Appliance Security, Authentication, Hardening
- Overview
- User Roles
- Authentication & Login
- Overview
- Read Me First
- How to Enable Administrator RBAC for local OS Users or AD Users (Mandatory)
- How to Configure Active Directory OS Login for Application Users
- How to Configure Additional AD User Appliance Administrators
- How to Configure Additional Local OS Appliance Administrators
- How to create a New RBAC Operator Role for Monitoring Copy Jobs and Stats
- How to Assign CLI commands to a Role
- How to Create a Custom Role
- Managing Access to CLI, WebUI
- How to Access the command line:
- How to Access the WebUI:
- Local OS administration and application cluster operations
- How to add new local admin with Access to the WebUI and CLI
- How to Add AD Users with Access to the WebUI:
- How to Configure password policies for local users and ban failed login attempts
- How to Configure admin only login mode and block user login
Overview
This section covers login and authentication options for Golden Copy administrators.
User Roles
- Golden Copy has an administrator role for cluster configuration and cluster operations (up, down, upgrades). The user is "ecaadmin".
- If additional administrator users are created they are only able to configure copies and run copy jobs. Cluster operations are blocked.
- This guide explains how to create new users, groups and create roles by assigning CLI commands to a group.
Authentication & Login
Overview
The Golden Copy vm supports OS login options and Application authentication options to allow configuration changes. The ecaadmin user is the appliance administrator that is used for managing the software operating environment changes to system configuration files and can also be used to start up and shutdown the application.
The options for OS login include locally created users and groups in the OS to control who can access CLI or Active Directory OS login can also be used.
Read Me First
- This feature is designed for 2 use cases
- Creating new administrators with all CLI command access with either local os login or remote AD login
- Creating a role for operators to monitor copy job progress and view stats but will unable to change configuration.
- Creating additional administrators
- NOTE: ecactl commands are restricted to the ecaadmin user that is the only appliance administrator
How to Enable Administrator RBAC for local OS Users or AD Users (Mandatory)
- Activate additional administrators with this command. Without this command no admin users will be allowed to run any commands other than the builtin ecaadmin appliance administrator. The builtin group for administrators is called ecactl.
- searchctl settings groups add --name ecactl --cmd '*'
How to Configure Active Directory OS Login for Application Users
- This requires joining the appliance to Active Directory.
- login as ecaadmin over ssh
- sudo -s (enter ecaadmin password)
- Type YAST
- Navigate to Windows Domain Membership
- Enter your AD domain and select options as per the screenshot below
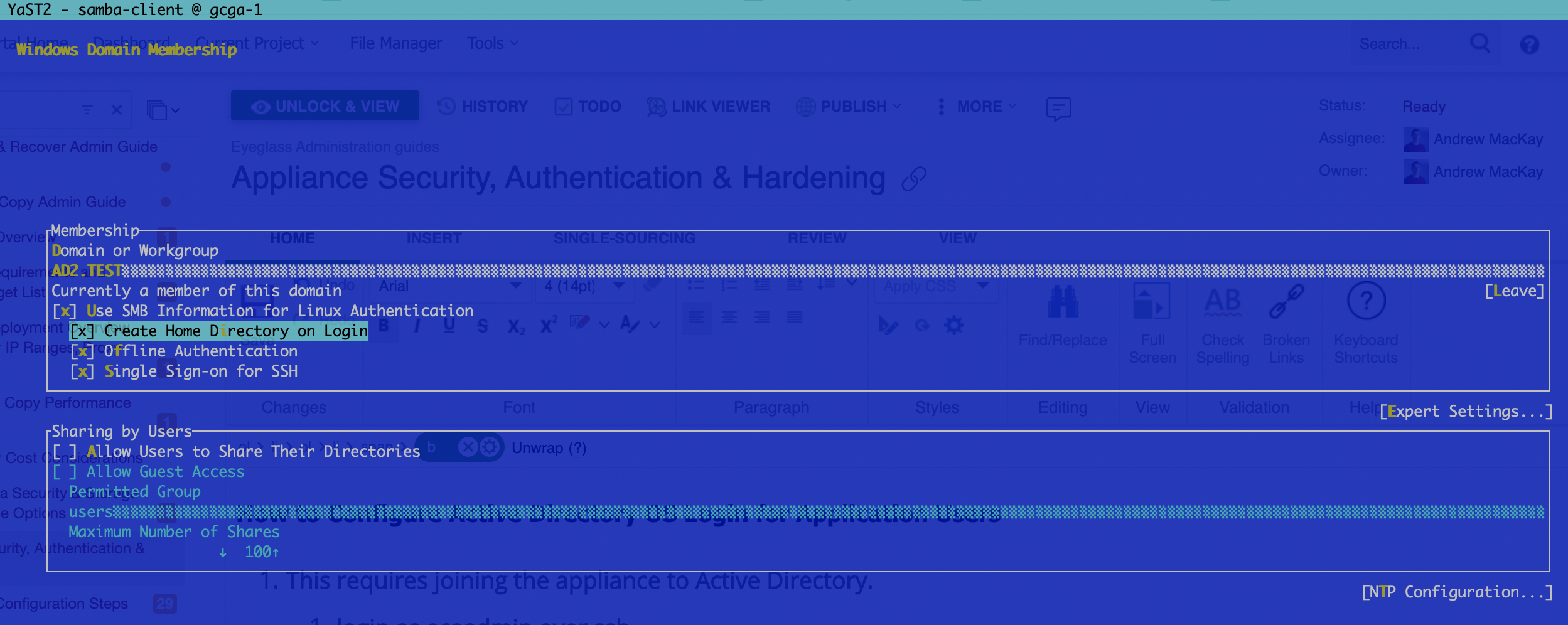
- Enter domain admin or an account that allows computers to be joined to the domain.
