How To Configure HoneyPot file Tripwire
- How to Configure Honeypot traps feature
- Overview
- Requirements
- Configuration
- Files at Base of SMB Share Configuration
- Sub Folder configuration
- How change the file name used for Honeypot files
- Ransomware Defender for ECS - Honeypot Configuration
- Object Honeypot configuration
- How to test Object honeypot
- Ransomware Event for Object Honeypot
How to Configure Honeypot traps feature
This feature allows a new type of detection based on honeypot files placed anywhere in the file system. This would be used where very sensitive data exists and will allow faster detection times for these locations in the file system. They can be placed in as many locations as needed.
- Can detect slow attack variants of Ransomware, or non-standard IO patterns.
- Detects file access to encrypt the file itself, and allows immediate critical lockout response.
- Can detect ransomware even when user behavior does not detect the initial attack pattern.
- Can reduce the number of files encrypted with any IO that touches these honeypot files, to reduce file system damage.
Overview
- Placed at the root of SMB or NFS mounts since this is the first place Ransomware can locate files since drive letters are mounted to the base of the SMB share.
- Uses files as bait for Ransomware, and detects atypical IO access patterns to any of the files in the folder along with many IO access patterns, to find variants that do not use a pattern previously seen before.
- Needs only 1 Signal to raise a Security Event. With Monitor Mode OFF / Critical Mode OFF one signal will place the event into the Major - DELAYED Lockout threshold. With Monitor Mode OFF / Critical Mode ON one signal will place the event into Critical threshold for immediate lockout.
Requirements
- A minimum of 3 files should exist in the honeypot at the base of the share, to trip the detector.
- Each share that needs protection needs the files created
- Create honey pot files at the base of the share and in a subfolder for maximum protection.
Configuration
Place the following files anywhere in the file system following the procedure below. From Windows Client repeat these steps on each SMB share that requires Honeypot files configured.
Best Practice: Always create files at the base of the share and in at least 1 subfolder.
NOTE: The file pattern to match by default is *igls-honeypot-*
Files at Base of SMB Share Configuration
- Mount the SMB share where you want the honeypot files: smb01 (example share) to drive letter z:
- Using cmd command prompt cd to this mount point. e.g. Z:\
- Create 3 files under the SMB share with these exact names :
- igls-honeypot-1
- igls-honeypot-2
- igls-honeypot-3
Sub Folder configuration
- Mount the SMB share where you want the honeypot files: smb01 (example share smb01 is /ifs/data/smb01 ) to drive letter z:
- Using cmd command prompt cd to this mount point. e.g. Z:\
- Created a folder name: igls-honeypot in this smb01 share (will be created with path: /ifs/data/smb01/igls-honeypot)
- Create 3 files under the igls-honeypot subfolder:
- igls-honeypot-1 - Path: /ifs/data/smb01/igls-honeypot/igls-honeypot-1
- igls-honeypot-2 - Path: /ifs/data/smb01/igls-honeypot/igls-honeypot-2
- igls-honeypot-3 - Path: /ifs/data/smb01/igls-honeypot/igls-honeypot-3
How change the file name used for Honeypot files
- Use this procedure to change the name of the honeypot file names needed for detection.
Procedure:
add the following to docker-compose.overrides.yml:
nano /opt/superna/eca/docker-compose.overrides.yml
Paste the below text into the file and make sure the spaces are respected exactl as shown below. Each indent is 2 spaces
add the following to eca-env-common.conf: (note any file that contains the string below will trip the detector this string can be changed from this example)
nano /opt/superna/eca/eca-env-common.conf
export ECA_RWD_HONEYPOT_DIR_PATTERN="file.docx"
In this example you would create files named 1-file.docx, 2-file.docx etc..
Follow the steps above to create files at the base of a share and in a subfolder under the share.
