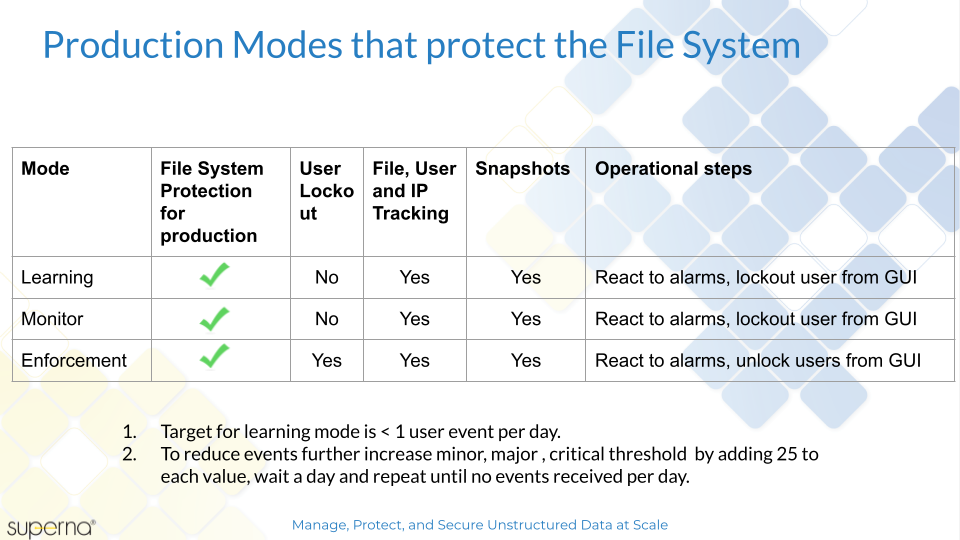
How Ransomware Defender Protects your Data
- 8 methods protect the file system as outlined below.
- User Behaviour based detection proven technology based on independent 3rd party testing of live Ransomware attacks https://www.av-comparatives.org/?s=superna
- Dynamic Realtime Learning of Behaviours
- Honey Pot tripwire
- Crowd Sourced file extensions (> 2500 updated monthly)
- Slow attack detection
- Burst attack detection
- Automated Escalation response
- Inbound API from external detection engines (IDS, IPS, Endpoint, XDR , SIEM)
How to determine threat response settings to meet your Company’s Risk Profile
The Ransomware Defender product has several options to tune the detection and response to a Ransomware attack. The more sensitive the detection the more likely a false positive can occur. Threat response options are outlined below with business impact considerations for each option. This section should be reviewed to determine how to configure the product in your environment.
The section below outlines the recommendations for each threat detection level.
Threat Response Settings
Automated Threat Responses Settings
- Critical Severity - Lockout of user account - is immediate
- Major Severity - A delayed lockout Grace Period is set ( user account lockout delayed by X minutes)
- Auto Snapshot of the file system at share path - on detection of ANY severity
Recommended Threat Response Setting for Low Risk tolerance
Monitor Only Mode enabled - Email Alerts
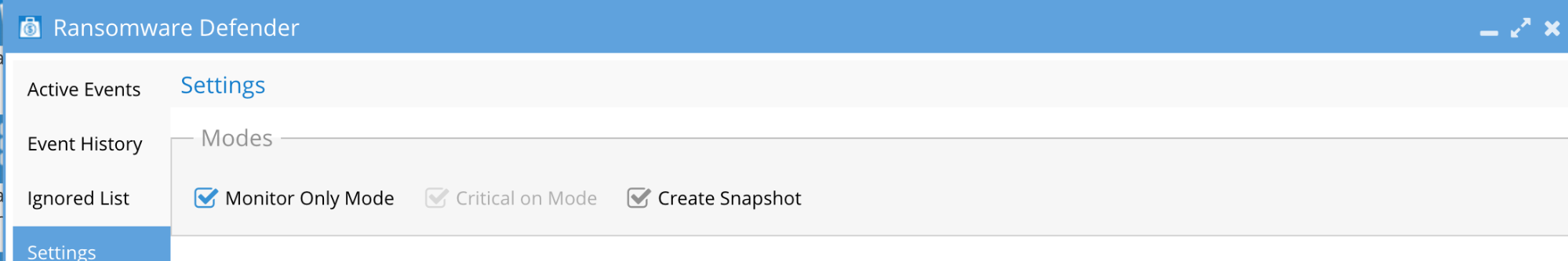
Recommended Threat Response Settings for Medium Risk tolerance
NOTE: In this configuration files can be encrypted up to the Grace Period value, but a snapshot has protected the file system at the point of detection allowing for accelerated recovery of files. The security event lists all affected files to build a recovery list of files.
