Eyeglass Alarm forwarding Syslog Guide
- Overview:
- Limitations
- Deprecation Notice
- Supported Alarms
- Requirements:
- Configuration of SYSLOG Forwarding
- How to Filter and Forward alarms
- How to forward by alarm Severity
- How to Forward by Alarm code (Recommended and Supported Method)
- How to Filter by Application
- How to Integrate Ransomware Defender Events with a SIEM
- Syslog format examples to be used for Parsing with a Syslog server
- Example alarm formats
- How to Trouble shoot SYSLOG Forwarding
- Syslog Format Documentation
- Example: Alarm for Ransomware Event
- Example: DR Failover
- Example: Easy Auditor
Overview:
Alarms can be forwarded over syslog. This guide explains how to filter and then forward alarms matching certain criteria. This guide contains the most common examples of how to filter by application or by severity of the alarms.
Limitations
- Syslog are limited in what information can be sent to these protocols. Email alerts will contain more information not available over Syslog
- The intent of SNMP forwarding is to make basic alarm type and severity, and detailed alarm data available in the GUI or via email that supports more text and attachments. This alarm solution provides notification of an alarm, the application that generated it, and the severity.
- Only the documented forwarding solutions below are supported.
Deprecation Notice
- SNMP forwarding has been deprecated as of 2.5.8.1
- NOTE: /var/log/messages will be deprecated and no longer supported in an up coming release as a log to use for forwarding alarms. In a release 2.5.7 syslog will not be used and dedicated alarms log with syslog-ng.
Supported Alarms
- Eyeglass alarms listed here
Requirements:
- Eyeglass OVF version 2.5.8 or greater. Open suse 15.1 or later. Upgrade to the latest OVF if required with the guide here.
Configuration of SYSLOG Forwarding
- The new alarm architecture will use a dedicated log that will roll over and provide alarm history external from the database and alarm history available in the GUI. Release 2.5.7 or later is required.
- Review all the filter examples to match your requirement and replace the filter with one of the following scenarios.
- Log location
- /opt/superna/sca/logs/igls_alarms.log
- Configure Syslog Forwarding
- Ssh to the appliance as admin user
- Sudo -s
- Enter admin password
- nano /etc/syslog-ng/conf.d/superna.conf
- The example below is going to forward specific ransomware defender events.
- Paste the text below into the file and change the text as follows:
- replace x.x.x.x with the ip address of the syslog server ip address you want to forward messages
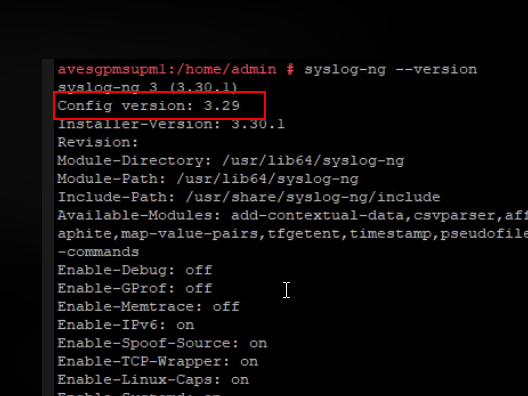
- NOTE Run this command syslog-ng --version and use the version number for Config Version field
- NOTE: Add the version number returned in the first line @version: x.xx
- NOTE Run this command syslog-ng --version and use the version number for Config Version field
@version: 3.29
filter f_superna {
};
source igls_src { file("/opt/superna/sca/logs/igls_alarms.log"); };
destination logserver { udp("x.x.x.x" port(514)); };
log {
source(igls_src);
filter(f_superna);
destination(logserver);
};
- After making changes syslog must be restarted to have the changes take effect
- systemctl restart syslog-ng
- Check that its running
- systemctl status syslog-ng
- It should show active running state
- done
How to Filter and Forward alarms
This section provides examples of how to filter for alarms to forward to syslog.
