How to Configure a Dell ECS and Data Protection Use Cases
- Overview
- Deployments Options
- Video Overview
- Smart Airgap with ECS Sync
- How to add Licenses
- How to add ECS to Eyeglass Inventory
- Security Guard
- Data Protection Use Cases
- Overview
- Backup Data on ECS
- Long Term Legal Hold Data
- Dell ECS Geo Drive
- Archive Data
Overview
This topic covers how to add an ECS cluster to Eyeglass inventory and license it for Ransomware Defender.
Deployments Options
- The ECS integration is based on the ECA deployment and allows an existing ECA cluster to be enabled for ECS event processing. See the installation guide here.
- Distributed ECA deployment is also possible to collect ECS clusters using a mini ECA deployment architecture to collect local web access logs and forward the events for centralized processing. See mini ECA guide here.
Video Overview
Smart Airgap with ECS Sync
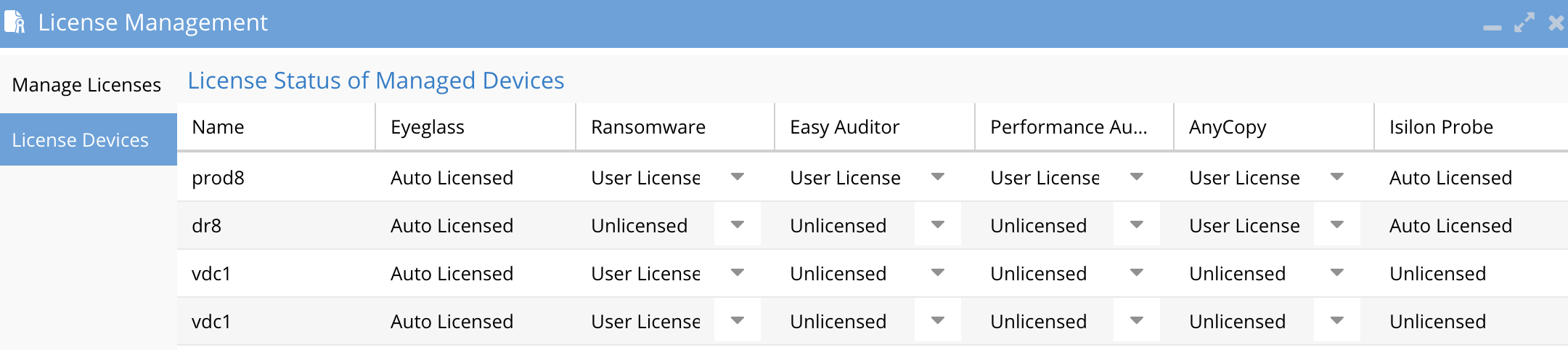
How to add Licenses
- Login to eyeglass as admin
- Open the License manager icon
- NOTE: Follow steps here to retrieve the license key with the order token.