- “Critical on Mode” uncheck to disable immediate lockouts
- Set Major delayed lockout timer (Grace Period) to a value that allows an administrator to reach and determine if lockout should occur (In the Screenshot below the “Grace Period” is set to 60 Minutes)
- “Create Snapshot” Mode enabled
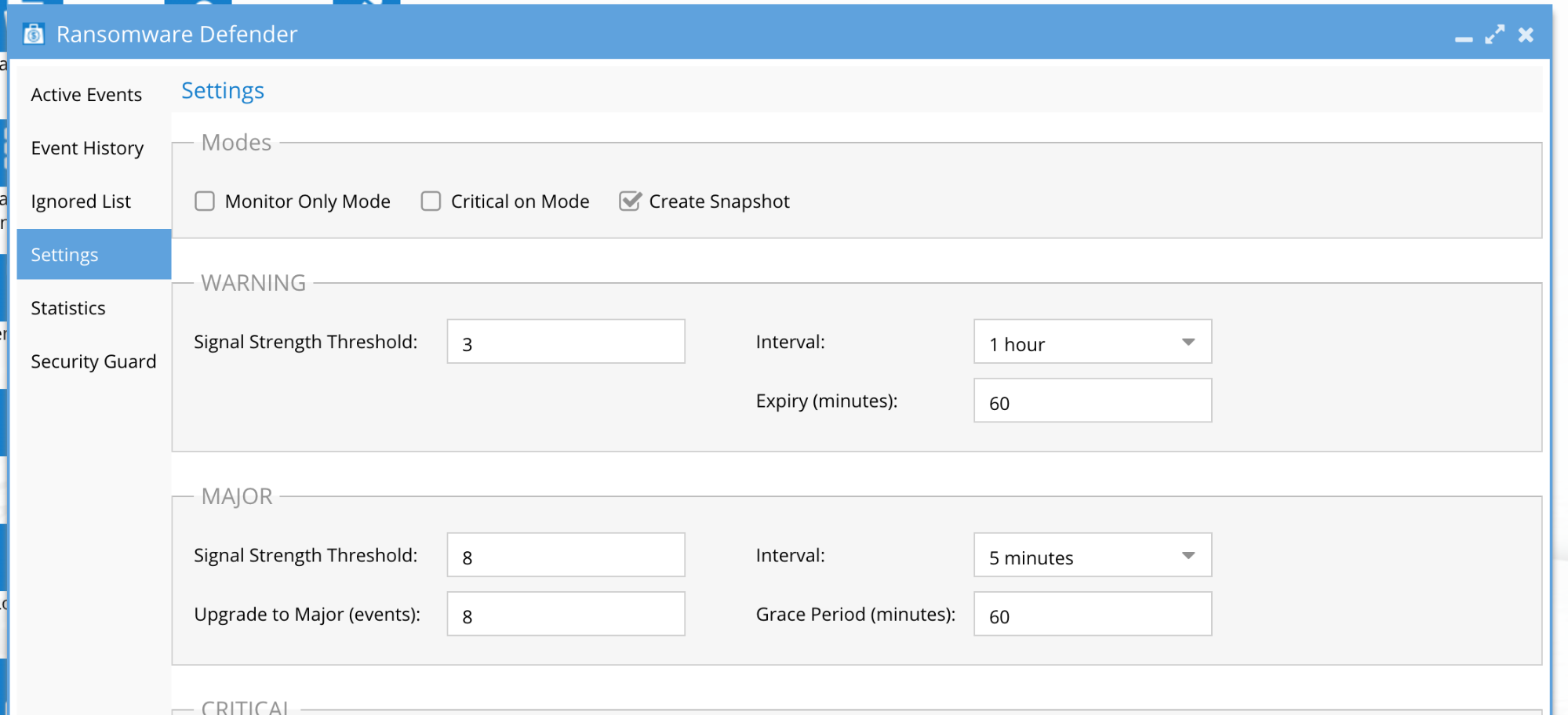
Recommended Threat Response Settings for Medium-High Risk tolerance
NOTE: In this configuration files users are locked out immediately, the risk of false-positive with a lockout is higher.
- “Critical on Mode” checked to enable immediate lockouts.
- Set Major delayed lockout timer “Grace Period” to a value that allows an administrator to reach and determine if lockout should occur. (In the Screenshot below the “Grace Period” is set to 60 Minutes)
- “Create Snapshot” mode enabled.