Zero Trust With Commvault Backup Solution and PowerScale
- Overview
- Solution Components
- Solution Deployment Diagram
- Solution Configuration Steps Job Integrated Pre-Backup Script
- Create the Zero Trust API Configuration
- Commvault Console - Add Pre-Backup Script to a target
- Solution Results Integrated Pre-Backup Script
- Configuration of Integration with Workflows
Overview
How can Zero Trust improve your backup security? With integrated backup repository automated immutable snapshots. Your backup infrastructure is mission critical and the bad actors are targeting your backup hosts. This solution guide will explain how to configure the Zero Trust API and integrate with Commvault to ensure a point in time recovery at the disk level exists automatically. This solution enhances protection by:
- Creating a rollback point Before any job runs to backup corporate data. This is accomplished using a httpClient workflow in Commvault and leverages Superna’s Zero Trust api to create critical snapshots on the PowerScale storage where the backup data is stored
- Key Integration
- Integrated job pre-Processing snapshots to protect the target backup data and allow rollback if a cyber attack or disaster impacts backup hosts.
- Create snapshots via workflows and integrate NAS target storage into workflows
- Optional - integrate with endpoint protection systems or IDS IPS systems to monitor attacks over the network targeting your backup infrastructure and create pro-active automatic immutable snapshots of your backup data.
Solution Components
- Commvault Command Center
- Ransomware Defender for PowerScale
- Ransomware Defender Zero Trust API license
- PowerScale Storage used as Library over SMB or NFS protocol
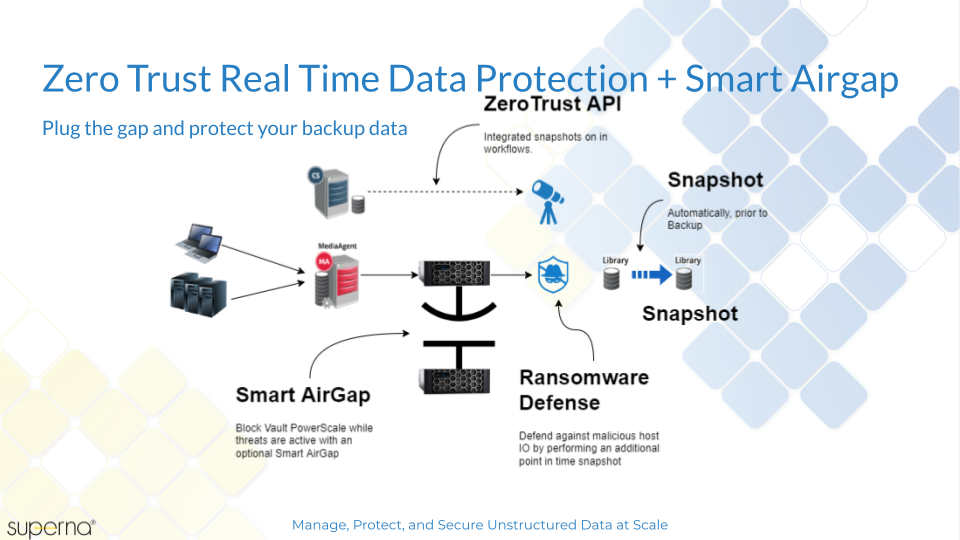
Solution Deployment Diagram
Solution Configuration Steps Job Integrated Pre-Backup Script
- Create an SMB share to store backup data example create an SMB share Commvault on path /ifs/cvMedia
- Create a PowerScale Backup Library in Commvault Control Center
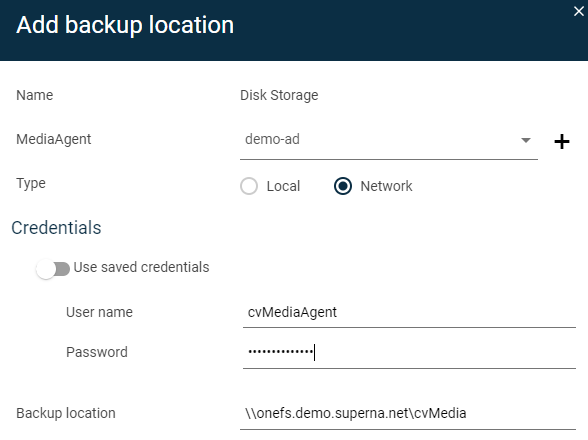
- This will be used to backup data to PowerScale for all clients.