- Once joined successfully, exit YAST using tab to select quit.
- Test ssh login with AD
- example login syntax for an AD domain called ad2.test with user demo1. NOTE: the double slash is required to escape slash character
- Linux ssh client login
- ssh ad2.test\\demo1@x.x.x.x OR
- ssh demo1@ad2.test@x.x.x.x
- Putty windows tool
- User name: demo1@ad2.test
- User name: demo1@ad2.test
- Linux ssh client login
- This allows OS login but blocks application CLI commands until the AD user is added to a role.
- Proceed to How to Configure Additional AD appliance Administrators .
How to Configure Additional AD User Appliance Administrators
- Follow these steps to add an AD user to the builtin ecactl local group that provides access to all searchctl commands.
- NOTE: You must follow the steps to join the appliance to AD before using these procedures.
- Login as ecaadmin user
- sudo /usr/sbin/usermod -a -G ecactl AD02\\xxxx (AD02 is the domain name in upper case and xxxx is the user name in AD to add to the group, NOTE the double slash is required as an escape character)
- Logout and test the user access
- example login syntax for an AD domain called ad2.test with user demo1. NOTE: the double slash is required to escape slash character
- Linux ssh client login
- ssh ad2.test\\demo1@x.x.x.x OR
- ssh demo1@ad2.test@x.x.x.x
- Putty windows tool
- User name: demo1@ad2.test
- test CLI commands
How to Configure Additional Local OS Appliance Administrators
- This command will add a new OS local user that will be added to the local OS group ecactl providing access to full appliance cli.
- Ssh ecaadmin@x.x.x.x
- searchctl settings users add --name NAME (you will be prompted to enter the ecaadmin appliance administrator password)
- Set the password for the new user
- sudo passwd NAME (where the user name is entered, you will be prompted to enter the eccaadmin user password, then you will be prompted to set the user password)
- or searchctl settings users remove --name NAME (you will be prompted to confirm)
- This new user will be able to login and run all commands required to manage the appliance, the user is added to the builtin administrator group called ecactl. NOTE: activation of all commands must be completed to enable commands.
- To view the users in this group cat /etc/group
- Login over ssh to test CLI commands
How to create a New RBAC Operator Role for Monitoring Copy Jobs and Stats
- Use this command to create a new group role to assign CLI commands to create a user role that defines an Operator role. This user will be able to monitor copy jobs and statistics on folder configurations.
- ssh to the appliance as ecaadmin
- sudo /usr/sbin/groupadd operator
- (note: do not use spaces or special characters, when prompted for a password enter the ecaadmin password)
- Add the new Group to the appliance with operator role commands
- searchctl settings groups add --name operator --cmd 'searchctl archivedfolders list' 'search jobs *' 'searchctl archivedfolders stats *'
- Add an AD user to the new operator group (NOTE: double slash is required to escape the \ character, use this AD syntax when adding the user)
- sudo /usr/sbin/usermod -a -G operator AD02\\demo1
- (optional) How to remove a user from a group (note: double slash to escape the \ character is required for AD users)
- sudo gpasswd -d AD02\\demo1 ecactl
- example login syntax for an AD domain called ad2.test with user demo1. NOTE: the double slash is required to escape slash character
- Linux ssh client login
- ssh ad2.test\\demo1@x.x.x.x OR
- ssh demo1@ad2.test@x.x.x.x
- Putty windows tool
- User name: demo1@ad2.test
- Linux ssh client login
- Test CLI commands
How to Assign CLI commands to a Role
- Overview
- The commands below allow creation of customer user roles based on a local OS group that can contain local users or AD users. The CLI commands can be assigned to the group. A default group is created named ecactl that is reserved for appliance administration only. New groups can be created using the steps above to create additional roles, the Operator role is defined in this guide.