- This will require a cluster down and up after the edits are complete
- ecactl cluster down
- then
- ecactl cluster up
Ransomware Defender for ECS - Honeypot Configuration
- How to Configure Honeypot traps feature
- Overview
- Requirements
- Configuration
- Files at Base of SMB Share Configuration
- Sub Folder configuration
- How change the file name used for Honeypot files
- Ransomware Defender for ECS - Honeypot Configuration
- Object Honeypot configuration
- How to test Object honeypot
- Ransomware Event for Object Honeypot
Object Honeypot configuration
- Create minimum 3 honeypot objects and place them directly under the bucket with the following naming convention
- igls-honeypot-1
- igls-honeypot-2
- Igls-honeypot-3
- NOTE: before creating those honeypot objects on ECS S3 bucket, it is recommended to disable the honeypot detection temporarily to avoid False Positive detection for honeypot during object creations. To disable that, follow this steps:
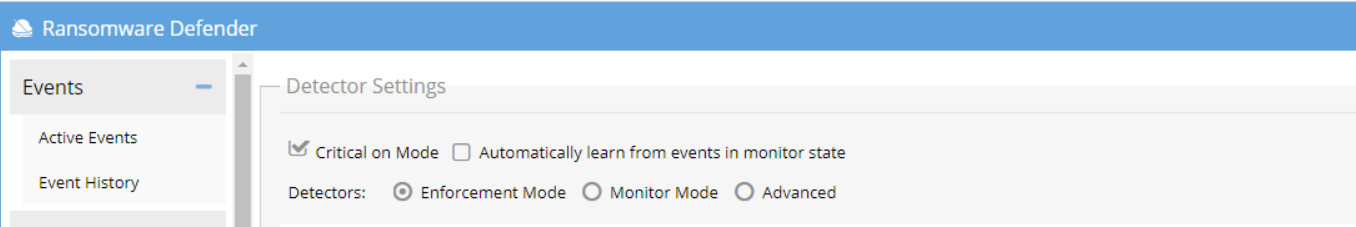
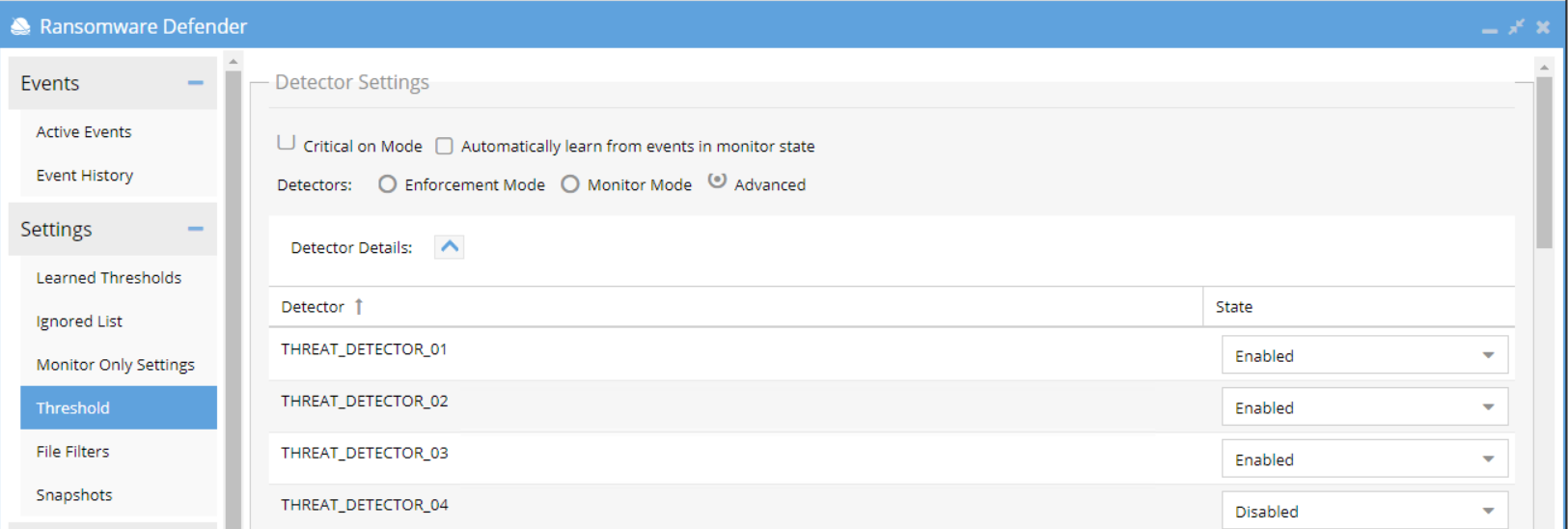
- From Eyeglass WebUI ⇒ Ransomware Defender ⇒ Settings ⇒ Threshold menu, select Advanced radio button
-
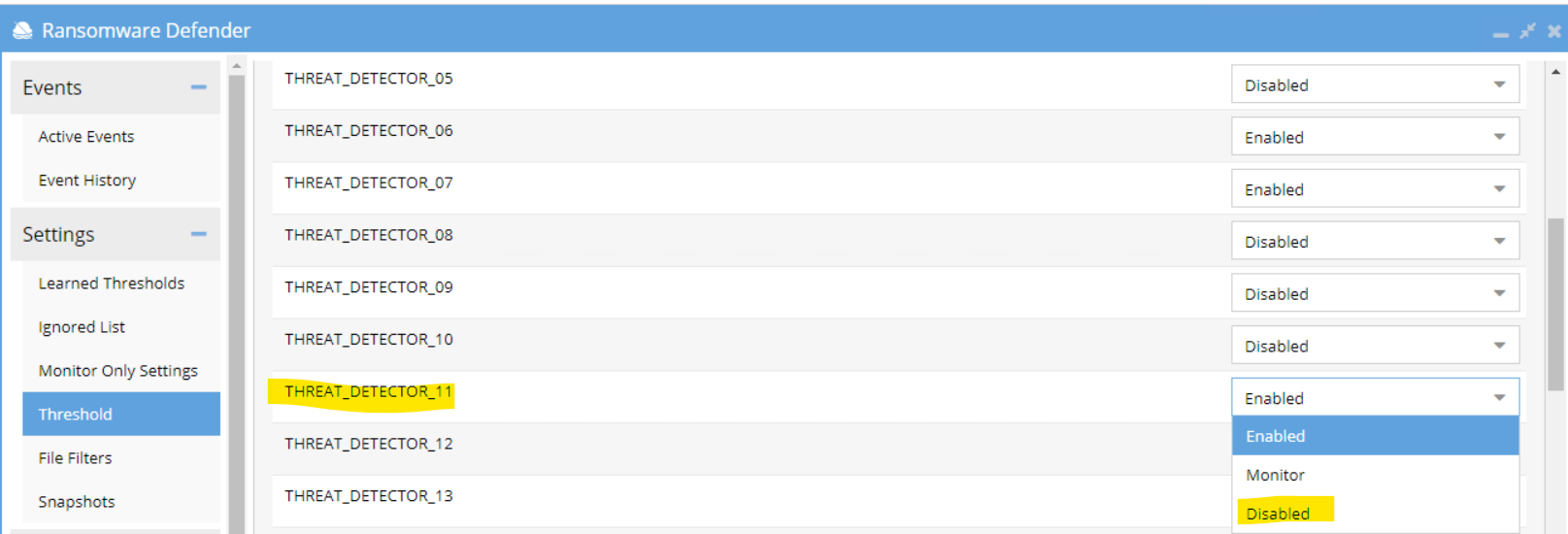
- Then for THREAT_DETECTOR_11, set it to Disable
-
- Click Submit button to apply the new setting
- Then to create those honeypot objects, we can use S3 browser tools (e.g. Cyberduck) .
- Connect to ECS S3 bucket using Cyberduck (or other S3 browser tools. The following example is based on Cyberduck interface)
- Browse and go to bucket where we want to place those honeypot files
- Right click the space inside that bucket, and select from menu => New File and provide the name igls-honeypot-1.