Create the Zero Trust API Configuration
- Create the Zero Trust API authentication token
- Login to Eyeglass as admin
- Main Menu select Eyeglass REST API
- Click create token and enter commvault
- Save this api key
- Get the curl command for Zero Trust Integration
- Select API Explorer tab
- Paste into the token field
- Scroll down to the Ransomware Defender v2 API's
- click the try out button (note this will create a snapshot for any critical paths that are configured)
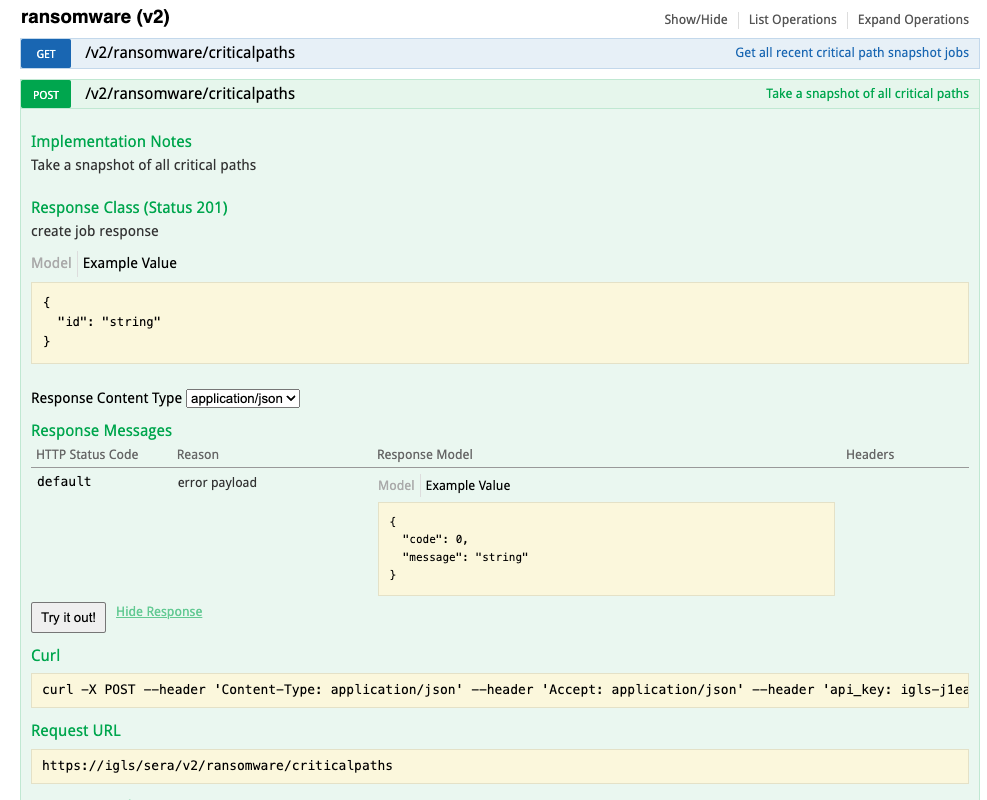
- Copy the curl syntax to a file to be used in steps later on.