How to forward by alarm Severity
To combine multiple Alarm severities or combine message strings see example below:
.
filter f_superna {
message("Severity:CRITICAL") or message("Severity:MAJOR") ;
};
How to Forward by Alarm code (Recommended and Supported Method)
Use this filter example to the best option to forward exactly the alarms you need using the alarm code guide. All possible alarms are listed and provides the best option to simplify forwarding exactly the alarms you need to external systems. Get the Alarm codes and use them in the filters.
filter f_superna {
message("RSW0002") or message("RSW0011") ;
};
How to Filter by Application
Each Eyeglass application has an alarm code to easily forward alarms based on the prefix.
- Ransomware Defender prefix - RSW
- Easy Auditor Prefix - EAU
- DR - SCA
How to Forward Ransomware Defender User Lockout and Restored Alarms Except for Security Guard Alarms
In the example below 2 commonly used Ransomware Defender alarms are needed.
- User locked out is RSW0002
- User access restored is RSW0011
- NOTE: Replace the yellow highlight with the security guard service account that you have configured.
filter f_superna {
(message("RSW0002") or message("RSW0011")) and not message("igls-sg") ;
};
This example forwards all Ransomware Defender and Easy Auditor alarms
filter f_superna {
message("RSW") or message("EAU") ;
};
This example forwards all Ransomware Defender alarms Except for Security Guard alarms
NOTE: Replace the yellow highlight with the security guard service account that you have configured.
filter f_superna {
(message("RSW")) and not message("igls-sg");
How to Integrate Ransomware Defender Events with a SIEM
- The syslog message alarms generated by Ransomware Defender when a user is detect with Ransomware an alarm includes details with user ID, ip address and a subset of some of the files that were detected. The ip address can be used in a SIEM trigger to find the Ethernet port of the IP address and disable the port. See the example message format below.
- Use the yellow highlighted sections below to build your parsing and trigger to capture the user name and PC IP address. Using this information build a trigger in your SIEM to take action on the Ethernet port the PC is connected.
- [DEBUG] IGLS_ALARMS:168 - Eyeglass, , Event: 2021-02-26 19:28:23.916, AID:AD02\sgdemo, Port:Nil, Type:null, EntityType:, Extra Data:{"clientIps":"172.31.1.65","info":"Successfully locked out user AD02\\sgdemo"}, Description:Locked user access.172.31.1.65, NSA, Severity:CRITICAL, Impact:false, Category:RSW0002
Syslog format examples to be used for Parsing with a Syslog server
How to search the Eyeglass appliance logs for examples of syslog alarm formatting
- Login to eyeglass vm over ssh as admin
- cat /opt/superna/sca/logs/igls_alarms.log
Example alarm formats
[DEBUG] IGLS_ALARMS:168 - Eyeglass, , Event: 2021-02-26 20:15:23.983, AID:\ifs\data\dfsdata\dlp\, Port:Nil, Type:null, EntityType:, Extra Data:{"reason":"There is no smart quota for /ifs/data/dfsdata/dlp/ limited by a Data Loss Prevention threat detector. no limit is enforced."}, Description:There is no smart quota for a path limited by a Data Loss Prevention threat detector , NSA, Severity:MAJOR, Impact:false, Category:EAU0005
[DEBUG] IGLS_ALARMS:168 - Eyeglass, , Event: 2021-02-26 19:28:14.496, AID:AD02\sgdemo, Port:Nil, Type:null, EntityType:, Extra Data:{"clientIps":"172.31.1.65","event severity":"CRITICAL","user name":"AD02\\sgdemo","affected files":"\\\\prod8\\System\\ifs\\igls-securityguard\\igls-securityguard-test-file-1614385692201.iglsrswtest","affected Isilon clusters":["prod8"],"detectors":"THREAT_DETECTOR_06","number of affected files":"1","info":"Lockout required."}, Description:Ransomware event received. Event severity: CRITICAL, user: AD02\sgdemo172.31.1.65, NSA, Severity:CRITICAL, Impact:false, Category:RSW0001