- Repeat for igls-honeypot-2 and igls-honeypot-3
- Example
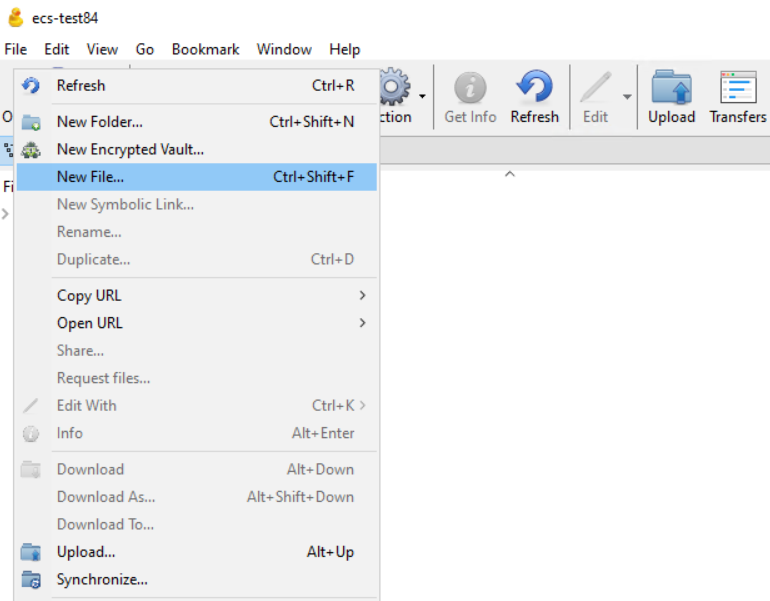
- Once created, it will be something like this:
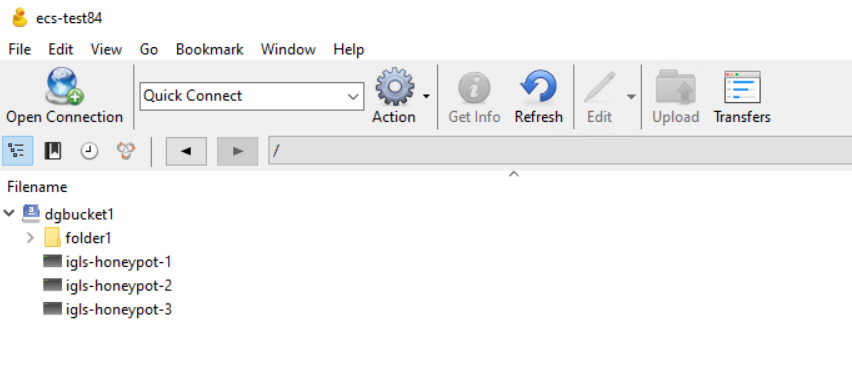
- Repeat those steps #2 and #3 to place honeypot object under different buckets that we want to protect with honeypot
- Once done, we need to set the THREAT_DETECTOR_11 back to ENABLE state:
- From Eyeglass ⇒ Ransomware Defender ⇒ Settings ⇒ Threshold menu, select Advanced radio button

-
- Then for THREAT_DETECTOR_11, set it back to Enable
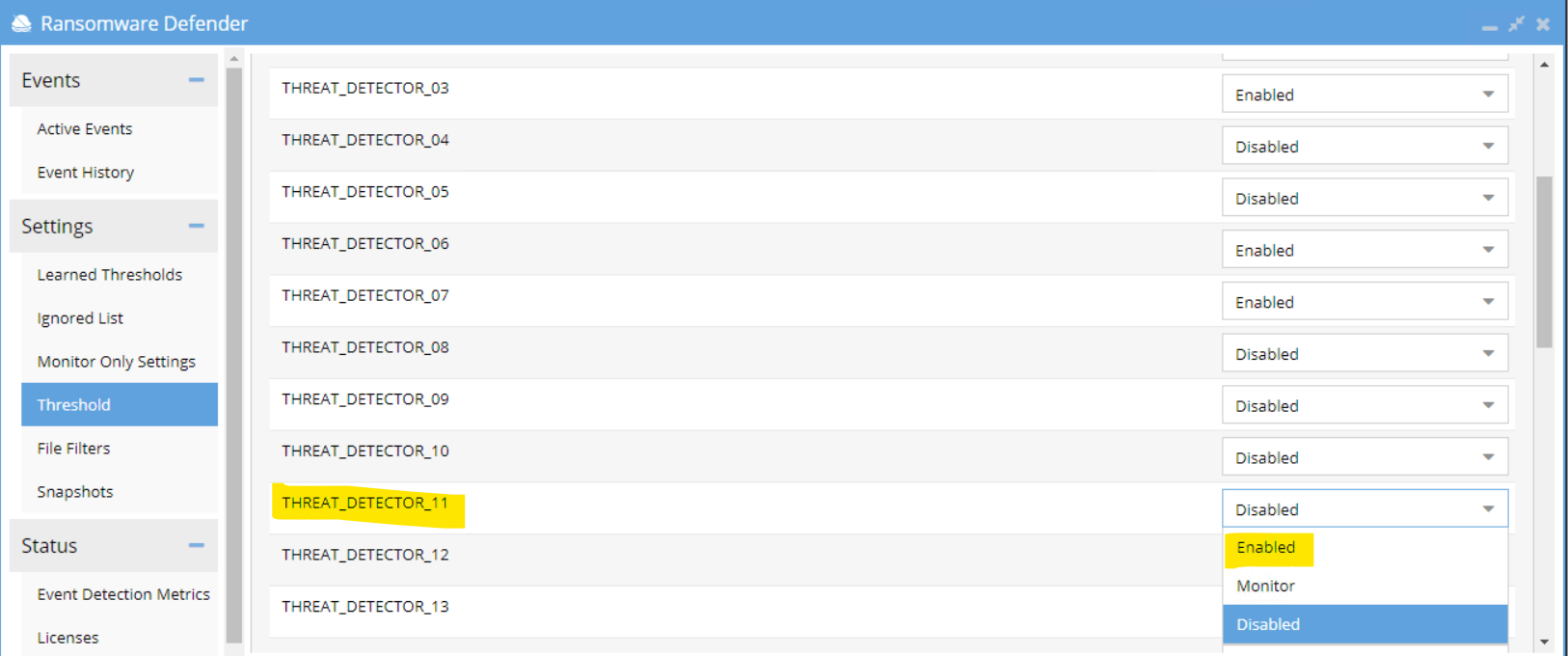
-
- Click the Submit button to apply.