- Upload the zip file ECS node licenses and accept the license terms
- Upload the zip file for the Ransomware Defender for ECS agent license and accept the license terms
- Open the License manager icon after the refresh
- Click the Licensed Devices tab
- Under the Ransomware Defender column, locate the ECS(s) and switch the license type to user licensed and click Submit
-
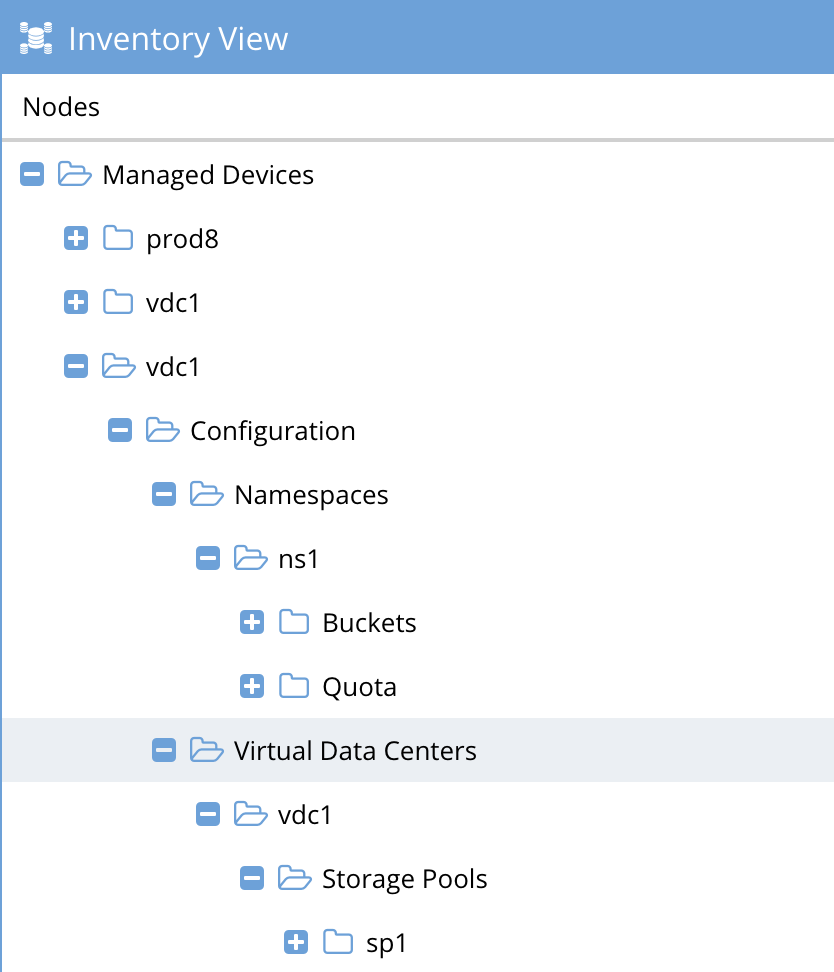
How to add ECS to Eyeglass Inventory
- Before You begin: Follow the minimum permissions service account creation in the minimum permissions topic here.
- Login to eyeglass as admin
- Click the Eyeglass Main menu , bottom left of console
- Click Add Managed Device
- Select the ECS tab
- Add the ip address of the ECS management IP, the eyeglass service account user and password.
- NOTE: A recovery service account user is needed in each name space that has a bucket. The service account(s) are entered in the object access section and must be added to each bucket with read and write permissions to the bucket.
.png)
- Click Submit
- Answer yes or no to add an additional device.
- Inventory collection job will appear in the Job icon on the running jobs tab.
- Open the inventory icon to verify that ECS inventory completed successfully. The inventory can be expanded to show the nodes, name space and storage buckets.
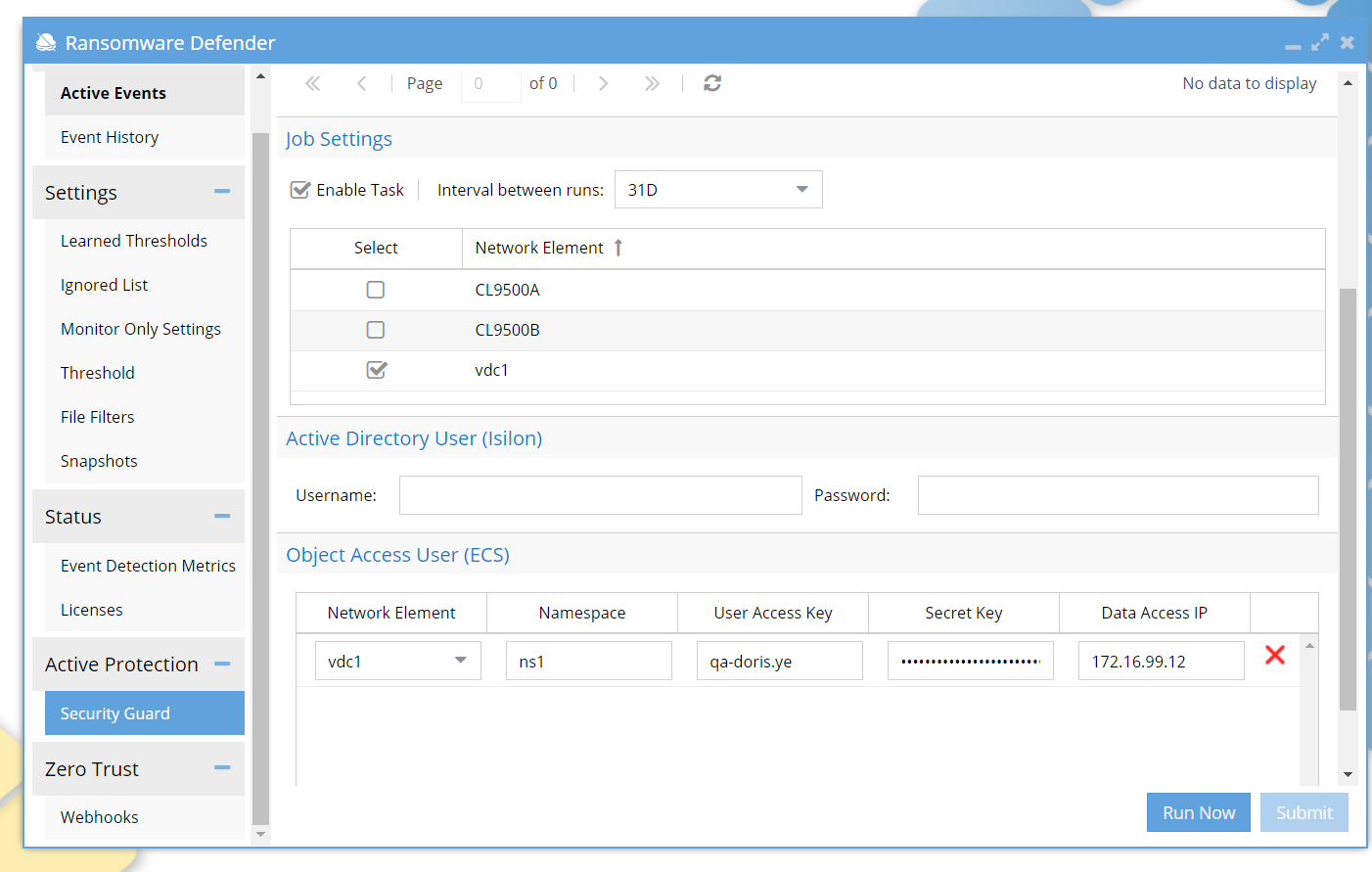
Security Guard
To configure the security guard on ECS, select your Network Element as the source and enter the namespace and credentials. If the data network is different from the management network, enter the IP address of a data node. Security Guard will use this IP address to write objects. It can be the IP of a load balancer.
Data Protection Use Cases
Overview
These are common use cases that expose data to Ransomware risks. The first layer of protection is alerting administrators that suspicious activity may be affecting the data described in these use cases. The Ransomware Defender for ECS solution offers both alerting and early warning in addition to mitigation protection with user account lockout feature that stops any encryption on a per-user basis.
Backup Data on ECS
- Backup applications that store backup data on ECS need the data protected. Backup data and applications are targets for malicious actors that want to take out backup data before an attack.
Long Term Legal Hold Data
- This is another data type that is commonly stored on ECS for long term storage of legal hold data. This data is required for legal compliance and would also be a target to inflict maximum damage by a malicious actor.
Dell ECS Geo Drive
- Geo Drive allows syncing local PC data to ECS as a backup solution backed by object storage. This solution enables long term archive for PC data with a locally mounted Windows driver letter.
- Ransomware will be able to attack Geodrive data through the Windows OS mounted drive.
Archive Data
- Long term storage of enterprise archive data is commonly stored on ECS object storage. This data is exposed by server applications that write this data and potentially exposes PB of data protected by a single user and secret key.