[DEBUG] IGLS_ALARMS:168 - Eyeglass, , Event: 2021-02-26 19:28:23.916, AID:AD02\sgdemo, Port:Nil, Type:null, EntityType:, Extra Data:{"clientIps":"172.31.1.65","info":"Successfully locked out user AD02\\sgdemo"}, Description:Locked user access.172.31.1.65, NSA, Severity:CRITICAL, Impact:false, Category:RSW0002
How to Trouble shoot SYSLOG Forwarding
- enable verbose logging
- ssh to eyeglass as admin
- sudo -s (enter admin password)
- syslog-ng-ctl verbose --set=on
- Check the statistics of the forwarding to the logserver label (this is the name assigned to the destination in all the examples)
- syslog-ng-ctl stats | grep logserver
- If the counters are not incrementing or show zeros it means nothing has matched your filter and nothing was forwarded to your destination
- Reset the stats to zero to test forwarding again to help trouble sheet the processed counter incrementing
- syslog-ng-ctl stats --reset
How to use packet capture to see syslog messages sent to your target syslog server
- Use this command to monitor any udp syslog messages sent based on matching alarms
- Login as admin
- sudo -s (enter admin password)
- Replace x.x.x.x in the command below with the ip address of your syslog server configured in the above settings file /etc/syslog-ng/config.d/f_superna.conf. This command will NOT display any data until a packet is sent to your syslog server based on the matching logic configured in your filter. Leave the command prompt running and continue to the next step.
- tcpdump -nnAs0 -i eth0 udp port 514 -v | grep -A 2 "x.x.x.x"
- Open new ssh session as the admin user leaving the other session running
- run the random test alarm command, this command will create a random alarm (NOTE: The random alarm may not match your filter logic, adjust your filter logic to match on severity using the example above following all steps to edit the file and restart syslog-ng)
- Run this command below several times until you see a packet appear in the first ssh session that is packet capturing all packets sent to your syslog server. This will help troubleshoot your filter and allow monitoring in realtime for any packets that are sent.
- igls test AlarmTest
- You may also run this command to verify any matches processed by Syslog-ng filter logic
- syslog-ng-ctl stats | grep logserver
- Repeat the test command and stats command to verify your forwarding is working. Check your syslog server to verify the messages are appearing after you have verified the stats and packet capture show successful packets are sent.
- Done.
Syslog Format Documentation
Syslog messages sent by Eyeglass are based on the messages recorded in Eyeglass log file /opt/superna/sca/logs/igls_alarms.log. When they are forwarded to the Syslog management server, they are received and displayed as messages with several sections separated by comma.
Example:
![]()
This Eyeglass forwarded syslog message has the following format (each section is separated by “comma”)
No | Section | Description |
| 1 | [DEBUG] IGLS_ALARMS:168 - Eyeglass | Always: [DEBUG] IGLS_ALARMS:168 - Eyeglass |
| 2 | Always: Empty | |
| 3 | Event: <value> | Value is the timestamp of the event |
| 4 | AID:<value> | Value is the entity of the alarm and it depends on the type of alarm (e.g. For Ransomware detection, the entity is the detected affected user name; For DR Zone Readiness, the entity is the source cluster, target cluster and access zone name) |
| 5 | Port:Nil | Value is always NIL |
| 6 | Type:null | Value is always null |
7 | EntityType: | Value is always blank |