How to test Object honeypot
The following steps are the two options to test honeypot
- Using Cyberduck, download those 3 honeypot objects to a local machine.
- Select those 3 honeypot objects and Right click and select Download from the menu
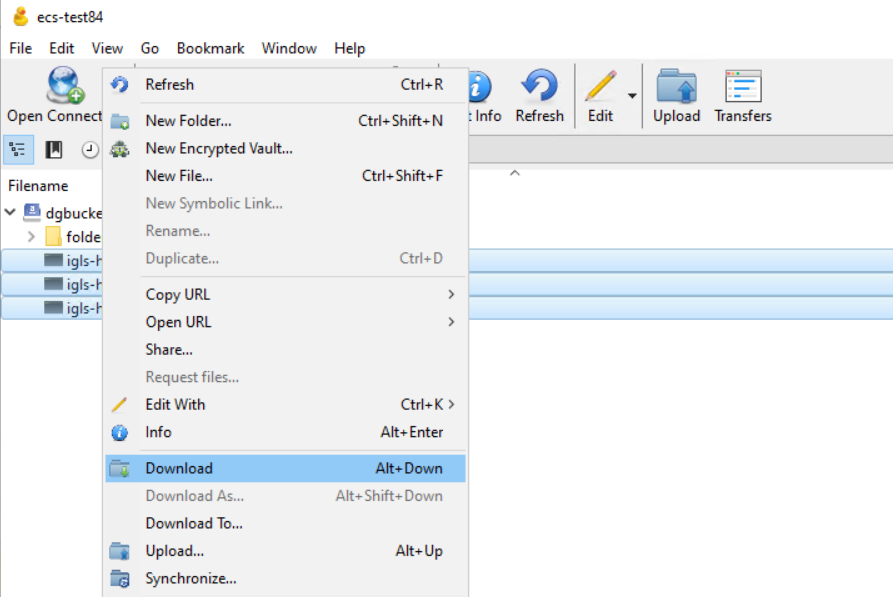
-
- Verify Ransomware Events from Active Events
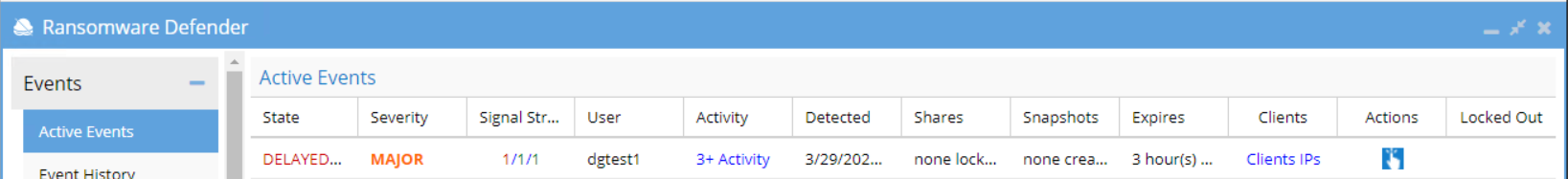
- Using Cyberduck, delete those 3 honeypot objects from ECS S3 bucket
- Select those 3 honeypot objects and Right click and select Delete from the menu