Commvault Console - Add Pre-Backup Script to a target
- On the Commvault backup target host create a path c:/zero-trust-scripts
- Optional if the OS version does not include curl command - Download https://skanthak.homepage.t-online.de/download/curl-7.64.1.cab
- Right click extract all files and copy all files into the path below. Copy the files in the i386 folder to c:/zero-trust-scripts/curl
- c:/zero-trust-scripts/curl
- Create a c:/zero-trust-scripts/zerotrust.cmd file
- paste the curl command copied from Eyeglass
- Edit the script as follows
- Replace all the single quotes ' with " (required by Windows batch files)
- add -d "" (allows empty body in the post request)
- add -k (ignores self signed certs)
- modify to call curl binary if you downloaded curl as per steps above, adjust to the OS version and location of curl as needed.
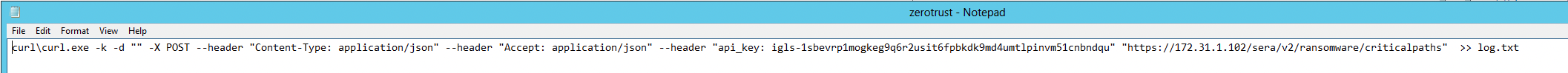
- example script NOTE: Make sure the ip address or hostname of eyeglass can be resolved or reached from the backup target host.
- curl\curl.exe -k -d "" -X POST --header "Content-Type: application/json" --header "Accept: application/json" --header "api_key: igls-1sbevrp1mogkeg9q6r2usit6fpbkdk9md4umtlpinvm51cnbndqu" "https://172.31.1.102/sera/v2/ransomware/criticalpaths"
- To suppress warnings on backup jobs if snapshots already exist you can simply set the 2nd line of the zerotrust.cmd with exit 0, this will ensure no warnings are listed on backup jobs
- The script will create a log file called log.txt to record each execution of the script from backup jobs.
- Configure the pre backup options on the sub client in commvault console
- Click on the target and then follow steps on the link below to add the script c:\zero-trust-scripts\zerotrust.cmd
- See guide link here for details https://documentation.commvault.com/11.24/essential/122245_editing_pre_process_and_post_process_commands.html
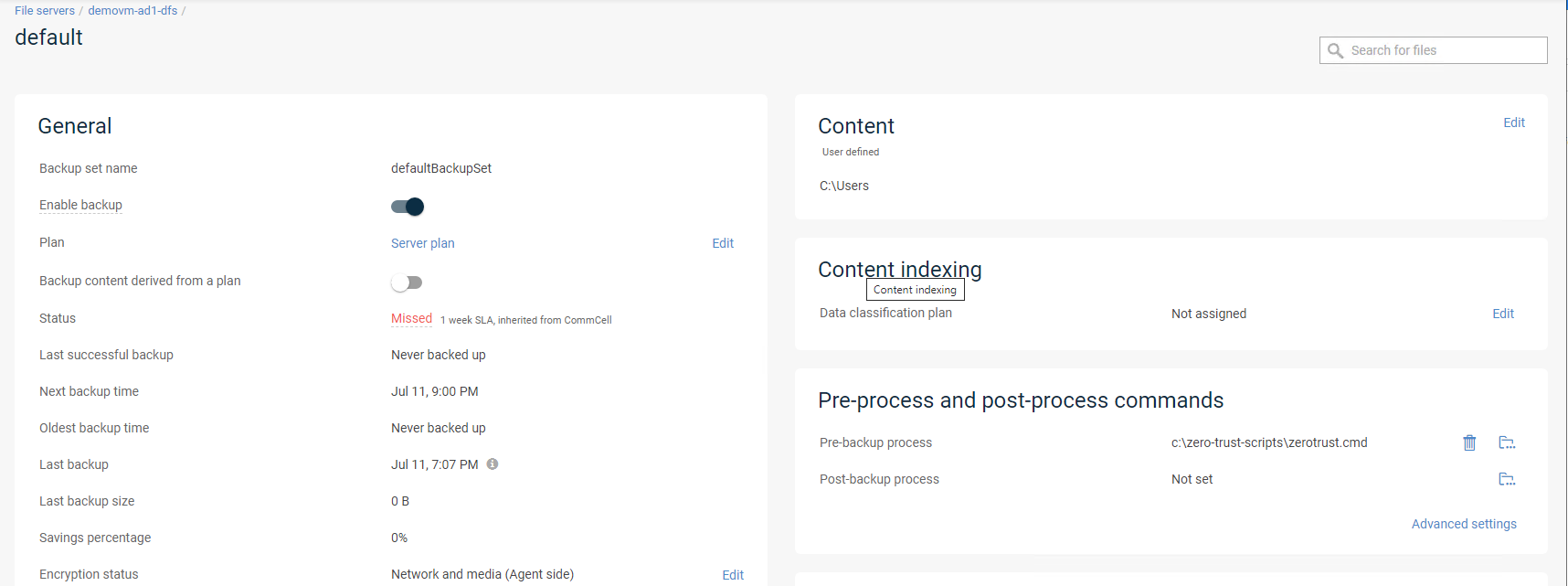
- Create a cmd file on the host c:\zero-trust-scripts\zerotrust.cmd and paste the curl command example (modified for your environment to the file) into the file on the target backup host.