| 8 | Extra Data:{<value>} | Extra Data. Value depends on the type of alarm. Consists of multiple subsections e.g. (not exhaustive list),:
|
| 9 | Description: <value> | Value: depends on the type of alarm. E.g. “Readiness job execution found warnings.” |
| 10 | NSA | Always : NSA |
| 11 | Severity:<value> | Value : depends on the severity of alarm |
| 12 | Impact:false | Value is always “false” |
| 13 | Category:<value> | Value is Alarm Code. refer to this document |
Example: Alarm for Ransomware Event
| No | Section | Extra Data | Description |
| 1 | [DEBUG] IGLS_ALARMS:168 - Eyeglass | ||
| 2 | |||
| 3 | Event: 2023-04-27 01:39:11.445 | Timestamp of the event | |
| 4 | AID:ADTEST1\tuser1 | the entity of the alarm => detected user for Ransomware Event | |
| 5 | Port:Nil | ||
| 6 | Type:null | ||
| 7 | EntityType: | ||
| 8 | Extra Data: | {"clientIps":"172.25.22.21" | Extra Data -Client machine IP address |
| event severity:"WARNING" | Extra Data - Ransomware Defender event severity | ||
| user name:"ADTEST1\\tuser1" | Extra Data - Ransomware Defender event - detected user | ||
| affected zone:"System" | Extra Data - Ransomware Defender event - access zone location of the detected event | ||
| affected Isilon clusters:["dg-isi34"] | Extra Data - Ransomware Defender event - name of PowerScale cluster of the detected event | ||
| detectors:"THREAT_DETECTOR_03" | Extra Data - Ransomware Defender event - type of Threat Detector of the detected event | ||
| number of affected files:"60" | Extra Data - Ransomware Defender event - Signal Strength of the detected event | ||
| info:"Lockout required."} | Extra Data - info related to the detected event | ||
| 9 | Description:Ransomware event received. Event severity: WARNING, user: ADTEST1\tuser1172.25.22.21 | Description of the event - include event severity, user, and clientIP | |
| 10 | NSA | ||
| 11 | Severity:CRITICAL | Severity of the Alarm | |
| 12 | Impact:false | ||
| 13 | Category:RSW0001 | Alarm Code - refer to this document |
Example: DR Failover
No | Section | Extra Data | Description |
1 | [DEBUG] IGLS_ALARMS:168 - Eyeglass |
| |
2 |
| ||
3 | Event: 2023-04-27 22:44:34.25 |
| Timestamp of the event |
4 | AID:DFS Policy Failover 2023-04-27_22-40-01 |
| the entity of the alarm => DFS mode failover |
5 | Port:Nil |
| |
6 | Type:null |
| |
7 | EntityType: |
| |
8 | Extra Data: | {"Status":"Success" | Extra Data: Status of Failover |
| Finished:1682649874241 | Extra Data: Failover Finish time | ||
| Started:1682649601989 | Extra Data: Failover Start time | ||
| URL:"https://172.25.22.42/failover_logs/DFS_Failover__dg-isi34__2023-04-27_22-40-01__SUCCESS/DFS_Failover__dg-isi34__2023-04-27_22-40-01__SUCCESS.html";} | Extra Data: URL of the Failover Log | ||
| 9 | Description:Failover Succeeded |
| Description of the event |
10 | NSA |
| |
11 | Severity:INFORMATIONAL |
| Severity of the Alarm |
12 | Impact:false |
| |
13 | Category:SCA0040 |
| Alarm Code - refer to this document |
Example: Easy Auditor
| No | Section | Extra Data | Description |
| 1 | [DEBUG] IGLS_ALARMS:168 - Eyeglass | ||
| 2 | |||
| 3 | Event: 2023-04-27 23:21:42.879 | Timestamp of the event | |
| 4 | AID:auditreport1 | the entity of the alarm => Easy Auditor report query name | |
| 5 | Port:Nil | ||
| 6 | Type:null | ||
| 7 | EntityType: | ||
| 8 | Extra Data: | {"info":[{"Search type:":"MANUAL"} | Extra Data: type of search: manual (not based on schedule) |
| {"Query name:":"auditreport1"} | Extra Data: query name | ||
| {"Number of records:":0}]} | |||
| 9 | Description:Easy Auditor Report job succeeded. | Description of the event | |
| 10 | NSA | ||
| 11 | Severity:INFORMATIONAL | Severity of the Alarm | |
| 12 | Impact:false | ||
| 13 | Category:EAU0006 | Alarm Code - refer to this document |
© Superna Inc