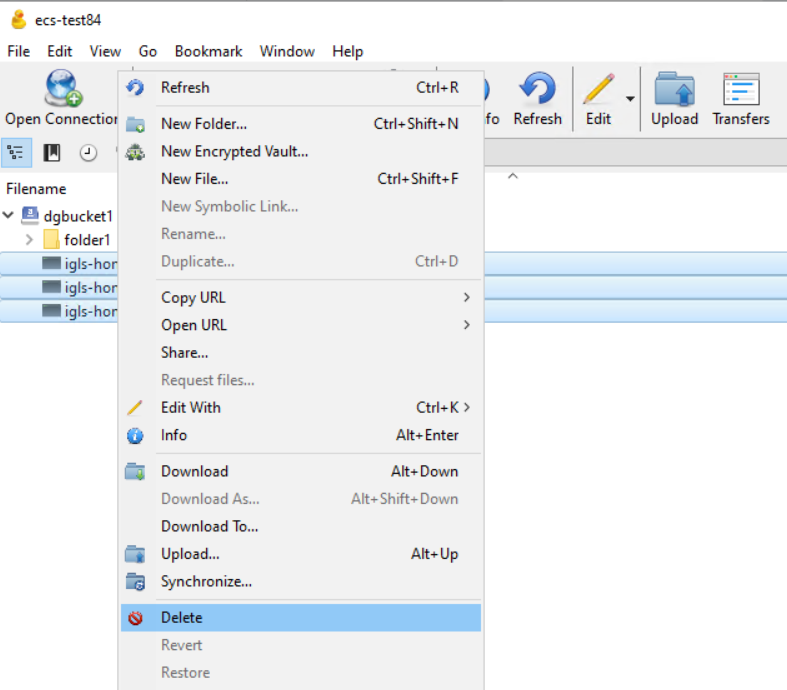
-
- Verify Ransomware Events from Active Events
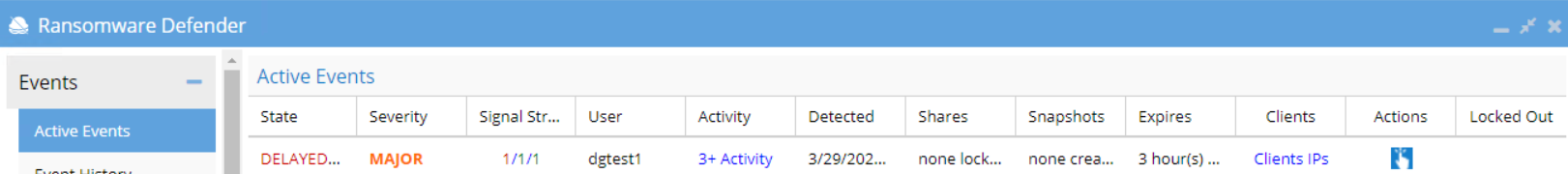
Ransomware Event for Object Honeypot
It needs only 1 Signal to raise a Security Event.
-
- With Enforcement Mode : ON and Critical on Mode : OFF, one signal will place the event into the Major - DELAYED Lockout threshold.
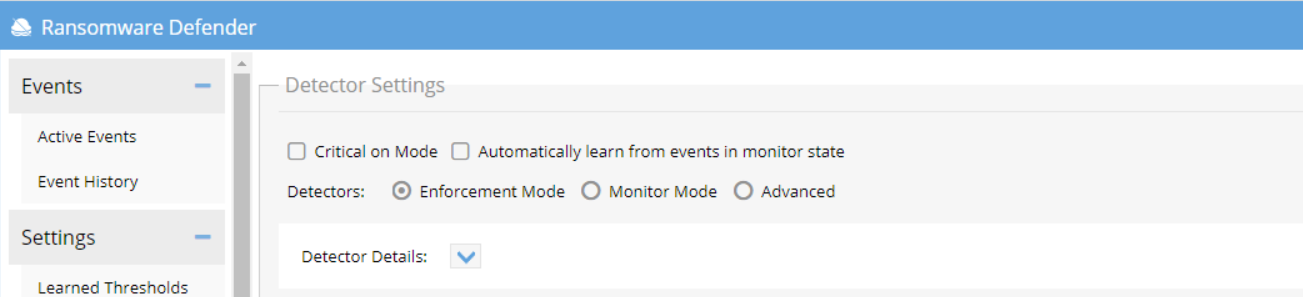
-
- With Enforcement Mode : ON and Critical on Mode : ON , one signal will place the event into the Critical threshold for immediate lockout.