- Test the file from a command prompt by pasting the string above into the command prompt, you should get a response on the.
- Now you can test a backup job for this host.
- Done.
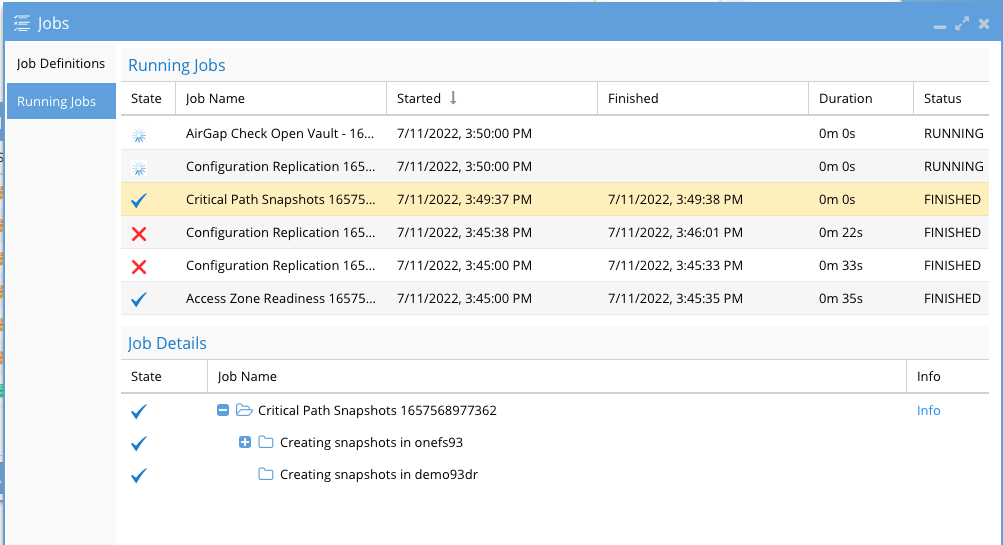
Solution Results Integrated Pre-Backup Script
- Run the configured host backup job
- Review the job execution to verify the script runs without error.
- NOTE: If a previous job has called the zero trust api and snapshots already exist, the return code will be non zero indicating no need to create a new snapshot.
- To suppress this you can simply set the 2nd line of the zerotrust.cmd with exit 0, this will ensure no warnings are listed on backup jobs
- Commvault job log shows the pre-backup script ran with return code 0 indicating data snapshot was created through Ransomware Defender Zero Trust API.