- Usage to add and remove CLI commands from a group
- searchctl settings groups add --name <group name> --cmd COMMANDS [COMMANDS ...]
- searchctl settings groups remove --name <group name> --cmd COMMANDS [COMMANDS ...]
- Examples of adding CLI commands to an existing group
- Giving access to cli commands as an administrator and all subcommands.
- searchctl settings groups add --name ecactl --cmd '*'
- Giving access to only searchctl archivedfolders list
- searchctl settings groups add --name DemoGr1 --cmd 'searchctl archivedfolders list'
- To add multiple commands at once use a space between each command
- searchctl settings groups add --name DemoGr1 --cmd 'searchctl archivedfolders *' 'searchctl jobs *'
How to Create a Custom Role
- Overview
- This example will create a new role with a group called role1 and assumes AD users are used, in this example the user is AD02\demo1 user in the domain called AD02. The prerequisite requires the appliance is joined to Active Directory following steps in this guide.
- This role will provide monitoring and configuration commands to add or delete or modify folder configurations and start archive copy jobs
- Login as ecaadmin user over ssh
- Create the group
- sudo /usr/sbin/groupadd role1
- Add a user to the group
- sudo /usr/sbin/usermod -a -G operator AD02\\demo1
- Add CLI commands to the group called role1
- searchctl settings groups add --name role1 --cmd 'searchctl archivedfolders *' 'searchctl jobs *' 'searchctl archivedfolders stats *'
- Done
Managing Access to CLI, WebUI
How to Access the command line:
- ssh to the appliance with a local user account.
- The default user is: "ecaadmin", and the default password is: "3y3gl4ss"
- example login syntax for an AD domain called ad2.test with user demo1. NOTE: the double slash is required to escape slash character
- Linux ssh client login
- ssh ad2.test\\demo1@x.x.x.x OR
- ssh demo1@ad2.test@x.x.x.x
- Putty windows tool
- User name: demo1@ad2.test
- Linux ssh client login
- done
How to Access the WebUI:
- https://x.x.x.x (this will present the login page and login with user@domain name and password. NOTE: The user must be added as a local admin first see below) .
Local OS administration and application cluster operations
- cluster CLI commands, webUI and upgrade administrator user is "ecaadmin".
- SSH login or webUI login.
- Configuration and appliance cluster operations.
- OS configuration changes requires sudo -s to become root user and this is granted to the ecaadmin appliance administrator only.
How to add new local admin with Access to the WebUI and CLI
- Create new local OS administrator with the command command in this section. This will add the user to the CLI admin role.
- This command will add the user to the webUI.
- searchctl settings admins add --name <OS user name> --local
- Then set the password for the webUI login
- Installation requires the WebUI password to be set. To reset or change this password follow these steps:
- Login to node 1 over ssh as ecaadmin user and run the command below
- NOTE: Enter the password after the user name
- ecactl cluster exec "htpasswd -b /opt/superna/eca/conf/nginx/.htpasswd <user name> password"
- done. The new password is active immediately on all nodes.
How to Add AD Users with Access to the WebUI:
- Active Directory users can only access the WebUI, no CLI access will be granted.
- The important thing to note is that login will be proxied through to the isilon authentication provider. This means the user you're attempting to give access must have access to at least one SMB share on your isilon to test the password. TCP Port 445 must be open from node 1 to the Isilon
- The important thing to note is that login will be proxied through to the isilon authentication provider. This means the user you're attempting to give access must have access to at least one SMB share on your isilon to test the password. TCP Port 445 must be open from node 1 to the Isilon
- searchctl settings admins add --name <AD user name> (NOTE: syntax is user@domain name)
How to Configure password policies for local users and ban failed login attempts
The all product steps can be followed here for password complexity and life time policies as well as ban failed login attempts
Operations Guide - All products Hardening Guide
How to Configure admin only login mode and block user login
This is for administrator only mode, where end users do not need to login to the UI, and allows an administrator listed on the admin list to login while all other users are blocked if not on the list. NOTE: This includes the local ecaadmin account. The admin list can be listed with searchctl settings admins list.
- Login to node 1 of the Golden Copy cluster as ecaadmin over ssh.
- edit conf file and make the change below.
- nano /opt/superna/eca/eca-env-common.conf
- Add this line export SEARCHMW_ADMIN_MODE_ONLY=true
- Save the file control+x
- Shut down the cluster and start up again to take effect
- ecactl cluster down
- wait until down completes.
- ecactcl cluster up .
- Now only users listed on the admin list will be allowed to login to execute commands.