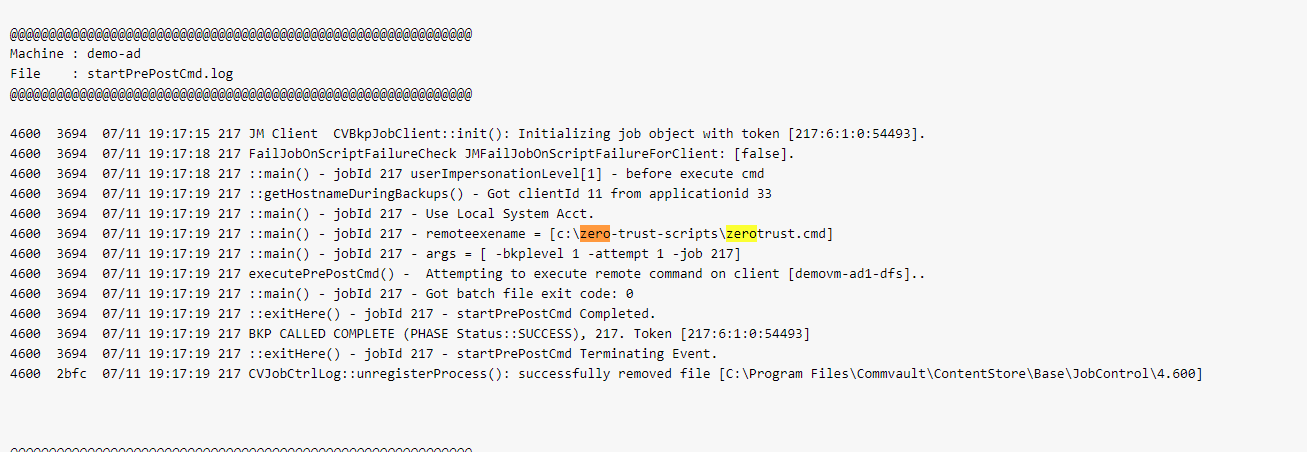
- Review the job execution to verify the script runs without error.
- check the eyeglass job, running jobs view to see the api reached eyeglass
- done
Configuration of Integration with Workflows
- Execute the Workflow
- Review the recent jobs view in Eyeglass
- Login to the PowerScale and verify the new Critical Paths snapshot
- What happens if another job runs, will it create another snapshot?
- The zero trust api has a hold of timer that blocks additional snapshots from being created until the timer expires. This ensures that too many snapshots are not created on the critical paths.
- The default hold-off timer is 1 hour, which means a maximum of 1 snapshot is allowed to be created per hour. Each snapshot has an expiry set for 4 hours and it will auto delete itself.
- How to change the default expiry on critical path snapshots.
- See the guide here.
- Commvault Control Center Workflow configuration
Create a new workflow. The following workflow:
- Creates a snapshot using the HttpClient
- Monitors Backup Progress
- Sends an email on backup success.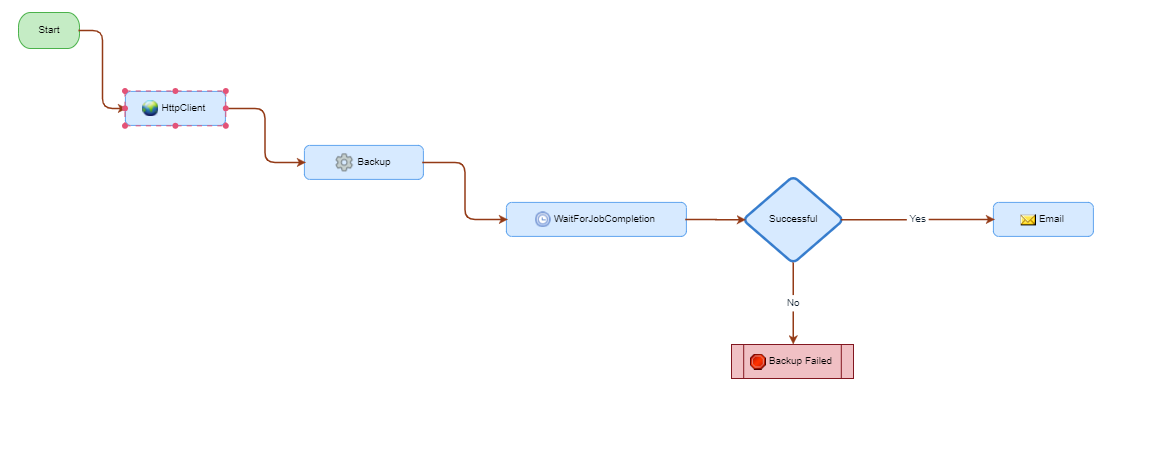
Integrating Superna Zero Trust Critical Paths
*Requires valid cert. Follow commvault procedure for importing self signed certificates:
https://documentation.commvault.com/11.24/expert/116142_adding_commvault_certificate_to_java_keystore_on_http_proxy_servers_with_self_signed_certificate.html
a. Add the HttpClient to your Workflow
b. Create Workflow Variables
string URI https://<igls.fq.dn>/sera/v2/ransomware/criticalpaths
string api_key <igls_criticalPaths_api_key>
string data {}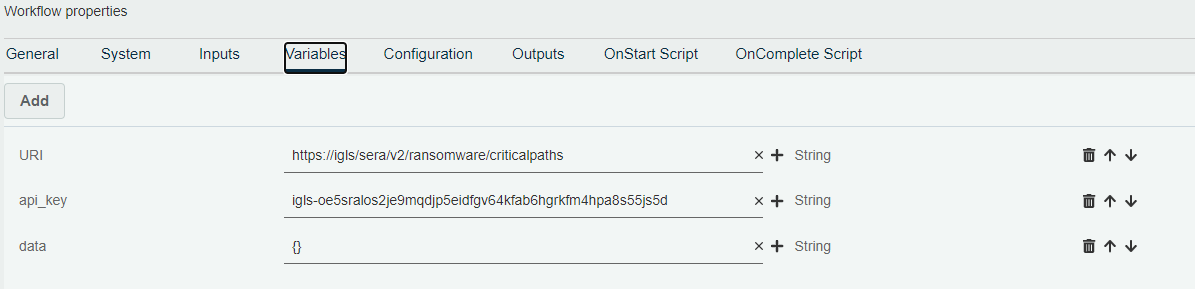
c. Configure HttpClient Inputs
Post: xpath:{/workflow/variables/URI}
Headers:
Accept application/json
Content-Type application/json
api_key xpath:{/workflow/variables/api_key}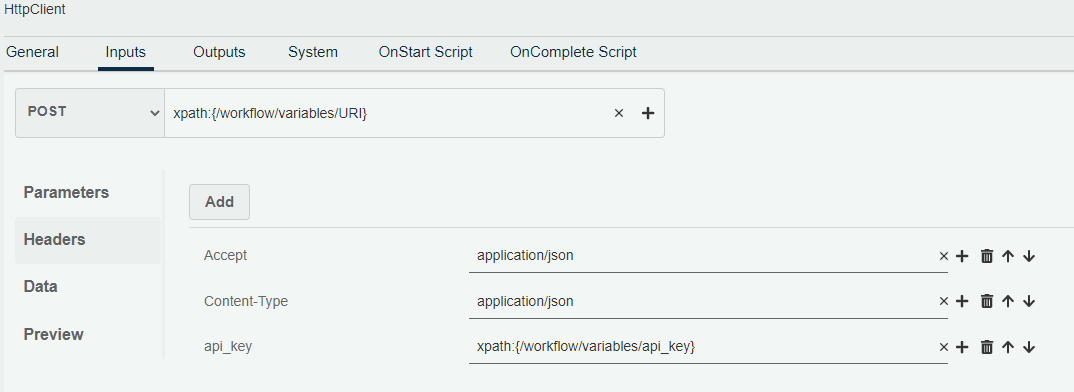
- Save and Deploy the Workflow
- The new Workflow is now available to be executed from the Workflow menu
- Done. Ready for Zero Trust.
© Superna Inc